Microsoft Windows Common Criteria Evaluation Hyper-V Security Target
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Microsoft Windows 10 Update Hello, Microsoft Has Begun
Subject Line: Microsoft Windows 10 Update Hello, Microsoft has begun pushing a warning message to Windows 10 computers that a critical security update must be performed. Several clients have informed us that they are seeing the warning message. It will appear as a generic blue screen after your computer has been powered up, and it states that after April 10, 2018 Microsoft will no longer support your version of Windows 10 until the critical security update has been performed. Please note if your UAN computer has not been recently connected to the internet, you would not have received this message. UAN has confirmed that the warning message is a genuine message from Microsoft, and UAN strongly encourages all clients to perform this critical security update as soon as possible. Please note: ‐ This update is a Microsoft requirement and UAN cannot stop or delay its roll out. To perform the critical security updated select the ‘Download update’ button located within the warning message. ‐ This update is very large, for those clients that have metered internet usage at their home may want to perform the update at a different location with unmetered high speed internet, perhaps at another family member’s home. ‐ Several UAN staff members have performed the critical security update on their home computers, and the process took more than an hour to complete. To check that your computer has been updated or to force the update at a time that is convenient to you, go to the windows Start button and click on Settings (the icon that looks like a gear above the Start button) > Update and Security > Windows Update > Check for Updates and then follow the instructions on the screen. -

Guide to Hardening Windows 10 Technical Guide
NOVEMBER 2020 Guide to Hardening Windows 10 For Administrators, Developers and Office Workers TABLE OF CONTENTS Introduction .......................................................................................................................... 4 Prerequisites ............................................................................................................................ 4 User roles ................................................................................................................................. 4 EFI (BIOS) Configuration ...................................................................................................... 5 To be enabled: ......................................................................................................................... 5 To be disabled: ......................................................................................................................... 5 Windows Defender Firewall .................................................................................................. 6 Enable logging of dropped packets ............................................................................................. 6 Disable enforcement of local rules and disable notifications .......................................................... 7 Block outbound connections by default ....................................................................................... 8 Secure potentially vulnerable protocols ...................................................................................... -

Microsoft Service Pack & Security Bulletin Support
Microsoft Service Pack & Security Bulletin Support ReadMe Revision History Date Revised Changes Made March 23, 2020 March 2020 Microsoft Security Update Contents What’s New? . 1 Microsoft Security Bulletins . 2 Current Microsoft Security Bulletin Status . 2 Enabling Windows Updates on Avid Systems . 6 Using a Microsoft WSUS Server for distributing Windows Updates. 7 Historical List of Microsoft Security Bulletin Exceptions . 7 What’s New? For March security bulletins, see “Current Microsoft Security Bulletin Status” on page 2. The section on “Notification Regarding the January 2020 Windows Updates” on page 3 has been updated to include information on MediaCentral Asset Management and MediaCentral Newsroom Management. See also http://avid.force.com/pkb/articles/en_US/Troubleshooting/en239659. Microsoft Security Bulletins Microsoft Security Bulletins Install Windows Security Patches and Service Packs. To download patches, run Windows Update. By default Avid supports all Windows Service Packs and security patches (sometimes referred to as “hot fixes”) which apply to the environments in which Avid products are deployed. We refer to them as Windows Updates in this document. Customers can schedule the download and installation of Windows Updates whenever they are available and make sense in their production environment. Avid tests the updates within several days of their availability. However, customers do not have to wait for the testing to be complete before installing the updates. Our current testing methodology is to utilize Windows Update on a representative sample of Avid products upon notification of new Security Bulletin availability by Microsoft. These systems are updated and observed while under test. Once the test period has completed (approx. -
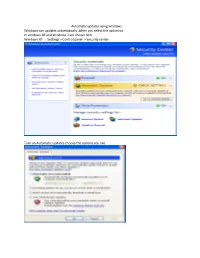
Automatic Updates Using Windows Windows Can Updates Automatically ,When You Select the Option On
Automatic updates using windows Windows can updates automatically ,when you select the option on. In windows XP and Windows 7 are shown here Windows XP : Settings > Control panel > Security center Turn on Automatic updates choose the options you like. In windows 7: Control panel > System and security So how can do all users let updates on system. By default, Windows only allows users with administrator user accounts to install updates. To allow all users to install updates, follow these steps: Click to open Windows Update. In the left pane, click Change settings. Do one of the following: To allow standard users to install updates, select the Allow all users to install updates on this computer check box. To prevent standard users from installing updates, clear the Allow all users to install updates on this computer check box. If you use automatic updating for Important or Recommended updates, those updates are installed regardless of whether the current user is an administrator or not. Different types of updates Updates are classified as Important, Recommended, Optional, and Featured. Important updates offer significant benefits, such as improved security, privacy, and reliability. They should be installed as they become available, and can be installed automatically with Windows Update. Recommended updates address non-critical problems or help enhance your computing experience. While these updates do not address fundamental issues with your computer or Windows software, they can offer meaningful improvements. These can be installed automatically. Optional updates can include updates, drivers, or new software from Microsoft to enhance your computing experience. You can only install these manually. -

