10-4031.1 C Case Info Account Info
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Windows 7 Operating Guide
Welcome to Windows 7 1 1 You told us what you wanted. We listened. This Windows® 7 Product Guide highlights the new and improved features that will help deliver the one thing you said you wanted the most: Your PC, simplified. 3 3 Contents INTRODUCTION TO WINDOWS 7 6 DESIGNING WINDOWS 7 8 Market Trends that Inspired Windows 7 9 WINDOWS 7 EDITIONS 10 Windows 7 Starter 11 Windows 7 Home Basic 11 Windows 7 Home Premium 12 Windows 7 Professional 12 Windows 7 Enterprise / Windows 7 Ultimate 13 Windows Anytime Upgrade 14 Microsoft Desktop Optimization Pack 14 Windows 7 Editions Comparison 15 GETTING STARTED WITH WINDOWS 7 16 Upgrading a PC to Windows 7 16 WHAT’S NEW IN WINDOWS 7 20 Top Features for You 20 Top Features for IT Professionals 22 Application and Device Compatibility 23 WINDOWS 7 FOR YOU 24 WINDOWS 7 FOR YOU: SIMPLIFIES EVERYDAY TASKS 28 Simple to Navigate 28 Easier to Find Things 35 Easy to Browse the Web 38 Easy to Connect PCs and Manage Devices 41 Easy to Communicate and Share 47 WINDOWS 7 FOR YOU: WORKS THE WAY YOU WANT 50 Speed, Reliability, and Responsiveness 50 More Secure 55 Compatible with You 62 Better Troubleshooting and Problem Solving 66 WINDOWS 7 FOR YOU: MAKES NEW THINGS POSSIBLE 70 Media the Way You Want It 70 Work Anywhere 81 New Ways to Engage 84 INTRODUCTION TO WINDOWS 7 6 WINDOWS 7 FOR IT PROFESSIONALS 88 DESIGNING WINDOWS 7 8 WINDOWS 7 FOR IT PROFESSIONALS: Market Trends that Inspired Windows 7 9 MAKE PEOPLE PRODUCTIVE ANYWHERE 92 WINDOWS 7 EDITIONS 10 Remove Barriers to Information 92 Windows 7 Starter 11 Access -

Adobe Introduction to Scripting
ADOBE® INTRODUCTION TO SCRIPTING © Copyright 2007 Adobe Systems Incorporated. All rights reserved. Adobe® Introduction to Scripting NOTICE: All information contained herein is the property of Adobe Systems Incorporated. No part of this publication (whether in hardcopy or electronic form) may be reproduced or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written consent of Adobe Systems Incorporated. The software described in this document is furnished under license and may only be used or copied in accordance with the terms of such license. This publication and the information herein is furnished AS IS, is subject to change without notice, and should not be construed as a commitment by Adobe Systems Incorporated. Adobe Systems Incorporated assumes no responsibility or liability for any errors or inaccuracies, makes no warranty of any kind (express, implied, or statutory) with respect to this publication, and expressly disclaims any and all warranties of merchantability, fitness for particular purposes, and non-infringement of third-party rights. Any references to company names in sample templates are for demonstration purposes only and are not intended to refer to any actual organization. Adobe®, the Adobe logo, Illustrator®, InDesign®, and Photoshop® are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. Apple®, Mac OS®, and Macintosh® are trademarks of Apple Computer, Inc., registered in the United States and other countries. Microsoft®, and Windows® are either registered trademarks or trademarks of Microsoft Corporation in the United States and other countries. JavaScriptTM and all Java-related marks are trademarks or registered trademarks of Sun Microsystems, Inc. -

File Management
File management Information about file management How to use the SFTP Wrapper Advanced: WinSCP SFTP Guide Advanced: CyberDuck SFTP Guide Restoring Backups Installation Locations File Manager How to use the SFTP Wrapper To quickly load up WinSCP, you can use our wrapper to automatically launch WinSCP and log you in without messing around with usernames/passwords/ports/protocols etc. It's super easy!* Our wrapper is currently Windows only; if you would like information on how to access your files using one of our other sFTP guides. Our wrapper is currently Windows only; if you would like information on how to access your files please see one of our other sFTP guides. 1. Make sure you have .NET Framework 4.0 (or higher) installed from Microsoft's website. This is needed for the wrapper to work properly. If your computer is on Windows 8 or later, you already have it! 2. Download and run it by clicking here: here NOTE: CLOSE THE PROGRAM AFTER INSTALLATION. 1. Head on over back to the "Service" > "Access" page and click the "Download" button and then confirm you have read the very serious warning, and click "Download" again. This will download your chPPK file, a tiny little file crammed with information on how to connect to your system. Note: If clicking the sFTP wrapper install URL shows a page full of text. You will need to go back and Right Click > Save As, and run the wrapper application from your download folder. Some browsers/browser versions will not automatically download this .application file. 2. -

