Brigade and Battalion Intelligence and Electronic Warfare Operations
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Erosion of Strategic Stability and the Future of Arms Control in Europe
Études de l’Ifri Proliferation Papers 60 THE EROSION OF STRATEGIC STABILITY AND THE FUTURE OF ARMS COntrOL IN EUROPE Corentin BRUSTLEIN November 2018 Security Studies Center The Institut français des relations internationales (Ifri) is a research center and a forum for debate on major international political and economic issues. Headed by Thierry de Montbrial since its founding in 1979, Ifri is a non- governmental, non-profit organization. As an independent think tank, Ifri sets its own research agenda, publishing its findings regularly for a global audience. Taking an interdisciplinary approach, Ifri brings together political and economic decision-makers, researchers and internationally renowned experts to animate its debate and research activities. The opinions expressed in this text are the responsibility of the author alone. ISBN: 978-2-36567-932-9 © All rights reserved, Ifri, 2018 How to quote this document: Corentin Brustlein, “The Erosion of Strategic Stability and the Future of Arms Control in Europe”, Proliferation Papers, No. 60, November 2018. Ifri 27 rue de la Procession 75740 Paris Cedex 15 – FRANCE Tel.: +33 (0)1 40 61 60 00 – Fax: +33 (0)1 40 61 60 60 Email: [email protected] Website: Ifri.org Author Dr. Corentin Brustlein is the Director of the Security Studies Center at the French Institute of International Relations. His work focuses on nuclear and conventional deterrence, arms control, military balances, and U.S. and French defense policies. Before assuming his current position, he had been a research fellow at Ifri since 2008 and the head of Ifri’s Deterrence and Proliferation Program since 2010. -
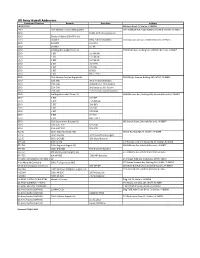
US Army Hawaii Addresses Command/Division Brigade Battalion Address 18 MEDCOM 160 Loop Road, Ft
US Army Hawaii Addresses Command/Division Brigade Battalion Address 18 MEDCOM 160 Loop Road, Ft. Shafter, HI 96858 25 ID 25th Infantry Division Headquarters 2091 Kolekole Ave, Building 3004, Schofield Barracks, HI 96857 25 ID (HQ) HHBN, 25th Infantry Division 25 ID Division Artillery (DIVARTY) HQ 25 ID DIVARTY HHB, 25th Field Artillery 1078 Waianae Avenue, Schofield Barracks, HI 96857 25 ID DIVARTY 2-11 FAR 25 ID DIVARTY 3-7 FA 25 ID 2nd Brigade Combat Team HQ 1578 Foote Ave, Building 500, Schofield Barracks, HI 96857 25 ID 2 BCT 1-14 IN BN 25 ID 2 BCT 1-21 IN BN 25 ID 2 BCT 1-27 IN BN 25 ID 2 BCT 2-14 CAV 25 ID 2 BCT 225 BSB 25 ID 2 BCT 65 BEB 25 ID 2 BCT HHC, 2 SBCT 25 ID 25th Combat Aviation Brigade HQ 1343 Wright Avenue, Building 100, WAAF, HI 96854 25 ID 25th CAB 209th Support Battalion 25 ID 25th CAB 2nd Battalion, 25th Aviation 25 ID 25th CAB 2ndRegiment Squadron, 6th Cavalry 25 ID 25th CAB 3-25Regiment General Support Aviation 25 ID 3rd Brigade Combat Team HQ Battalion 1640 Waianae Ave, Building 649, Schofield Barracks, HI 96857 25 ID 3 BCT 2-27 INF 25 ID 3 BCT 2-35 INF BN 25 ID 3 BCT 29th BEB 25 ID 3 BCT 325 BSB 25 ID 3 BCT 325 BSTB 25 ID 3 BCT 3-4 CAV 25 ID 3 BCT HHC, 3 BCT 25 ID 25th Sustainment Brigade HQ 181 Sutton Street, Schofield Barracks, HI 96857 25 ID 25th SUST BDE 524 CSSB 25 ID 25th SUST BDE 25th STB 311 SC 311th Signal Command HQ Wisser Rd, Bldg 520, Ft. -

