32-Bit Virus Threats on 64-Bit Windows Atli Guðmundsson Senior Software Engineer Symantec Security Response
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Exploring the X64
Exploring the x64 Junichi Murakami Executive Officer, Director of Research Fourteenforty Research Institute, Inc. Who am I? • Junichi Murakami – @Fourteenforty Research Institute, Inc. – Both Windows and Linux kernel development – Reversing malware and P2P software, etc. – Speaker at: • Black Hat 2008 US and Japan, AVAR 2009, RSA Conference(2009-) – Instructor at Security & Programming Camp(2006-) 2 Environment • Windows 7 x64 Edition • Visual Studio 2008 • Windbg • IDA Pro Advanced – STD doesn’t support x64, an offering is needed! 4 Agenda • Windows x64 • ABI(Application Binary Interface) • API Hooking • Code Injection 5 Windows x64 • Native x64 and WoW64 • Virtual Address Space – 2^64 = 16 Exa Byte ( Exa: 10^18) – but, limited to 16TB by Microsoft • File/Registry reflection • New 64-bit APIs – IsWow64Process, GetNativeSystemInfo, etc. 6 ABI • Binary Format • Register • Calling Convention • Exception Handling • Systemcall(x64, WoW64) 11 Binary Format(Cont.) • Some fields were extended to 64-bits – IMAGE_NT_HEADERS.IMAGE_OPTIONAL_HEADER • ImageBase • SizeOfStackReserve • SizeOfStackCommit • SizeOfHeapReserve • SizeOfHeapCommit 13 Calling Convention • first 4 parameters are passed by RCX, RDX, R8, R9 – 5th and later are passed on the stack • caller allocates register home space on the stack • RAX is used for return values • leaf / non-leaf function – leaf function: never use stack – PE32+ contains non-leaf function’s information in its EXCEPTION DIRECTORY • Register’s volatility – volatile: RAX, RCX, RDX, R8-R11 15 Exception Handling • -

Through the Looking Glass: Webcam Interception and Protection in Kernel
VIRUS BULLETIN www.virusbulletin.com Covering the global threat landscape THROUGH THE LOOKING GLASS: and WIA (Windows Image Acquisition), which provides a WEBCAM INTERCEPTION AND still image acquisition API. PROTECTION IN KERNEL MODE ATTACK VECTORS Ronen Slavin & Michael Maltsev Reason Software, USA Let’s pretend for a moment that we’re the bad guys. We have gained control of a victim’s computer and we can run any code on it. We would like to use his camera to get a photo or a video to use for our nefarious purposes. What are our INTRODUCTION options? When we talk about digital privacy, the computer’s webcam The simplest option is just to use one of the user-mode APIs is one of the most relevant components. We all have a tiny mentioned previously. By default, Windows allows every fear that someone might be looking through our computer’s app to access the computer’s camera, with the exception of camera, spying on us and watching our every move [1]. And Store apps on Windows 10. The downside for the attackers is while some of us think this scenario is restricted to the realm that camera access will turn on the indicator LED, giving the of movies, the reality is that malware authors and threat victim an indication that somebody is watching him. actors don’t shy away from incorporating such capabilities A sneakier method is to spy on the victim when he turns on into their malware arsenals [2]. the camera himself. Patrick Wardle described a technique Camera manufacturers protect their customers by incorporating like this for Mac [8], but there’s no reason the principle into their devices an indicator LED that illuminates when can’t be applied to Windows, albeit with a slightly different the camera is in use. -

