Windows 10 Step by Step
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Office 365 Via SJU Microsoft Account
Office 365 via SJU Microsoft Account SJU email accounts are also Microsoft Accounts, allowing students to download and install Microsoft Office 2016 on up to five personal devices. To access the software, login to email through MySJU. Once logged into MySJU, click on the “Email” link, located in the top of the page. ** If you have any issues logging into Email or MySJU, Contact (718) 990-5000. ** 1. Once logged in to Outlook, access Office 365 menu by clicking in the upper left part of the page. 2. The Office 365 Installation page will appear at the top of the screen. CLICK on “INSTALL OFFICE”. The version of the installation that will appear will depend on the operating system that is being used at the time of login. If Microsoft Office for Mac is needed, the student must sign in to the website with a Mac. If the Windows version of Microsoft Office is needed, the student must sign in to the website with a Windows computer. 3. Steps on how to continue the installation will appear. If you do not see the button to click “Run.” You may have to check your Downloads folder to see if the installation has fully downloaded. Once it is completed, you can open it up to install. You must remain connected to the internet for the software to install. Office will be automatically activated with your SJU account when the install is finalized. 4. After installation is complete. Open up one of the programs, such as Microsoft Word to complete activation. Click on the prompts to get to the Sign-In page. -

Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C
Before the FEDERAL COMMUNICATIONS COMMISSION Washington, D.C. 20554 In the Matter of ) ) PN Comments – Accessibility of ) CG Docket No. 10-213 Communications Technologies ) To: Consumer & Governmental Affairs Bureau COMMENTS OF MICROSOFT CORPORATION Accessibility is a business imperative for Microsoft, as both a matter of compliance and an area ripe for innovation. We are investing in design principles and natural user interfaces that help individuals of all abilities,1 and innovating in touch, gesture, and speech recognition that can be used to improve communications services available to people with disabilities. Some of our innovations were not designed exclusively for accessibility, such as the work we’ve done on the Windows touch interface, or Bing’s voice-activated search for our Windows Phone digital personal assistant Cortana. Other innovation is focused on helping people with disabilities, such as Microsoft’s partnership with the UK non-profit “Guide Dogs for the Blind” to enable better independent mobility, which we discuss below. In implementing the Twenty-First Century Communications and Video Accessibility Act of 2010 (“CVAA”), the Commission has left space for such innovation to occur by avoiding overly prescriptive regulations and setting reasonable compliance deadlines that provide industry time to research break-through solutions. For a company like Microsoft, that is already investing 1 Microsoft, Digital Inclusion and Natural User Interface Technology: A Policy Framework, http://download.microsoft.com/download/C/1/A/C1AA2411-C3AE-4D21-8C46- F33CE49BBFCF/Digital-Inclusion-Natural-User-Interface-Technology.pdf. in accessibility solutions and offers a multitude of devices, software and services to a wide range of customers around the world, that space is key for us to best use our technological know-how to deliver accessibility advancements that benefit people with disabilities. -

NTFS • Windows Reinstallation – Bypass ACL • Administrators Privilege – Bypass Ownership
Windows Encrypting File System Motivation • Laptops are very integrated in enterprises… • Stolen/lost computers loaded with confidential/business data • Data Privacy Issues • Offline Access – Bypass NTFS • Windows reinstallation – Bypass ACL • Administrators privilege – Bypass Ownership www.winitor.com 01 March 2010 Windows Encrypting File System Mechanism • Principle • A random - unique - symmetric key encrypts the data • An asymmetric key encrypts the symmetric key used to encrypt the data • Combination of two algorithms • Use their strengths • Minimize their weaknesses • Results • Increased performance • Increased security Asymetric Symetric Data www.winitor.com 01 March 2010 Windows Encrypting File System Characteristics • Confortable • Applying encryption is just a matter of assigning a file attribute www.winitor.com 01 March 2010 Windows Encrypting File System Characteristics • Transparent • Integrated into the operating system • Transparent to (valid) users/applications Application Win32 Crypto Engine NTFS EFS &.[ßl}d.,*.c§4 $5%2=h#<.. www.winitor.com 01 March 2010 Windows Encrypting File System Characteristics • Flexible • Supported at different scopes • File, Directory, Drive (Vista?) • Files can be shared between any number of users • Files can be stored anywhere • local, remote, WebDav • Files can be offline • Secure • Encryption and Decryption occur in kernel mode • Keys are never paged • Usage of standardized cryptography services www.winitor.com 01 March 2010 Windows Encrypting File System Availibility • At the GUI, the availibility -

