Breaking Trust: Shades of Crisis Across an Insecure Software Supply Chain #Accyber
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Drinkerdrinker
FREE DRINKERDRINKER Volume 41 No. 3 June/July 2019 The Anglers, Teddington – see page 38 WETHERSPOON OUR PARTNERSHIP WITH CAMRA All CAMRA members receive £20 worth of 50p vouchers towards the price of one pint of real ale or real cider; visit the camra website for further details: camra.org.uk Check out our international craft brewers’ showcase ales, featuring some of the best brewers from around the world, available in pubs each month. Wetherspoon also supports local brewers, over 450 of which are set up to deliver to their local pubs. We run regular guest ale lists and have over 200 beers available for pubs to order throughout the year; ask at the bar for your favourite. CAMRA ALSO FEATURES 243 WETHERSPOON PUBS IN ITS GOOD BEER GUIDE Editorial London Drinker is published on behalf of the how CAMRA’s national and local Greater London branches of CAMRA, the campaigning can work well together. Of Campaign for Real Ale, and is edited by Tony course we must continue to campaign Hedger. It is printed by Cliffe Enterprise, Eastbourne, BN22 8TR. for pubs but that doesn’t mean that we DRINKERDRINKER can’t have fun while we do it. If at the CAMRA is a not-for-profit company limited by guarantee and registered in England; same time we can raise CAMRA’s profile company no. 1270286. Registered office: as a positive, forward-thinking and fun 230 Hatfield Road, St. Albans, organisation to join, then so much the Hertfordshire AL1 4LW. better. Material for publication, Welcome to a including press The campaign will be officially releases, should preferably be sent by ‘Summer of Pub’ e-mail to [email protected]. -
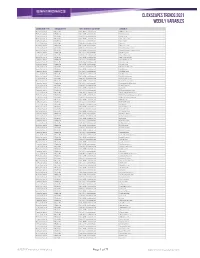
Clickscapes Trends 2021 Weekly Variables
ClickScapes Trends 2021 Weekly VariableS Connection Type Variable Type Tier 1 Interest Category Variable Home Internet Website Arts & Entertainment 1075koolfm.com Home Internet Website Arts & Entertainment 8tracks.com Home Internet Website Arts & Entertainment 9gag.com Home Internet Website Arts & Entertainment abs-cbn.com Home Internet Website Arts & Entertainment aetv.com Home Internet Website Arts & Entertainment ago.ca Home Internet Website Arts & Entertainment allmusic.com Home Internet Website Arts & Entertainment amazonvideo.com Home Internet Website Arts & Entertainment amphitheatrecogeco.com Home Internet Website Arts & Entertainment ancestry.ca Home Internet Website Arts & Entertainment ancestry.com Home Internet Website Arts & Entertainment applemusic.com Home Internet Website Arts & Entertainment archambault.ca Home Internet Website Arts & Entertainment archive.org Home Internet Website Arts & Entertainment artnet.com Home Internet Website Arts & Entertainment atomtickets.com Home Internet Website Arts & Entertainment audible.ca Home Internet Website Arts & Entertainment audible.com Home Internet Website Arts & Entertainment audiobooks.com Home Internet Website Arts & Entertainment audioboom.com Home Internet Website Arts & Entertainment bandcamp.com Home Internet Website Arts & Entertainment bandsintown.com Home Internet Website Arts & Entertainment barnesandnoble.com Home Internet Website Arts & Entertainment bellmedia.ca Home Internet Website Arts & Entertainment bgr.com Home Internet Website Arts & Entertainment bibliocommons.com -

Distributed Attacks and the Healthcare Industry 01/14/2021
