Method for Effectiveness Assessment of Electronic Warfare Systems In
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Erosion of Strategic Stability and the Future of Arms Control in Europe
Études de l’Ifri Proliferation Papers 60 THE EROSION OF STRATEGIC STABILITY AND THE FUTURE OF ARMS COntrOL IN EUROPE Corentin BRUSTLEIN November 2018 Security Studies Center The Institut français des relations internationales (Ifri) is a research center and a forum for debate on major international political and economic issues. Headed by Thierry de Montbrial since its founding in 1979, Ifri is a non- governmental, non-profit organization. As an independent think tank, Ifri sets its own research agenda, publishing its findings regularly for a global audience. Taking an interdisciplinary approach, Ifri brings together political and economic decision-makers, researchers and internationally renowned experts to animate its debate and research activities. The opinions expressed in this text are the responsibility of the author alone. ISBN: 978-2-36567-932-9 © All rights reserved, Ifri, 2018 How to quote this document: Corentin Brustlein, “The Erosion of Strategic Stability and the Future of Arms Control in Europe”, Proliferation Papers, No. 60, November 2018. Ifri 27 rue de la Procession 75740 Paris Cedex 15 – FRANCE Tel.: +33 (0)1 40 61 60 00 – Fax: +33 (0)1 40 61 60 60 Email: [email protected] Website: Ifri.org Author Dr. Corentin Brustlein is the Director of the Security Studies Center at the French Institute of International Relations. His work focuses on nuclear and conventional deterrence, arms control, military balances, and U.S. and French defense policies. Before assuming his current position, he had been a research fellow at Ifri since 2008 and the head of Ifri’s Deterrence and Proliferation Program since 2010. -

Future EW Capabilities
CRITICAL UNCLASSIFIED INFORMATION Future EW Capabilities COL Daniel Holland, ACM-EW Director [email protected] 706-791-8476 CRITICAL17 UNCLASSIFIEDAug 2021 INFORMATION Future Army EW Capabilities AISR Target identification, geo-location, and advanced non-kinetic effects delivery for the MDO fight. HELIOS (MDSS) Altitude 60k’ EW Planning and Management Tool LOS 500 kms (nadir 18 kms) HADES (MDSS) Altitude 40k+’ UAV LOS 400 kms Spectrum Analyzer MFEW Air Large MFEW Air Small Altitude 15k-25k’ Altitude 2500-8000’ LOS 250-300 kms LOS 100-150 kms C2 Counter Fire XX Radar SAM SRBM MEMSS C2 TT Radar Tech Effects CP TA Radar C2 AISR – Aerial ISR DEA – Defensive Electromagnetic Attack GSR- Ground Surveillance Radar TA Radar ERCA – Extended Range Cannon Artillery FLOT – Forward Line of Troops IFPC – Indirect Fire Protection Capability GMLS-ER – Guided Multiple Launch Rocket System Extended Rng UGS HADES – High Accuracy Detection & Exploitation System HELIOS – High altitude Extended range Long endurance Intel Observation System LOS – Line of Sight MDSS – Multi-Domain Sensor System MEMSS - Modular Electromagnetic Spectrum System TLS EAB MFEW – Multifunction Electromagnetic Warfare Ground to Air TLS BCT M-SHORAD – Mobile Short Range Air Defense Close fight TLS – Terrestrial Layer System 30km 70km 150km TT – Target Tracking 500km FLOT THREAT TA – Target Acquisition PrSM Ver 14.6 – 30 Jul 21 155mm ERCA GMLS-ER UGS – Unmanned Ground System AREA UNCLASSIFIED Electronic Warfare Planning and Management Tool (EWPMT) Electromagnetic Warfare/Spectrum -

