Seldon Deploy
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

WORLD FINTECH REPORT 2018 Contents 4 Preface
in collaboration with WORLD FINTECH REPORT 2018 Contents 4 Preface 8 Executive Summary FinTechs Are Redefining the Financial Services Customer Journey 13 Competition and Rising Expectations Spur 14 Customer-Centricity Push – Identify gaps left by traditional Financial Services providers and explore changing customer expectations. Emerging Technologies Enable Customer 19 Journey Transformation – Data and insights are reshaping personalized experiences through automation and distributed ledger technology. Alignment with Customer Goals, Creation of 27 Trust, and Delivery of Digital, Agile, and Efficient Processes Are Catalysts for Success – Firms are driving innovation and operational excellence through agile and digital teams. World FinTech Report 2018 The Symbiotic Relationship between FinTechs and Traditional Financial Institutions 35 FinTech and Incumbent Firms’ Respective 36 Competitive Advantages and Shortcomings Make Collaboration a Logical Fit – A partnership ecosystem of FinTechs, incumbents, and other vendors fosters a win-win for stakeholders. Finding the Right Partners for Collaboration 44 Is Essential – Maintaining and accelerating scale is a common FinTech firm struggle, so the right collaboration partner is critical. Successful Collaboration Requires Commitment 49 and Agility from FinTechs and Incumbents – Selection of the appropriate engagement model boosts FinTech scale-up efforts. The Path Forward: An Impending Role for BigTechs? 60 – BigTechs could have massive impact on the Financial Services industry. Preface Once rather homogenous and somewhat staid, the financial services marketplace has transformed into a dynamic milieu of bar-raising specialists. These new-age professionals are devoted to meeting and exceeding the expectations of consumers who have become accustomed to personalized services from industries such as retail, travel, and electronics. Financial services customers no longer rely on one or two firms. -

Kubernetes & AI with Run:AI, Red Hat & Excelero
Kubernetes & AI with Run:AI, Red Hat & Excelero AI WEBINAR Date/Time: Tuesday, June 9 | 9 am PST What’s next in technology and innovation? Kubernetes & AI with Run:AI, Red Hat & Excelero AI WEBINAR Your Host: Presenter: Presenter: Presenter: Tom Leyden Omri Geller Gil Vitzinger William Benton VP Marketing CEO & Co-Founder Software Developer Engineering Manager Kubernetes for AI Workloads Omri Geller, CEO and co-founder, Run:AI A Bit of History Needed flexibility Reproducibility and and better utilization portability Bare Metal Virtual Machines Containers Containers scale easily, they’re lightweight and efficient, they can run any workload, are flexible and can be isolated …But they need orchestration 2 Enter Kubernetes Track, Create Efficient Execute Across Schedule and Cluster Different Operationalize Utilization Hardware 3 Today, 60% of Those Who Deploy Containers Use K8s for Orchestration* *CNCF 4 Now let’s talk about AI Computing Power Fuels Development of AI Deep Learning Classical Machine Learning Manual Engineering 6 Artificial Intelligence is a Completely Different Ballgame New Distributed Experimentation accelerators computing R&D 7 Data Science Workflows and Hardware Accelerators are Highly Coupled Data Hardware scientists accelerators Constant Workflow Under-utilized hassles Limitations GPUs 8 This Leads to Frustration on Both Sides Data Scientists are IT leaders are frustrated – speed and frustrated – GPU productivity are low utilization is low 9 AI Workloads are Also Built on Containers NGC – Nvidia pre-trained models for -