Distributed Attacks and the Healthcare Industry 01/14/2021 Report #: 202101141030 Agenda Image source: CBS News • Overview of distributed attacks • Supply chain attacks • Discussion of SolarWinds attack • Managed Service Provider attacks • Discussion of Blackbaud attack • How to think about distributed attacks • References • Questions Slides Key: Non-Technical: Managerial, strategic and high- level (general audience) Technical: Tactical / IOCs; requiring in-depth knowledge (sysadmins, IRT) 2 Overview: Distributed Attacks What is a distributed attack? Traditional attack = a single compromise impacts a single organization 3 Overview: Distributed Attacks (continued) What is a distributed attack? Distributed attack = a single compromise that impacts multiple organizations Image source: cyber.gc.ca 4 Overview: Distributed Attacks (continued) But what about DDoS (distributed denial of service) attacks? Not a distributed attack in the context of the presentation, since it only targets one organization! Image source: F5 Networks We will be discussing two types of distributed attacks in this presentation, both of which present a significant threat to healthcare: supply chain attacks and managed service provider attacks. We will be analyzing two cases: the SolarWinds attack (supply chain), as well as the Blackbaud breach (managed service provider). This presentation is based on the best information available at the time of delivery – new details will emerge. 5 Supply Chain Attacks Image source: Slidebazaar What is a supply chain? • A supply chain -

Systematic Scoping Review on Social Media Monitoring Methods and Interventions Relating to Vaccine Hesitancy
TECHNICAL REPORT Systematic scoping review on social media monitoring methods and interventions relating to vaccine hesitancy www.ecdc.europa.eu ECDC TECHNICAL REPORT Systematic scoping review on social media monitoring methods and interventions relating to vaccine hesitancy This report was commissioned by the European Centre for Disease Prevention and Control (ECDC) and coordinated by Kate Olsson with the support of Judit Takács. The scoping review was performed by researchers from the Vaccine Confidence Project, at the London School of Hygiene & Tropical Medicine (contract number ECD8894). Authors: Emilie Karafillakis, Clarissa Simas, Sam Martin, Sara Dada, Heidi Larson. Acknowledgements ECDC would like to acknowledge contributions to the project from the expert reviewers: Dan Arthus, University College London; Maged N Kamel Boulos, University of the Highlands and Islands, Sandra Alexiu, GP Association Bucharest and Franklin Apfel and Sabrina Cecconi, World Health Communication Associates. ECDC would also like to acknowledge ECDC colleagues who reviewed and contributed to the document: John Kinsman, Andrea Würz and Marybelle Stryk. Suggested citation: European Centre for Disease Prevention and Control. Systematic scoping review on social media monitoring methods and interventions relating to vaccine hesitancy. Stockholm: ECDC; 2020. Stockholm, February 2020 ISBN 978-92-9498-452-4 doi: 10.2900/260624 Catalogue number TQ-04-20-076-EN-N © European Centre for Disease Prevention and Control, 2020 Reproduction is authorised, provided the -

How Location-Based Social Network Applications Are Being Used
Sean David Brennan HOW LOCATION-BASED SOCIAL NETWORK APPLICATIONS ARE BEING USED JYVÄSKYLÄN YLIOPISTO TIETOJENKÄSITTELYTIETEIDEN LAITOS 2015 ABSTRACT Brennan, Sean David How Location-Based Social Network Applications Are Being Used Jyväskylä: University of Jyväskylä, 2015, 60 p. Information Systems Science, Master’s Thesis Supervisor: Veijalainen, Jari Location-based social network applications have globally become very popular with the expansion of smartphone usage. Location-based social networks (LBSN) can be defined as a site that uses Web 2.0 technology, GPS, WiFi positioning or mobile devices to allow people to share their locations, which is referred to commonly as a check-in, and to connect with their friends, find places of interest, and leave reviews or tips on specific venues. The aim of this study was to examine how location-based social applications are being used. The methods of this study comprised of a literature review and a discussion on prior research based on a selection of user studies on location-based social networks. This study also aimed at answering a number of sub-questions on user behavior such as activity patterns, motivations for sharing location, privacy concerns, and current and future trends in the field. Twelve LBSN user behavior studies were reviewed in this study. Eight of the user studies reviewed involved the application Foursquare. Research methods on eight of the reviewed studies were studies utilizing databases of the check-ins from the application itself or utilizing Twitter in their analysis. Four of the reviewed studies were user studies involving interviews and surveys. Three main themes emerged from the articles, which were activity patterns, motivations for sharing, and privacy concerns. -
