Codemashschedule 2020
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Working with Unreliable Observers Using Reactive Extensions
Master thesis WORKING WITH UNRELIABLE OBSERVERS USING REACTIVE EXTENSIONS November 10, 2016 Dorus Peelen (s4167821) Computing science Radboud University [email protected] — Supervisors: Radboud University: Rinus Plasmeijer Aia Software: Jeroen ter Hofstede Contents 1 Introduction 5 1.1 Overview of thesis . .7 2 Background 8 2.1 Aia Software . .8 2.2 Current situation . .8 2.3 The use case . .9 2.3.1 Technical details . 10 2.3.2 Potential problems . 11 2.4 Problem description . 11 2.5 Desired Properties of the new system . 11 3 Overview of Rx 13 3.1 Basic Ideas of Rx . 13 3.2 Observer and Observable . 15 3.3 Hot vs Cold observables . 15 3.4 Marble diagrams . 16 3.5 Transformations on Event Streams . 16 3.6 Schedulers . 16 3.7 Control process in Rx . 17 3.8 Interactive vs reactive . 18 3.9 Push-back and backpressure . 18 3.10 Operators with unbounded Queue . 19 3.11 Explanation and example of different operators in Rx . 19 3.11.1 Select .................................. 19 3.11.2 SelectMany ............................... 20 3.11.3 Where .................................. 20 3.11.4 Delay .................................. 20 3.11.5 Merge and Concat ........................... 21 3.11.6 Buffer and Window ........................... 21 3.11.7 GroupBy ................................. 21 3.11.8 Amb .................................... 21 3.11.9 Debounce, Sample and Throttle ................... 22 3.11.10 ObserveOn ................................ 22 3.12 Related work . 22 3.12.1 TPL . 23 3.12.2 iTasks . 23 4 The experiment 25 4.1 Important properties . 25 4.2 Test architecture . 26 4.2.1 Design . 26 2 4.2.2 Concepts . -
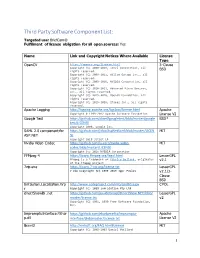
Third Party Software Component List: Targeted Use: Briefcam® Fulfillment of License Obligation for All Open Sources: Yes
Third Party Software Component List: Targeted use: BriefCam® Fulfillment of license obligation for all open sources: Yes Name Link and Copyright Notices Where Available License Type OpenCV https://opencv.org/license.html 3-Clause Copyright (C) 2000-2019, Intel Corporation, all BSD rights reserved. Copyright (C) 2009-2011, Willow Garage Inc., all rights reserved. Copyright (C) 2009-2016, NVIDIA Corporation, all rights reserved. Copyright (C) 2010-2013, Advanced Micro Devices, Inc., all rights reserved. Copyright (C) 2015-2016, OpenCV Foundation, all rights reserved. Copyright (C) 2015-2016, Itseez Inc., all rights reserved. Apache Logging http://logging.apache.org/log4cxx/license.html Apache Copyright © 1999-2012 Apache Software Foundation License V2 Google Test https://github.com/abseil/googletest/blob/master/google BSD* test/LICENSE Copyright 2008, Google Inc. SAML 2.0 component for https://github.com/jitbit/AspNetSaml/blob/master/LICEN MIT ASP.NET SE Copyright 2018 Jitbit LP Nvidia Video Codec https://github.com/lu-zero/nvidia-video- MIT codec/blob/master/LICENSE Copyright (c) 2016 NVIDIA Corporation FFMpeg 4 https://www.ffmpeg.org/legal.html LesserGPL FFmpeg is a trademark of Fabrice Bellard, originator v2.1 of the FFmpeg project 7zip.exe https://www.7-zip.org/license.txt LesserGPL 7-Zip Copyright (C) 1999-2019 Igor Pavlov v2.1/3- Clause BSD Infralution.Localization.Wp http://www.codeproject.com/info/cpol10.aspx CPOL f Copyright (C) 2018 Infralution Pty Ltd directShowlib .net https://github.com/pauldotknopf/DirectShow.NET/blob/ LesserGPL -