MILITARY INTELLIGENCE PB 34-04-4 Volume 30 Number 4 October-December 2004 STAFF: FEATURES Commanding General Major General Barbara G
MILITARY INTELLIGENCE PB 34-04-4 Volume 30 Number 4 October-December 2004 STAFF: FEATURES Commanding General Major General Barbara G. Fast 8 Tactical Intelligence Shortcomings in Iraq: Restructuring Deputy Commanding General Battalion Intelligence to Win Brigadier General Brian A. Keller by Major Bill Benson and Captain Sean Nowlan Deputy Commandant for Futures Jerry V. Proctor Director of Training Development 16 Measuring Anti-U.S. Sentiment and Conducting Media and Support Analysis in The Republic of Korea (ROK) Colonel Eileen M. Ahearn by Major Daniel S. Burgess Deputy Director/Dean of Training Development and Support 24 Army’s MI School Faces TRADOC Accreditation Russell W. Watson, Ph.D. by John J. Craig Chief, Doctrine Division Stephen B. Leeder 25 USAIC&FH Observations, Insights, and Lessons Learned Managing Editor (OIL) Process Sterilla A. Smith by Dee K. Barnett, Command Sergeant Major (Retired) Editor Elizabeth A. McGovern 27 Brigade Combat Team (BCT) Intelligence Operations Design Director SSG Sharon K. Nieto by Michael A. Brake Associate Design Director and Administration 29 North Korean Special Operations Forces: 1996 Kangnung Specialist Angiene L. Myers Submarine Infiltration Cover Photographs: by Major Harry P. Dies, Jr. Courtesy of the U.S. Army Cover Design: 35 Deconstructing The Theory of 4th Generation Warfare Specialist Angiene L. Myers by Del Stewart, Chief Warrant Officer Three (Retired) Purpose: The U.S. Army Intelli- gence Center and Fort Huachuca (USAIC&FH) publishes the Military DEPARTMENTS Intelligence Professional Bulle- tin quarterly under provisions of AR 2 Always Out Front 58 Language Action 25-30. MIPB disseminates mate- rial designed to enhance individu- 3 CSM Forum 60 Professional Reader als’ knowledge of past, current, and emerging concepts, doctrine, materi- 4 Technical Perspective 62 MIPB 2004 Index al, training, and professional develop- ments in the MI Corps. -

Organization of the Roman Military 150 CE
Organization of the Roman Military 150 CE It was the strength and proficiency of the Roman army that held the empire together against internal revolts and threats from beyond the borders. The army was unique in the classical world: a professional standing army, with state-provided weapons and armor, salaried troops, and 30 or so legions (the main body of the army) permanently stationed at garrison towns along imperial frontiers. Legions were reinforced with auxiliary troops drawn from the local population. To support the army and protect merchant shipping from piracy, Rome maintained a large navy with fleets in the Mediterranean Sea, the Atlantic Ocean, and along the Rhine and Danube Rivers. LEGION UNITS Legion A body of about 5,000 foot soldiers, uniformly legionaries (160 in first cohort centuries). There were 6 trained and equipped—similar to a modern army division. centuries in the 2nd to 10th cohorts and 5 in the first A legion was the smallest formation in the Roman army cohort. capable of sustained independent operations. Cavalry A small force of about 120 mounted legionaries Cohort (10) The distinct tactical units of a legion, each attached to each legion for escort, messenger, and about 480 men strong—equivalent in size and function to reconnaissance duties. They were not usually seen on a modern infantry battalion. The first cohort was the battlefield. approximately double strength (around 800 men) and Artillery Each legion had 60 engines (catapults). One contained the best soldiers. engine was capable of shooting yard-long, heavy bolts Century (59) An administrative unit within a cohort. -