The Disappearing Human: Gnostic Dreams in a Transhumanist World
religions Article The Disappearing Human: Gnostic Dreams in a Transhumanist World Jeffrey C. Pugh Department of Religious Studies, Elon University, Elon, NC 27244-2020, USA; [email protected] Academic Editor: Noreen Herzfeld Received: 25 January 2017; Accepted: 18 April 2017; Published: 3 May 2017 Abstract: Transhumanism is dedicated to freeing humankind from the limitations of biological life, creating new bodies that will carry us into the future. In seeking freedom from the constraints of nature, it resembles ancient Gnosticism, but complicates the question of what the human being is. In contrast to the perspective that we are our brains, I argue that human consciousness and subjectivity originate from complex interactions between the body and the surrounding environment. These qualities emerge from a distinct set of structural couplings embodied within multiple organ systems and the multiplicity of connections within the brain. These connections take on different forms, including structural, chemical, and electrical manifestations within the totality of the human body. This embodiment suggests that human consciousness, and the intricate levels of experience that accompany it, cannot be replicated in non-organic forms such as computers or synaptic implants without a significant loss to human identity. The Gnostic desire to escape our embodiment found in transhumanism carries the danger of dissolving the human being. Keywords: Singularity; transhumanism; Merleau-Ponty; Kurzweil; Gnosticism; AI; emergence; technology 1. Introduction In 1993, the mathematician and science fiction writer Vernor Vinge gave a talk at the Vision 21 symposium sponsored by NASA introducing the idea of the Singularity, an evolutionary moment when we would create the capacity for superhuman intelligence that would transcend the human and take us into the posthuman world (Vinge 1993). -

Electromagnetic Side Channels of an FPGA Implementation of AES
Electromagnetic Side Channels of an FPGA Implementation of AES Vincent Carlier, Herv´e Chabanne, Emmanuelle Dottax and Herv´e Pelletier SAGEM SA Abstract. We show how to attack an FPGA implementation of AES where all bytes are processed in parallel using differential electromag- netic analysis. We first focus on exploiting local side channels to isolate the behaviour of our targeted byte. Then, generalizing the Square at- tack, we describe a new way of retrieving information, mixing algebraic properties and physical observations. Keywords: side channel attacks, DEMA, FPGA, AES hardware im- plementation, Square attack. 1 Introduction Side channel attacks first appear in [Koc96] where timing attacks are de- scribed. This kind of attack tends to retrieve information from the secret items stored inside a device by observing its behaviour during a crypto- graphical computation. In a timing attack, the adversary measures the time taken to perform the computations and deduces additionnal information about the cryptosystems. Similarly, power analysis attacks are introduced in [KJJ99] where the attacker wants to discover the secrets by analysing the power consumption. Smart cards are targets of choice as their power is sup- plied externally. Usually we distinguish Simple Power Analysis (SPA), that tries to gain information directly from the power consumption, and Differ- ential Power Analysis (DPA) where a large number of traces are acquired and statistically processed. Another side channel is the one that exploits the Electromagnetic (EM) emanations. Indeed, these emanations are correlated with the current flowing through the device. EM leakage in a PC environ- ment where eavesdroppers reconstruct video screens has been known for a 1 long time [vE85], see also [McN] for more references. -

The Virtual Worlds of Japanese Cyberpunk
arts Article New Spaces for Old Motifs? The Virtual Worlds of Japanese Cyberpunk Denis Taillandier College of International Relations, Ritsumeikan University, Kyoto 603-8577, Japan; aelfi[email protected] Received: 3 July 2018; Accepted: 2 October 2018; Published: 5 October 2018 Abstract: North-American cyberpunk’s recurrent use of high-tech Japan as “the default setting for the future,” has generated a Japonism reframed in technological terms. While the renewed representations of techno-Orientalism have received scholarly attention, little has been said about literary Japanese science fiction. This paper attempts to discuss the transnational construction of Japanese cyberpunk through Masaki Goro’s¯ Venus City (V¯ınasu Shiti, 1992) and Tobi Hirotaka’s Angels of the Forsaken Garden series (Haien no tenshi, 2002–). Elaborating on Tatsumi’s concept of synchronicity, it focuses on the intertextual dynamics that underlie the shaping of those texts to shed light on Japanese cyberpunk’s (dis)connections to techno-Orientalism as well as on the relationships between literary works, virtual worlds and reality. Keywords: Japanese science fiction; cyberpunk; techno-Orientalism; Masaki Goro;¯ Tobi Hirotaka; virtual worlds; intertextuality 1. Introduction: Cyberpunk and Techno-Orientalism While the inversion is not a very original one, looking into Japanese cyberpunk in a transnational context first calls for a brief dive into cyberpunk Japan. Anglo-American pioneers of the genre, quite evidently William Gibson, but also Pat Cadigan or Bruce Sterling, have extensively used high-tech, hyper-consumerist Japan as a motif or a setting for their works, so that Japan became in the mid 1980s the very exemplification of the future, or to borrow Gibson’s (2001, p. -