An Opinionated Guide to Technology Frontiers
TECHNOLOGY RADAR An opinionated guide to technology frontiers Volume 24 #TWTechRadar thoughtworks.com/radar The Technology Advisory Board (TAB) is a group of 20 senior technologists at Thoughtworks. The TAB meets twice a year face-to-face and biweekly by phone. Its primary role is to be an advisory group for Thoughtworks CTO, Contributors Rebecca Parsons. The Technology Radar is prepared by the The TAB acts as a broad body that can look at topics that affect technology and technologists at Thoughtworks. With the ongoing global pandemic, we Thoughtworks Technology Advisory Board once again created this volume of the Technology Radar via a virtual event. Rebecca Martin Fowler Bharani Birgitta Brandon Camilla Cassie Parsons (CTO) (Chief Scientist) Subramaniam Böckeler Byars Crispim Shum Erik Evan Fausto Hao Ian James Lakshminarasimhan Dörnenburg Bottcher de la Torre Xu Cartwright Lewis Sudarshan Mike Neal Perla Rachel Scott Shangqi Zhamak Mason Ford Villarreal Laycock Shaw Liu Dehghani TECHNOLOGY RADAR | 2 © Thoughtworks, Inc. All Rights Reserved. About the Radar Thoughtworkers are passionate about technology. We build it, research it, test it, open source it, write about it and constantly aim to improve it — for everyone. Our mission is to champion software excellence and revolutionize IT. We create and share the Thoughtworks Technology Radar in support of that mission. The Thoughtworks Technology Advisory Board, a group of senior technology leaders at Thoughtworks, creates the Radar. They meet regularly to discuss the global technology strategy for Thoughtworks and the technology trends that significantly impact our industry. The Radar captures the output of the Technology Advisory Board’s discussions in a format that provides value to a wide range of stakeholders, from developers to CTOs. -

Front-End Development with ASP.NET Core, Angular, And
Table of Contents COVER TITLE PAGE FOREWORD INTRODUCTION WHY WEB DEVELOPMENT REQUIRES POLYGLOT DEVELOPERS WHO THIS BOOK IS FOR WHAT THIS BOOK COVERS HOW THIS BOOK IS STRUCTURED WHAT YOU NEED TO USE THIS BOOK CONVENTIONS SOURCE CODE ERRATA 1 What’s New in ASP.NET Core MVC GETTING THE NAMES RIGHT A BRIEF HISTORY OF THE MICROSOFT .NET WEB STACK .NET CORE INTRODUCING ASP.NET CORE NEW FUNDAMENTAL FEATURES OF ASP.NET CORE AN OVERVIEW OF SOME ASP.NET CORE MIDDLEWARE ASP.NET CORE MVC SUMMARY 2 The Front‐End Developer Toolset ADDITIONAL LANGUAGES YOU HAVE TO KNOW JAVASCRIPT FRAMEWORKS CSS FRAMEWORKS PACKAGE MANAGERS TASK RUNNERS SUMMARY 3 Angular in a Nutshell ANGULAR CONCEPTS THE LANGUAGE OF ANGULAR SETTING UP AN ANGULAR PROJECT THE STRUCTURE OF AN ANGULAR APP DATA BINDING DIRECTIVES SERVICES AND DEPENDECY INJECTION MULTIPLE COMPONENTS INPUT AND OUTPUT PROPERTIES TALKING TO THE BACK END USING ANGULAR WITH ASP.NET MVC VISUAL STUDIO 2017 SUPPORT FOR ANGULAR SUMMARY 4 Bootstrap in a Nutshell INTRODUCTION TO BOOTSTRAP BOOTSTRAP STYLES COMPONENTS JAVASCRIPT CUSTOMIZING BOOTSTRAP WITH LESS BOOTSTRAP SUPPORT IN VISUAL STUDIO 2017 AND ASP.NET CORE SUMMARY 5 Managing Dependencies with NuGet and Bower GENERAL CONCEPTS NUGET NPM (NODE.JS PACKAGE MANAGER) BOWER SUMMARY 6 Building Your Application with Gulp and webpack WHAT FRONT‐END BUILD SYSTEMS ARE FOR A DEEPER LOOK AT GULP INTRODUCTION TO WEBPACK VISUAL STUDIO 2017 AND BUILD SYSTEMS SUMMARY 7 Deploying ASP.NET Core THE NEW HOSTING MODEL OF ASP.NET CORE INSTALLING ON INTERNET INFORMATION SERVICES ON PREMISE -