Dynamics NAV2013 Large Scale Hosting on Windows Azure
Microsoft Dynamics NAV Large scale hosting on 2013 R2 Windows Azure Whitepaper April 2014 Contents Introduction 4 Assumptions 4 Who is the audience of this whitepaper? 4 Windows Azure components that are needed to deploy a scalable Microsoft Dynamics NAV 2013 R2 with high availability 6 What is Windows Azure? 6 The Windows Azure SLA 6 The Windows Azure Cloud Service 6 Port-forwarding endpoints 6 Load-balancing endpoints 7 Availability sets 8 Scale 8 How to deploy Microsoft Dynamics NAV 2013 R2 for multitenancy 9 Deployment scripts on the product media 9 Certificates and SSL 9 URLs 10 Load Balancing Microsoft Dynamics NAV 11 Adding/Removing Tenants 15 Adding/Removing Microsoft Dynamics NAV servers 15 ClickOnce deployment of the Microsoft Dynamics NAV Windows client 16 Application code considerations 17 Upgrade 18 Backup 19 Monitoring 19 How to deploy SQL Server with high availability and what is supported by Microsoft Dynamics NAV 2013 R2 21 SQL Server Always-On Availability Groups 21 SQL Server Always-On Failover Clusters 21 SQL Server Database Mirror 21 SQL Azure 21 NAV Service Sample Scripts 22 Main scripts 22 Helper scripts 22 Helper DLL 22 Definitions 23 The scripts 27 Helper scripts 29 Scripts deployed to Microsoft Dynamics NAV Server 29 Folder structure on the provisioning machine 30 Folder structure on the server 30 How to get started 31 2 Large scale hosting on Windows Azure Whitepaper 3 Large scale hosting on Windows Azure Whitepaper Introduction This whitepaper describes in detail how to deploy Microsoft Dynamics NAV 2013 R2 on Windows Azure so you can serve a very large number of customers with high availability. -

Microsoft Security Intelligence Report
Microsoft Security Intelligence Report Volume 20 | July through December, 2015 This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. This document is provided “as-is.” Information and views expressed in this document, including URL and other Internet website references, may change without notice. You bear the risk of using it. Copyright © 2016 Microsoft Corporation. All rights reserved. The names of actual companies and products mentioned herein may be the trademarks of their respective owners. Authors Charlie Anthe Dana Kaufman Anthony Penta Cloud and Enterprise Security Azure Active Directory Team Safety Platform Nir Ben Zvi Nasos Kladakis Ina Ragragio Enterprise and Cloud Group Azure Active Directory Team Windows and Devices Group Patti Chrzan Daniel Kondratyuk Tim Rains Microsoft Digital Crimes Unit Azure Active Directory Team Commercial Communications Bulent Egilmez Andrea Lelli Paul Rebriy Office 365 - Information Windows Defender Labs Bing Protection Geoff McDonald Stefan Sellmer Elia Florio Windows Defender Labs Windows Defender Labs Windows Defender Labs Michael McLaughlin Mark Simos Chad Foster Identity Services Enterprise Cybersecurity Bing Group Nam Ng Roger Grimes Enterprise Cybersecurity Vikram Thakur Microsoft IT Group Windows Defender Labs Paul Henry Niall O'Sullivan Alex Weinert Wadeware LLC Microsoft Digital Crimes Unit Azure Active Directory Team Beth Jester Daryl Pecelj Terry Zink Windows Defender Microsoft IT Information -

Second Edition Microsoft Azure Essentials
Fundamentals of Azure Second Edition Microsoft Azure Essentials Michael Collier Robin Shahan PUBLISHED BY Microsoft Press A division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2016 by Michael Collier, Robin Shahan All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. ISBN: 978-1-5093-0296-3 Microsoft Press books are available through booksellers and distributors worldwide. If you need support related to this book, email Microsoft Press Support at [email protected]. Please tell us what you think of this book at http://aka.ms/tellpress. This book is provided “as-is” and expresses the author’s views and opinions. The views, opinions and information expressed in this book, including URL and other Internet website references, may change without notice. Some examples depicted herein are provided for illustration only and are fictitious. No real association or connection is intended or should be inferred. Microsoft and the trademarks listed at http://www.microsoft.com on the “Trademarks” webpage are trademarks of the Microsoft group of companies. All other marks are property of their respective owners. Acquisitions Editor: Devon Musgrave Developmental Editor: Carol Dillingham Editorial Production: Cohesion Copyeditor: Ann Weaver Cover: Twist Creative • Seattle To my wife, Sonja, and sons, Aidan and Logan; I love you more than words can express. I could not have written this book without your immense support and patience. —Michael S. Collier I dedicate this book to the many people who helped make this the best book possible by reviewing, discussing, and sharing their technical wisdom. -