Wireless GPON ONT
GPON 4 Ethernet Ports | 1 PON | VoIP | 802.11n | 802.11ac GRG-4260us Wireless GPON ONT The GRG-4260us is an advanced GPON ONT gateway with 1 GPON WAN port, 4 Gigabit Ethernet LAN ports, 2 FXS ports, 1 USB2.0 Host and IEEE802.11 series Wi-Fi. The Wi-Fi not only provides an 802.11n 2T2R 2.4GHz Band which is backward compatible with 802.11g/b but also supports high performance 802.11ac with 3T3R design at 5GHz band. GRG-4260us provides powerful functions which telephone companies have applied on the xDSL CPE IAD device, and remote management utilities (such as TR-069) for network management and maintenance. FEATURES .UPnP, IPv6 compliant .WPA and 802.1x/ WPS 2.0/ Radius Client .PhyR and G.INP .NAT/PAT .Supports TR-069/TR-098/TR-181i2 .IGMP Proxy/ Fast Leave/ Snooping/ Proxy .Configuration backup and restoration .DHCP Server/Client .Web-based management (HTTPS/HTTP) .Embedded SNMP agent .Supports remote administration, automatic .IP/MAC address filtering firmware upgrade and configuration .Static route/ RIP/ RIP v2 routing functions .Integrated 802.11ac AP (backward compatible .DNS Proxy/Relay with 802.11a/n) www.comtrend.com GRG-4260us 4 Ethernet Ports | 1 PON | VoIP | 802.11n | 802.11ac SPECIFICATIONS Hardware Networking Protocols .PPPoE pass-through, Multiple PPPoE sessions on single WAN .GPON X 1 Bi-directional Optical (1310nm/1490nm) .RJ-45 X 4 for LAN, (10/100/1000 Base T) interface .RJ-11 X 2 for FXS (optional) .PPPoE filtering of non-PPPoE packets between WAN and LAN .USB2.0 host X 1 .Transparent bridging between all LAN and WAN interfaces -

Scala Infochannel Player Setup Guide
SETUP GUIDE P/N: D40E04-01 Copyright © 1993-2002 Scala, Inc. All rights reserved. No part of this publication, nor any parts of this package, may be copied or distributed, transmitted, transcribed, recorded, photocopied, stored in a retrieval system, or translated into any human or computer language, in any form or by any means, electronic, mechanical, magnetic, manual, or otherwise, or disclosed to third parties without the prior written permission of Scala Incorporated. TRADEMARKS Scala, the exclamation point logo, and InfoChannel are registered trademarks of Scala, Inc. All other trademarks or registered trademarks are the sole property of their respective companies. The following are trademarks or registered trademarks of the companies listed, in the United States and other countries: Microsoft, MS-DOS, Windows, Windows 95, Windows 98, Windows NT, Windows 2000, Windows XP, DirectX, DirectDraw, DirectSound, ActiveX, ActiveMovie, Internet Explorer, Outlook Express: Microsoft Corporation IBM, IBM-PC: International Business Machines Corporation Intel, Pentium, Indeo: Intel Corporation Adobe, the Adobe logo, Adobe Type Manager, Acrobat, ATM, PostScript: Adobe Systems Incorporated TrueType, QuickTime, Macintosh: Apple Computer, Incorporated Agfa: Agfa-Gevaert AG, Agfa Division, Bayer Corporation “Segoe” is a trademark of Agfa Monotype Corporation. “Flash” and “Folio” are trademarks of Bauer Types S.A. Some parts are derived from the RSA Data Security, Inc. MD5 Message-Digest Algorithm. JPEG file handling is based in part on the work of the Independent JPEG Group. Lexsaurus Speller Technology Copyright © 1992, 1997 by Lexsaurus Software Inc. All rights reserved. TIFF-LZW and/or GIF-LZW: Licensed under Unisys Corporation US Patent No. 4,558,302; End-User use restricted to use on only a single personal computer or workstation which is not used as a server. -

