Establishing Trust in Disconnected Environments Featuring Grace Lewis As Interviewed by Suzanne Miller
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Samsung Podcasts RSS Spec 060921
Samsung Podcasts RSS Spec June 2021 SAMSUNG C&S SAMSUNG CONFIDENTIAL Introduction The purpose of this document is to provide technical guidelines to podcasters for optimal exposure of their RSS feeds on Samsung Podcasts. Notes • Submitting feeds to Samsung Podcasts will not prevent submission to other platforms. • Samsung Podcasts will not re-cache or re-host audio content. • These guidelines are meant to reflect requirements used by other standard podcast platforms. • Some requirements are meant to support future V2 features, marked in red. Samsung Proprietary and Confidential 2 RSS Feed Requirements Samsung Proprietary and Confidential 3 Feed Requirements: Podcast “Podcast” is defined as an ordered collection of episodes. A podcast must: • Be described by a valid RSS feed that conforms to RSS 2.0 specifications • Be freely reachable, not requiring login, token, or similar information • Be uniquely defined by its <link> field (Samsung Podcasts will handle a podcast as a new podcast if this field changes) Samsung Podcasts will use podcast metadata accessed via the <link> field. Podcasters will need to ensure that artwork files are valid, reachable, and accurate. Samsung Podcasts may choose to cache artwork and metadata to optimize performance, but will not cache or re-host audio data. Unreachable or uninterpretable RSS feeds will be disabled by Samsung Podcasts. Please ensure that explicit words in Podcast titles and descriptions are censored in your metadata before submitting. Failure to censor explicit words could result in suspension of content from the platform. 4 Feed Requirements: Episode “Episode” is defined as an audio segment expressed through an audio file. Podcast episodes must: • Be uniquely defined by its <guid> field (Samsung Podcasts will handle an episode as new if the GUID is new or changed) • Be freely reachable, not requiring login, token, or similar information • Provide a supported audio file format (mp3, m4a, aac, wav, ogg) Samsung Podcasts will use episode metadata accessed via the <link> field and episode <guid> field. -

Reuters Institute Digital News Report 2020
Reuters Institute Digital News Report 2020 Reuters Institute Digital News Report 2020 Nic Newman with Richard Fletcher, Anne Schulz, Simge Andı, and Rasmus Kleis Nielsen Supported by Surveyed by © Reuters Institute for the Study of Journalism Reuters Institute for the Study of Journalism / Digital News Report 2020 4 Contents Foreword by Rasmus Kleis Nielsen 5 3.15 Netherlands 76 Methodology 6 3.16 Norway 77 Authorship and Research Acknowledgements 7 3.17 Poland 78 3.18 Portugal 79 SECTION 1 3.19 Romania 80 Executive Summary and Key Findings by Nic Newman 9 3.20 Slovakia 81 3.21 Spain 82 SECTION 2 3.22 Sweden 83 Further Analysis and International Comparison 33 3.23 Switzerland 84 2.1 How and Why People are Paying for Online News 34 3.24 Turkey 85 2.2 The Resurgence and Importance of Email Newsletters 38 AMERICAS 2.3 How Do People Want the Media to Cover Politics? 42 3.25 United States 88 2.4 Global Turmoil in the Neighbourhood: 3.26 Argentina 89 Problems Mount for Regional and Local News 47 3.27 Brazil 90 2.5 How People Access News about Climate Change 52 3.28 Canada 91 3.29 Chile 92 SECTION 3 3.30 Mexico 93 Country and Market Data 59 ASIA PACIFIC EUROPE 3.31 Australia 96 3.01 United Kingdom 62 3.32 Hong Kong 97 3.02 Austria 63 3.33 Japan 98 3.03 Belgium 64 3.34 Malaysia 99 3.04 Bulgaria 65 3.35 Philippines 100 3.05 Croatia 66 3.36 Singapore 101 3.06 Czech Republic 67 3.37 South Korea 102 3.07 Denmark 68 3.38 Taiwan 103 3.08 Finland 69 AFRICA 3.09 France 70 3.39 Kenya 106 3.10 Germany 71 3.40 South Africa 107 3.11 Greece 72 3.12 Hungary 73 SECTION 4 3.13 Ireland 74 References and Selected Publications 109 3.14 Italy 75 4 / 5 Foreword Professor Rasmus Kleis Nielsen Director, Reuters Institute for the Study of Journalism (RISJ) The coronavirus crisis is having a profound impact not just on Our main survey this year covered respondents in 40 markets, our health and our communities, but also on the news media. -
What Is a Podcast? the Term Podcast Comes from a Combination of Ipod and Broadcast
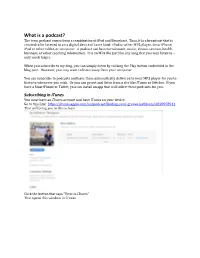
What is a podcast? The term podcast comes from a combination of iPod and Broadcast. Thus, it is a broadcast that is created to be listened to on a digital device of some kind: iPod or other MP3 player, SmartPhone, iPad or other tablet, or computer. A podcast can be entertainment, music, drama, sermon, health, business, or other coaching information. It is an MP3 file just like any song that you may listen to – only much larger. When you subscribe to my blog, you can simply listen by clicking the Play button embedded in the blog post. However, you may want to listen away from your computer. You can subscribe to podcasts and have them automatically delivered to your MP3 player for you to listen to whenever you wish. Or you can go out and listen from a site like iTunes or Stitcher. If you have a SmartPhone or Tablet, you can install an app that will collect these podcasts for you. Subscribing in iTunes You must have an iTunes account and have iTunes on your device. Go to this link: https://itunes.apple.com/us/podcast/finding-your-groove-kathleen/id829978911 That will bring you to this screen Click the button that says “View in iTunes” That opens this window in iTunes Click the Subscribe button just underneath the photo. To share this podcast with someone else, click the drop-down arrow just to the right of the Subscribe button. That will give you these share options: Tell a Friend, Share on Twitter, Share on Facebook, Copy Link (allows you to manually e-mail someone). -