Minimum Hardware and Operating System
Hardware and OS Specifications File Stream Document Management Software – System Requirements for v4.5 NB: please read through carefully, as it contains 4 separate specifications for a Workstation PC, a Web PC, a Server and a Web Server. Further notes are at the foot of this document. If you are in any doubt as to which specification is applicable, please contact our Document Management Technical Support team – we will be pleased to help. www.filestreamsystems.co.uk T Support +44 (0) 118 989 3771 E Support [email protected] For an in-depth list of all our features and specifications, please visit: http://www.filestreamsystems.co.uk/document-management-specification.htm Workstation PC Processor (CPU) ⁴ Supported AMD/Intel x86 (32bit) or x64 (64bit) Compatible Minimum Intel Pentium IV single core 1.0 GHz Recommended Intel Core 2 Duo E8400 3.0 GHz or better Operating System ⁴ Supported Windows 8, Windows 8 Pro, Windows 8 Enterprise (32bit, 64bit) Windows 10 (32bit, 64bit) Memory (RAM) ⁵ Minimum 2.0 GB Recommended 4.0 GB Storage Space (Disk) Minimum 50 GB Recommended 100 GB Disk Format NTFS Format Recommended Graphics Card Minimum 128 MB DirectX 9 Compatible Recommended 128 MB DirectX 9 Compatible Display Minimum 1024 x 768 16bit colour Recommended 1280 x 1024 32bit colour Widescreen Format Yes (minimum vertical resolution 800) Dual Monitor Yes Font Settings Only 96 DPI font settings are supported Explorer Internet Minimum Microsoft Internet Explorer 11 Network (LAN) Minimum 100 MB Ethernet (not required on standalone PC) Recommended -

A Definitive Guide to Windows 10 Management: a Vmware Whitepaper
A Definitive Guide to Windows 10 Management: A VMware Whitepaper November 2015 Table of Contents Executive Summary.................................................................................................................3 Challenges with Windows Management..........................................................................5 How Windows 10 Differs........................................................................................................7 Windows 10 Management Features....................................................................................9 New Methods of Updates......................................................................................................10 New Methods of Enrollment and Device Provisioning................................................11 Unified Application Experiences.........................................................................................13 Domain Joined Management................................................................................................16 Application Delivery.............................................................................................................17 Universal Applications.........................................................................................................17 Classic Windows Applications.........................................................................................17 Cloud-based Applications.................................................................................................17 -

Experimental Evidence on Predatory Pricing Policies
A Service of Leibniz-Informationszentrum econstor Wirtschaft Leibniz Information Centre Make Your Publications Visible. zbw for Economics Edlin, Aaron S.; Roux, Catherine; Schmutzler, Armin; Thöni, Christian Working Paper Hunting unicorns? Experimental evidence on predatory pricing policies Working Paper, No. 258 Provided in Cooperation with: Department of Economics, University of Zurich Suggested Citation: Edlin, Aaron S.; Roux, Catherine; Schmutzler, Armin; Thöni, Christian (2017) : Hunting unicorns? Experimental evidence on predatory pricing policies, Working Paper, No. 258, University of Zurich, Department of Economics, Zurich, http://dx.doi.org/10.5167/uzh-138188 This Version is available at: http://hdl.handle.net/10419/173418 Standard-Nutzungsbedingungen: Terms of use: Die Dokumente auf EconStor dürfen zu eigenen wissenschaftlichen Documents in EconStor may be saved and copied for your Zwecken und zum Privatgebrauch gespeichert und kopiert werden. personal and scholarly purposes. Sie dürfen die Dokumente nicht für öffentliche oder kommerzielle You are not to copy documents for public or commercial Zwecke vervielfältigen, öffentlich ausstellen, öffentlich zugänglich purposes, to exhibit the documents publicly, to make them machen, vertreiben oder anderweitig nutzen. publicly available on the internet, or to distribute or otherwise use the documents in public. Sofern die Verfasser die Dokumente unter Open-Content-Lizenzen (insbesondere CC-Lizenzen) zur Verfügung gestellt haben sollten, If the documents have been made available under an Open gelten abweichend von diesen Nutzungsbedingungen die in der dort Content Licence (especially Creative Commons Licences), you genannten Lizenz gewährten Nutzungsrechte. may exercise further usage rights as specified in the indicated licence. www.econstor.eu University of Zurich Department of Economics Working Paper Series ISSN 1664-7041 (print) ISSN 1664-705X (online) Working Paper No. -

