Multiple Vulnerabilities in Microsoft Internet Explorer
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows® 10 Iot Enterprise Nel Dettaglio
Windows 10 IoT Enterprise | Il nuovo S.O. Microsoft per applicazioni industriali Windows 10 IoT Enterprise Il nuovo S.O. Microsoft per applicazioni industriali Windows 10 IoT Enterprise Il nuovo S.O. Microsoft per applicazioni industriali Indice PAG 2 White_Paper | Windows 10 IoT © 2019 FEC Italia Windows 10 IoT Enterprise | Il nuovo S.O. Microsoft per applicazioni industriali Introduzione Windows 10 è una piattaforma composta da diversi sistemi operativi suddivisi in due categorie: Windows 10 per applicazioni consumer e office automation e Windows 10 IoT per applicazioni industriali. Windows 10 Windows 10 IoT — Enterprise — Enterprise — Education — Mobile Enterprise — Pro — Core — Home Un unico sistema operativo, molti vantaggi Windows 10 IoT Enterprise è stato progettato per applicazioni industriali moderne e sicure e fornisce tutte le usuali funzionalità di Windows 10 con in aggiunta le funzionalità avanzate di sicurezza incluse nelle versioni precedentemente denominate Embedded (Safety&Locking). Sistemi operativi precedenti Windows 10 IoT Enterprise Standard fully featured PRO Language packs (MUI) Standard&Industrial fully featured Industrial Safety&Locking Safety&Locking Language packs (MUI) Language packs (MUI) Embedded PAG 3 White_Paper | Windows 10 IoT © 2019 FEC Italia Windows 10 IoT Enterprise | Il nuovo S.O. Microsoft per applicazioni industriali Sicurezza e Funzionalità Lockdown Ecco solo alcune delle features che Windows IoT Enterprise offre in termini di sicurezza: » Le ultime tecnologie e funzionalità rivolte alla sicurezza e protezione dei dati azien- dali e delle credenziali di accesso ai dispositivi, con alta resistenza a malware di ultima generazione » Accesso solo a dispositivi autorizzati » Esecuzione solo di applicazioni autorizzate » Lockdown features (UWF, USB filters, AppLocker..) — UWF Unified Write Filter di tasti, quale ad esempio lo swipe da destra Questo filtroprotegge il disco da cambia- che attiva l’Action Center onde evitare accessi menti indesiderati. -

Microsoft Windows Server 2019 Version 1809 Hyper-V
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

Download Win 10 Version 1809
download win 10 version 1809 How to Manually Install Windows 10 1809 October 2018 Update (Updated) Microsoft released Windows 10 October 2018 Update version 1809 and if you don’t want to get it via Windows Update you can manually install it. Microsoft recently announced that the latest Windows 10 feature update, Windows 10 October 2018 update Version 1809, is now available. In addition to security and performance improvements, this version also includes several new features. In addition, there are improvements to the UI, including Dark Mode for File Explorer, the new Your Phone app, a new screenshot tool, and a lot more. Just like previous feature updates, this one will roll out over Windows Update in staggered phases depending on the system you’re running it on. But some of you might want to install it or do a clean install manually. Manually Install Windows 10 1809. An easy way to manually install the new feature update is to use Microsoft’s own utility. To get started, head to the Windows 10 Download page and click the Update now button to download the Update Assistant tool. From this point on, the process of upgrading is straightforward. Launch the tool, and it will check your system for compatibility and download the update. Note that doing it this way, your current files, apps, and settings will be kept. It’s also worth mentioning that you can cancel the update by clicking in mind you can cancel the update while it’s running if you have second thoughts while it’s running. -