Conductive Concrete’ Shields Electronics from EMP Attack
‘Conductive concrete’ shields electronics from EMP attack November 14, 2016 Credit: Craig Chandler/University Communication/University of Nebraska-Lincoln An attack via a burst of electromagnetic energy could cripple vital electronic systems, threatening national security and critical infrastructure, such as power grids and data centers. The technology is ready for commercialization, and the University of Nebraska-Lincoln has signed an agreement to license this shielding technology to American Business Continuity Group LLC, a developer of disaster-resistant structures. Electromagnetic energy is everywhere. It travels in waves and spans a wide spectrum, from sunlight, radio waves and microwaves to X- rays and gamma rays. But a burst of electromagnetic waves caused by a high-altitude nuclear explosion or an EMP device could induce electric current and voltage surges that cause widespread electronic failures. "EMP is very lethal to electronic equipment," said Tuan, professor of civil engineering. "We found a key ingredient that dissipates wave energy. This technology oöers a lot of advantages so the construction industry is very interested." EMP-shielding concrete stemmed from Tuan and Nguyen's partnership to study concrete that conducts electricity. They ñrst developed their patented conductive concrete to melt snow and ice from surfaces, such as roadways and bridges. They also recognized and conñrmed it has another important property – the ability to block electromagnetic energy. Their technology works by both absorbing and reòecting electromagnetic waves. The team replaced some standard concrete aggregates with their key ingredient – magnetite, a mineral with magnetic properties that absorbs microwaves like a sponge. Their patented recipe includes carbon and metal components for better absorption as well as reòection. -

"The Infinite Plasticity of the Digital"
"The Infinite Plasticity of the Digital" http://reconstruction.eserver.org/043/leaver.htm Ever since William Gibson coined the term "cyberspace" in his debut novel Neuromancer , his work has been seen by many as a yardstick for postmodern and, more recently, posthuman possibilities. This article critically examines Gibson's second trilogy ( Virtual Light , Idoru and All Tomorrow's Parties ), focusing on the way digital technologies and identity intersect and interact, with particular emphasis on the role of embodiment. Using the work of Donna Haraway, Judith Butler and N. Katherine Hayles, it is argued that while William Gibson's second trilogy is infused with posthuman possibilities, the role of embodiment is not relegated to one choice among many. Rather the specific materiality of individual existence is presented as both desirable and ultimately necessary to a complete existence, even in a posthuman present or future. "The Infinite Plasticity of the Digital": Posthuman Possibilities, Embodiment and Technology in William Gibson's Interstitial Trilogy Tama Leaver Communications technologies and biotechnologies are the crucial tools recrafting our bodies. --- Donna Haraway, "A Cyborg Manifesto" She is a voice, a face, familiar to millions. She is a sea of code ... Her audience knows that she does not walk among them; that she is media, purely. And that is a large part of her appeal. --- William Gibson, All Tomorrow's Parties <1> In the many, varied academic responses to William Gibson's archetypal cyberpunk novel Neuromancer , the most contested site of meaning has been Gibson's re-deployment of the human body. Feminist critic Veronica Hollinger, for example, argued that Gibson's use of cyborg characters championed the "interface of the human and the machine, radically decentring the human body, the sacred icon of the essential self," thereby disrupting the modernist and humanist dichotomy of human and technology, and associated dualisms of nature/culture, mind/body, and thus the gendered binarism of male/female (33). -

