Linux History
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

WIKINOMICS How Mass Collaboration Changes Everything
WIKINOMICS How Mass Collaboration Changes Everything EXPANDED EDITION Don Tapscott and Anthony D. Williams Portfolio Praise for Wikinomics “Wikinomics illuminates the truth we are seeing in markets around the globe: the more you share, the more you win. Wikinomics sheds light on the many faces of business collaboration and presents a powerful new strategy for business leaders in a world where customers, employees, and low-cost producers are seizing control.” —Brian Fetherstonhaugh, chairman and CEO, OgilvyOne Worldwide “A MapQuest–like guide to the emerging business-to-consumer relation- ship. This book should be invaluable to any manager—helping us chart our way in an increasingly digital world.” —Tony Scott, senior vice president and chief information officer, The Walt Disney Company “Knowledge creation happens in social networks where people learn and teach each other. Wikinomics shows where this phenomenon is headed when turbocharged to engage the ideas and energy of customers, suppli- ers, and producers in mass collaboration. It’s a must-read for those who want a map of where the world is headed.” —Noel Tichy, professor, University of Michigan and author of Cycle of Leadership “A deeply profound and hopeful book. Wikinomics provides compelling evidence that the emerging ‘creative commons’ can be a boon, not a threat to business. Every CEO should read this book and heed its wise counsel if they want to succeed in the emerging global economy.” —Klaus Schwab, founder and executive chairman, World Economic Forum “Business executives who want to be able to stay competitive in the future should read this compelling and excellently written book.” —Tiffany Olson, president and CEO, Roche Diagnostics Corporation, North America “One of the most profound shifts transforming business and society in the early twenty-first century is the rapid emergence of open, collaborative innovation models. -

The Application Usage and Risk Report an Analysis of End User Application Trends in the Enterprise
The Application Usage and Risk Report An Analysis of End User Application Trends in the Enterprise 8th Edition, December 2011 Palo Alto Networks 3300 Olcott Street Santa Clara, CA 94089 www.paloaltonetworks.com Table of Contents Executive Summary ........................................................................................................ 3 Demographics ............................................................................................................................................. 4 Social Networking Use Becomes More Active ................................................................ 5 Facebook Applications Bandwidth Consumption Triples .......................................................................... 5 Twitter Bandwidth Consumption Increases 7-Fold ................................................................................... 6 Some Perspective On Bandwidth Consumption .................................................................................... 7 Managing the Risks .................................................................................................................................... 7 Browser-based Filesharing: Work vs. Entertainment .................................................... 8 Infrastructure- or Productivity-Oriented Browser-based Filesharing ..................................................... 9 Entertainment Oriented Browser-based Filesharing .............................................................................. 10 Comparing Frequency and Volume of Use -

Dennis Brylow in Theory, Simulating an Operating System Is the Same As the Real Thing. in Practice, It Is N
Experimental Operating System Lab on a Dime Dennis Brylow Department of Mathematics, Statistics and Computer Science In theory, simulating an Operating System is the same as the real thing. In practice, it is not. Setting up specialized Operating System Laboratory hardware usually requires more time, money, and space than most schools can afford. Marquette©s Systems Lab has concentrated specifically on developing a scalable, duplicable design for an Experimental Operating System Laboratory environment with minimal cost and very low space requirements. Our Experimental Operating Systems Laboratory serves as a target platform in undergraduate courses on Hardware Systems (COSC 065), Operating Systems (COSC 125 and COEN 183), Embedded Operating Systems (COSC 195) and Compiler Construction (COSC 170). Coming Soon: Additional modules for coursework in Embedded and Realtime Systems, Networking protocol stacks, Wireless Networking, and Internetworking . http://www.mscs.mu.edu/~brylow/xinu/ XINU in the 21st Century Purdue University©s XINU Operating System has been successfully deployed in classrooms, research labs, and commercial products for more than 20 years. Marquette University presents a new reimplementation of XINU, targeted to modern RISC architectures, written in ANSI-compliant C, and particularly well-suited to embedded platforms with scarce resources. Special Purpose Serial Consoles XINU Backends Serial Annex (optional) Private Network Marquette©s Systems Lab General Purpose runs XINU on inexpensive Laboratory Workstations wireless routers containing XINU the Embedded MIPS32 Server processor. Production Network XINU Backends XINU Server XINU Frontends Backend targets upload student kernel General purpose server with multiple General purpose computer laboratory over private network on boot, run O/S network interfaces manages a private workstations can compile the XINU directly. -

