Computational Limitations in Robust Classification and Win-Win Results
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Typical Stability
Typical Stability Raef Bassily∗ Yoav Freundy Abstract In this paper, we introduce a notion of algorithmic stability called typical stability. When our goal is to release real-valued queries (statistics) computed over a dataset, this notion does not require the queries to be of bounded sensitivity – a condition that is generally assumed under differential privacy [DMNS06, Dwo06] when used as a notion of algorithmic stability [DFH+15b, DFH+15c, BNS+16] – nor does it require the samples in the dataset to be independent – a condition that is usually assumed when generalization-error guarantees are sought. Instead, typical stability requires the output of the query, when computed on a dataset drawn from the underlying distribution, to be concentrated around its expected value with respect to that distribution. Typical stability can also be motivated as an alternative definition for database privacy. Like differential privacy, this notion enjoys several important properties including robustness to post-processing and adaptive composition. However, privacy is guaranteed only for a given family of distributions over the dataset. We also discuss the implications of typical stability on the generalization error (i.e., the difference between the value of the query computed on the dataset and the expected value of the query with respect to the true data distribution). We show that typical stability can control generalization error in adaptive data analysis even when the samples in the dataset are not necessarily independent and when queries to be computed are not necessarily of bounded- sensitivity as long as the results of the queries over the dataset (i.e., the computed statistics) follow a distribution with a “light” tail. -

An Efficient Boosting Algorithm for Combining Preferences Raj
An Efficient Boosting Algorithm for Combining Preferences by Raj Dharmarajan Iyer Jr. Submitted to the Department of Electrical Engineering and Computer Science in partial fulfillment of the requirements for the degree of Master of Science at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY September 1999 © Massachusetts Institute of Technology 1999. All rights reserved. A uth or .............. ..... ..... .................................. Department of E'ectrical ngineering and Computer Science August 24, 1999 C ertified by .. ................. ...... .. .............. David R. Karger Associate Professor Thesis Supervisor Accepted by............... ........ Arthur C. Smith Chairman, Departmental Committe Graduate Students MACHU OF TEC Lo NOV LIBRARIES An Efficient Boosting Algorithm for Combining Preferences by Raj Dharmarajan Iyer Jr. Submitted to the Department of Electrical Engineering and Computer Science on August 24, 1999, in partial fulfillment of the requirements for the degree of Master of Science Abstract The problem of combining preferences arises in several applications, such as combining the results of different search engines. This work describes an efficient algorithm for combining multiple preferences. We first give a formal framework for the problem. We then describe and analyze a new boosting algorithm for combining preferences called RankBoost. We also describe an efficient implementation of the algorithm for certain natural cases. We discuss two experiments we carried out to assess the performance of RankBoost. In the first experi- ment, we used the algorithm to combine different WWW search strategies, each of which is a query expansion for a given domain. For this task, we compare the performance of Rank- Boost to the individual search strategies. The second experiment is a collaborative-filtering task for making movie recommendations. -

Download This PDF File