Virtual Classroom Challenges Amid Pandemic for Future Teachers
The Gonzaga Bulletin A student publication of Gonzaga University DECEMBER 3, 2020 www.gonzagabulletin.com VOL. 132 ISSUE 15 Virtual classroom challenges amid pandemic for future teachers By NATALIE RIETH ue to COVID-19 restrictions, Gonzaga Dstudents enrolled in the special education classroom placement and classroom management courses have had to face a delayed classroom placement within schools local to the Spokane area. This set- back has given students the unique opportunity of observing challenges faced by students and teachers within the special education classroom as a result of the pandemic. Before receiving their placement, students were required to complete a virtual module, where they were introduced to online teaching styles and virtual educational platforms, as a part of the 30 hours they must complete observing their assigned classroom. With a mix of students placed in in-person and remote classrooms, students have been able to reflect on the effects the pandemic has had within special education classrooms in each COVID-19 learning environment. Sarah Merlino, a student enrolled in both special education courses, attends BULLETIN FILE PHOTO SEE TEACHERS PAGE 2 GU grad, Lexi Rutherford, student teaches a second grade classroom at St. Aloysius Catholic School in 2016. Gonzaga says goodbye to three key staff members By KAYLA FREIDRICH During the last couple of months, Gonzaga University has seen the resignation of many high positions in multiple offices and is left with the task of figuring out what to do with these positions moving forward. Kelly Alvarado-Young, Amy Swank and Richard Menard have all made significant contributions to their respective departments during their time at GU. -

Chapter 2: Literature Review 19
Value impact of social media: a perspective from the independent brewery sector GODSON, Mark St John Available from the Sheffield Hallam University Research Archive (SHURA) at: http://shura.shu.ac.uk/25371/ A Sheffield Hallam University thesis This thesis is protected by copyright which belongs to the author. The content must not be changed in any way or sold commercially in any format or medium without the formal permission of the author. When referring to this work, full bibliographic details including the author, title, awarding institution and date of the thesis must be given. Please visit http://shura.shu.ac.uk/25371/ and http://shura.shu.ac.uk/information.html for further details about copyright and re-use permissions. Value impact of social media: A perspective from the independent brewery sector Mark St John Godson A thesis submitted in partial fulfilment of the requirements of Sheffield Hallam University for the degree of Doctor of Business Administration December 2018 ii Table of Contents Chapter 1: Introduction 1 1.1: Introduction - What is this Study About? 1 1.2: Why is this of Interest from a Research Perspective? 3 1.2.1: Background to the independent brewery sector 3 1.2.2: Topicality of social media 4 1.2.3: Personal interests of the researcher 5 1.3: Research Aims, Objectives and Questions 6 1.4: Conducting the Research 8 1.5: Expected Contribution to Knowledge and Practice 8 1.6: Supporting Literature 14 1.7: Structure of Thesis 16 Chapter 2: Literature Review 19 2.1: Introduction 19 2.1.1: Literature review method -

The Emerging Cyber Threat to Industrial Control Systems 03
