CYBORGIZATION and VIRTUAL WORLDS: Portals to Altered Reality
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CLONES, BONES and TWILIGHT ZONES: PROTECTING the DIGITAL PERSONA of the QUICK, the DEAD and the IMAGINARY by Josephj
CLONES, BONES AND TWILIGHT ZONES: PROTECTING THE DIGITAL PERSONA OF THE QUICK, THE DEAD AND THE IMAGINARY By JosephJ. Beard' ABSTRACT This article explores a developing technology-the creation of digi- tal replicas of individuals, both living and dead, as well as the creation of totally imaginary humans. The article examines the various laws, includ- ing copyright, sui generis, right of publicity and trademark, that may be employed to prevent the creation, duplication and exploitation of digital replicas of individuals as well as to prevent unauthorized alteration of ex- isting images of a person. With respect to totally imaginary digital hu- mans, the article addresses the issue of whether such virtual humans should be treated like real humans or simply as highly sophisticated forms of animated cartoon characters. TABLE OF CONTENTS I. IN TR O DU C T IO N ................................................................................................ 1166 II. CLONES: DIGITAL REPLICAS OF LIVING INDIVIDUALS ........................ 1171 A. Preventing the Unauthorized Creation or Duplication of a Digital Clone ...1171 1. PhysicalAppearance ............................................................................ 1172 a) The D irect A pproach ...................................................................... 1172 i) The T echnology ....................................................................... 1172 ii) Copyright ................................................................................. 1176 iii) Sui generis Protection -

Humana.Mente Complete Issue 26.Pdf
EDITORIAL MANAGER: DUCCIO MANETTI - UNIVERSITY OF FLORENCE Editorial EXECUTIVE DIRECTOR: SILVANO ZIPOLI CAIANI - UNIVERSITY OF MILAN VICE DIRECTOR: MARCO FENICI - UNIVERSITY OF SIENA Board INTERNATIONAL EDITORIAL BOARD JOHN BELL - UNIVERSITY OF WESTERN ONTARIO GIOVANNI BONIOLO - INSTITUTE OF MOLECULAR ONCOLOGY FOUNDATION MARIA LUISA DALLA CHIARA - UNIVERSITY OF FLORENCE DIMITRI D'ANDREA - UNIVERSITY OF FLORENCE BERNARDINO FANTINI - UNIVERSITÉ DE GENÈVE LUCIANO FLORIDI - UNIVERSITY OF OXFORD MASSIMO INGUSCIO - EUROPEAN LABORATORY FOR NON-LINEAR SPECTROSCOPY GEORGE LAKOFF - UNIVERSITY OF CALIFORNIA, BERKELEY PAOLO PARRINI - UNIVERSITY OF FLORENCE ALBERTO PERUZZI - UNIVERSITY OF FLORENCE JEAN PETITOT - CREA, CENTRE DE RECHERCHE EN ÉPISTÉMOLOGIE APPLIQUÉE CORRADO SINIGAGLIA - UNIVERSITY OF MILAN BAS C. VAN FRAASSEN - SAN FRANCISCO STATE UNIVERSITY CONSULTING EDITORS CARLO GABBANI - UNIVERSITY OF FLORENCE ROBERTA LANFREDINI - UNIVERSITY OF FLORENCE MARCO SALUCCI - UNIVERSITY OF FLORENCE ELENA ACUTI - UNIVERSITY OF FLORENCE MATTEO BORRI - UNIVERSITÉ DE GENÈVE ROBERTO CIUNI - UNIVERSITY OF DELFT Editorial SCILLA BELLUCCI, LAURA BERITELLI, RICCARDO FURI, ALICE GIULIANI, STEFANO LICCIOLI, UMBERTO MAIONCHI Staff HUMANA.MENTE - QUARTERLY JOURNAL OF PHILOSOPHY TABLE OF CONTENTS INTRODUCTION Fiorella Battaglia, Antonio Carnevale Epistemological and Moral Problems with Human Enhancement III PAPERS Volker Gerhardt Technology as a Medium of Ethics and Culture 1 Nikil Mukerji, Julian Nida-Rümelin Towards a Moderate Stance on Human Enhancement 17 Christopher -