Ground Electronic Warfare: Background and Issues for Congress
Ground Electronic Warfare: Background and Issues for Congress September 17, 2019 Congressional Research Service https://crsreports.congress.gov R45919 SUMMARY R45919 Ground Electronic Warfare: Background and September 17, 2019 Issues for Congress John R. Hoehn Ground electronic warfare (EW) is a group of programs directed by the Army and Marine Corp Analyst in Military which are designed to effect ground forces use of the electromagnetic spectrum. The U.S. Capabilities and Programs military has several ground EW programs that are used for different missions. These programs can broadly be categorized into counter-improvised explosive device (C-IED) systems, counter- unmanned aerial systems (C-UAS), and communications and radar jammers. Over the past several years, senior leaders in the Army and Marine Corps have testified about the need to improve EW capabilities. Role of EW in Ground Operations EW is a component of modern warfare, particularly in response to threats posed by potential adversaries such as Russia and China. EW refers to operations that use the electromagnetic spectrum (i.e., the “airwaves”) to detect, listen to, jam, and deceive (or “spoof”) enemy radars, radio communication systems, data links, and other electronic systems. EW also refers to operations that defend against enemy attempts to do the same. Ground EW programs have gained importance in an era of “great power competition.” Countries like Russia and China have developed so-called anti-access/area denial (A2/AD) systems, some of which are designed to prevent U.S. military access to radio and satellite communications, and to deny the use of radars for artillery and air defense operations. -

This Index Lists the Army Units for Which Records Are Available at the Eisenhower Library
DWIGHT D. EISENHOWER LIBRARY ABILENE, KANSAS U.S. ARMY: Unit Records, 1917-1950 Linear feet: 687 Approximate number of pages: 1,300,000 The U.S. Army Unit Records collection (formerly: U.S. Army, U.S. Forces, European Theater: Selected After Action Reports, 1941-45) primarily spans the period from 1917 to 1950, with the bulk of the material covering the World War II years (1942-45). The collection is comprised of organizational and operational records and miscellaneous historical material from the files of army units that served in World War II. The collection was originally in the custody of the World War II Records Division (now the Modern Military Records Branch), National Archives and Records Service. The material was withdrawn from their holdings in 1960 and sent to the Kansas City Federal Records Center for shipment to the Eisenhower Library. The records were received by the Library from the Kansas City Records Center on June 1, 1962. Most of the collection contained formerly classified material that was bulk-declassified on June 29, 1973, under declassification project number 735035. General restrictions on the use of records in the National Archives still apply. The collection consists primarily of material from infantry, airborne, cavalry, armor, artillery, engineer, and tank destroyer units; roughly half of the collection consists of material from infantry units, division through company levels. Although the collection contains material from over 2,000 units, with each unit forming a separate series, every army unit that served in World War II is not represented. Approximately seventy-five percent of the documents are from units in the European Theater of Operations, about twenty percent from the Pacific theater, and about five percent from units that served in the western hemisphere during World War II. -

Defense Primer: Electronic Warfare
Updated October 29, 2020 Defense Primer: Electronic Warfare Electronic warfare (EW), as defined by the Department of Electronic protection involves actions to protect access Defense (DOD), are military activities that use to the spectrum for friendly military assets. electromagnetic energy to control the electromagnetic Electronic attack uses electromagnetic energy to spectrum (“the spectrum”) and attack an enemy. The degrade or deny an enemy’s use of the spectrum. spectrum is a range of frequencies for electromagnetic EW support identifies and catalogues emissions of energy. EW supports command and control (C2) by friendly or enemy forces to either protect U.S. forces or allowing military commanders’ access to the spectrum to develop a plan to deny an enemy’s access to the communicate with forces, while preventing potential spectrum. adversaries from accessing the spectrum to develop an These subsets of EW often mutually support each other in operational picture and communicate with their forces. operations. EW support uses equipment to assess both Some have argued that EW is a component of anti- friendly and adversary electronic emissions. This access/area denial (A2/AD) campaigns. information can then be used to develop a protection plan to maintain access to the spectrum or an attack plan to deny Role of EW in Military Operations adversaries vital access. Radar jamming (electronic attack) Since the introduction of two-way radios, militaries have can serve a protection function for friendly forces to become dependent on the spectrum. This reliance has penetrate defended airspace, and it prevents an adversary expanded over the past century to include nearly every from having a complete operating picture. -