Microsoft Windows Server 2019 Version 1809 Hyper-V
Operational and Administrative Guidance Microsoft Windows Server, Microsoft Windows 10 version 1909 (November 2019 Update), Microsoft Windows Server 2019 version 1809 Hyper-V Common Criteria Evaluation under the Protection Profile for Virtualization, including the Extended Package for Server Virtualization Revision date: January 15, 2021 © 2021 Microsoft. All rights reserved. Microsoft Windows Server and Windows 10 Hyper-V Administrative Guidance Copyright and disclaimer The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs-NonCommercial VLicense (which allows redistribution of the work). To view a copy of this license, visithttp://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. Microsoft may have patents, patent applications, trademarks, copyrights, or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. The example companies, organizations, products, people and events depicted herein are fictitious. -

The Control Panel and Settings in Windows 10 Most Programs and Apps Have Settings Specific to That Program
GGCS Introduction to Windows 10 Part 3: The Control Panel and Settings in Windows 10 Most programs and apps have settings specific to that program. For example, in a word processor such as Microsoft Word there are settings for margins, fonts, tabs, etc. If you have another word processor, it can have different settings for margins, fonts, etc. These specific settings only affect one program. The settings in the Control Panel and in Settings are more general and affect the whole computer and peripherals such as the mouse, keyboard, monitor and printers. For example, if you switch the right and left buttons on the mouse in the Control Panel or in Settings, they are switched for everything you click on. If you change the resolution of the monitor, it is changed for the desktop, menus, Word, Internet Explorer and Edge, etc. How to display the Control Panel 1. Right-click the Windows Start button or press the Windows key on the keyboard + X. 2. Click “Control Panel” on the popup menu as shown in the first screen capture. In Windows 10, many of the settings that once were in the Control Panel have moved to Settings. However, there are often links in Settings that take you back to the Control Panel and many other settings that still only exist in the Control Panel. Settings versus Control Panel is an evolving part of Windows design that started with Windows 8. It is not clear at this time whether the Control Panel will eventually go away or whether it will simply be used less frequently by most users. -

Security Update Notification
6605 19 ½ Mile Road Sterling Heights, MI 48314-1408 USA Tel: +1-586-254-0020 | Fax: +1-586-254-0053 [email protected] | www.sisconet.com Security Update Notification Microsoft Common Controls ActiveX Control (MSCOMCTL.OCX) Vulnerability 12 December 2012 (Links Updated 21 April 2016) NOTE: This Security Update Notification supersedes the version previously posted by SISCO dated 7 August 2012. An additional vulnerability was found by Microsoft requiring a new update. If you did not apply the update described in the 7 August 2012 notice you only need to apply the update described here. If you did apply the update described in the 7 August 2012 notice you will also need to apply the update from this notice. Microsoft Security Bulletin MS12‐060 disclosed a Critical Vulnerability in the Windows Common Controls that could allow remote code execution http://technet.microsoft.com/en‐us/security/bulletin/ms12‐060 . This ActiveX control is bundled with the Visual Basic 6 redistributable run‐time package that SISCO includes with our products. There is a security patch available from Microsoft for this vulnerability that many systems will receive under normal Windows update processes. HOWEVER, unless your computer has a Microsoft product installed (i.e. Office, SQL Server, BizTalk, etc.) that is checked during the Microsoft Windows Update process you will not receive an update. Microsoft’s Windows Update process will not detect the presence of this vulnerable control if you have not installed one or more of these other Microsoft products. The presence of the VB6 redistributable run‐time package that SISCO installs will not be detected by the Windows Update process if you do not have these other Microsoft products installed. -