Mind-Crafting: Anticipatory Critique of Transhumanist Mind-Uploading in German High Modernist Novels Nathan Jensen Bates a Disse
Mind-Crafting: Anticipatory Critique of Transhumanist Mind-Uploading in German High Modernist Novels Nathan Jensen Bates A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy University of Washington 2018 Reading Committee: Richard Block, Chair Sabine Wilke Ellwood Wiggins Program Authorized to Offer Degree: Germanics ©Copyright 2018 Nathan Jensen Bates University of Washington Abstract Mind-Crafting: Anticipatory Critique of Transhumanist Mind-Uploading in German High Modernist Novels Nathan Jensen Bates Chair of the Supervisory Committee: Professor Richard Block Germanics This dissertation explores the question of how German modernist novels anticipate and critique the transhumanist theory of mind-uploading in an attempt to avert binary thinking. German modernist novels simulate the mind and expose the indistinct limits of that simulation. Simulation is understood in this study as defined by Jean Baudrillard in Simulacra and Simulation. The novels discussed in this work include Thomas Mann’s Der Zauberberg; Hermann Broch’s Die Schlafwandler; Alfred Döblin’s Berlin Alexanderplatz: Die Geschichte von Franz Biberkopf; and, in the conclusion, Irmgard Keun’s Das Kunstseidene Mädchen is offered as a field of future inquiry. These primary sources disclose at least three aspects of the mind that are resistant to discrete articulation; that is, the uploading or extraction of the mind into a foreign context. A fourth is proposed, but only provisionally, in the conclusion of this work. The aspects resistant to uploading are defined and discussed as situatedness, plurality, and adaptability to ambiguity. Each of these aspects relates to one of the three steps of mind- uploading summarized in Nick Bostrom’s treatment of the subject. -
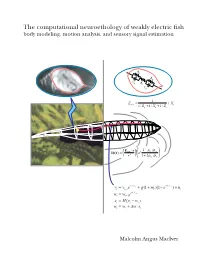
M.A. Maciver's Dissertation
The computational neuroethology of weakly electric fish body modeling, motion analysis, and sensory signal estimation R s R s C R s i C s 1 Z = + X prey + + s 1/ Rp 1/ Xp 1/ Zs −ρ ρ E ⋅r 1 p / w δφ(r) = fish a3 3 + ρ ρ r 1 2 p / w − t − t = 1/ v + + − 1/ v + vt vt−1e g(1 mt )(1 e ) nt − t = 1/ w wt wt−1e = − st H(vt wt ) = + ∆ ⋅ wt wt w st Malcolm Angus MacIver THE COMPUTATIONAL NEUROETHOLOGY OF WEAKLY ELECTRIC FISH: BODY MODELING, MOTION ANALYSIS, AND SENSORY SIGNAL ESTIMATION BY MALCOLM ANGUS MACIVER B.Sc., University of Toronto, 1991 M.A., University of Toronto, 1992 THESIS Submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Neuroscience in the Graduate College of the University of Illinois at Urbana-Champaign, 2001 Urbana, Illinois c Copyright by Malcolm Angus MacIver, 2001 ABSTRACT Animals actively influence the content and quality of sensory information they acquire through the positioning of peripheral sensory surfaces. Investigation of how the body and brain work together for sensory acquisition is hindered by 1) the limited number of techniques for tracking sensory surfaces, few of which provide data on the position of the entire body surface, and by 2) our inability to measure the thousands of sensory afferents stimulated during behav- ior. I present research on sensory acquisition in weakly electric fish of the genus Apteronotus, where I overcame the first barrier by developing a markerless tracking system and have de- ployed a computational approach toward overcoming the second barrier. -