Efficient Algorithms for Comparing, Storing, and Sharing
EFFICIENT ALGORITHMS FOR COMPARING, STORING, AND SHARING LARGE COLLECTIONS OF EVOLUTIONARY TREES A Dissertation by SUZANNE JUDE MATTHEWS Submitted to the Office of Graduate Studies of Texas A&M University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY May 2012 Major Subject: Computer Science EFFICIENT ALGORITHMS FOR COMPARING, STORING, AND SHARING LARGE COLLECTIONS OF EVOLUTIONARY TREES A Dissertation by SUZANNE JUDE MATTHEWS Submitted to the Office of Graduate Studies of Texas A&M University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY Approved by: Chair of Committee, Tiffani L. Williams Committee Members, Nancy M. Amato Jennifer L. Welch James B. Woolley Head of Department, Hank W. Walker May 2012 Major Subject: Computer Science iii ABSTRACT Efficient Algorithms for Comparing, Storing, and Sharing Large Collections of Evolutionary Trees. (May 2012) Suzanne Jude Matthews, B.S.; M.S., Rensselaer Polytechnic Institute Chair of Advisory Committee: Dr. Tiffani L. Williams Evolutionary relationships between a group of organisms are commonly summarized in a phylogenetic (or evolutionary) tree. The goal of phylogenetic inference is to infer the best tree structure that represents the relationships between a group of organisms, given a set of observations (e.g. molecular sequences). However, popular heuristics for inferring phylogenies output tens to hundreds of thousands of equally weighted candidate trees. Biologists summarize these trees into a single structure called the consensus tree. The central assumption is that the information discarded has less value than the information retained. But, what if this assumption is not true? In this dissertation, we demonstrate the value of retaining and studying tree collections. -

Rxada: an Ada Implementation of the Reactivex API - 1 PREVIOUSLY, in ADA-EUROPE 2007
RxAda: An Ada implementation of the ReactiveX API Alejandro R. Mosteo 2017-jun-13 2017-jun-13 - RxAda: An Ada implementation of the ReactiveX API - 1 PREVIOUSLY, IN ADA-EUROPE 2007... SANCTA: An Ada 2005 General-Purpose Architecture for Mobile Robotics Research 2017-jun-13 - RxAda: An Ada implementation of the ReactiveX API - 2 ABOUT ME Robotics, Perception, and Real-Time group (RoPeRT) http://robots.unizar.es/ Universidad de Zaragoza, Spain 2017-jun-13 - RxAda: An Ada implementation of the ReactiveX API - 3 CONTENTS • Motivation • What is ReactiveX – Language agnostic – Java – Ada • RxAda – Design challenges/decisions – Current implementation status – Future steps 2017-jun-13 - RxAda: An Ada implementation of the ReactiveX API - 4 PERSONAL MOTIVATION • Android development – Questionable design decisions for background tasks that interact with the GUI • Found RxJava – Simpler, saner way of doing multitasking – Documented comprehensively – Very active community in the Rx world • Achievable in Ada? – Aiming for the RxJava simplicity of use 2017-jun-13 - RxAda: An Ada implementation of the ReactiveX API - 5 EVENT-DRIVEN / ASYNCHRONOUS SYSTEMS <User drags map> ↓ Find nearby items ↓⌛ Request images ↓⌛↓⌛↓⌛↓⌛ Crop/Process image ↓⌛ Update GUI markers 2017-jun-13 - RxAda: An Ada implementation of the ReactiveX API - 6 OVERVIEW Event-driven systems ↓ Reactive Programming (philosophy) ↓ ReactiveX / Rx (specification) ↓ Rx.Net, RxJava, RxJS, RxC++, … ↓ RxAda 2017-jun-13 - RxAda: An Ada implementation of the ReactiveX API - 7 REACTIVE MANIFESTO (2014-sep-16 -