A Nova Mídia Podcast: Um Estudo De Caso Do Programa Matando Robôs Gigantes
UNIVERSIDADE FEDERAL DO RIO DE JANEIRO ESCOLA DE COMUNICAÇÃO CENTRO DE FILOSOFIA E CIÊNCIAS HUMANAS JORNALISMO A NOVA MÍDIA PODCAST: UM ESTUDO DE CASO DO PROGRAMA MATANDO ROBÔS GIGANTES TÁBATA CRISTINA PIRES FLORES RIO DE JANEIRO 2014 UNIVERSIDADE FEDERAL DO RIO DE JANEIRO ESCOLA DE COMUNICAÇÃO CENTRO DE FILOSOFIA E CIÊNCIAS HUMANAS JORNALISMO A NOVA MÍDIA PODCAST: UM ESTUDO DE CASO DO PROGRAMA MATANDO ROBÔS GIGANTES Monografia submetida à Banca de Graduação como requisito para obtenção do diploma de Comunicação Social/ Jornalismo. TÁBATA CRISTINA PIRES FLORES Orientador: Octávio Aragão RIO DE JANEIRO 2014 UNIVERSIDADE FEDERAL DO RIO DE JANEIRO ESCOLA DE COMUNICAÇÃO TERMO DE APROVAÇÃO A Comissão Examinadora, abaixo assinada, avalia a Monografia A nova mídia podcast: um estudo de caso do programa Matando Robôs Gigantes, escrita por Tábata Flores. Monografia examinada: Rio de Janeiro, ___ de _______________ de 2014. Comissão Examinadora: Orientador: Prof. Octávio Aragão Doutor em Artes Visuais pela Escola de Belas Artes - UFRJ Departamento de Comunicação - UFRJ Prof. Fernando Mansur Doutor em Comunicação pela Escola de Comunicação - UFRJ Departamento de Comunicação - UFRJ Lúcio Luiz Corrêa da Silva Doutorando em Educação pela Universidade Estácio de Sá Programa de Pós-Graduação em Educação (Tecnologias de Informação e Comunicação nos Processos Educacionais) – Universidade Estácio de Sá RIO DE JANEIRO 2014 FICHA CATALOGRÁFICA FLORES, Tábata. A nova mídia podcast: um estudo de caso do programa Matando Robôs Gigantes. Rio de Janeiro, 2014. Monografia (Graduação em Comunicação Social/Jornalismo) – Universidade Federal do Rio de Janeiro – UFRJ, Escola de Comunicação – ECO. Orientador: Octávio Aragão Orientadora: Raquel Paiva de Araújo Soares FLORES, Tábata. A nova mídia podcast: um estudo de caso do programa Matando Robôs Gigantes. -