The Brigade Combat Team (BCT): a Revolution in Organizational Structure
University of Southern Maine USM Digital Commons Muskie School Capstones and Dissertations Student Scholarship 12-2020 The Brigade Combat Team (BCT): A Revolution in Organizational Structure Adam Davis University of Southern Maine, Muskie School of Public Service Follow this and additional works at: https://digitalcommons.usm.maine.edu/muskie_capstones Part of the Defense and Security Studies Commons, Infrastructure Commons, Military and Veterans Studies Commons, Nonprofit Administration and Management Commons, Operations and Supply Chain Management Commons, Organizational Behavior and Theory Commons, and the Policy Design, Analysis, and Evaluation Commons Recommended Citation Davis, Adam, "The Brigade Combat Team (BCT): A Revolution in Organizational Structure" (2020). Muskie School Capstones and Dissertations. 165. https://digitalcommons.usm.maine.edu/muskie_capstones/165 This Capstone is brought to you for free and open access by the Student Scholarship at USM Digital Commons. It has been accepted for inclusion in Muskie School Capstones and Dissertations by an authorized administrator of USM Digital Commons. For more information, please contact [email protected]. The Brigade Combat Team (BCT): A Revolution in Organizational Structure Adam Davis Capstone paper for Master of Policy, Planning, and Management Program Muskie School of Public Service University of Southern Maine December 2020 Professor Joseph McDonnell, Capstone Advisor THE BRIGADE COMBAT TEAM (BCT) 2 Abstract This paper explores the U.S. Army’s force reorganization around the Brigade Combat Team (BCT), which began in 2002. The BCT shifted how various army units interacted by changing the echelon at which different types of units report to a single commander, essentially creating self-sufficient units of about 2,500 soldiers instead of the previous self-sufficient units of about 15,000 soldiers. -

Protecting US Security by Minimizing the Role of Nuclear Weapons
Blechman and Rumbaugh Protecting US Security by Minimizing the Role of Nuclear Weapons: A NEW US NUCLEAR POLICY Barry Blechman and Russell Rumbaugh MAY 2015 STIMSON | 1 Protecting US Security by Minimizing the Role of Nuclear Weapons: a New US Nuclear Policy This paper was prepared in September 2014 and commissioned by the Center for Strategic and International Studies (CSIS). It will be published in “Project Atom: A Competitive Strategies Approach to Defining U.S. Nuclear Strategy and Posture for 2025- 2050” (Washington, DC: CSIS, 2015.) 2 | APRIL 2015 CONTENTS Introduction . 5 US Conventional Military Dominance . 5 The Limited Role of Nuclear Weapons . 8 Minimizing the Roles of Nuclear Weapons in US Policies and Those of Other Nations . 12 Contingencies . 19 Conclusion . 23 “After seventy years of indulging fantasies of what nuclear weapons can do, it is high time to acknowledge that they do very little and adapt US nuclear policy, strategy, and forces to those facts.” Blechman and Rumbaugh INTRODUCTION Nuclear weapons remain the most potent destructive force known to humanity . Yet, US nuclear policies and doctrines remain encumbered by Cold War beliefs in the potential utility of nuclear weapons, even though the United States enjoys a dominant geopolitical position in the world, un- derpinned by a conventional military superiority greater than any ever known before . These false hopes that nuclear weapons can play a range of political and military roles in US security policy cause the United States to mistakenly pursue a nuclear strategy that is costly — not only in material terms, but also in geopolitical terms . In the worst case scenarios, this strategy could be catastroph- ic in terms of human lives and the nation’s future . -