T G¨ P 2012 C N Deadline: December 31, 2011 The Gödel Prize for outstanding papers in the area of theoretical computer sci- ence is sponsored jointly by the European Association for Theoretical Computer Science (EATCS) and the Association for Computing Machinery, Special Inter- est Group on Algorithms and Computation Theory (ACM-SIGACT). The award is presented annually, with the presentation taking place alternately at the Inter- national Colloquium on Automata, Languages, and Programming (ICALP) and the ACM Symposium on Theory of Computing (STOC). The 20th prize will be awarded at the 39th International Colloquium on Automata, Languages, and Pro- gramming to be held at the University of Warwick, UK, in July 2012. The Prize is named in honor of Kurt Gödel in recognition of his major contribu- tions to mathematical logic and of his interest, discovered in a letter he wrote to John von Neumann shortly before von Neumann’s death, in what has become the famous P versus NP question. The Prize includes an award of USD 5000. AWARD COMMITTEE: The winner of the Prize is selected by a committee of six members. The EATCS President and the SIGACT Chair each appoint three members to the committee, to serve staggered three-year terms. The committee is chaired alternately by representatives of EATCS and SIGACT. The 2012 Award Committee consists of Sanjeev Arora (Princeton University), Josep Díaz (Uni- versitat Politècnica de Catalunya), Giuseppe Italiano (Università a˘ di Roma Tor Vergata), Mogens Nielsen (University of Aarhus), Daniel Spielman (Yale Univer- sity), and Eli Upfal (Brown University). ELIGIBILITY: The rule for the 2011 Prize is given below and supersedes any di fferent interpretation of the parametric rule to be found on websites on both SIGACT and EATCS. -

Theory and Algorithms for Modern Problems in Machine Learning and an Analysis of Markets
Theory and Algorithms for Modern Problems in Machine Learning and an Analysis of Markets by Ashish Rastogi A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy Department of Computer Science Courant Institute of Mathematical Sciences New York University May 2008 Richard Cole—Advisor Mehryar Mohri—Advisor °c Ashish Rastogi All Rights Reserved, 2008 To the most wonderful parents in the whole world, Mrs. Asha Rastogi and Mr. Shyam Lal Rastogi iv Acknowledgements First and foremost, I would like to thank my advisors, Professor Richard Cole and Professor Mehryar Mohri, for their unwavering support, guidance and constant encouragement. They have been inspiring mentors and much of what lies in the following pages can be credited to them. Working under their supervision has been one of the most enriching experiences of my life. I would also like to thank Professor Joel Spencer, Professor Arun Sun- dararajan, Professor Subhash Khot and Dr. Corinna Cortes for agreeing to serve as members on my thesis committee. Professor Spencer’s class on Random Graphs remains one of the most stim- ulating courses I undertook as a graduate student. Internships at Google through the summers of 2005, 2006 and 2007 were some of the most enjoy- able periods of my graduate school life. Many thanks are due to Dr. Corinna Cortes for providing me with the opportunity to work on several challenging problems at Google. Research initiated during these internships culminated in the development of ideas that form the bulk of this thesis. I would also like to thank my peers from the graduate school. -

40Th ACM Symposium on Theory of Computing (STOC 2008) Saturday
40th ACM Symposium on Theory of Computing (STOC 2008) Saturday, May 17, 2008 7:00pm – 10:00pm Registration (Conference Centre) 8:00pm – 10:00pm Reception (Palm Court) Sunday, May 18, 2008 8:00am – 5:00pm Registration (Conference Centre) 8:10am – 8:35am Breakfast (Conference Centre) Session 1A Session 1B (Theatre) (Saanich Room) Chair: Venkat Guruswami Chair: David Shmoys (Cornell (University of Washington and University) Institute for Advanced Study) 8:35am - 8:55am Parallel Repetition in Projection The Complexity of Temporal Games and a Concentration Bound Constraint Satisfaction Problems Anup Rao Manuel Bodirsky, Jan Kara 9:00am - 9:20am SDP Gaps and UGC Hardness for An Effective Ergodic Theorem Multiway Cut, 0-Extension and and Some Applications Metric Labeling Satyadev Nandakumar Rajeskar Manokaran, Joseph (Seffi) Naor, Prasad Raghavendra, Roy Schwartz 9:25am – 9:45am Unique Games on Expanding Algorithms for Subset Selection Constraint Graphs are Easy in Linear Regression Sanjeev Arora, Subhash A. Khot, Abhimanyu Das, David