Despliegue España-América Latina De Broadcatching E-Learning
Despliegue España-América Latina de Broadcatching e-learning Rafael García Monroy E.T.S.I.T. U.P.M. Departamento Ingeniería de Sistemas Telemáticos e-mail: [email protected] Abstract . Los avances tecnológicos y la eliminación de fronteras que resultan del potente y exponencial despliegue de Internet permiten que compartir vídeos de material educativo de gran calidad sea viable. Ya que las exigencias de los usuarios finales –alumnos- crecen paralelamente a la adopción de los avances mencionados, y las posibilidades reales de mejorar los servicios son una realidad, no queda más que emplear las herramientas existentes para crear nuevos modelos innovadores que mejoren constantemente las plataformas de difusión de conocimiento, pilar del desarrollo sostenible. El siguiente artículo describe el despliegue de un modelo e-learning basado en Broadcatching (BitTorrent, + RSS), a través del cual clases de vídeo grabadas en España podrán ser inmediatamente distribuidas a universidades latinoamericanas con las que se tenga convenio, compartiendo recursos de red y, de gran importancia, diseminando los ficheros educativos con una excelente calidad de contenido. De esta manera, la distancia, el costo de distribución y las limitaciones temporales pasan a segundo plano, permitiendo que los contenidos educativos de primera calidad tengan un acceso de naturaleza universal. Palabras clave: BitTorrent, broadcatching, e-learning, P2P, RSS, vídeo. 1 Introducción redes de distribución. Y es precisamente este el punto que hay que explotar para que el alumno obtenga el La cooperación en cualquier ámbito conlleva al mejor contenido educativo posible: la obtención de desarrollo sostenible, en que las partes implicadas vídeos de clase de alta definición que son pesados, comparten el fruto de la inversión. -

History Podcasts
BOSTON COLLEGE DEPARTMENT OF HISTORY SUMMER 2013 Podcasts 47 podcast series for history lovers with long commutes, a little free time, or a beach vacation Africa Past and Present Cool Things in the Collection, Kansas http://afripod.aodl.org/ Museum of History https://itunes.apple.com/us/podcast/cool- American Social History Project things-in-collection/id151869274 http://ashp.cuny.edu/category/category/ podcasts/ Darwin from the Fitzwilliam Museum, Cambridge Ancient Authors Podcasts http://www.darwinendlessforms.org/ http://www.haverford.edu/classics/audio/ podcasts/#darwinfest Ancient Rome Refocused Drinking Matters: The History of Early http://www.ancientromerefocused.org/ Modern Drinking Houses https://itunes.apple.com/us/podcast/ Archaeology from OUP drinking-matters/id279398893 http://podcasts.ox.ac.uk/keywords/ archaeology Early American Social History (Warwick University) BBC History Magazine Podcasts https://itunes.apple.com/us/itunes-u/early- http://www.historyextra.com/podcasts american-social-history/id407479152 BBC Radio 4 In our Time Footnoting History http://www.bbc.co.uk/programmes/ http://www.footnotinghistory.com/ b006qykl/episodes/player calendar-of-podcasts.html Binge Thinking History Podcast Free Audio Books from the Public Domain http://bingethinkinghistory.blogspot.com/ http://librivox.org/ Boston College Front Row Podcasts Henry VIII Podcasts from the British Library http://frontrow.bc.edu/programs/ http://www.bl.uk/whatson/podcasts/ prevexhibition/henry/index.html British Library Oral History Podcasts http://sounds.bl.uk/Oral-history -

Is There a Podcast in Your Future?
Is There a Podcast In Your Future? October 24, 2109 ATE PI Conference Michael Lesiecki, [email protected] Center for Occupational Research and Development Acknowledgements At CORD Did You Know? • Podcasting has been around for awhile (since the 1980s, to be exact), but in the last few years, the level of interest amongst listeners has grown dramatically.* • Today, approximately 67 million Americans over the age of 12 listen to podcasts monthly.* * https://www.impactbnd.com/blog/how-to-measure-podcast-metrics-performance Did You Know? • Podcasting has been around for awhile (since the 1980s, to be exact), but in the last few years, the level of interest amongst listeners has grown dramatically.* • Today, approximately 67 million Americans over the age of 12 listen to podcasts monthly.* What Would You Like To Know? * https://www.impactbnd.com/blog/how-to-measure-podcast-metrics-performance Five Steps to a Successful Podcast 1. Start With a Mission https://www.entrepreneur.com/article/243024 Five Steps to a Successful Podcast 1. Start With a Mission 2. Create a clever name, use clever titles https://www.entrepreneur.com/article/243024 Five Steps to a Successful Podcast 1. Start With a Mission 2. Create a clever name 3. Secure interesting interviews https://www.entrepreneur.com/article/243024 Five Steps to a Successful Podcast 1. Start With a Mission 2. Create a clever name 3. Secure interesting interviews 4. Produce high quality audio https://www.entrepreneur.com/article/243024 Five Steps to a Successful Podcast 1. Start With a Mission 2. Create a clever name 3. Secure interesting interviews 4. -