Measuring the Effectiveness of Generic Malware Models
San Jose State University SJSU ScholarWorks Master's Projects Master's Theses and Graduate Research Fall 2017 Measuring the Effectiveness of Generic Malware Models Naman Bagga San Jose State University Follow this and additional works at: https://scholarworks.sjsu.edu/etd_projects Part of the Computer Sciences Commons Recommended Citation Bagga, Naman, "Measuring the Effectiveness of Generic Malware Models" (2017). Master's Projects. 566. DOI: https://doi.org/10.31979/etd.8486-cfhx https://scholarworks.sjsu.edu/etd_projects/566 This Master's Project is brought to you for free and open access by the Master's Theses and Graduate Research at SJSU ScholarWorks. It has been accepted for inclusion in Master's Projects by an authorized administrator of SJSU ScholarWorks. For more information, please contact [email protected]. Measuring the Effectiveness of Generic Malware Models A Project Presented to The Faculty of the Department of Computer Science San Jose State University In Partial Fulfillment of the Requirements for the Degree Master of Science by Naman Bagga December 2017 ○c 2017 Naman Bagga ALL RIGHTS RESERVED The Designated Project Committee Approves the Project Titled Measuring the Effectiveness of Generic Malware Models by Naman Bagga APPROVED FOR THE DEPARTMENTS OF COMPUTER SCIENCE SAN JOSE STATE UNIVERSITY December 2017 Dr. Mark Stamp Department of Computer Science Dr. Jon Pearce Department of Computer Science Dr. Thomas Austin Department of Computer Science ABSTRACT Measuring the Effectiveness of Generic Malware Models by Naman Bagga Malware detection based on machine learning techniques is often treated as a problem specific to a particular malware family. In such cases, detection involves training and testing models for each malware family. -