Kempe Alexandra Kolla, David Steurer, Madhur Tulsiani, Nisheeth Vishnoi 9:45am - 10:10am Break Session 2 (Theatre) Chair: Joan Feigenbaum (Yale University) 10:10am - 11:10am Rethinking Internet Routing Invited talk by Jennifer Rexford (Princeton University) 11:10am - 11:20am Break Session 3A Session 3B (Theatre) (Saanich Room) Chair: Xiaotie Deng (City Chair: Anupam Gupta (Carnegie University of Hong Kong) Mellon University) The Pattern Matrix Method for 11:20am – 11:40am Interdomain Routing and Games Lower Bounds on Quantum Hagay Levin, Michael Schapira, Communication Aviv Zohar Alexander A. Sherstov 11:45am – 12:05pm Optimal approximation for the Classical Interaction Cannot Submodular Welfare Problem in Replace a Quantum Message the value oracle model Dmitry Gavinsky Jan Vondrak 12:10pm – 12:30pm Optimal Mechanism Design and Span-program-based quantum Money Burning algorithm for evaluating formulas Jason Hartline, Tim Ben W. -

Game Theory, Alive Anna R
Game Theory, Alive Anna R. Karlin Yuval Peres 10.1090/mbk/101 Game Theory, Alive Game Theory, Alive Anna R. Karlin Yuval Peres AMERICAN MATHEMATICAL SOCIETY Providence, Rhode Island 2010 Mathematics Subject Classification. Primary 91A10, 91A12, 91A18, 91B12, 91A24, 91A43, 91A26, 91A28, 91A46, 91B26. For additional information and updates on this book, visit www.ams.org/bookpages/mbk-101 Library of Congress Cataloging-in-Publication Data Names: Karlin, Anna R. | Peres, Y. (Yuval) Title: Game theory, alive / Anna Karlin, Yuval Peres. Description: Providence, Rhode Island : American Mathematical Society, [2016] | Includes bibliographical references and index. Identifiers: LCCN 2016038151 | ISBN 9781470419820 (alk. paper) Subjects: LCSH: Game theory. | AMS: Game theory, economics, social and behavioral sciences – Game theory – Noncooperative games. msc | Game theory, economics, social and behavioral sciences – Game theory – Cooperative games. msc | Game theory, economics, social and behavioral sciences – Game theory – Games in extensive form. msc | Game theory, economics, social and behavioral sciences – Mathematical economics – Voting theory. msc | Game theory, economics, social and behavioral sciences – Game theory – Positional games (pursuit and evasion, etc.). msc | Game theory, economics, social and behavioral sciences – Game theory – Games involving graphs. msc | Game theory, economics, social and behavioral sciences – Game theory – Rationality, learning. msc | Game theory, economics, social and behavioral sciences – Game theory – Signaling, -

Online Rank Aggregation
JMLR: Workshop and Conference Proceedings 25:539{553, 2012 Asian Conference on Machine Learning Online Rank Aggregation Shota Yasutake [email protected] Panasonic System Networks Co., Ltd Kohei Hatano [email protected] Eiji Takimoto [email protected] Masayuki Takeda [email protected] Kyushu University Editor: Steven C.H. Hoi and Wray Buntine Abstract We consider an online learning framework where the task is to predict a permutation which represents a ranking of n fixed objects. At each trial, the learner incurs a loss defined as Kendall tau distance between the predicted permutation and the true permutation given by the adversary. This setting is quite natural in many situations such as information retrieval and recommendation tasks. We prove a lower bound of the cumulative loss and hardness results. Then, we propose an algorithm for this problem and prove its relative loss bound which shows our algorithm is close to optimal. Keywords: online learning, ranking, rank aggregation, permutation 1. Introduction The rank aggregation problem have gained much attention due to developments of infor- mation retrieval on the Internet, online shopping stores, recommendation systems and so on. The problem is, given m permutations of n fixed elements, to find a permutation that minimizes the sum of \distances" between itself and each given permutation. Here, each permutation represents a ranking over n elements. So, in other words, the ranking aggre- gation problem is to find an \average" ranking which reflects the characteristics of given rankings. In particular, the optimal ranking is called Kemeny optimal (Kemeny, 1959; Kemeny and Snell, 1962) when the distance is defined as Kendall tau distance (which we will define later). -