Copyrighted Material
Index affordances 241–2 apps 11, 27–33, 244–5 afterlife 194, 227, 261 Ariely, Dan 28 Agar, Nicholas 15, 162, 313 Aristotle 154, 255 Age of Spiritual Machines, The 47, 54 Arkin, Ronald 64 AGI (Artificial General Intelligence) Armstrong, Stuart 12, 311 61–86, 98–9, 245, 266–7, Arp, Hans/Jean 240–2, 246 298, 311 artificial realities, see virtual reality AGI Nanny 84, 311 Asimov, Isaac 45, 268, 274 aging 61, 207, 222, 225, 259, 315 avatars 73, 76, 201, 244–5, 248–9 AI (artificial intelligence) 3, 9, 12, 22, 30, 35–6, 38–44, 46–58, 72, 91, Banks, Iain M. 235 95, 99, 102, 114–15, 119, 146–7, Barabási, Albert-László 311 150, 153, 157, 198, 284, 305, Barrat, James 22 311, 315 Berger, T.W. 92 non-determinism problem 95–7 Bernal,J.D.264–5 predictions of 46–58, 311 biological naturalism 124–5, 128, 312 altruism 8 biological theories of consciousness 14, Amazon Elastic Compute Cloud 40–1 104–5, 121–6, 194, 312 Andreadis, Athena 223 Blackford, Russell 16–21, 318 androids 44, 131, 194, 197, 235, 244, Blade Runner 21 265, 268–70, 272–5, 315 Block, Ned 117, 265 animal experimentationCOPYRIGHTED 24, 279–81, Blue Brain MATERIAL Project 2, 180, 194, 196 286–8, 292 Bodington, James 16, 316 animal rights 281–2, 285–8, 316 body, attitudes to 4–5, 222–9, 314–15 Anissimov, Michael 12, 311 “Body by Design” 244, 246 Intelligence Unbound: The Future of Uploaded and Machine Minds, First Edition. Edited by Russell Blackford and Damien Broderick. -

William Gibson's Neuromancer and Its Relevanceto Culture And
“KALAM” International Journal of Faculty of Arts and Culture, South Eastern University of Sri Lanka William Gibson’s Neuromancer and Its Relevanceto Culture and Technology Noeline Shirome .G South Eastern University of Sri Lanka Abstract We live in a time where technology is in a rapid growth. These advancements have made various changes in the cultural sphere. Computers have drastically started to influence the lifestyle of people through various systems of information technology. Thus, within a fragment of time anyone can access to any sort of resources on the planet. This advancement is in way shrinking the division of mind and machine as most people depend vastly on the outside sources of intelligence through technological devices. The concept of mind uploading, trans-humans, cyber space, virtual reality, and etc. have interested the cyberpunk writers and influenced them to project these ideas in their literary texts. Thus the present paper explores the relationship between William Gibson’s cyberpunk science fiction Neuromancer and its relevance to culture and technology. It first focuses on the novel Neuromancer, and then goes onto its cultural and technological relevance with present time, and discusses the close connection between reality and cyberpunk literature. Key words Cyberpunk, cyber space, mind uploading, mindclones, mindfile, William Gibson Introduction in the novel named Henry Dorsett Case is a The link between computer technology and hacker who eventually gets into the digitalised literature play an important role in society, as system and logs into the Matrix where the literary texts reflects the contemporary copy of his consciousness exists forever. The situation. In this context, cyberpunk science similar idea of this mind uploading is now an fictions play an important role in exploring emerging concept in the twenty-first century. -

Brain Uploading-Related Group Mind Scenarios
MIRI MACHINE INTELLIGENCE RESEARCH INSTITUTE Coalescing Minds: Brain Uploading-Related Group Mind Scenarios Kaj Sotala University of Helsinki, MIRI Research Associate Harri Valpola Aalto University Abstract We present a hypothetical process of mind coalescence, where artificial connections are created between two or more brains. This might simply allow for an improved formof communication. At the other extreme, it might merge the minds into one in a process that can be thought of as a reverse split-brain operation. We propose that one way mind coalescence might happen is via an exocortex, a prosthetic extension of the biological brain which integrates with the brain as seamlessly as parts of the biological brain in- tegrate with each other. An exocortex may also prove to be the easiest route for mind uploading, as a person’s personality gradually moves away from the aging biological brain and onto the exocortex. Memories might also be copied and shared even without minds being permanently merged. Over time, the borders of personal identity may become loose or even unnecessary. Sotala, Kaj, and Harri Valpola. 2012. “Coalescing Minds: Brain Uploading-Related Group Mind Scenarios.” International Journal of Machine Consciousness 4 (1): 293–312. doi:10.1142/S1793843012400173. This version contains minor changes. Kaj Sotala, Harri Valpola 1. Introduction Mind uploads, or “uploads” for short (also known as brain uploads, whole brain emu- lations, emulations or ems) are hypothetical human minds that have been moved into a digital format and run as software programs on computers. One recent roadmap chart- ing the technological requirements for creating uploads suggests that they may be fea- sible by mid-century (Sandberg and Bostrom 2008). -