Ground Electronic Warfare: Background and Issues for Congress
Ground Electronic Warfare: Background and Issues for Congress September 17, 2019 Congressional Research Service https://crsreports.congress.gov R45919 SUMMARY R45919 Ground Electronic Warfare: Background and September 17, 2019 Issues for Congress John R. Hoehn Ground electronic warfare (EW) is a group of programs directed by the Army and Marine Corp Analyst in Military which are designed to effect ground forces use of the electromagnetic spectrum. The U.S. Capabilities and Programs military has several ground EW programs that are used for different missions. These programs can broadly be categorized into counter-improvised explosive device (C-IED) systems, counter- unmanned aerial systems (C-UAS), and communications and radar jammers. Over the past several years, senior leaders in the Army and Marine Corps have testified about the need to improve EW capabilities. Role of EW in Ground Operations EW is a component of modern warfare, particularly in response to threats posed by potential adversaries such as Russia and China. EW refers to operations that use the electromagnetic spectrum (i.e., the “airwaves”) to detect, listen to, jam, and deceive (or “spoof”) enemy radars, radio communication systems, data links, and other electronic systems. EW also refers to operations that defend against enemy attempts to do the same. Ground EW programs have gained importance in an era of “great power competition.” Countries like Russia and China have developed so-called anti-access/area denial (A2/AD) systems, some of which are designed to prevent U.S. military access to radio and satellite communications, and to deny the use of radars for artillery and air defense operations. -

Cyberspace Operations
Updated December 15, 2020 Defense Primer: Cyberspace Operations Overview force; (2) compete and deter in cyberspace; (3) strengthen The Department of Defense (DOD) defines cyberspace as a alliances and attract new partnerships; (4) reform the global domain within the information environment department; and (5) cultivate talent. consisting of the interdependent network of information technology infrastructures and resident data, including the Three operational concepts identified in the DOD Cyber internet, telecommunications networks, computer systems, Strategy are to conduct cyberspace operations to collect and embedded processors and controllers. The DOD intelligence and prepare military cyber capabilities to be Information Network (DODIN) is a global infrastructure used in the event of crisis or conflict, and to defend forward carrying DOD, national security, and related intelligence to disrupt or halt malicious cyber activity at its source, community information and intelligence. including activity that falls below the level of armed conflict. Defending forward may involve a more aggressive Cyberspace operations are composed of the military, active defense, meaning activities designed to disrupt an intelligence, and ordinary business operations of the DOD adversary’s network when hostile activity is suspected. in and through cyberspace. Military cyberspace operations use cyberspace capabilities to create effects that support Cyber Mission Force operations across the physical domains and cyberspace. DOD began to build a Cyber Mission Force (CMF) in 2012 Cyberspace operations differ from information operations to carry out DOD’s cyber missions. The CMF consists of (IO), which are specifically concerned with the use of 133 teams that are organized to meet DOD’s three cyber information-related capabilities during military operations missions. -