02 Lloyd’s disclaimer This report has been co-produced by Lloyd's, CyberCube and Guy Carpenter for general information purposes only. While care has been taken in gathering the data and preparing the report Lloyd's does not make any representations or warranties as to its accuracy or completeness and expressly excludes to the maximum extent permitted by law all those that might otherwise be implied. Lloyd's accepts no responsibility or liability for any loss or damage of any nature occasioned to any person as a result of acting or refraining from acting as a result of, or in reliance on, any statement, fact, figure or expression of opinion or belief contained in this report. This report does not constitute advice of any kind. © Lloyd’s 2021 All rights reserved About Lloyd’s Lloyd's is the world's specialist insurance and reinsurance market. Under our globally trusted name, we act as the market's custodian. Backed by diverse global capital and excellent financial ratings, Lloyd's works with a global network to grow the insured world –building resilience of local communities and strengthening global economic growth. With expertise earned over centuries, Lloyd's is the foundation of the insurance industry and the future of it. Led by expert underwriters and brokers who cover more than 200 territories, the Lloyd’s market develops the essential, complex and critical insurance needed to underwrite human progress. About CyberCube CyberCube delivers the world’s leading cyber risk analytics for the insurance industry. With best-in-class data access and advanced multi-disciplinary analytics, the company’s cloud-based platform helps insurance organizations make better decisions when placing insurance, underwriting cyber risk and managing cyber risk aggregation. -

Quarterly Report on Global Security Trends
Quarterly Report on Global Security Trends 3rd Quarter of 2020 Table of Contents 1. Executive Summary ............................................................................................................. 2 2. Featured Topics ..................................................................................................................... 4 2.1. Intensifying attacks on supply chains .................................................................... 4 2.1.1. Supply chain attack .............................................................................................. 6 2.1.1.1. Methods of supply chain attacks ................................................................. 6 2.1.1.2. Danger of supply chain attacks ................................................................. 10 2.1.2. Countermeasures against supply chain attacks ..................................... 11 2.1.2.1. Security measures in software development ....................................... 11 2.1.2.2. Security measures in service entrustment ............................................ 13 2.1.3. Conclusion ............................................................................................................. 14 2.2. Increase of double-extortion ransomware attacks ......................................... 15 2.2.1. Overall status of double-extortion ransomware attacks ....................... 15 2.2.2. Double-extortion ransomware attacks ........................................................ 16 2.2.3. How should we respond to double-extortion -
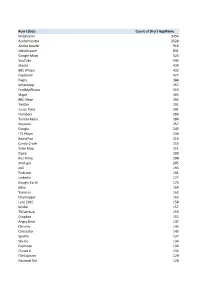
Row Labels Count of Short Appname Mobileiron 3454 Authenticator 2528
Row Labels Count of Short AppName MobileIron 3454 Authenticator 2528 Adobe Reader 916 vWorkspace 831 Google Maps 624 YouTube 543 iBooks 434 BBC iPlayer 432 Facebook 427 Pages 388 WhatsApp 357 FindMyiPhone 313 Skype 303 BBC News 292 Twitter 291 Junos Pulse 291 Numbers 289 TuneIn Radio 284 Keynote 257 Google 243 ITV Player 234 BoardPad 219 Candy Crush 215 Tube Map 211 Zipcar 209 Bus Times 208 mod.gov 205 4oD 193 Podcasts 191 LinkedIn 177 Google Earth 172 eBay 164 Yammer 163 Citymapper 163 Lync 2010 158 Kindle 157 TVCatchup 153 Dropbox 152 Angry Birds 147 Chrome 143 Calculator 143 Spotify 137 Sky Go 136 Evernote 134 iTunes U 132 FileExplorer 129 National Rail 128 iPlayer Radio 127 FasterScan 125 BBC Weather 125 FasterScan HD 124 Gmail 123 Instagram 116 Cleaner Brent 107 Viber 104 Find Friends 98 PDF Expert 95 Solitaire 91 