Microsoft Patches Were Evaluated up to and Including CVE-2020-1587
Honeywell Commercial Security 2700 Blankenbaker Pkwy, Suite 150 Louisville, KY 40299 Phone: 1-502-297-5700 Phone: 1-800-323-4576 Fax: 1-502-666-7021 https://www.security.honeywell.com The purpose of this document is to identify the patches that have been delivered by Microsoft® which have been tested against Pro-Watch. All the below listed patches have been tested against the current shipping version of Pro-Watch with no adverse effects being observed. Microsoft Patches were evaluated up to and including CVE-2020-1587. Patches not listed below are not applicable to a Pro-Watch system. 2020 – Microsoft® Patches Tested with Pro-Watch CVE-2020-1587 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability CVE-2020-1584 Windows dnsrslvr.dll Elevation of Privilege Vulnerability CVE-2020-1579 Windows Function Discovery SSDP Provider Elevation of Privilege Vulnerability CVE-2020-1578 Windows Kernel Information Disclosure Vulnerability CVE-2020-1577 DirectWrite Information Disclosure Vulnerability CVE-2020-1570 Scripting Engine Memory Corruption Vulnerability CVE-2020-1569 Microsoft Edge Memory Corruption Vulnerability CVE-2020-1568 Microsoft Edge PDF Remote Code Execution Vulnerability CVE-2020-1567 MSHTML Engine Remote Code Execution Vulnerability CVE-2020-1566 Windows Kernel Elevation of Privilege Vulnerability CVE-2020-1565 Windows Elevation of Privilege Vulnerability CVE-2020-1564 Jet Database Engine Remote Code Execution Vulnerability CVE-2020-1562 Microsoft Graphics Components Remote Code Execution Vulnerability -

Data File Manager
Data File Manager Welcome to Data File Manager! Thank you for using the data file manager. Highlights of the data file manager are as follows: Intuitive operability Buttons on the tool menu, drag & drop, and context menu with a right click are supported to use each function. Tree view for data in SD memory card Files and folders in SD memory card are shown in a tree structure and target files can easily be found. Operations for files and folders Files and folders can be added, renamed or deleted. PLC maintenance Viewing the PLC status, such as Run/Stop state or error status, downloading/uploading user programs, or upgrading the system software of the PLC are supported. MICRO/I maintenance Viewing the target information, such as system software version or external memory device information, or downloading/uploading project is supported. Notes - Data File Manager There are the following notes when you use Data File Manager: Supported hardware Data File Manager supports the following hardware: FC4A series MICROSmart FC5A series MICROSmart Pentra FC6A series MICROSmart FT1A series SmartAXIS expect FT1A Touch HG3G/4G series MICRO/I HG2G-5F series MICRO/I HG2G-5T series MICRO/I HG1G series MICRO/I SD card access (SmartAXIS Pro & Lite) SD card inserted on SmartAXIS series can be accessed while the PLC is stopped only. Downloading or uploading the user program (PLC) You can download or upload the user programs using ZLD files, which can be created or read with WindLDR. Downloading or uploading the project (MICRO/I) You can download or upload the project using ZNV files, which can be created or read with WindO/I-NV4. -

Development of a Windows Device Driver for the Nintendo Wii Remote Entwicklung Eines Windows Treibers Für Die Nintendo Wii Remote
Development of a Windows Device Driver for the Nintendo Wii Remote Entwicklung eines Windows Treibers für die Nintendo Wii Remote Julian Löhr School of Informatics SRH Hochschule Heidelberg Heidelberg, Germany [email protected] Abstract—This paper is about the development of a device The Wii Remote uses Bluetooth for its wireless driver for the Nintendo Wii Remote on Windows PC’s. communication and is thereby connectable with a pc[1]. Windows does recognize the Wii Remote as a game controller, Keywords—Windows driver development, Wii Remote, human but as shown in Fig. 1 no inputs are exposed. Therefore it is not interface device, game controller, Bluetooth usable without any third party support. There are various programs to enable the Wii Remote to be used within video I. INTRODUCTION games, but all of them just map the inputs to keyboard keys[2]. Many PC games do support game controllers. The So this is useful for some single-player games, but does not Nintendo Wii Remote is a wireless controller for the Nintendo support analog input[2]. Additionally if multiple controllers are Wii console and the Nintendo Wii U console. It features needed, e.g. for local multiplayer games like FIFA, this several buttons, acceleration sensors and an infrared sensor. solution is not sufficient enough[2]. Furthermore it is possible to expand the controller via an additional port with various attachments. Those attachments So the objective is to develop a device driver to enable it as are, i.e. the Nunchuk, a controller with additional buttons and a native game controller. -
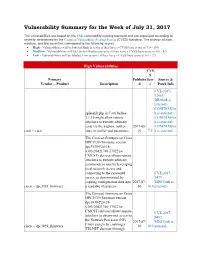
Vulnerability Summary for the Week of July 31, 2017
Vulnerability Summary for the Week of July 31, 2017 The vulnerabilities are based on the CVE vulnerability naming standard and are organized according to severity, determined by the Common Vulnerability Scoring System (CVSS) standard. The division of high, medium, and low severities correspond to the following scores: High - Vulnerabilities will be labeled High severity if they have a CVSS base score of 7.0 - 10.0 Medium - Vulnerabilities will be labeled Medium severity if they have a CVSS base score of 4.0 - 6.9 Low - Vulnerabilities will be labeled Low severity if they have a CVSS base score of 0.0 - 3.9 High Vulnerabilities CVS S Primary Publishe Scor Source & Vendor -- Product Description d e Patch Info CVE-2017- 12065 BID(link is external) CONFIRM(lin spikekill.php in Cacti before k is external) 1.1.16 might allow remote CONFIRM(lin attackers to execute arbitrary k is external) code via the avgnan, outlier- 2017-08- CONFIRM(lin cacti -- cacti start, or outlier-end parameter. 01 7.5 k is external) The Comcast firmware on Cisco DPC3939 (firmware version dpc3939-P20-18- v303r20421746-170221a- CMCST) devices allows remote attackers to execute arbitrary commands as root by leveraging local network access and connecting to the syseventd CVE-2017- server, as demonstrated by 9479 copying configuration data into 2017-07- MISC(link is cisco -- dpc3939_firmware a readable filesystem. 30 10.0 external) The Comcast firmware on Cisco DPC3939 (firmware version dpc3939-P20-18- v303r20421746-170221a- CMCST) devices allows remote CVE-2017- attackers to obtain root access to 9482 the Network Processor (NP) 2017-07- MISC(link is Linux system by enabling a cisco -- dpc3939_firmware 30 10.0 external) TELNET daemon (through CVS S Primary Publishe Scor Source & Vendor -- Product Description d e Patch Info CVE-2017-9479 exploitation) and then establishing a TELNET session. -