The Boosting Apporach to Machine Learning
Nonlinear Estimation and Classification, Springer, 2003. The Boosting Approach to Machine Learning An Overview Robert E. Schapire AT&T Labs Research Shannon Laboratory 180 Park Avenue, Room A203 Florham Park, NJ 07932 USA www.research.att.com/ schapire December 19, 2001 Abstract Boosting is a general method for improving the accuracy of any given learning algorithm. Focusing primarily on the AdaBoost algorithm, this chapter overviews some of the recent work on boosting including analyses of AdaBoost’s training error and generalization error; boosting’s connection to game theory and linear programming; the relationship between boosting and logistic regression; extensions of AdaBoost for multiclass classification problems; methods of incorporating human knowledge into boosting; and experimental and applied work using boosting. 1 Introduction Machine learning studies automatic techniques for learning to make accurate pre- dictions based on past observations. For example, suppose that we would like to build an email filter that can distinguish spam (junk) email from non-spam. The machine-learning approach to this problem would be the following: Start by gath- ering as many examples as posible of both spam and non-spam emails. Next, feed these examples, together with labels indicating if they are spam or not, to your favorite machine-learning algorithm which will automatically produce a classifi- cation or prediction rule. Given a new, unlabeled email, such a rule attempts to predict if it is spam or not. The goal, of course, is to generate a rule that makes the most accurate predictions possible on new test examples. 1 Building a highly accurate prediction rule is certainly a difficult task. -
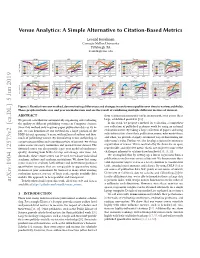
Venue Analytics: a Simple Alternative to Citation-Based Metrics
Venue Analytics: A Simple Alternative to Citation-Based Metrics Leonid Keselman Carnegie Mellon University Pittsburgh, PA [email protected] AI/ML HCI Robotics Theory Vision 12 9 7 12 6 8 10 6 10 5 7 8 5 8 6 NIPS (10.9) CHI (7.2) 4 RSS (6.2) STOC (11.7) CVPR (8.2) 4 5 6 ICML (9.5) CSCW (5.2) ICRA (5.2) 6 FOCS (11.0) ECCV (6.4) 3 4 AAAI (7.7) 3 UIST (5.0) WAFR (5.2) CCC (10.4) ICCV (6.2) 4 AISTATS (7.5) UbiComp (4.8) 2 IJRR (5.1) 4 SODA (10.2) 3 PAMI (5.5) venue scores venue scores 2 venue scores venue scores venue scores UAI (5.8) ICWSM (4.6) HRI (4.1) APPROX-RANDOM (7.9) 2 IJCV (4.3) 2 2 IJCAI (5.5) 1 DIS (3.1) 1 IROS (3.8) COLT (7.8) 1 WACV (3.7) 1970 1980 1990 2000 2010 1970 1980 1990 2000 2010 1970 1980 1990 2000 2010 1970 1980 1990 2000 2010 1970 1980 1990 2000 2010 year year year year year Database IR/Web NLP Graphics Crypto 7 8 10 9 6 6 7 8 8 5 5 6 7 VLDB (7.8) WWW (6.8) EMNLP (6.6) 5 SIGGRAPH (7.6) 6 TCC (9.1) 6 4 4 SIGMOD (7.6) KDD (6.2) ACL (5.9) 4 SIGGRAPH Asia (7.4) 5 CRYPTO (7.2) ICDE (6.4) 3 CIKM (4.7) 3 NAACL (5.3) TOG (5.5) 4 EUROCRYPT (7.2) 4 3 PODS (5.9) ICWSM (4.6) TACL (4.8) TVCG (5.0) J. -
Machine Learning Classification Over Encrypted Data
Machine Learning Classification over Encrypted Data Raphaël Bost∗ Raluca Ada Popayz Stephen Tuz Shafi Goldwasserz Abstract Machine learning classification is used in numerous settings nowadays, such as medical or genomics predictions, spam detection, face recognition, and financial predictions. Due to privacy concerns, in some of these applications, it is important that the data and the classifier remain confidential. In this work, we construct three major classification protocols that satisfy this privacy constraint: hyperplane decision, Naïve Bayes, and decision trees. We also enable these protocols to be combined with AdaBoost. At the basis of these constructions is a new library of building blocks for constructing classifiers securely; we demonstrate that this library can be used to construct other classifiers as well, such as a multiplexer and a face detection classifier. We implemented and evaluated our library and classifiers. Our protocols are efficient, taking milliseconds to a few seconds to perform a classification when running on real medical datasets. 