Higher Inductive Types (Hits) Are a New Type Former!
Git as a HIT Dan Licata Wesleyan University 1 1 Darcs Git as a HIT Dan Licata Wesleyan University 1 1 HITs 2 Generator for 2 equality of equality HITs Homotopy Type Theory is an extension of Agda/Coq based on connections with homotopy theory [Hofmann&Streicher,Awodey&Warren,Voevodsky,Lumsdaine,Garner&van den Berg] 2 Generator for 2 equality of equality HITs Homotopy Type Theory is an extension of Agda/Coq based on connections with homotopy theory [Hofmann&Streicher,Awodey&Warren,Voevodsky,Lumsdaine,Garner&van den Berg] Higher inductive types (HITs) are a new type former! 2 Generator for 2 equality of equality HITs Homotopy Type Theory is an extension of Agda/Coq based on connections with homotopy theory [Hofmann&Streicher,Awodey&Warren,Voevodsky,Lumsdaine,Garner&van den Berg] Higher inductive types (HITs) are a new type former! They were originally invented[Lumsdaine,Shulman,…] to model basic spaces (circle, spheres, the torus, …) and constructions in homotopy theory 2 Generator for 2 equality of equality HITs Homotopy Type Theory is an extension of Agda/Coq based on connections with homotopy theory [Hofmann&Streicher,Awodey&Warren,Voevodsky,Lumsdaine,Garner&van den Berg] Higher inductive types (HITs) are a new type former! They were originally invented[Lumsdaine,Shulman,…] to model basic spaces (circle, spheres, the torus, …) and constructions in homotopy theory But they have many other applications, including some programming ones! 2 Generator for 2 equality of equality Patches Patch a a 2c2 diff b d = < b c c --- > d 3 3 id a a b b -

DVCS Or a New Way to Use Version Control Systems for Freebsd
Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions DVCS or a new way to use Version Control Systems for FreeBSD Ollivier ROBERT <[email protected]> BSDCan 2006 Ottawa, Canada May, 12-13th, 2006 Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions Agenda 1 Brief history of VCS 2 FreeBSD context & gures 3 Is Arch/baz suited for FreeBSD? 4 Mercurial to the rescue 5 New processes & policies needed 6 Conclusions Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions The ancestors: SCCS, RCS File-oriented Use a subdirectory to store deltas and metadata Use lock-based architecture Support shared developments through NFS (fragile) SCCS is proprietary (System V), RCS is Open Source a SCCS clone exists: CSSC You can have a central repository with symlinks (RCS) Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions CVS, the de facto VCS for the free world Initially written as shell wrappers over RCS then rewritten in C Centralised server Easy UI Use sandboxes to avoid locking Simple 3-way merges Can be replicated through CVSup or even rsync Extensive documentation (papers, websites, books) Free software and used everywhere (SourceForge for example) Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions CVS annoyances and aws BUT.. -

Coverity Static Analysis
Coverity Static Analysis Quickly find and fix Overview critical security and Coverity® gives you the speed, ease of use, accuracy, industry standards compliance, and quality issues as you scalability that you need to develop high-quality, secure applications. Coverity identifies code critical software quality defects and security vulnerabilities in code as it’s written, early in the development process when it’s least costly and easiest to fix. Precise actionable remediation advice and context-specific eLearning help your developers understand how to fix their prioritized issues quickly, without having to become security experts. Coverity Benefits seamlessly integrates automated security testing into your CI/CD pipelines and supports your existing development tools and workflows. Choose where and how to do your • Get improved visibility into development: on-premises or in the cloud with the Polaris Software Integrity Platform™ security risk. Cross-product (SaaS), a highly scalable, cloud-based application security platform. Coverity supports 22 reporting provides a holistic, more languages and over 70 frameworks and templates. complete view of a project’s risk using best-in-class AppSec tools. Coverity includes Rapid Scan, a fast, lightweight static analysis engine optimized • Deployment flexibility. You for cloud-native applications and Infrastructure-as-Code (IaC). Rapid Scan runs decide which set of projects to do automatically, without additional configuration, with every Coverity scan and can also AppSec testing for: on-premises be run as part of full CI builds with conventional scan completion times. Rapid Scan can or in the cloud. also be deployed as a standalone scan engine in Code Sight™ or via the command line • Shift security testing left. -