Emerging Trends in Management, IT and Education ISBN No.: 978-87-941751-2-4
Emerging Trends in Management, IT and Education ISBN No.: 978-87-941751-2-4 Paper 3 A STUDY ON REINVENTION AND CHALLENGES OF IBM Kiran Raj K. M1 & Krishna Prasad K2 1Research Scholar College of Computer Science and Information Science, Srinivas University, Mangalore, India 2 College of Computer Science and Information Science, Srinivas University, Mangalore, India E-mail: [email protected] Abstract International Business Machine Corporation (IBM) is one of the first multinational conglomerates to emerge in the US-headquartered in Armonk, New York. IBM was established in 1911 in Endicott, New York, as Computing-Tabulating-Recording Company (CTR). In 1924, CTR was renamed IBM. Big Blue has been IBM's nickname since 19 80. IBM stared with the production of scales, punch cards, data processors and time clock now produce and sells computer hardware and software, middleware, provides hosting and consulting services.It has a worldwide presence, operating in over 175 nations with 3,50,600 staff with $79. 6 billion in annual income (Dec 2018). It is currently competing with Microsoft, Google, Apple, and Amazon. 2012 to 2017 was tough time for IBM, although it invests in the field of research where it faced challenges while trying to stay relevant in rapidly changing Tech-Market. While 2018 has been relatively better and attempting to regain its place in the IT industry. With 3,000 scientists, it invests 7% of its total revenue to Research & Development in 12 laboratories across 6 continents. This resulted in the U.S. patent leadership in IBM's 26th consecutive year. In 2018, out of the 9,100 patents that granted to IBM 1600 were related to Artificial Intelligence and 1,400 related to cyber-security. -
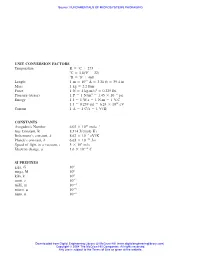
UNIT CONVERSION FACTORS Temperature K C 273 C 1.8(F 32
Source: FUNDAMENTALS OF MICROSYSTEMS PACKAGING UNIT CONVERSION FACTORS Temperature K ϭ ЊC ϩ 273 ЊC ϭ 1.8(ЊF Ϫ 32) ЊR ϭ ЊF ϩ 460 Length 1 m ϭ 1010 A˚ ϭ 3.28 ft ϭ 39.4 in Mass 1 kg ϭ 2.2 lbm Force 1 N ϭ 1 kg-m/s2 ϭ 0.225 lbf Pressure (stress) 1 P ϭ 1 N/m2 ϭ 1.45 ϫ 10Ϫ4 psi Energy 1 J ϭ 1W-sϭ 1 N-m ϭ 1V-C 1Jϭ 0.239 cal ϭ 6.24 ϫ 1018 eV Current 1 A ϭ 1 C/s ϭ 1V/⍀ CONSTANTS Avogadro’s Number 6.02 ϫ 1023 moleϪ1 Gas Constant, R 8.314 J/(mole-K) Boltzmann’s constant, k 8.62 ϫ 10Ϫ5 eV/K Planck’s constant, h 6.63 ϫ 10Ϫ33 J-s Speed of light in a vacuum, c 3 ϫ 108 m/s Electron charge, q 1.6 ϫ 10Ϫ18 C SI PREFIXES giga, G 109 mega, M 106 kilo, k 103 centi, c 10Ϫ2 milli, m 10Ϫ3 micro, 10Ϫ6 nano, n 10Ϫ9 Downloaded from Digital Engineering Library @ McGraw-Hill (www.digitalengineeringlibrary.com) Copyright © 2004 The McGraw-Hill Companies. All rights reserved. Any use is subject to the Terms of Use as given at the website. Source: FUNDAMENTALS OF MICROSYSTEMS PACKAGING CHAPTER 1 INTRODUCTION TO MICROSYSTEMS PACKAGING Prof. Rao R. Tummala Georgia Institute of Technology ................................................................................................................. Design Environment IC Thermal Management Packaging Single Materials Chip Opto and RF Functions Discrete Passives Encapsulation IC Reliability IC Assembly Inspection PWB MEMS Board Manufacturing Assembly Test Downloaded from Digital Engineering Library @ McGraw-Hill (www.digitalengineeringlibrary.com) Copyright © 2004 The McGraw-Hill Companies. -