How to Convert Desktop Apps to Universal Windows Platform Apps with Desktop Bridge
How to convert desktop apps to Universal Windows Platform apps with Desktop Bridge If you're looking to bring your traditional app to the Universal Windows Platform, this guide walks you through the steps to use the DesktopAppConverter to convert your app. On Windows 10, Microsoft is not only adding new features and making the operating system more secure, but it's also investing on making the Windows Store the single place for users to acquire apps. The caveat with the Windows Store is that it doesn't include support for distribution of traditional desktop applications -- you're only able to download Universal Windows Platform (UWP) apps. However, Microsoft is making some changes, and now thanks to Desktop Bridge, we're slowly starting to see desktop apps and tools available in the Store. What's Desktop Bridge? How does Desktop Bridge works? Things you need before converting an app How to prepare your computer to convert apps How to convert desktop apps into Windows Store apps How to install a converted app on Windows 10 What's Desktop Bridge? It's all part of an initiative called Project Centennial, which now you know as Desktop Bridge. The new approach is essentially a "bridge" that let developers take traditional desktop applications and convert them into Universal Windows Platform (modern) apps. The idea behind Desktop Bridge is that great apps take time and effort, and if they're already working, Microsoft doesn't want you to abandon that code. With Desktop Bridge, you can take your existing desktop application (Win32, WPF, and Windows Forms), make a little modification (if necessary), and bring that great code to the new platform, which can also take advantage of many new features. -

Snagit-Complete-Help-Guide-2020.Pdf
Snagit Help Version 2020.1 December 2019 Copyright © 2019 TechSmith Corporation. All rights reserved All rights reserved This manual, as well as the software described in it, is furnished under license and may be used or copied only in accordance with the terms of such license. The content of this manual is furnished for informational use only, is subject to change without notice and should not be construed as a commitment by TechSmith Corporation. TechSmith Corporation assumes no responsibility or liab- ility for any errors or inaccuracies that may appear in this manual. Trademarks All-In-One Capture, Camtasia, Camtasia Relay, Camtasia Studio, Coach’s Eye, Coach’s Eye +, DubIt, EnSharpen, Enterprise Wide, Jing, Knowmia, Morae, Rich Recording Technology (RRT), Screencast, Screencast.com, ScreenChomp, Show The World, SmartFocus, Snagit, TechSmith, TechSmith AppShow, TechSmith Fuse, TechSmith Loop, TechSmith Relay, TechSmith Screencast, TechSmith Smart Player, and TSCC are either registered marks or marks of TechSmith Corporation in the U.S. and/or other countries. This list is not a comprehensive list of all TechSmith Corporation marks. The absence of a name/mark or logo in this notice does not constitute a waiver of any intellectual prop- erty rights that TechSmith Corporation has established in any of its product, feature or service names/marks or logos. All other marks are the property of their respective owners. Snagit Help | 1 Table of Contents Table of Contents 2 What's New in Snagit 2020 10 Introduction to Capture 13 Open the Capture -
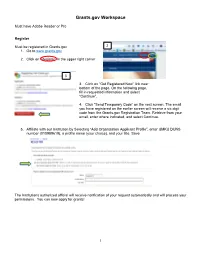
Grants.Gov Workspace
Grants.gov Workspace Must have Adobe Reader or Pro Register Must be registered in Grants.gov 2 1. Go to www.grants.gov 2. Click on “Register” in the upper right corner 3 3. Click on “Get Registered Now” link near bottom of the page. On the following page, fill in requested information and select “Continue”. 4. Click “Send Temporary Code” on the next screen. The email you have registered on the earlier screen will receive a six digit code from the Grants.gov Registration Team. Retrieve from your email, enter where indicated, and select Continue. 5. Affiliate with our Institution by Selecting “Add Organization Applicant Profile”, enter UMKU DUNS number (010989619), a profile name (your choice), and your title. Save. 5 The Institutions authorized official will receive notification of your request automatically and will process your permissions. You can now apply for grants! 1 Initiate Workspace Application Once you’re registered, on the Grants.gov home page you can now select Login, which is in the upper right corner next to Register. There are couple of ways you can get to the correct application forms. Within the guidelines for the funding opportunity announcement (FOA), you can click on “Go to Grants.gov” to download an application package. You can search for the FOA from “Search Grants” tab in Grants.gov. o Once you find it, click on the Opp Number o Then click on “Package” o Then click on “Apply” o To receive updates on this funding opportunity, Select Subscribe to Opportunity in the top right of this page. -
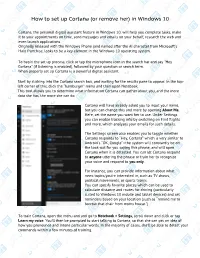
How to Set up Cortana (Or Remove Her) in Windows 10
How to set up Cortana (or remove her) in Windows 10 Cortana, the personal digital assistant feature in Windows 10, will help you complete tasks, make it to your appointments on time, send messages and emails on your behalf, research the web and even launch applications. Orignally released with the Windows Phone (and named after the AI character from Microsoft's Halo franchise, looks to be a key element in the Windows 10 operating system. To begin the set up process, click or tap the microphone icon in the search bar and say "Hey Cortana" (if listening is enabled), followed by your question or search term. When properly set up Cortana is a powerful digital assistant. Start by clicking into the Cortana search box, and waiting for the results pane to appear. In the top- left corner of this, click the “hamburger” menu and then open Notebook. This tool allows you to determine what information Cortana can gather about you, and the more data she has, the more she can do. Cortana will have already asked you to input your name, but you can change this and more by opening About Me. Here, set the name you want her to use. Under Settings you can enable tracking info by switching on Find flights and more, which analyses your emails for such details. The Settings screen also enables you to toggle whether Cortana responds to “Hey, Cortana” which is very similar to Android’s “OK, Google“–the system will constantly be on the look-out for you saying this phrase, and will open Cortana when it is detected. -