Santiago Quintero Pabón –
LIX - École Polytechnique Palaiseau Santiago Quintero France Æ +33 (0) 7 67 39 73 30 Pabón Q [email protected] Contact Information Last Name: Quintero Pabón Given Name: Santiago Birth Date: 21-oct-1994 Nationality: Colombian Education Pontificia Universidad Javeriana Cali, CO + Five years B.Sc. Degree in Computer Science and Engineering, (equivalent to a master degree) 2012-2017 École Polytechnique Palaiseau, FR + PhD in Computer Sciences, Thesis: "Foundational approach to computation in today’s systems" 2018-Current Supervisors: Catuscia Palamidessi, Frank Valencia. Work Experience COMETE at LIX, École Polytechnique Palaiseau, FR + PhD Student 2018-Current AVISPA research group at Pontificia Universidad Javeriana Cali, CO + Research Assistant 2018 PORTAL ACTUALICESE.COM S.A.S. Cali, CO + Development Analyst 2017-2018 COMETE research group at Inria-Saclay Palaiseau, FR + Research Intern November 2017 Pontificia Universidad Javeriana Cali, CO + Teaching Assistant 2014-2016 Teaching Assistant....................................................................................................... Courses: Introduction to Programming, Programming Fundamentals and Structures, Logic in Computer Science, Computability and Formal Languages, Introduction to Systems Modeling. Major Projects............................................................................................................. + October 2015 - June 2016: ’Financial inclusion for the emerging middle class in Colombia’ Designed, prototyped and developed a financial -

Darcs 2.0.0 (2.0.0 (+ 75 Patches)) Darcs
Darcs 2.0.0 (2.0.0 (+ 75 patches)) Darcs David Roundy April 23, 2008 2 Contents 1 Introduction 7 1.1 Features . 9 1.2 Switching from CVS . 11 1.3 Switching from arch . 12 2 Building darcs 15 2.1 Prerequisites . 15 2.2 Building on Mac OS X . 16 2.3 Building on Microsoft Windows . 16 2.4 Building from tarball . 16 2.5 Building darcs from the repository . 17 2.6 Building darcs with git . 18 2.7 Submitting patches to darcs . 18 3 Getting started 19 3.1 Creating your repository . 19 3.2 Making changes . 20 3.3 Making your repository visible to others . 20 3.4 Getting changes made to another repository . 21 3.5 Moving patches from one repository to another . 21 3.5.1 All pulls . 21 3.5.2 Send and apply manually . 21 3.5.3 Push . 22 3.5.4 Push —apply-as . 22 3.5.5 Sending signed patches by email . 23 3.6 Reducing disk space usage . 26 3.6.1 Linking between repositories . 26 3.6.2 Alternate formats for the pristine tree . 26 4 Configuring darcs 29 4.1 prefs . 29 4.2 Environment variables . 32 4.3 General-purpose variables . 33 4.4 Remote repositories . 34 3 4 CONTENTS 4.5 Highlighted output . 36 4.6 Character escaping and non-ASCII character encodings . 36 5 Best practices 39 5.1 Introduction . 39 5.2 Creating patches . 39 5.2.1 Changes . 40 5.2.2 Keeping or discarding changes . 40 5.2.3 Unrecording changes . -

Rxpy Documentation Release 3.1.1
RxPY Documentation Release 3.1.1 Dag Brattli Jul 16, 2020 CONTENTS 1 Installation 3 2 Rationale 5 3 Get Started 7 3.1 Operators and Chaining.........................................8 3.2 Custom operator.............................................9 3.3 Concurrency............................................... 10 4 Migration 15 4.1 Pipe Based Operator Chaining...................................... 15 4.2 Removal Of The Result Mapper..................................... 16 4.3 Scheduler Parameter In Create Operator................................. 16 4.4 Removal Of List Of Observables.................................... 17 4.5 Blocking Observable........................................... 17 4.6 Back-Pressure.............................................. 18 4.7 Time Is In Seconds............................................ 18 4.8 Packages Renamed............................................ 18 5 Operators 19 5.1 Creating Observables........................................... 19 5.2 Transforming Observables........................................ 19 5.3 Filtering Observables........................................... 20 5.4 Combining Observables......................................... 20 5.5 Error Handling.............................................. 20 5.6 Utility Operators............................................. 21 5.7 Conditional and Boolean Operators................................... 21 5.8 Mathematical and Aggregate Operators................................. 21 5.9 Connectable Observable Operators..................................