Windows 10 Insider Preview Build 17763 the Final!
Windows 10 Insider Preview Build 17763 The Final! 1 / 5 Windows 10 Insider Preview Build 17763 The Final! 2 / 5 3 / 5 Windows 10 Insider Preview Build 17763 ... that Microsoft is “beginning the phase of checking in final code to prepare for the final release,” in Microsoft's words. Windows 10 Insider Preview Build 17763 will be RTM version ... the final release of Windows Server 2019, Version 1809, #LTSC and #SAC .... on announcement of insider 18298, I installed it. ... Insiders in the Slow ring running older builds need to update to Build 17763 (the final build for the ... -windows-10-insider-preview-build-18290/#JXQz3xoIzbTegKMH.97 ... Build 17763 is released version of Win 10 and you can download ISO from here.. and i roll back to 16232. Windows 10 Insider Preview 16251.0 (rs3_release) (2) error Last failed install attempt on 7/28/2017 - 0x80070643.. Windows 10 October 2018 Update: Could build 17763 be the final ... The latest Windows 10 Insider Preview for version 1809 or Redstone 5 is .... Microsoft will reportedly give Windows 10 preview 17763 to OEMs as the final build ... in conjunction with Windows 10 Insider Preview (Build 17763 or greater). Assassin’s Creed 3 PC Games Download Yet another preview of Windows 10 October 2018 Update (build 17763) outs to Insiders with more fixes to stabilize the final version. Avatar for ... Bullies Children Acting Out: The Rebellion of Attention Seeking Disorder CSS – a guide for the unglued Nero Burning ROM 2018 19.0.00800 Full Crack Serial Number Download Another week, another Insider Preview build for those in the Fast ring! Today's build is 17763, and is one of the last builds Insiders are going to .. -

Support Newsletter Issue 30
RM Education RM Support Newsletter Issue 30 Support Newsletter Issue 30 Included in this issue • Moving to Windows 10 – Avoiding common issues • CC4 news and updates (Windows 10 v1809, UEV update and CC4UPD218) • Intune for Education and Printix cloud printing • Office 2019 for CC4 • RM Unify – RM recommendations for summer work • RM Seminars – Autumn 2019 information • New research identifies issues with online safety in schools 1 RM Education [email protected] Support Newsletter Issue 30 Support Newsletter July 2019 Welcome to issue 30 of the support newsletter. This is the summer 2019 edition and so is heavily focussed on your ‘summer refresh’. We know that many customers will be looking to move to Windows 10 as the demise of Windows 7 rapidly approaches (January 2020 – now less than six months away). As such you’ll find attached to the email of this newsletter a PDF file named ‘Moving to Windows 10 – Avoiding common issues’, which we recommend that all customers read through (there are also links to this PDF below if you are reading the online version of the newsletter). As well as moving to Windows 10, there’s also a section for RM Unify customers giving some advice and recommendations for summer work too. This newsletter also includes the normal security information, updates and development news. Please do feed back suggestions for content you’d like to see us cover in the future – email us at [email protected]. Please note you may be the only person within your establishment to receive this newsletter so please pass on to your colleagues. -

Microsoft Windows Common Criteria Evaluation Security Target
Microsoft Common Criteria Security Target Microsoft Windows Common Criteria Evaluation Microsoft Windows 10 version 1809 (October 2018 Update) Microsoft Windows Server 2019 (October 2018 Update) Security Target Document Information Version Number 0.05 Updated On June 18, 2019 Microsoft © 2019 Page 1 of 126 Microsoft Common Criteria Security Target Version History Version Date Summary of changes 0.01 June 27, 2018 Initial draft 0.02 December 21, 2018 Updates from security target evaluation 0.03 February 21, 2019 Updates from evaluation 0.04 May 6, 2019 Updates from GPOS PP v4.2.1 0.05 June 18, 2019 Public version Microsoft © 2019 Page 2 of 126 Microsoft Common Criteria Security Target This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. -
Download Windows 10 Update 1809 Windows 10: Continue Support for Versions 1803 and Onward
download windows 10 update 1809 Windows 10: continue support for versions 1803 and onward. I have a question for the Windows team. I want to know if it is possible to continue support for Windows 10 version 1803 and onward? I am using 1809. I am asking is because when 1903 comes out someday, my device might not be able to work with it. I would like to use it but do not want to spend $$ buying a new device. 1809 is a good version. It seems like Microsoft will end support for different versions of Windows 10 different times. Subscribe Subscribe to RSS feed. Report abuse. Replies (6) Support for version 1809 ends on May 12, 2020. All this means is that you will not receive updates for that version, it does not mean that your Windows will cease to function, it will continue working as it always has . If your device cannot take the 1903 update, then it will refuse to install, that is all that will happen, you have nothing to worry about . Power to the Developer! MSI GV72 - 17.3", i7-8750H (Hex Core), 32GB DDR4, 4GB GeForce GTX 1050 Ti, 256GB NVMe M2, 2TB HDD. Report abuse. Was this reply helpful? Sorry this didn't help. Great! Thanks for your feedback. How satisfied are you with this reply? Thanks for your feedback, it helps us improve the site. How satisfied are you with this reply? Thanks for your feedback. I mean continue support for versions like 1803, 1809 and onward. I don't think anyone want the versions to end support. -