Everybody and Nobody: Visions of Individualism and Collectivity in the Age of AI
International Journal of Communication 10(2016), Forum 5669–5683 1932–8036/2016FRM0002 Everybody and Nobody: Visions of Individualism and Collectivity in the Age of AI ARAM SINNREICH (provocateur) American University, USA JESSA LINGEL University of Pennsylvania, USA GIDEON LICHFIELD Quartz, USA ADAM RICHARD ROTTINGHAUS University of Tampa, USA LONNY J AVI BROOKS California State University, East Bay, USA In Homer’s The Odyssey (one of humanity’s earliest surviving works of speculative fiction), the story’s hero, Odysseus, pulls off one of literature’s great escapes. Trapped in a cave by the giant, man- eating cyclops Polyphemus, the wily Greek lulls the monster to sleep with divinely powerful wine, then pokes out his only eye with a flaming wooden stake. Right before Polyphemus passes out, Odysseus prepares an insult to go along with the injury: when the Cyclops asks his name, he responds by claiming it’s “Nobody.” Thus, when the blinded Polyphemus seeks help from his fellow monsters and retribution from his divine father, the sea god Poseidon, all the poor creature can tell them is that “Nobody’s killing me” and “Nobody made me suffer” (Fagles, 1996). The plan works, and Odysseus escapes with his remaining men to their ship, as the blind cyclops, relying on his ears instead of his eyes, heaves boulders in their direction. This is when the hero commits his greatest error: Despite his men’s entreaties, he begins to taunt the cyclops, reveling in his victory by revealing his true identity: Cyclops— if any man on the face of the earth should ask you who blinded you, shamed you so—say Odysseus, raider of cities, he gouged out your eye, Laertes’ son who makes his home in Ithaca! (Fagles, 1996, p. -

Humanity's Capability of Transcendence Through Artificial
California State University, Monterey Bay Digital Commons @ CSUMB Capstone Projects and Master's Theses Spring 5-2016 Humanity’s Capability of Transcendence through Artificial Intelligence Zena McCartney California State University, Monterey Bay Follow this and additional works at: https://digitalcommons.csumb.edu/caps_thes Part of the Philosophy Commons Recommended Citation McCartney, Zena, "Humanity’s Capability of Transcendence through Artificial Intelligence" (2016). Capstone Projects and Master's Theses. 529. https://digitalcommons.csumb.edu/caps_thes/529 This Capstone Project is brought to you for free and open access by Digital Commons @ CSUMB. It has been accepted for inclusion in Capstone Projects and Master's Theses by an authorized administrator of Digital Commons @ CSUMB. Unless otherwise indicated, this project was conducted as practicum not subject to IRB review but conducted in keeping with applicable regulatory guidance for training purposes. For more information, please contact [email protected]. Humanity’s Capability of Transcendence through Artificial Intelligence What does it mean to be a human in a technological society? Source: Cazy89. Artificial Intelligence. Cruz, Alejandro. Flickr Commons. WikiMedia Project. Web. 28 December 2008. Digital Image. Senior Capstone Practical and Professional Ethics Research Essay David Reichard Division of Humanities and Communication Spring 2016 0 TABLE OF CONTENTS ACKNOWLEDGEMENTS .............................................................................................................2 -