Using Powershell Script to Manage the Windows 10 Update Policy
Using PowerShell Script to Manage the Windows 10 Update Policy Introduction The main objective of this article is to provide step-by-step instructions on how to use PowerShell script to set and modify the Windows update policy using a Windows bundle. The Windows 10 update settings can be easily re-configured using this bundle. This document includes the following information: • Prerequisites • Creating the Bundle • Deploying the Bundle • Logging Results Prerequisites Prior to deploying the bundle, you need be aware of the following: • The Windows bundle can be deployed only on Windows 10 devices. • Using the bundle, you can modify the update settings for Windows 10 devices. However, if the same setting is controlled by a group policy, the latter will prevail. • Prior to deploying the bundle, you must enable script execution by running the following command: Set-ExecutionPolicy <Unrestricted / AllSigned / RemoteSigned>). By default, the value set as Restricted. Creating the Bundle To create the Windows bundle: 1. In ZENworks Control Center, create a Windows bundle and add the modifyWindowsUpdateConfiguration.ps1, the settings.xml and the Setupconfig.ini files. For the Setupconfig.ini file, ensure that you specify the Destination Directory as %systemdrive%\Users\Default\AppData\Local\Microsoft\Windows\WSUS\ For information on how to create Windows bundles, see https://www.novell.com/documentation/zenworks-2017-update- 1/zen_cm_software_distribution/data/ba480hx.html 2. In the Bundles page, click the bundle that was created in the previous step and click Actions > Launch. 3. Click the Run Script Action link and in the Edit Action – Script dialog, specify the Action Name, Script File Name, Script Parameters and Path to Script Engine. -

GV-LPR Plugin Fence & Light GV-IP LPR Camera · GV-USB Dongle
Introduction GeoVision's License Plate Recognition is an effective and low-maintenance solution to ensure the security of parking lots, which are prone to crimes due to isolated and unstaffed corners. In addition to providing high-resolution video monitoring, the LPR solution can detect and recognize vehicle license plates upon motion or I/O trigger. When a GV-LPR device -- Edge GV-IP LPR Camera, GV-DSP LPR, or PC-based GV-DVR LPR / VMS LPR -- detects or recognizes license plates in video sources, it sends the LPR results to the access control system GV-ASManager. Access can be granted when the detected license plate numbers match the vehicles registered in GV-ASManager's database. Alarm notifications and playing back LPR results are also supported. Setting & Database GV-Software Video Source + Plate Recongition Edge GV-IP LPR Camera GV-ASManager Video Source + Plate Recongition Supporting up to 255 GV- Live View, Recording and LPR devices Playback · GV-DVR / NVR / VMS · GV-Recording Server Analog Camera GV-DSP LPR Video Source + Plate Recongition Live View · GV-ASManager GV-I/O Box · GV-Edge Recording Manager Analog Camera · GV-Center V2 GV-DVR LPR / GV-VMS LPR Event Text Message / Log PC installed with · GV-DVR / NVR / VMS · GV-Vital Sign Monitor · GV-LPR Plugin Fence & Light GV-IP LPR Camera · GV-USB Dongle Note: Edge GV-IP LPR Camera includes GV-LPR2811-DL / GV-LPR2800-DL / GV-LPR1200. -1- License Plate Recognition August 30, 2021 Available Versions of Machine Learning (ML) Recognition Engines Argentina Australia Austria Belgium Brazil Canada China Chile Columbia Croatia Czech Republic France Germany Hungary India Ireland Israel Italy Morocco Mexico Norway Poland Portugal Qatar Russia Slovakia South Africa Spain Taiwan UK USA Vietnam Note: There is a Global version which is suitable for most of the other countries. -
Documentation on Checking for Windows Updates with Nagios XI
The Industry Standard In Infrastructure Monitoring Nagios XI Checking For Windows Updates With Nagios XI Purpose This document describes how to use Nagios XI to monitor for high priority updates from Microsoft on a remote Windows host. This includes critical and security updates, service packs, and update rollups. Monitoring for updates from Microsoft with Nagios XI allows for automated checks to alert you when a new Window updates are released so you can apply them in a timely manor and ensure a safe and secure network environment. Target Audience This document is intended for use by Nagios XI Administrators who are interested in monitoring Windows machines to determine if they require updates to ensure their network infrastructure is safe, secure, and up- to-date. Prerequisites NSClient++ and NRPE You must have NSClient++ installed on the Windows machine you intend to monitor. NSClient++ itself does not know how to check the Windows updates status however it will be configured to execute a PowerShell script (a plugin) that will be able to check the Windows update status. NSClient++ must be configured to allow NRPE checks from the Nagios XI server. These specific documents will show you how to install NSClient++ and configure it to accept NRPE requests: • Installing The XI Windows Agent • Configuring The XI Windows Agent • Enabling the NRPE Listener in NSClient • Enabling the NRPE Listener in NSClient 0.4.x This guide is specifically aimed at NSClient++ v 0.4.x or newer, the previous 0.3.x version of NSClient++ is no longer supported by the developer of the application. -