Using TOST in Teaching Operating Systems and Concurrent Programming Concepts
Advances in Science, Technology and Engineering Systems Journal Vol. 5, No. 6, 96-107 (2020) ASTESJ www.astesj.com ISSN: 2415-6698 Special Issue on Multidisciplinary Innovation in Engineering Science & Technology Using TOST in Teaching Operating Systems and Concurrent Programming Concepts Tzanko Golemanov*, Emilia Golemanova Department of Computer Systems and Technologies, University of Ruse, Ruse, 7020, Bulgaria A R T I C L E I N F O A B S T R A C T Article history: The paper is aimed as a concise and relatively self-contained description of the educational Received: 30 July, 2020 environment TOST, used in teaching and learning Operating Systems basics such as Accepted: 15 October, 2020 Processes, Multiprogramming, Timesharing, Scheduling strategies, and Memory Online: 08 November, 2020 management. TOST also aids education in some important IT concepts such as Deadlock, Mutual exclusion, and Concurrent processes synchronization. The presented integrated Keywords: environment allows the students to develop and run programs in two simple programming Operating Systems languages, and at the same time, the data in the main system tables can be monitored. The Concurrent Programming paper consists of a description of TOST system, the features of the built-in programming Teaching Tools languages, and demonstrations of teaching the basic Operating Systems principles. In addition, some of the well-known concurrent processing problems are solved to illustrate TOST usage in parallel programming teaching. 1. Introduction • Visual OS simulators This paper is an extension of work originally presented in 29th The systems from the first group (MINIX [2], Nachos [3], Xinu Annual Conference of the European Association for Education in [4], Pintos [5], GeekOS [6]) run on real hardware and are too Electrical and Information Engineering (EAEEIE) [1]. -

DB2 10.5 with BLU Acceleration / Zikopoulos / 349-2
Flash 6X9 / DB2 10.5 with BLU Acceleration / Zikopoulos / 349-2 DB2 10.5 with BLU Acceleration 00-FM.indd 1 9/17/13 2:26 PM Flash 6X9 / DB2 10.5 with BLU Acceleration / Zikopoulos / 349-2 00-FM.indd 2 9/17/13 2:26 PM Flash 6X9 / DB2 10.5 with BLU Acceleration / Zikopoulos / 349-2 DB2 10.5 with BLU Acceleration Paul Zikopoulos Sam Lightstone Matt Huras Aamer Sachedina George Baklarz New York Chicago San Francisco Athens London Madrid Mexico City Milan New Delhi Singapore Sydney Toronto 00-FM.indd 3 9/17/13 2:26 PM Flash 6X9 / DB2 10.5 with BLU Acceleration / Zikopoulos / 349-2 McGraw-Hill Education books are available at special quantity discounts to use as premiums and sales promotions, or for use in corporate training programs. To contact a representative, please visit the Contact Us pages at www.mhprofessional.com. DB2 10.5 with BLU Acceleration: New Dynamic In-Memory Analytics for the Era of Big Data Copyright © 2014 by McGraw-Hill Education. All rights reserved. Printed in the Unit- ed States of America. Except as permitted under the Copyright Act of 1976, no part of this publication may be reproduced or distributed in any form or by any means, or stored in a database or retrieval system, without the prior written permission of pub- lisher, with the exception that the program listings may be entered, stored, and exe- cuted in a computer system, but they may not be reproduced for publication. All trademarks or copyrights mentioned herein are the possession of their respective owners and McGraw-Hill Education makes no claim of ownership by the mention of products that contain these marks. -
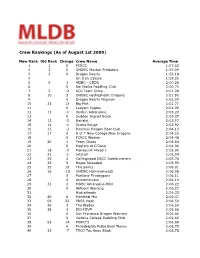
Ranking System.Xlsx
Crew Rankings (As of August 1st 2009) New Rank Old Rank Change Crew Name Average Time 1 1 0 FCRCC 1:57.62 2 2 0 OHDBC Mayfair Predators 1:59.09 3 3 0 Dragon Beasts 1:59.18 4 On S'en Calisse 1:59.25 561ADBC - CSDC 2:00.26 6 0 Kai Ikaika Paddling Club 2:00.73 7 5 -2 SCC Team Chiro 2:01.28 8 10 2 OHDBC Hydrophobic Dragons 2:01.90 9 0 Dragon Hearts Magnum 2:02.59 10 23 13 Big Fish 2:02.77 11 0 Laoyam Eagles 2:02.99 12 11 -1 Verdun Adrenaline 2:03.22 13 0 Sudden Impact Black 2:03.37 14 12 -2 Hanalei 2:03.57 15 14 -1 Scotia Rouge 2:03.92 16 13 -3 Piranhas Dragon Boat Club 2:04.13 17 17 0 U of T New College New Dragons 2:04.25 18 0 FCRCC Women 2:04.48 19 20 1 Team Chaos 2:04.84 20 0 Masters of D'Zone 2:04.96 21 19 -2 Manayunk Mixed I 2:05.00 22 21 -1 Jetstart 2:05.04 23 25 2 Collingwood DBCC Sidelaunchers 2:05.76 24 29 5 Mojos Reloaded 2:05.95 25 35 10 The Saints 2:06.01 26 16 -10 OHDBC Hammerheads 2:06.08 27 0 Portland Firedragons 2:06.11 28 0 Anniemaniacs 2:06.14 29 31 2 MDBC Adrenaline-HRV 2:06.22 30 0 Without Warning 2:06.27 31 HydraHeads 2:06.33 32 40 8 Montreal Mix 2:06.47 33 56 23 PDBC Heat 2:06.50 34 36 2 The Blades 2:06.50 35 38 3 DCH DVP 2:06.56 36 0 San Francisco Dragon Warriors 2:06.60 37 0 Victoria College Paddling Club 2:06.66 38 52 14 MOFO''s 2:06.68 39 0 Philadelphia Police Boat Teams 2:06.75 40 33 -7 TECO Tan Anou Black 2:06.78 41 41 0 3R Dragon - Mixed 2:07.19 42 37 -5 TECO Tan Anou Red 2:07.20 43 49 6 University Elite Force 2:07.27 44 39 -5 Mayfair Warriors 2:07.39 45 51 6 Hydroblades 2:07.39 46 24 -22 PDBC 2:07.79 47 0 UC -