CNCF Webinar Taming Your AI/ML Workloads with Kubeflow
CNCF Webinar Taming Your AI/ML Workloads with Kubeflow The Journey to Version 1.0 David Aronchick (Microsoft) - @aronchick Elvira Dzhuraeva (Cisco) - @elvirafortune Johnu George (Cisco) - @johnugeorge SNARC Maze Solver Minsky / Edmonds (1951) 2000 3 2006 4 2007 5 2008 6 2010 7 2013 8 2014 9 2015 10 Today 11 One More ML ???Solution??? 12 One More ML ???Solution??? 13 14 GitHub Natural Language Search Prototype MVP With Demo In Jupyter Demo with front-end mockup with Experiments.Github.Com: +3 Months Notebook: 2 Weeks blog post: +3 Days https://github.com/hamelsmu/code_search https://towardsdatascience.com/semantic-code-se https://experiments.github.com/ arch-3cd6d244a39c 15 Resource Provisioning Numpy Scheduling Experiment Tracking Jupyter Access Control Declarative Deployment TF.Transform Drivers HP Tuning TF.Estimator Orchestration Profiling Docker Lifecycle Management Validation Seldon Networking KubeCon 2017 17 Resource Provisioning Numpy Scheduling Experiment Tracking Jupyter Access Control Declarative Deployment TF.Transform Drivers HP Tuning TF.Estimator Orchestration Profiling Docker Lifecycle Management Validation Seldon Networking Mission (2017) Make it Easy for Everyone to Develop, Deploy and Manage Portable, Distributed ML on Kubernetes 20 Kubeflow 2018 Mission (2018) Make it Easy for Everyone to Develop, Deploy and Manage Portable, Distributed ML on Kubernetes 23 Kubeflow 2019 Mission (2019) Make it Easy for Everyone to Develop, Deploy and Manage Portable, Distributed ML on Kubernetes 26 Mission (2020) Make it Easy for Everyone -
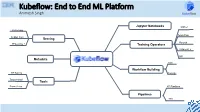
Kubeflow: End to End ML Platform Animesh Singh
Kubeflow: End to End ML Platform Animesh Singh Jupyter Notebooks MXNet KFServing Tensorflow Seldon Core Serving Pytorch TFServing, + Training Operators XGBoost, + MPI Metadata Kale Workflow Building HP Tuning Fairing Tensorboard Tools Prometheus KF Pipelines Pipelines TFX Your Speaker Today: CODAIT 2 Animesh Singh Kubeflow STSM and Chief Architect - Data and AI Open Source github.com/kubeflow Platform o CTO, IBM RedHat Data and AI Open Source Alignment o IBM Kubeflow Engagement Lead, Kubeflow Committer o Chair, Linux Foundation AI - Trusted AI o Chair, CD Foundation MLOps Sig o Ambassador, CNCF o Member of IBM Academy of Technology (IBM AoT) © 2019 IBM Corporation Kubeflow: Current IBM Contributors Untrained Model Christian Kadner Weiqiang Zhuang Tommy Li Andrew Butler Prepared Preparedand Trained AnalyzedData Model Data Deployed Model Jin Chi He Feng Li Ke Zhu Kevin Yu IBM is the 2nd Largest Contributor IBM is the 2nd Largest Contributor IBMers contributing across projects in Kubeflow Kubeflow Services kubectl apply -f tfjob High Level Kubernetes API Server Services Notebooks Low Level APIs / Services Pipelines TFJob PyTorchJob Pipelines CR KFServing Argo Jupyter CR MPIJob Katib Seldon CR Study Job Spark Job Istio Mesh and Gateway Kubebench TFX Developed By Kubeflow Developed Outside Kubeflow Adapted from Kubeflow Contributor Summit 2019 talk: Kubeflow and ML Landscape (Not all components are shown) Community is growing! 8 Multi-User Isolation ML Lifecycle: Build: Development, Training and HPO Untrained Model Prepared Preparedand Trained -