U.S. ARMY: UNIT RECORDS, Sixth Engineer Special Brigade, 1944-1945
DWIGHT D. EISENHOWER LIBRARY ABILENE, KANSAS U.S. ARMY: UNIT RECORDS, Sixth Engineer Special Brigade, 1944-1945 1,600 pages (approximate) Boxes 554-555b The 6th Engineer Special Brigade (ESB) was activated on January 20, 1944, and assigned to the U.S. 1st Army. Throughout the first half of that year the Brigade received reinforcements of men and additional support units. Until the invasion of Normandy, the reconstituted Brigade was involved in training operations in England. There were three Engineer Combat Battalions assigned to the 6th ESB: the 147th, 149th, and 203rd. Along with some supporting units, these battalions landed on Omaha Beach as part of the First Army on June 6, 1944. The remainder of the Brigade landed in follow-up waves throughout that month. After the initial assault on Normandy, the Brigade assisted in the expansion of the beachhead. Most duties for the three Combat Battalions consisted of scouting out and clearing minefields, while the supporting units for the Brigade were involved with the processing of prisoners, transportation of supplies and personnel, and other rear area functions. Records for the 6th ESB are scattered from January 1944 to May 1945, with a number of months being completely absent. Most of the documentation is concentrated between the months of June 1944 and November 1944. Because it was an Engineer unit the 6th ESB was frequently broken up, with it’s subordinate battalions and companies being detached to various units during and after the Normandy landings. The records are therefore made up mostly of these detached units, so they will not appear as part of an overall Brigade history. -

A Comparison of Deployed Occupational Tasks Performed by Different Types of Military Battalions and Resulting Low Back Pain
MILITARY MEDICINE, 178, 8:e937, 2013 A Comparison of Deployed Occupational Tasks Performed by Different Types of Military Battalions and Resulting Low Back Pain MAJ Tanja C. Roy, SP USA*; CPT Heather P. Lopez, SP USA† ABSTRACT With deployment Soldiers must now wear body armor and additional equipment while performing occupational tasks, representing a large demand that has not been considered when studying military occupations. The purpose of this study was to: (1) describe tasks required by different occupational battalions within a Brigade Downloaded from https://academic.oup.com/milmed/article/178/8/e937/4259694 by guest on 04 October 2021 Combat Team; (2) establish the incidence of low back pain (LBP) in each battalion and; (3) determine which tasks predict LBP within the different battalions. This was a prospective cohort study investigating 805 Soldiers in a Brigade Combat Team deployed to Afghanistan for 1 year. Demographic, occupational, and fitness variables were recorded. There was no difference in time spent on fitness training between the battalions. Occupational tasks performed by deployed Soldiers vary in the level of physical demand between battalions. Infantry had the highest fitness score (257); wore the heaviest equipment (70 lb.); spent the most time wearing body armor (49 hours/week), performing dismounted patrol (29 hours/week), and lifting objects (35 hours/week); spent the least amount of time working at a desk (14 hours/week); but had a similar incidence of LBP (77%) compared to other battalions. History of LBP and time spent wearing body armor were the two most consistent predictors of LBP across battalion types. -

Pubsafhrg1 1.Pdf
DEPARTMENT OF PUBLIC SAFETY FY 2014-15 JOINT BUDGET COMMITTEE UPDATED HEARING AGENDA Friday, November 22, 2013 9:00 am – 12:00 pm 9:00-9:05 INTRODUCTIONS AND OPENING COMMENTS 9:05-9:35 DISASTER EMERGENCY FUND – REVENUES, EXPENDITURES, AND FUND BALANCE 1. Please provide details on what commitments the Governor has made to local governments regarding the non-federal match of local expenses. Has the Governor made any commitments to local governments to provide state funding for non-federal match local costs? If yes, provide detail on how the Governor is determining how much state funding to provide, when to provide the funding, and how the Governor is determining which counties to provide the funding to? How much is this additional state financial commitment going to cost the state over time? 2. Are counties going to be able to accept state funding in light of their TABOR limits? 3. Do counties have TABOR emergency reserves by individual county? Are counties in compliance with TABOR requirements for a reserve and can they draw down on their TABOR reserves to resolve some of their disaster emergency costs? 4. How does the FEMA process work with regard to claims being processed? Do all claims have to go through the state or are locals able to make claims directly to FEMA? How long do agencies have to submit claims after a disaster? How long does it take FEMA to respond to claims and reimburse the state or the local agency for the claims? 5. The Disaster Emergency Fund table on page 19 of the JBC staff briefing document shows $3.1 million of reimbursements for the High Park disaster event.