Science Fiction in a Reality Check» Evening?
HOW CAN I PLAN A «SCIENCE FICTION IN A REALITY CHECK» EVENING? DO YOU WANT TO PLAN AN EVENING IN WHICH YOU PUT SCI- ENCE FICTION FANTASY TO THE TEST? HOW REALISTIC IS A PHASER, TELEPORTATION OR THE HOLODECK? YOU CAN FIND OUT MORE ABOUT HOW TO ORGANIZE SUCH AN EVENING HERE: Science fiction films often contain technologies that rely on visions stemming directly from real-life technology. Whether it is Jules Verne, Isaac Asimov or Georges Lucas — every one of them uses science as a source for their technologies of the future. That is how stories about nuclear submarines, swarm robots or prosthetic bodies come about. These films shed light on the boundaries of the ethically defensible and often show possible negative consequences of technologies — but they also excessively raise hope for what will be possible in the future. In this format, the goal is to talk about the reality of such visions and about what we as a society desire in terms of progress. The ’reality check’ format is particularly suitable for high school students. It gives researchers the opportunity to comment on these films and to discuss them with young people who have a whole lot of future ahead of them. 01 1. FIND A FILM AND A RESEARCHER! Find a film that addresses a topic that is particularly interesting for students. Ask yourself: Which technological question is behind the film? Does technology play a significant role in the selected film such that it would be worth having a discussi- on about it afterwards? Form a “what if ” questions that the film poses regarding technology. -

A History of Laser Scanning, Part 2: the Later Phase of Industrial and Heritage Applications
A History of Laser Scanning, Part 2: The Later Phase of Industrial and Heritage Applications Adam P. Spring Abstract point clouds of 3D information thus generated (Takase et al. The second part of this article examines the transition of 2003). Software packages can be proprietary in nature—such as midrange terrestrial laser scanning (TLS)–from applied Leica Geosystems’ Cyclone, Riegl’s RiScan, Trimble’s Real- research to applied markets. It looks at the crossover of Works, Zoller + Fröhlich’s LaserControl, and Autodesk’s ReCap technologies; their connection to broader developments in (“Leica Cyclone” 2020; “ReCap” n.d.; “RiScan Pro 2.0” n.d.; computing and microelectronics; and changes made based “Trimble RealWorks” n.d.; “Z+F LaserControl” n.d.)—or open on application. The shift from initial uses in on-board guid- source, like CloudCompare (Girardeau-Montaut n.d.). There are ance systems and terrain mapping to tripod-based survey for even plug-ins for preexisting computer-aided design (CAD) soft- as-built documentation is a main focus. Origins of terms like ware packages. For example, CloudWorx enables AutoCAD users digital twin are identified and, for the first time, the earliest to work with point-cloud information (“Leica CloudWorx” examples of cultural heritage (CH) based midrange TLS scans 2020; “Leica Cyclone” 2020). Like many services and solutions, are shown and explained. Part two of this history of laser AutoCAD predates the incorporation of 3D point clouds into scanning is a comprehensive analysis upto the year 2020. design-based workflows (Clayton 2005). Enabling the user base of pre-existing software to work with point-cloud data in this way–in packages they are already educated in–is a gateway to Introduction increased adoption of midrange TLS. -

Posthuman Cyberware
POSTHUMAN CYBERWARE: The idea of an implantable memory chip that lets you instantly Blurring the Boundaries of Mind, download new skills sounds great, but could such a device actually Body, and Computer work? Given the different formats that their brains use for storing semantic content, would you need, say, one version of the implant for English speakers and another for Japanese speakers? And which Volume 01 in the of your cognitive functions could a hacker access by compromising Posthuman Cyberware Sourcebook series such a device? Could a human mind figure out how to operate a cy- borg body that has wheels or dozens of robotic tentacles? If relatively small changes in brain temperature can cause behavioral impacts (or Written and edited by: Matthew E. Gladden even brain damage), is it really advisable to implant a heat-spewing miniaturized supercomputer in someone’s cranium? If you’ve ever Special thanks to thought about any of these questions when designing or running an All those who offered feedback regarding the research and ma- adventure, then this is the book – and series – for you. terials that eventually found their way into this volume, as well There are many remarkable and pioneering games (like Cyber- as those whose work as game designers, gamers, scholars, and punk 2020, Shadowrun, Cyberspace, GURPS Cyberpunk, Kazei-5, Trans- authors provided inspiration for this project, including: human Space, Ex Machina, Eclipse Phase, and Interface Zero 2.0) that in- Magdalena Szczepocka Sven Dwulecki corporate futuristic neuroprosthetic hardware and cybernetic aug- mentation as significant elements of their game-worlds, character Bartosz Kłoda-Staniecko Mateusz Zimnoch design, and adventure plots.