Case Studies on Innovation
I N N O V A A T I O N 1 www.ibscdc.org ITC’s E-Choupal: A Mirage of the American studios declared in May 2007 Immelt charted his own leadership style Poor? that it had obtained the rights for and brought about a cultural revolution in developing a theme park based on the GE. Expectations were high and the E-Choupal is a novel initiative of ITC extremely successful character of the challenges were many. Immelt had to face Limited (ITC), an Indian conglomerate, popular culture Harry Potter in US, UK several challenges. He had to provide to improve its marketing channel in and all over the world. Walt Disney parks leadership and lend vision to a large, diverse agriculture. It has its roots in Project and resorts have also tried to get the rights conglomerate like GE in the post 9/11 Symphony – a pilot project launched in for Harry Potter theme park but failed to volatile global business scenario. He also 1999 to organise ITC’s agri business. The strike a deal with the creator of the Harry had to shift the company’s focus towards business model was designed to Potter character, J.K. Rowling. Universal innovation and customer centricity in accommodate farmers, intermediaries in and Disney have been competing in the addition to posting continued growth in a the traditional model and the company entertainment industry for many years, and sluggish economy. The case study discusses through information technology. The main Walt Disney had been a leader in theme Immelt’s innovation and customer centric objective of e-Choupal is dissemination and parks. -

Porting the Embedded Xinu Operating System to the Raspberry Pi Eric Biggers Macalester College, [email protected]
Macalester College DigitalCommons@Macalester College Mathematics, Statistics, and Computer Science Mathematics, Statistics, and Computer Science Honors Projects 5-2014 Porting the Embedded Xinu Operating System to the Raspberry Pi Eric Biggers Macalester College, [email protected] Follow this and additional works at: https://digitalcommons.macalester.edu/mathcs_honors Part of the OS and Networks Commons, Software Engineering Commons, and the Systems Architecture Commons Recommended Citation Biggers, Eric, "Porting the Embedded Xinu Operating System to the Raspberry Pi" (2014). Mathematics, Statistics, and Computer Science Honors Projects. 32. https://digitalcommons.macalester.edu/mathcs_honors/32 This Honors Project - Open Access is brought to you for free and open access by the Mathematics, Statistics, and Computer Science at DigitalCommons@Macalester College. It has been accepted for inclusion in Mathematics, Statistics, and Computer Science Honors Projects by an authorized administrator of DigitalCommons@Macalester College. For more information, please contact [email protected]. MACALESTER COLLEGE HONORS PAPER IN COMPUTER SCIENCE Porting the Embedded Xinu Operating System to the Raspberry Pi Author: Advisor: Eric Biggers Shilad Sen May 5, 2014 Abstract This thesis presents a port of a lightweight instructional operating system called Em- bedded Xinu to the Raspberry Pi. The Raspberry Pi, an inexpensive credit-card-sized computer, has attracted a large community of hobbyists, researchers, and educators since its release in 2012. However, the system-level software running on the Raspberry Pi has been restricted to two ends of a spectrum: complex modern operating systems such as Linux at one end, and very simple hobbyist operating systems or simple “bare-metal” programs at the other end. -