Introducing Windows Azure for IT Professionals
Introducing Windows ServerIntroducing Release 2012 R2 Preview Introducing Windows Azure For IT Professionals Mitch Tulloch with the Windows Azure Team PUBLISHED BY Microsoft Press A Division of Microsoft Corporation One Microsoft Way Redmond, Washington 98052-6399 Copyright © 2013 Microsoft Corporation All rights reserved. No part of the contents of this book may be reproduced or transmitted in any form or by any means without the written permission of the publisher. Library of Congress Control Number: 2013949894 ISBN: 978-0-7356-8288-7 Microsoft Press books are available through booksellers and distributors worldwide. If you need support related to this book, email Microsoft Press Book Support at [email protected]. Please tell us what you think of this book at http://www.microsoft.com/learning/booksurvey. Microsoft and the trademarks listed at http://www.microsoft.com/about/legal/en/us/IntellectualProperty/ Trademarks/EN-US.aspx are trademarks of the Microsoft group of companies. All other marks are property of their respective owners. The example companies, organizations, products, domain names, email addresses, logos, people, places, and events depicted herein are fictitious. No association with any real company, organization, product, domain name, email address, logo, person, place, or event is intended or should be inferred. This book expresses the author’s views and opinions. The information contained in this book is provided without any express, statutory, or implied warranties. Neither the authors, Microsoft Corporation, nor -

Graphical User Interface (Gui) Lab
GRAPHICAL USER INTERFACE (GUI) LAB This lab will guide you through the complex process of graphical user interface (GUI) creation. GUI’s are interfaces computer users invoke to make computer programs easier to use. They provide a graphical means to perform simple and complex operations or procedures. Computer programmers make most of their applications as GUIs so users are not required to learn computer programming languages. We each use GUIs on a daily basis. Any computer program that implements buttons or menus to perform tasks is GUI based. Some examples include; Microsoft Word, ArcMap, ENVI, S-Plus, etc. GUIs in IDL In IDL there are two ways to create GUIs; manual script generation (writing code line by line as we have done in the previous labs) or semi-automatic script generation (this process uses a GUI already built into IDL to generate GUIs (this will make more sense later in the lab)). Before we create a functional GUI we need to understand basic GUI architecture. GUIs are comprised of numerous widgets that interact to accomplish a task. Common widgets used in IDL include the base widget (widget_base), button widgets (widget_button), text widgets (widget_text), and label widgets (widget_label). MANUAL GUI CREATION Let’s create a simple GUI (manually) to display a few basic concepts. First we must create the base widget (the matrix within which all other widgets in the GUI are contained). 1. Use the widget_base function to create a base widget by typing the following code in the IDL editor window. ; creates a widget_base called base Pro simp_widg base = widget_base(XSIZE = 175, YSIZE =50, TITLE='A Simple Example') ;realize the widget widget_control, base, /REALIZE end The XSIZE and YSIZE keywords specify the horizontal and vertical size (in pixels) of the base widget, while the TITLE keyword creates a title for the widget.