Programming Model Intel Itanium 64
11/11/2003 64-bit computing AMD Opteron 64 Application of Win32 Executable File Legacy 64 bit platforms Inbuilt 128-bit bus DDR memory controller with memory bandwidth speed up to 5.3GB/s. Infectors on Intel Itanium and AMD Benefits of 64-bit processors Opteron Based Win64 Systems Use of hyper transport protocol, “glueless” architecture. Oleg Petrovsky and Shali Hsieh Increased integer dynamic range Computer Associates International Inc. Available in up to 8 way configuration with the clock speeds 1 Computer Associates Plaza, Islandia, NY 11749, Much larger addressable memory space of 1.4 GHz, 1.6 GHz and 1.8 GHz . USA Benefits to database, scientific and cryptography Reuses already familiar 32-bit x86 instruction set and applications extends it to support 64-bit operands, registers and memory pointers. AMD64 Programming Model AMD64: Programming model Intel Itanium 64 X86 32-64 64 bit Itanium line of processors is being developed by Intel XMM8 X86 80-Bit Extends general use registers to 64-bit, adds additional eight 64-Bit X87 general purpose 64-bit registers. Itanium - 800 MHz, no on die L3 cache, Itanium 2 - 1GHz, RAX EAX AX 3MB L3 on die, Itanium 2003 (Madison) - 1.5 GHz, 6MB L3 on die cache, 410M transistors, largest integration on a RBX Reuses x86 instruction set. single silicon crystal today. XMM15 RCX Runs 32-bit code without emulation or translation to a native Itanium line of processors utilizes more efficient and robust XMM0 than legacy x86 instruction set architecture F instruction set. R8 L A Itanium has to use x86-to-IA-64 decoder a specifically Minimizes learning curve. -
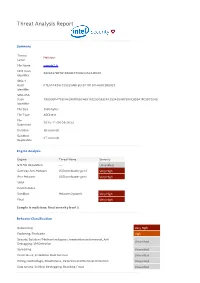
Sample2.Js Malware Summary
Threat Analysis Report Summary Threat Malicious Level File Name sample2.js MD5 Hash 580E637B97B16698CC750B445223D5C0 Identifier SHA-1 Hash 07E507426F72522DABFECF91181D7F64DC3B8D23 Identifier SHA-256 Hash 790999F47B2FA4396FF6B0A6916E295D832A12B3495A87590C859A1FE9D73245 Identifier File Size 3586 bytes File Type ASCII text File 2015-11-06 09:26:23 Submitted Duration 38 seconds Sandbox 27 seconds Replication Engine Analysis Engine Threat Name Severity GTI File Reputation --- Unverified Gateway Anti-Malware JS/Downloader.gen.f Very High Anti-Malware JS/Downloader.gen.f Very High YARA Custom Rules Sandbox Malware.Dynamic Very High Final Very High Sample is malicious: f inal severit y level 5 Behavior Classif icat ion Networking Very High Exploiting, Shellcode High Security Solution / Mechanism bypass, termination and removal, Anti Unverified Debugging, VM Detection Spreading Unverified Persistence, Installation Boot Survival Unverified Hiding, Camouflage, Stealthiness, Detection and Removal Protection Unverified Data spying, Sniffing, Keylogging, Ebanking Fraud Unverified Dynamic Analysis Action Severity Malware behavior: networking activities from non-executable file Very High ATTENTION: connection made to a malicious website (see Web/URL Very High reputation for details) Detected suspicious Java Script content High Downloaded data from a webserver Low Modified INTERNET_OPTION_CONNECT_RETRIES: number of times that Low WinInet attempts to resolve and connect to a host Connected to a specific service provider Low Cracks a URL into its component -
Flare-On 5: Challenge 7 Solution – Worldofwarcraft.Exe
Flare-On 5: Challenge 7 Solution – WorldOfWarcraft.exe Challenge Author: Ryan Warns Summary This challenge implements a 32-bit Windows binary meant to run in a Windows on Windows (WOW) environment. Analysis I often start my analysis of samples by quickly skimming the output of static analysis tools and looking through IDA. Performing basic static analysis on the binary we see that WorldOfWarcraft.exe is a simple 32-bit DLL. Running strings.exe on this binary shows us several strings that look like they might be related to the key. USER32 WS2_32 %[email protected] Cannot read payload! n1ght_4lve$_R_c00L.bin A_l1ttl3_P1C_0f_h3aV3n RSDS R:\objchk_win7_x86\i386\WorldOfWarcraft.pdb Figure 1 - strings in WorldOfWarcraft.exe Opening the binary in IDA we can see that the binary doesn’t appear to implement much in the way of functionality, with the main function only calling 3 subroutines. The subroutine at address 0x1001A60 contains references to our strings of interest. FireEye, Inc., 1440 McCarthy Blvd., Milpitas, CA 95035 | +1 408.321.6300 | +1 877.FIREEYE (347.3393) | [email protected] | www.FireEye.com 1 Figure 2 - Decompilation of function using interesting strings I’ve cleaned up the decompilation in the screenshot above to be slightly more accurate. Quickly skimming sub_1001910 reveals that this function grabs the contents of a file, so it looks like sub_0x1001A60 will read the file n1ght_4lve$_R_c00L.bin and XOR the contents against the string A_l1ttl3_P1C_0f_h3aV3n. The result of this operation is compared to a static array on the stack, and if the two match the sample will print our key. -