1 Introduction Classifiers are an invaluable tool for many tasks today, such as medical or genomics predictions, spam detection, face recognition, and finance. Many of these applications handle sensitive data [WGH12, SG11, SG13], so it is important that the data and the classifier remain private. Consider the typical setup of supervised learning, depicted in Figure1. Supervised learning algorithms consist of two phases: (i) the training phase during which the algorithm learns a model w from a data set of labeled examples, and (ii) the classification phase that runs a classifier C over a previously unseen feature vector x, using the model w to output a prediction C(x; w). -
Testing Closeness of Discrete Distributions
Testing Closeness of Discrete Distributions The MIT Faculty has made this article openly available. Please share how this access benefits you. Your story matters. Citation Tugkan Batu, Lance Fortnow, Ronitt Rubinfeld, Warren D. Smith, and Patrick White. 2013. Testing Closeness of Discrete Distributions. J. ACM 60, 1, Article 4 (February 2013), 25 pages. As Published http://dx.doi.org/10.1145/2432622.2432626 Publisher Association for Computing Machinery (ACM) Version Original manuscript Citable link http://hdl.handle.net/1721.1/90630 Terms of Use Creative Commons Attribution-Noncommercial-Share Alike Detailed Terms http://creativecommons.org/licenses/by-nc-sa/4.0/ Testing Closeness of Discrete Distributions∗ Tu˘gkan Batu† Lance Fortnow‡ Ronitt Rubinfeld§ Warren D. Smith¶ Patrick White November 5, 2010 Abstract Given samples from two distributions over an n-element set, we wish to test whether these dis- tributions are statistically close. We present an algorithm which uses sublinear in n, specifically, O(n2/3ǫ−8/3 log n), independent samples from each distribution, runs in time linear in the sample size, makes no assumptions about the structure of the distributions, and distinguishes the cases when the distance between the distributions is small (less than max ǫ4/3n−1/3/32,ǫn−1/2/4 ) { } or large (more than ǫ) in ℓ1 distance. This result can be compared to the lower bound of Ω(n2/3ǫ−2/3) for this problem given by Valiant [54]. Our algorithm has applications to the problem of testing whether a given Markov process is rapidly mixing. We present sublinear algorithms for several variants of this problem as well. -

Calibrating Noise to Variance in Adaptive Data Analysis
Proceedings of Machine Learning Research vol 75:1–10, 2018 31st Annual Conference on Learning Theory Calibrating Noise to Variance in Adaptive Data Analysis Vitaly Feldman [email protected] Google Brain Thomas Steinke [email protected] IBM Research – Almaden Editors: Sebastien Bubeck, Vianney Perchet and Philippe Rigollet Abstract Datasets are often used multiple times and each successive analysis may depend on the outcome of previous analyses. Standard techniques for ensuring generalization and statistical validity do not account for this adaptive dependence. A recent line of work studies the challenges that arise from such adaptive data reuse by considering the problem of answering a sequence of “queries” about the data distribution where each query may depend arbitrarily on answers to previous queries. The strongest results obtained for this problem rely on differential privacy – a strong notion of algorithmic stability with the important property that it “composes” well when data is reused. However the notion is rather strict, as it requires stability under replacement of an arbitrary data element. The simplest algorithm is to add Gaussian (or Laplace) noise to distort the empirical answers. However, analysing this technique using differential privacy yields suboptimal accuracy guarantees when the queries have low variance. Here we propose a relaxed notion of stability based on KL divergence that also composes adaptively. We show that our notion of stability implies a bound on the mutual information between the dataset and the output of the algorithm and then derive new generalization guarantees implied by bounded mutual information. We demonstrate that a simple and natural algorithm based on adding noise scaled to the standard deviation of the query provides our notion of stability.