Real-Time Transport of Internet Telephony Service Utilizing Embedded Resource-Constrained Systems Kyle Persohn Marquette University
Marquette University e-Publications@Marquette Master's Theses (2009 -) Dissertations, Theses, and Professional Projects Real-Time Transport of Internet Telephony Service Utilizing Embedded Resource-Constrained Systems Kyle Persohn Marquette University Recommended Citation Persohn, Kyle, "Real-Time Transport of Internet Telephony Service Utilizing Embedded Resource-Constrained Systems" (2012). Master's Theses (2009 -). Paper 162. http://epublications.marquette.edu/theses_open/162 REAL-TIME TRANSPORT OF INTERNET TELEPHONY SERVICE UTILIZING EMBEDDED RESOURCE-CONSTRAINED SYSTEMS by Kyle Persohn A Thesis Submitted to the Faculty of the Graduate School, Marquette University, in Partial Fulfillment of the Requirements for the Degree of Master of Science Milwaukee, Wisconsin August 2012 ABSTRACT REAL-TIME TRANSPORT OF INTERNET TELEPHONY SERVICE UTILIZING EMBEDDED RESOURCE-CONSTRAINED SYSTEMS Kyle Persohn Marquette University, 2012 This thesis presents a real-time framework for resource-constrained devices that improves the listening quality of Voice over Internet Protocol calls transported over congested networks. Many VoIP standards and implementations exist, but gaps in the design space encourage further exploration that previous work fails to address. We describe an experimental hardware platform that expands upon a previous design to accommodate technical research and educational needs. Our framework, based on the Real-Time Transport Protocol, integrates closely with existing software constructs available in the Embedded Xinu operating system. We offer features derived from RTP by means of a kernel device that alleviates an application from directly interacting with the underlying protocol. An example application based on Xinu's RTP implementation demonstrates measurable robustness to packet loss and delay variation (jitter)|adverse conditions affecting networks used for VoIP, such as the Internet. -

Proving Safety Properties of Software Kang Gui Iowa State University
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Digital Repository @ Iowa State University Iowa State University Capstones, Theses and Graduate Theses and Dissertations Dissertations 2012 Proving safety properties of software Kang Gui Iowa State University Follow this and additional works at: https://lib.dr.iastate.edu/etd Part of the Computer Engineering Commons, and the Computer Sciences Commons Recommended Citation Gui, Kang, "Proving safety properties of software" (2012). Graduate Theses and Dissertations. 12335. https://lib.dr.iastate.edu/etd/12335 This Dissertation is brought to you for free and open access by the Iowa State University Capstones, Theses and Dissertations at Iowa State University Digital Repository. It has been accepted for inclusion in Graduate Theses and Dissertations by an authorized administrator of Iowa State University Digital Repository. For more information, please contact [email protected]. Proving safety properties of software by Kang Gui A dissertation submitted to the graduate faculty in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY Major: Computer Engineering Program of Study Committee: Suraj C. Kothari, Major Professor Srinivas Aluru Tien Nguyen Manimaran Govindarasu Samik Basu Iowa State University Ames, Iowa 2012 Copyright c Kang Gui, 2012. All rights reserved. ii DEDICATION To my parents Yousheng Gui and Jianping Chang iii TABLE OF CONTENTS LIST OF TABLES . vi LIST OF FIGURES . vii ACKNOWLEDGEMENTS . ix ABSTRACT . x CHAPTER 1. OVERVIEW . 1 1.1 Dissertation Outline . .3 CHAPTER 2. RELATED WORKS . 5 2.1 Finding Defects of Large Source Code . .5 2.2 Graph Based Program Analysis .