Podcasting As Public Media: the Future of U.S
International Journal of Communication 14(2020), 1683–1704 1932–8036/20200005 Podcasting as Public Media: The Future of U.S. News, Public Affairs, and Educational Podcasts PATRICIA AUFDERHEIDE American University, USA DAVID LIEBERMAN The New School, USA ATIKA ALKHALLOUF American University, USA JIJI MAJIRI UGBOMA The New School, USA This article identifies a U.S.-based podcasting ecology as public media and then examines the threats to its future. It first identifies characteristics of a set of podcasts in the United States that allow them to be usefully described as public podcasting. Second, it looks at current business trends in podcasting as platformization proceeds. Third, it identifies threats to public podcasting’s current business practices. Finally, it analyzes responses within public podcasting to the potential threats. The article concludes that currently, the public podcast ecology in the United States maintains some immunity from the most immediate threats, but there are also underappreciated threats to it, both internally and externally. Keywords: podcasting, public media, platformization, business trends, public podcasting ecology As U.S. podcasting becomes a commercially viable part of the media landscape, are its public service functions at risk? This article explores that question, in the process postulating that the concept of public podcasting has utility in describing not only a range of podcasting practices, but also an ecology within the larger podcasting ecology—one that permits analysis of both business methods and social practices, and one that deserves attention and even protection. This analysis contributes to the burgeoning literature on Patricia Aufderheide: [email protected] David Lieberman: [email protected] Atika Alkhallouf: [email protected] Jiji Majiri Ugboma: [email protected] Date submitted: 2019‒09‒27 Copyright © 2020 (Patricia Aufderheide, David Lieberman, Atika Alkhallouf, and Jiji Majiri Ugboma). -

History Contents
RSS - Wikipedia, the free encyclopedia Page 1 of 6 RSS From Wikipedia, the free encyclopedia (Redirected from RSS feeds) RSS (most commonly expanded as Really Simple RSS Syndication ) is a family of web feed formats used to publish frequently updated works—such as blog entries, news headlines, audio, and video—in a standardized format. [2] An RSS document (which is called a "feed", "web feed", [3] or "channel") includes full or summarized text, plus metadata such as publishing dates and authorship. Web feeds benefit publishers by letting them syndicate content automatically. They benefit readers who want to subscribe to timely updates The RSS logo from favored websites or to aggregate feeds from many sites into one place. RSS feeds can be read Filename .rss, .xml using software called an "RSS reader", "feed extension reader", or "aggregator", which can be web-based, application/rss+xml desktop-based, or mobile-device-based. A Internet standardized XML file format allows the media type (Registration Being information to be published once and viewed by Prepared) [1] many different programs. The user subscribes to a feed by entering into the reader the feed's URI or Type of Web syndication by clicking an RSS icon in a web browser that format initiates the subscription process. The RSS reader Extended XML checks the user's subscribed feeds regularly for from new work, downloads any updates that it finds, and provides a user interface to monitor and read the feeds. RSS formats are specified using XML, a generic specification for the creation of data formats. Although RSS formats have evolved from as early as March 1999, [4] it was between 2005 and 2006 when RSS gained widespread use, and the (" ") icon was decided upon by several major Web browsers. -