GV-LPR Plugin Fence & Light GV-IP LPR Camera · GV-USB Dongle
Introduction GeoVision's License Plate Recognition is an effective and low-maintenance solution to ensure the security of parking lots, which are prone to crimes due to isolated and unstaffed corners. In addition to providing high-resolution video monitoring, the LPR solution can detect and recognize vehicle license plates upon motion or I/O trigger. When a GV-LPR device -- Edge GV-IP LPR Camera, GV-DSP LPR, or PC-based GV-DVR LPR / VMS LPR -- detects or recognizes license plates in video sources, it sends the LPR results to the access control system GV-ASManager. Access can be granted when the detected license plate numbers match the vehicles registered in GV-ASManager's database. Alarm notifications and playing back LPR results are also supported. Setting & Database GV-Software Video Source + Plate Recongition Edge GV-IP LPR Camera GV-ASManager Video Source + Plate Recongition Supporting up to 255 GV- Live View, Recording and LPR devices Playback · GV-DVR / NVR / VMS · GV-Recording Server Analog Camera GV-DSP LPR Video Source + Plate Recongition Live View · GV-ASManager GV-I/O Box · GV-Edge Recording Manager Analog Camera · GV-Center V2 GV-DVR LPR / GV-VMS LPR Event Text Message / Log PC installed with · GV-DVR / NVR / VMS · GV-Vital Sign Monitor · GV-LPR Plugin Fence & Light GV-IP LPR Camera · GV-USB Dongle Note: Edge GV-IP LPR Camera includes GV-LPR2811-DL / GV-LPR2800-DL / GV-LPR1200. -1- License Plate Recognition August 30, 2021 Available Versions of Machine Learning (ML) Recognition Engines Argentina Australia Austria Belgium Brazil Canada China Chile Columbia Croatia Czech Republic France Germany Hungary India Ireland Israel Italy Morocco Mexico Norway Poland Portugal Qatar Russia Slovakia South Africa Spain Taiwan UK USA Vietnam Note: There is a Global version which is suitable for most of the other countries. -