The Cyberspace Concept Cyberpunk: the Idea William Gibson Computer
Cyberpunk: The Idea Term coined in by Bruce Bethke The Cyberspace Concept punk part reflects streetwise attitude Tone tends to be dark, cynical Immersion in computer generated, shared worlds is a key theme Social Informatics Other themes Alteration of human bodies, genes Thomas Haigh Popular culture, music, media power Week 10 Critical of corporate power Often romantic, rebellious Social Informatics - Cyberspace 1 Social Informatics - Cyberspace 2 William Gibson Computer Technology in SF Creates idea of cyberspace Common by mid-1950s Best known in novel Necromancer, 1984 Futuristic technology lags history Early appearance in short story “Burning Chrome” Big, expensive, central computers Science fiction writer then living in Used mostly for mathematics Canada Nobody much predicts No particular knowledge of computers Personal computer Writes Neuromancer & earlier stories on manual typewriter Microchips, miniaturization Imagines technology in very visual, Interactive graphics impressionistic kind of way Main extrapolation is artificial intelligence Vivid, spatial, seedy (film noir influence) Often arrives spontaneously Social Informatics - Cyberspace 3 Social Informatics - Cyberspace 4 Networking: Science Fiction Gibson’s Cyberspace Famously defined as “consensual hallucination” for Little realistic treatment pre-1980 exchange of data Very much like real space John Brunner, Shockwave Rider, 1975 invents idea of computer “worm” Big mainframes are like skyscrapers Valuable data is protected Vernor Vinge, “True -

Defense Primer: Electronic Warfare
Updated October 29, 2020 Defense Primer: Electronic Warfare Electronic warfare (EW), as defined by the Department of Electronic protection involves actions to protect access Defense (DOD), are military activities that use to the spectrum for friendly military assets. electromagnetic energy to control the electromagnetic Electronic attack uses electromagnetic energy to spectrum (“the spectrum”) and attack an enemy. The degrade or deny an enemy’s use of the spectrum. spectrum is a range of frequencies for electromagnetic EW support identifies and catalogues emissions of energy. EW supports command and control (C2) by friendly or enemy forces to either protect U.S. forces or allowing military commanders’ access to the spectrum to develop a plan to deny an enemy’s access to the communicate with forces, while preventing potential spectrum. adversaries from accessing the spectrum to develop an These subsets of EW often mutually support each other in operational picture and communicate with their forces. operations. EW support uses equipment to assess both Some have argued that EW is a component of anti- friendly and adversary electronic emissions. This access/area denial (A2/AD) campaigns. information can then be used to develop a protection plan to maintain access to the spectrum or an attack plan to deny Role of EW in Military Operations adversaries vital access. Radar jamming (electronic attack) Since the introduction of two-way radios, militaries have can serve a protection function for friendly forces to become dependent on the spectrum. This reliance has penetrate defended airspace, and it prevents an adversary expanded over the past century to include nearly every from having a complete operating picture. -
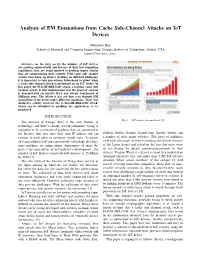
Analysis of EM Emanations from Cache Side-Channel Attacks on Iot Devices
Analysis of EM Emanations from Cache Side-Channel Attacks on IoT Devices Moumita Dey School of Electrical and Computer Engineering, Georgia Institute of Technology, Atlanta, USA [email protected] Abstract— As the days go by, the number of IoT devices are growing exponentially and because of their low computing capabilities, they are being targeted to perform bigger attacks that are compromising their security. With cache side channel attacks increasing on devices working on different platforms, it is important to take precautions beforehand to detect when a cache side channel attack is performed on an IoT device. In this paper, the FLUSH+RELOAD attack, a popular cache side channel attack, is first implemented and the proof of concept is demonstrated on GnuPG RSA and bitcnts benchmark of MiBench suite. The effects it has are then seen through EM emanations of the device under different conditions. There was distinctive activity observed due to FLUSH+RELOAD attack, which can be identified by profiling the applications to be monitored. INTRODUCTION Fig. 1. IoT devices demand trend [1] The Internet of Things (IoT) is the next frontier in technology, and there’s already several companies trying to capitalize it. Its a network of products that are connected to the Internet, thus they have their own IP address and can GitHub, Netflix, Shopify, SoundCloud, Spotify, Twitter, and connect to each other to automate simple tasks. As prices a number of other major websites. This piece of malicious of semiconductor fall and connectivity technology develops, code took advantage of devices running out-of-date versions more machines are going online.