HBSAAL Newsletter December 2019
HBSAAL Newsletter December 2019 INTRODUCTION Dear Friends and Members, It is my pleasure to share with you the first HBS Alumni Angels of London (HBSAAL) newsletter. With over 5,000 alumni in London we play an important role in helping foster an increasingly vibrant and economically important start-up ecosystem. Our local Alumni chapter was launched in 2011, and in that time our members have made investments totalling £7.2M (excluding secondary investments) in over 40 companies. We all know that angel investing requires patience and a portfolio mindset, so we are delighted with notable exits such as Stupeflix and DogBuddy along with significant up-rounds from recent investments such as FlatFair, Seldon, Urban and Pavegen. This past July five companies that received investment from our members were shortlisted for the UK British Angel Association (UKBAA) awards. HBS alum Romi Savova of PensionBee won Best High Growth Woman Founder. Our investors bring more than just cash they also bring a strong network and valuable business experience. We are all committed to life-long learning and our educational events have covered topics ranging from thematic investing in artificial intelligence and fintech to practical tips on angel investing. We had a successful pitch event on Nov 19th, and on Nov 27th we hosted a panel discussion with some of the most successful angel investors in the UK. This was hosted at McKinsey & Co’s new UK headquarters. We will also shortly be introducing you to the wider HBS Alumni Global organisation where you can gain access to syndicated deals from HBSAA Chapters, such as New York, Silicon Valley, Beijing, Paris and Brazil along with access to global educational webinars. -

Build an Event Driven Machine Learning Pipeline on Kubernetes
Assign Hyperparameters Initial Model and Train Create Model PreparedPrepared andand Trained AnalyzedAnalyzed Model DataData Monitor DeployedDeployed Validate and Deploy ModelModel Build an Event Driven Machine Learning Pipeline on Kubernetes Yasushi Osonoi Animesh Singh Developer Advocate IBM STSM, IBM kubeflow kfserving maintainer osonoi animeshsingh Center for Open Source Improving Enterprise AI lifecycle in Open Source Data and AI Technologies (CODAIT) Code – Build and improve practical frameworks to enable more developers to realize immediate value. Content – Showcase solutions for complex and real-world AI problems. Community – Bring developers and data scientists to engage with IBM • Team contributes to over 10 open source projects • 17 committers and many contributors in Apache projects • Over 1100 JIRAs and 66,000 lines of code committed to Apache Spark itself; over 65,000 LoC into SystemML • Over 25 product lines within IBM leveraging Apache Spark • Speakers at over 100 conferences, meetups, unconferences and more CODAIT codait.org 3 DEVELOPER ADVOCATE in TOKYO Tokyo Team is a part of Worldwide Developer Advocate Teams! Developer Advocate City Leader WW Developer Advocate WW Developer Advocate Client Developer Advocate AKIRA ONISHI NORIKO KATO KYOKO NISHITO YASUSHI OSONOI Program Manager WW Developer Advocate WW Developer Advocate Digital Developer Advocate TOSHIO YAMASHITA TAIJI HAGINO AYA TOKURA JUNKI SAGAWA @taiponrock https://developer.ibm.com/patterns/ https://developer.ibm.com/jp/ Please follow me @osonoi IBM’s history -

The AI Growth Capital of Europe 2 London: the AI Growth Capital of Europe London: the AI Growth Capital of Europe 3
London: The AI Growth Capital of Europe 2 London: The AI Growth Capital of Europe London: The AI Growth Capital of Europe 3 About CognitionX CognitionX is the AI advice platform that connects every organisation with a global on-demand network of AI experts. The platform allows experts in AI from around the world to share invaluable expertise with organisations of any size and sector who want to tap into that knowledge. Through the platform, organisations can find an answer to their AI question very quickly, regardless of where they are. AI experts can either share knowledge for free or charge a fee. Founded in 2015, CognitionX’s mission is to drive innovation in, and deployment of, AI by making expertise universally accessible, levelling the playing field for the millions of organisations who don’t have access to strategy consultants or advisory boards, while also giving AI experts a new outlet for, and a way to monetise, their expertise. CognitionX.com Report authors Stephen Allott James Kingston Mick Endsor Matthew Miller Tabitha Goldstaub Milan Sachania Ed Janvrin 4 London: The AI Growth Capital of Europe London: The AI Growth Capital of Europe 5 Mayor’s Foreword There are few areas of innovation that have the power to define our future economy and society more than artificial intelligence. As Mayor of London, it is my goal to ensure both that London is at the forefront of developing and capitalising on these new technologies, and that all Londoners can benefit from the opportunities they will create. I commissioned CognitionX to undertake this research in order to discover the facts behind what many already know to be true - that London is the AI capital of Europe, and that our supportive and welcoming tech ecosystem is the best place to build and scale an AI company. -