Intelligent Security
Windows 10 Windows 10 Windows 10 Windows 10 Windows 10 Windows 10 commercial edition comparison Pro for Pro Business E3 E5 Workstation Per device Per device Per user Per user Per user Intelligent Security Threat protection Attack Surface Reduction ◑ ◑ ◕ ◕ ● Integrity enforcement of operating system boot up process Integrity enforcement of sensitive operating system components Advanced vulnerability and zero-day exploit mitigations Reputation based network protection for browsers Host-based firewall Ransomware mitigations Hardware based isolation for Microsoft Edge Application Control Device Control (e.g.: USB) Network protection for web-based threats Host intrusion prevention rules Enterprise management of hardware-based isolation for Microsoft Edge1 Customizable allow/deny lists (e.g.: IP/URL, Files, Certificates) Device-based conditional access Centrally manageable tamper protection of operating system Next Generation Protection ◑ ◑ ◑ ◑ ● Pre-execution emulation executables and scripts Runtime behavior monitoring In memory anomaly and behavior monitoring Machine learning and AI based protection from viruses and malware Published April 2020 v1909 1 Windows 10 Windows 10 Windows 10 Windows 10 Windows 10 Windows 10 commercial edition comparison Pro for Pro Business E3 E5 Workstation Per device Per device Per user Per user Per user Cloud protection for fastest responses to new/unknown web-based threats Protection from fileless based attacks Advanced machine learning and AI based protection for apex level viruses and malware threats Advanced -

Installing and Configuring Vmware Dynamic Environment Manager
Installing and Configuring VMware Dynamic Environment Manager VMware Dynamic Environment Manager 9.11 Installing and Configuring VMware Dynamic Environment Manager You can find the most up-to-date technical documentation on the VMware website at: https://docs.vmware.com/ VMware, Inc. 3401 Hillview Ave. Palo Alto, CA 94304 www.vmware.com © Copyright 2020 VMware, Inc. All rights reserved. Copyright and trademark information. VMware, Inc. 2 Contents About Installing and Configuring VMware Dynamic Environment Manager 6 1 Introduction to VMware Dynamic Environment Manager 7 Application Configuration Management 7 User Environment Settings 8 Personalization of Application and Windows Settings 8 Migration of Application Settings 9 Dynamic Configuration of the Desktop 9 2 VMware Dynamic Environment Manager Scenario Considerations 10 Using VMware Dynamic Environment Manager with Mandatory Profiles 10 Using VMware Dynamic Environment Manager with Roaming Profiles 11 Using VMware Dynamic Environment Manager with Local Profiles 12 3 Installation and Deployment Prerequisites 14 VMware Dynamic Environment Manager Infrastructure and Terminology 14 Overview of the VMware Dynamic Environment Manager Deployment 16 Infrastructure Requirements 16 VMware Dynamic Environment Manager Configuration Share 17 Profile Archives Share 18 Software Requirements 19 Registry Access Requirements 20 Licensing Requirements 20 4 Installing VMware Dynamic Environment Manager 21 Overview of the VMware Dynamic Environment Manager Deployment 22 Install VMware Dynamic Environment