SlideShark 89 Netflix 89 Dictation 89 com.amazon.AmazonUK 88 Flashlight 81 iMovie 79 Temple Run 2 77 Smart Office 2 74 Dictionary 72 UK & ROI 71 Journey Pro 71 iPhoto 70 TripAdvisor 68 Guardian iPad edition 68 Shazam 67 Messenger 65 Bible 64 BBC Sport 63 Rightmove 62 London 62 Sky Sports 61 Subway Surf 60 Temple Run 60 Yahoo Mail 58 thetrainline 58 Minion Rush 58 Demand 5 57 Documents 55 Argos 55 LBC 54 Sky+ 51 MailOnline 51 GarageBand 51 Calc 51 TV Guide 49 Phone Edition 49 Translate 48 Print Portal 48 Standard 48 Word 47 Skitch 47 CloudOn 47 Tablet Edition 46 MyFitnessPal 46 Bus London 46 Snapchat 45 Drive 42 4 Pics 1 Word 41 TED 39 Skyscanner 39 SoundCloud 39 PowerPoint 39 Zoopla 38 Flow Free 38 Excel 38 Radioplayer -

Kaspersky Lab Threat Predictions for 2018
Kaspersky Security Bulletin: KASPERSKY LAB THREAT PREDICTIONS FOR 2018 Version 1.1. KASPERSKY SECURITY BULLETIN: THREAT PREDICTIONS FOR 2018 CONTENTS Introduction ..................................................................................................3 Advanced Persistent Threat Predictions by the Global Research and Analysis Team (GReAT) .....................4 Introduction .............................................................................................5 Our record ................................................................................................6 What can we expect in 2018? ...........................................................7 Conclusion .............................................................................................18 Industry and Technology Predictions .............................................19 Introduction ..........................................................................................20 Threat Predictions for Automotive ..........................................21 Threat Predictions for Connected Health ........................... 26 Threat Predictions for Financial Services ............................30 Threat Predictions for Industrial Security ........................... 35 Threat Predictions for Cryptocurrencies ........................... 39 Conclusion ............................................................................................42 This report was updated on December 6, 2017 – with additional content for Threat Predictions for Financial Services -

Cyber Security Report 2021 Contents
CYBER SECURITY REPORT 2021 CONTENTS 04 CHAPTER 1: INTRODUCTION TO THE CHECK POINT 2021 SECURITY REPORT 07 CHAPTER 2: TIMELINE OF 2020'S MAJOR CYBER EVENTS 12 CHAPTER 3: 2020’S CYBER SECURITY TRENDS 13 From on-premise to cloud environments: spotlighting the SolarWinds supply chain attack 15 Vishing: the new old-school 17 Double extortion ramping up 2 19 ‘HellCare’—have healthcare attacks gone too far? 21 Thread hijacking—your own email could be used against you 23 Remote access vulnerabilities 26 Mobile threats—from COVID-19 to zero-click attacks 28 Privilege escalation in the cloud 30 CHAPTER 4: SILVER LININGS IN 2020 CHECK POINT SOFTWARE SECURITY REPORT 2021 34 CHAPTER 5: GLOBAL MALWARE STATISTICS 35 Cyber attack categories by region 37 Global Threat Index map 38 Top malicious file types—web versus email 40 Global malware statistics 40 Top malware families 42 Global analysis of malware families 53 CHAPTER 6: HIGH-PROFILE GLOBAL VULNERABILITIES 54 Draytek Vigor Command Injection (CVE-2020-8515) 55 F5 BIG-IP Remote Code Execution (CVE-2020-5902) 3 56 Citrix ADC Authentication Bypass (CVE-2020-8193) 57 CHAPTER 7: RECOMMENDATIONS FOR PREVENTING THE NEXT CYBER PANDEMIC 58 Real-time prevention 58 Secure your everything 59 Consolidation and visibility 59 Absolute Zero-Trust security 60 Keep your threat intelligence up to date 61 APPENDIX: MALWARE FAMILY STATISTICS CHECK POINT SOFTWARE SECURITY REPORT 2021 CHAPTER 1 “PREDICTION IS VERY DIFFICULT, ESPECIALLY IF IT'S ABOUT THE FUTURE.” —Niels Bohr, Nobel Laureate in Physics 4 INTRODUCTION TO CHECK POINT 2021 SECURITY REPORT CHECK POINT SOFTWARE 1SECURITY REPORT 2021 The year 2020 will be one that we will all remember for a very long time.