From Notebook to Kubeflow Pipelines with Minikf & Kale
From Notebook to Kubeflow Pipelines with MiniKF & Kale Stefano Fioravanzo, Software Engineer, Arrikto Vangelis Koukis, Founder & CTO, Arrikto The Problem ● Setting up an ML stack/pipeline is incredibly hard ● Setting up a production ML stack/pipeline is even harder ● Setting up an ML stack/pipeline that works across the 81% of enterprises that use multi-cloud* environments is EVEN HARDER * Note: For the purposes of this presentation, “local” is a specific type of “multi-cloud” Source: “Building an ML stack with Kubeflow” by Abhishek Gupta, Google AI Huddle - Bay Area Perception: ML Products are mostly about ML Data Verification Machine Resource Management Data Collection Serving Infrastructure ML Code Configuration Monitoring Feature Extraction Process Analysis Tools Management Tools Credit: Hidden Technical Debt of Machine Learning Systems, D. Sculley, et al. Reality: ML Requires DevOps; lots of it Data Machine Monitoring Verification Resource Management Data Collection Configuration Serving ML Infrastructure Code Analysis Tools Feature Extraction Process Management Tools Credit: Hidden Technical Debt of Machine Learning Systems, D. Sculley, et al. Why Kubeflow ● End-to-end solution for ML on Kubernetes ● Containerized workload ● Experiment exploration with state-of-art AI technologies ● Easy on-boarding ● Outstanding community and industry support Community! 6 Just a SMALL sample of community contributions Arrikto IBM ● Jupyter manager UI ● Pipeline components for spark, ffdl ● Pipelines volume support ● Katib ● MiniKF ● KFServing ● -

Red Hat Openshift with Data Services Powered by Intel® Technology
Solution Brief Hybrid-Multicloud | Enterprise Container Platform Cloud-Native, Hybrid-Multicloud Platform: Red Hat OpenShift with Data Services Powered by Intel® Technology Transform your business and get ready for hybrid-multicloud databases, AI, and machine-learning workloads with Red Hat OpenShift Container Platform and Red Hat Data Services on Intel® technology Executive Summary Hybrid-cloud-capable, cloud-native infrastructure is a major part of data center deployments, whether you’re talking about databases, artificial intelligence (AI), machine-learning, or telecommunications workloads. Today’s cloud-native applications use a distributed cloud approach, with some workloads running in private clouds and others running in public Solution Benefits clouds. Ninety-three percent of enterprises have a multicloud strategy.1 • Simple scalability from on- Infrastructure modernization, automation, and cloud-native containers premises to the hybrid cloud helps are important aspects of business transformation. The portability and enterprises easily accommodate repeatability of containers can create cost and resource savings, coupled with additional changes in workload faster time to market and rapid innovation. Containers have little overhead, demands. which helps to lower hardware, maintenance, and licensing costs. They can • High storage performance of be implemented quickly, and components can be shared among containers. Red Hat Data Services (OpenShift Organizations need high performance from their workloads to remain Container Storage) powered by competitive. They require flexible solutions that can run traditional Intel® Optane™ SSDs can help data analytics and AI applications. The solution described in this brief, enterprises get the most out of co-developed by Intel and Red Hat, helps enterprises modernize their data their Intel® Xeon® processors centers and start taking advantage of containers while lowering total costs. -