Copyrighted Material
Index Numerics Address Resolution Protocol (ARP), 1052–1053 admin password, SOHO network, 16-bit Windows applications, 771–776, 985, 1011–1012 900, 902 Administrative Tools window, 1081–1083, 32-bit (x86) architecture, 124, 562, 769 1175–1176 64-bit (x64) architecture, 124, 562, 770–771 administrative tools, Windows, 610 administrator account, 1169–1170 A Administrators group, 1171 ADSL (Asynchronous Digital Subscriber Absolute Software LoJack feature, 206 Line), 1120 AC (alternating current), 40 Advanced Attributes window, NTFS AC adapters, 311–312, 461, 468–469 partitions, 692 Accelerated Graphics Port (AGP), 58 Advanced Computing Environment (ACE) accelerated video cards (graphics initiative, 724 accelerator cards), 388 Advanced Confi guration and Power access points, wireless, 996, 1121 Interface (ACPI) standard, 465 access time, hard drive, 226 Advanced Graphics Port (AGP) card, access tokens, 1146–1147 391–392 Account Operators group, 1172 Advanced Graphics Port (AGP) port, 105 ACE (Advanced Computing Environment) Advanced Host Controller Interface (AHCI), initiative, 724 212–213 ACPI (Advanced Confi guration and Power Advanced Micro Devices (AMD), 141–144 Interface) standard, 465 Advanced Packaging Tool (APT), 572 Action Center, 1191–1192 Advanced Power Management (APM) Active Directory Database, 1145–1146, 1183 standard, 465 active heat sink, 150 Advanced Programmable Interrupt active matrix display, LCD (thin-fi lm Controller (APIC), 374 transistor (TFT) display), 470 Advanced RISC Computing Specifi cation active partition, 267, -

Download Deploying Windows 7, Essential Guidance
FROM THE Windows® 7 Resource Kit Mitch Tulloch, Tony Northrup, Jerry Honeycutt, Ed Wilson, and the Windows 7 Team at Microsoft I Chapter 3 Deployment Platform .............................................. 85 I Chapter 4 Planning Deployment ............................................ 113 I Chapter 5 Testing Application Compatability ........................... 139 I Chapter 6 Developing Disk Images ......................................... 179 I Chapter 7 Migrating User State Data ...................................... 223 I Chapter 8 Deploying Applications .......................................... 247 I Chapter 9 Preparing Windows PE ........................................... 273 I Chapter 10 Confi guring Windows Deployment Services .............. 293 I Chapter 11 Using Volume Activation ........................................ 335 I Chapter 12 Deploying with Microsoft Deployment Toolkit ........... 355 DEPLOYING WINDOWS 7 83 Chapter 3 Deployment Platform n Tools Introduction 85 n Windows 7 Deployment Terminology 87 n Platform Components 89 n Deployment Scenarios 99 n Understanding Setup 101 n Basic Deployment Process 105 n Microsoft Deployment Toolkit Process 107 n Summary 110 n Additional Resources 111 uilding on technology that the Windows Vista operating system introduced, Windows 7 Bdeployment technology has evolved significantly since Windows XP Professional . For example, it supports file-based disk imaging to make high-volume deployments quicker, more efficient, and more cost effective . The Windows 7 operating system also provides -

Hardening Windows 2000
Hardening Windows 2000 Philip Cox ([email protected]) Version 1.3 March 14, 2002 Abstract Determining what steps need to be taken to secure a system is one of the most frustrating things that system administrators have to do. This white paper provides a method for getting a Win2K server to a “secure” baseline. From this baseline you can work forward to install additional services. The focus of this white paper is on the Win2K server, but much of the information is applicable to Win2K Professional as well. This paper is excerpted and modified from Chapter 21 of the “Windows 2000 Security Handbook” (ISBN: 0-07- 212433-4, copyright Osborne/McGraw-Hill) authored by Phil Cox and Tom Sheldon (www.windows2000securityhandbook.com). Original material and content © Osborne/McGraw-Hill, 2000-2001. Supplemental material and updates © SystemExperts Corporation, 1995 - 2002. All rights reserved. All trademarks used herein are the property of their respective owners. Original material and content © Osborne/McGraw-Hill, 2000-2001. Supplemental material and updates © SystemExperts Corporation, 1995 - 2001. Table of Contents Abstract......................................................................................................................................................................1 Table Of Contents......................................................................................................................................................2 The Requirements ......................................................................................................................................................3