Open Content by Daniel Jacobson and Harold Neal
Open Content By Daniel Jacobson and Harold Neal National Public Radio (Presented on July 24, 2008) Overview ‣ Who is NPR? ‣ Landscape of Open Content ‣ RSS ‣ NPR’s Solution ‣ NPR’s Architecture ‣ NPR API Demo ‣ API Stats and Details ‣ The Future of NPR’s API ‣ Questions? Who is NPR? ‣ NPR (National Public Radio) ‣ Leading producer and distributor of radio programming ‣ All Things Considered, Morning Edition, Fresh Air, Wait, Wait, Don’t Tell Me, etc. ‣ Broadcasted on over 800 local radio stations nationwide ‣ NPR Digital Media ‣ Website (NPR.org) with audio content from radio programs ‣ Web-Only content including blogs, slideshows, editorial columns ‣ About 250 produced podcasts, with over 600 in directory ‣ Mobile sites ‣ API and other syndication Open Content Landscape Amount of Content Available in APIs Content UGC E-Comme rce Major Media Aggregators Aggregators Sites Producers Content Providers What is Major Media Doing? ‣ Most offer RSS for very specific feeds ‣ Some offer extended RSS or comparable ‣ MediaRSS extensions ‣ Podcast enclosures ‣ Very few comprehensive APIs (although seems to be changing) Really Successful Syndication Really Stingy Syndication ‣ Gets some content out there ‣ There is meaty real content there ‣ Drives traffic back to the site ‣ Namespace extensions are limited ‣ A lot of traction in the marketplace ‣ Embraces content lock-down model NPR’s Solution… Offer Full Content : Open API ‣ Allows users to innovate and be creative with our content ‣ A few of us, millions of you ‣ Unlimited people thinking about -

INTERNET BLOGGING/PODCASTS and WEB COMMUNITIES Blogs, Podcasts, Web Communities and Similar Internet Postings Are a Window Throu
INTERNET BLOGGING/PODCASTS AND WEB COMMUNITIES Blogs, Podcasts, Web communities and similar Internet postings are a window through which the world sees us. Officers, employees, and soldiers will find innovative opportunities to use this technology to present both the Gospel and the ministry of The Salvation Army. This creativity is strongly encouraged, with the following safeguards. Salvation Army personnel must be guided by the following: A. Avoid anything likely to injure the body of Christ, or reflect unfavorably upon the integrity and purpose of The Salvation Army. B. Only official Salvation Army Blogs/Podcasts registered with Territorial Headquarters or National Headquarters may contain the following: 1. Registered Salvation Army identification, such as a crest, shield, or other service marks or trademarks. 2. Pictures, videos or sound recordings from Salvation Army activities. (Exception: A personal Blog/Podcast may contain pictures or video of family members in uniform or in Salvation Army activities.) 3. Copyrighted Salvation Army music or literature. C. Official Salvation Army Blogs/Podcasts must be guided by the following: 1. Any Blog/Podcast underwritten in any fashion from Salvation Army funds is considered official. This underwriting includes the Blog/Podcast being hosted on a Salvation Army server or hosting fees paid from Salvation Army funds. 2. The establishment of an official Salvation Army Blog/Podcast must be approved by the Command Headquarters for corps and other ministry units. Command Headquarters Blogs/Podcasts must be approved by the Territorial Headquarters. All "official" sites must be registered with the National/Territorial Community Relations Department. 3. Any pictures, videos, music and literature posted must have the appropriate releases or copyright permission on file. -

Download Tut Tv Show Torrent Nefarious
download tut tv show torrent nefarious. It uses Jackett and Transmission under the hood. Jackett searches for torrents and Transmission handles the downloading. Search and discover TV & Movies (by popularity, genres, year etc) Auto download TV & Movies Find similar and recommended TV & Movies (via The Movie Database & Rotten Tomatoes) Manually search and download Jackett’s torrent results Supports blacklisting torrent results (i.e, permanently avoid a bad/fake torrent) Supports quality profiles (i.e only download 1080p Movies and 720p TV) Supports whether to download media with hardcoded subtitles or not Supports user defined keywords to filter results (i.e, ignore “x265”, “hevc” codecs) Monitor transmission results & status from within the app Self/auto updating application, so you’re always up-to-date Supports multiple users and permission groups (i.e, admin users and regular users) Responsive Design (looks great on desktops, tablets and small devices like phones) Includes movie trailers Automatically renames media Supports multiple languages (TMDB supports internationalized Titles, Descriptions and Poster artwork) Webhook support (i.e, can post to Slack, Telegram etc when media downloads) Imports existing libraries VPN integration (optional) Auto download subtitles. Contents. Screenshots. Login. Search. TV Result. Movie Result. Download Status. Discover via TMDB. Discover via Rotten Tomatoes. Wanted. Watching. Settings. Search Manual. Mobile Friendly. Dependencies. Setup. You must have docker and docker-compose already installed. See dependencies. Part 1. Clone the nefarious repository: Copy the default environment file to make changes: Edit .env as needed for your settings, at least defining HOST_DOWNLOAD_PATH to something like HOST_DOWNLOAD_PATH=/path/to/downloads . You should never need to edit the docker-compose.yml file since all settings are read from .env .