Explainable. Repeatable. Scalable. Pachyderm: Enterprise
Pachyderm: Enterprise Engineered to make data science Containerized Explainable. Data Pipelines Repeatable. Scalable. Data Versioning Data Lineage The unspoken truth about real-world data science. Instead of spending time innovating and us- ing data science as a force-multiplier to the business, most data science teams are stuck between disparate systems, juggling ad-hoc GOOGLE CLOUD scripts, and hacking their way through com- plex pipeline jungles. AWS AZURE How Pachyderm can help Pachyderm is an enterprise-grade, open source data science platform that makes ex- ON-PREM plainable, repeatable, and scalable Machine Learning (ML) and Artificial Intelligence (AI) HYBRID a reality. Data Versioning Containerized Data True Data Lineage Pipelines A robust data versioning engine Pachyderm enables you to build Pachyderm provides you with true powers the heart of the Pachyderm end-to-end data pipelines using data lineage. Our solution helps platform. Every change to your any language or framework you capture the entire journey data gets tracked and managed you want. Together with data of your data, code, models, and with ease. Adding, removing and versioning, Pacyderm Pipelines results in one unified system. With modifying files all get meticulously intelligently process only changed that power at your finger tips, your captured and recorded by the data, while also efficiently data team can reason about the Pachyderm engine automatically. distributing the computation complex relationships between With git-like familiarity, teams of across the cluster for faster results. them and drive business decisions data scientists can swiftly track the efficiently. dependencies and relationships between datasets, their models, and everything in between with “Pachyderm helped us confidence. -
2021 Mlops Platforms Vendor Analysis Report
2021 MLOps Platforms Vendor Analysis Report Executive guidance on selecting the optimal technology solution for supporting your MLOps journey 1 Intro Defined as a separate discipline only recently, the MLOps movement has already moved from the сonceptualization stage to corporate boardroom discussions on implementation. But while nearly every industry has now entered the AI race, adoption of operations best practices and thus competitiveness remains unequal. AI and ML leaders today already have a better understanding of the MLOps lifecycle and the procedures and technology required for deploying new models into production (and subsequently scaling them). The State of AI 2021 report by McKinsey notes that 51% of AI high performers have standard tool frameworks and development processes in place for developing AI models. However, laggards can still catch up and even overtake the leaders if they get strategic with process standardization and automation, which in fact is what most MLOps platforms promise to facilitate. An MLOps platform is a centralized infrastructure hub featuring resources, tools, frameworks, and process automation scenarios for managing all steps of the machine learning lifecycle. Machine Learning Lifecycle Datasets e Tr as s a ele re in R tu in D a g e p Fe l oy e t u p Experiment ML Ops m o C g Te in g s a tin k g c r Code Pa Monito 2 Back in the day, IDEs revolutionized the speed and quality of software development. MLOps vendors are now attempting to create a similar level of speed, convenience, and automation for data scientists with the ultimate promise of reducing model development and deployment timelines by 2X-10X. -
Introduction 2 ML on Kubernetes 3 Tooling Availability 3 Effective
Introduction 2 ML on Kubernetes 3 Tooling availability 3 Effective Resources Utilization 4 Separation of Concerns 4 Popular ML tools with Kubernetes 5 AI, Machine Learning and Deep Learning 5 Machine Learning Phases & Tools 7 Experimental Phase 8 Data Preparation, Cleanup, and Visualization 9 ML Framework and Model Algorithm 10 Model Training 11 Validation and Tuning 13 Production Phase 14 Model Training 15 Model Serving 16 Model Performance and Tuning 16 Higher-level Machine Learning Tools 17 Jupyter Notebook 17 Pipelines 19 KubeFlow 19 How Spectro Cloud Can Help 20 Introduction With businesses and enterprises continuing to transform themselves into technology companies, applications are the new life-blood of business. Applications are defining the way most companies in many industries compete, to provide the best customer experiences and drive competitive advantage. As these companies look to further drive positive business outcomes, they’re increasingly relying on insights from the massive amounts of data they’ve generated and collected over the years. However, with traditional algorithms finding it difficult to process and provide any meaningful value from the data, organizations are turning to data science and machine learning. These new technologies not only help analyze the data, but provide real-time business decisions and intelligence, without human intervention. From human-like voice assistants, to fraud detection or even automatic mortgage approvals - the possibilities of machine learning applications are limitless. Increasingly conventional and machine-learning applications alike are built and deployed as containers, running on the popular orchestration platform Kubernetes. Enterprises are adopting Kubernetes to drive down operational costs, increase business agility, and provide faster time to market for their applications.