Recovery Media Creation Guide Based on Active Backup for Business 2.1.1 Table of Contents
Recovery Media Creation Guide Based on Active Backup for Business 2.1.1 Table of Contents Introduction Method 1: Automatically Create Recovery Media System Requirements and Supported Media Types 4 Create USB Recovery Media 5 Create ISO Recovery Media 7 Cancel Recovery Media or Troubleshoot Failure 9 Method 2: Manually Create Recovery Media System Requirements and Limitations 10 Create Recovery Media with the Windows ADK 11 Pack Recovery Media 13 Boot Recovery Media (ISO Image or USB Drive) 16 Appendix Copy Drivers 17 Install Drivers 17 Configure Resolution 18 Configure Language Settings 18 Add Certificate to WinPE Image 19 2 Introduction Synology Active Backup for Business is a business-wise and all-in-one backup solution that supports backing up physical devices including Windows PCs and Windows servers. With this solution, you can create recovery media to restore an entire device either automatically or manually. Recovery media must be created manually if the device intended to be restored is running a 32-bit version of Windows or contains specific driver versions, time zone, or language. However, recovery media can be created automatically if the device intended to be restored is not running a 32-bit version of Windows and does not contain specific drivers, time zone, and language. We recommend you to create recovery media automatically, if possible, because this method is easier. This Recovery Media Creation Guide details the methods for creating recovery media automatically or manually. Please refer to the following chapters detailing the methods, requirements, limitations, and processes of recovery media creation. 3 Introduction Method 1: Automatically Create Recovery Media Synology Active Backup for Business Recovery Media Creator is a desktop tool affiliated to our business data protection solution — Active Backup for Business. -
March 2021 Abstract: Critical Or Security Patches – March 2021
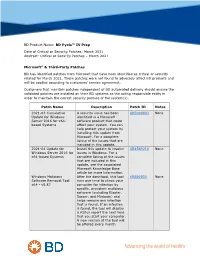
BD Product Name: BD Pyxis™ IV Prep Date of Critical or Security Patches: March 2021 Abstract: Critical or Security Patches – March 2021 Microsoft® & Third-Party Patches BD has identified patches from Microsoft that have been identified as critical or security related for March 2021. These patches were not found to adversely affect BD products and will be applied according to customers’ service agreement. Customers that maintain patches independent of BD automated delivery should ensure the validated patches are installed on their BD systems as the acting responsible entity in order to maintain the correct security posture of the system(s). Patch Name Description Patch ID Notes 2021-03 Cumulative A security issue has been KB5000803 None Update for Windows identified in a Microsoft Server 2016 for x64- software product that could based Systems affect your system. You can help protect your system by installing this update from Microsoft. For a complete listing of the issues that are included in this update, 2021-01 Update for Install this update to resolve KB4589210 None Windows Server 2016 for issues in Windows. For a x64-based Systems complete listing of the issues that are included in this update, see the associated Microsoft Knowledge Base article for more information. Windows Malicious After the download, this tool KB890830 None Software Removal Tool runs one time to check your x64 - v5.87 computer for infection by specific, prevalent malicious software (including Blaster, Sasser, and Mydoom) and helps remove any infection that is found. If an infection is found, the tool will display a status report the next time that you start your computer. -
Mcafee Policy Auditor Content Update V1326
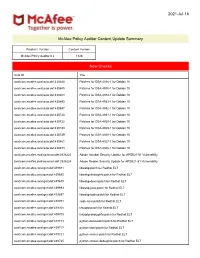
2021-Jul-16 McAfee Policy Auditor Content Update Summary Product / Version Content Version McAfee Policy Auditor 6.x 1326 New Checks Oval ID Title oval:com.mcafee.oval.auto:def:430640 Patches for DSA-4936-1 for Debian 10 oval:com.mcafee.oval.auto:def:430680 Patches for DSA-4935-1 for Debian 10 oval:com.mcafee.oval.auto:def:430683 Patches for DSA-4934-1 for Debian 10 oval:com.mcafee.oval.auto:def:430693 Patches for DSA-4933-1 for Debian 10 oval:com.mcafee.oval.auto:def:430697 Patches for DSA-4932-1 for Debian 10 oval:com.mcafee.oval.auto:def:430720 Patches for DSA-4931-1 for Debian 10 oval:com.mcafee.oval.auto:def:430732 Patches for DSA-4930-1 for Debian 10 oval:com.mcafee.oval.auto:def:430733 Patches for DSA-4929-1 for Debian 10 oval:com.mcafee.oval.auto:def:430739 Patches for DSA-4928-1 for Debian 10 oval:com.mcafee.oval.auto:def:430861 Patches for DSA-4927-1 for Debian 10 oval:com.mcafee.oval.auto:def:430873 Patches for DSA-4926-1 for Debian 10 oval:com.mcafee.oval.common:def:2938223 Adobe Acrobat Security Update for APSB21-51 Vulnerability oval:com.mcafee.oval.common:def:2938224 Adobe Reader Security Update for APSB21-51 Vulnerability oval:com.mcafee.oval.gen:def:439681 libwebp patch for Redhat EL7 oval:com.mcafee.oval.gen:def:439685 libwebp-debuginfo patch for Redhat EL7 oval:com.mcafee.oval.gen:def:439689 libwebp-devel patch for Redhat EL7 oval:com.mcafee.oval.gen:def:439693 libwebp-java patch for Redhat EL7 oval:com.mcafee.oval.gen:def:439697 libwebp-tools patch for Redhat EL7 oval:com.mcafee.oval.gen:def:439701 ceph-iscsi patch -

Installing and Configuring Vmware Dynamic Environment Manager
Installing and Configuring VMware Dynamic Environment Manager VMware Dynamic Environment Manager 9.11 Installing and Configuring VMware Dynamic Environment Manager You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com © Copyright 2020 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents About Installing and Configuring VMware Dynamic Environment Manager 6 1 Introduction to VMware Dynamic Environment Manager 7 Application Configuration Management 7 User Environment Settings 8 Personalization of Application and Windows Settings 8 Migration of Application Settings 9 Dynamic Configuration of the Desktop 9 2 VMware Dynamic Environment Manager Scenario Considerations 10 Using VMware Dynamic Environment Manager with Mandatory Profiles 10 Using VMware Dynamic Environment Manager with Roaming Profiles 11 Using VMware Dynamic Environment Manager with Local Profiles 12 3 Installation and Deployment Prerequisites 14 VMware Dynamic Environment Manager Infrastructure and Terminology 14 Overview of the VMware Dynamic Environment Manager Deployment 16 Infrastructure Requirements 16 VMware Dynamic Environment Manager Configuration Share 17 Profile Archives Share 18 Software Requirements 19 Registry Access Requirements 20 Licensing Requirements 20 4 Installing VMware Dynamic Environment Manager 21 Overview of the VMware Dynamic Environment Manager Deployment 22 Install VMware Dynamic Environment