(RUNTIME) a Salud Total
Windows 7 Developer Guide Published October 2008 For more information, press only: Rapid Response Team Waggener Edstrom Worldwide (503) 443-7070 [email protected] Downloaded from www.WillyDev.NET The information contained in this document represents the current view of Microsoft Corp. on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This guide is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, IN THIS SUMMARY. Complying with all applicable copyright laws is the responsibility of the user. Without limiting the rights under copyright, no part of this document may be reproduced, stored in or introduced into a retrieval system, or transmitted in any form, by any means (electronic, mechanical, photocopying, recording or otherwise), or for any purpose, without the express written permission of Microsoft. Microsoft may have patents, patent applications, trademarks, copyrights or other intellectual property rights covering subject matter in this document. Except as expressly provided in any written license agreement from Microsoft, the furnishing of this document does not give you any license to these patents, trademarks, copyrights, or other intellectual property. Unless otherwise noted, the example companies, organizations, products, domain names, e-mail addresses, logos, people, places and events depicted herein are fictitious, and no association with any real company, organization, product, domain name, e-mail address, logo, person, place or event is intended or should be inferred. -

Summary Both the Desktop Graphics And
Summary Both the desktop graphics and animated film industries are striving to create spectacular, lifelike worlds. Film quality realism requires complicated per-pixel operations, previously impractical for desktop graphics which must render frames as fast as 60 times per second. The 3D Blaster GeForce2 GTS is the first Graphics Processing Unit (GPU) with the 3D performance and enhanced feature set necessary to approach this distinct level of realism. The 3D Blaster GeForce2 GTS is a State of the Art 3D Graphics Accelerator. The combination between Nvidia’s 2nd Generation Transform & Lighting (T&L) Architecture and the Nvidia Shading Rasterizer (NSR) produces one of the most stunning and realistic visuals ever seen on screen. The integrated NSR makes advanced per-pixel shading capabilities possible. This breakthrough technology has the ability to process seven pixel operations in a single pass on each of four pixel pipelines, simultaneously. The end result of this is to allow individual pixel control of colour, shadow, light, reflectivity, emissivity, specularity, loss, dirt, and other visual and material components used to create amazingly realistic objects and environments. Per-pixel shading delivers the next-generation of visual realism by going beyond the limited texture mapping techniques of previous graphics processors. • New HyperTexel architecture delivers 1.6 gigatexels per second for staggering frame rates and high- performance anti-aliasing • New NVIDIA Shading Rasterizer (NSR) delivers per pixel shading and lighting for rich, -

2 - Player Input Handling Csc 165 Computer Game Architecture Overview
CSc 165 Lecture Notes 2 - Player Input Handling CSc 165 Computer Game Architecture Overview • Device Types • Device Abstractions 2 - Input Handling • Controllers • Input Handling Packages • Event Queues • Input Action Commands (making the inputs do things) 2 CSc 165 Lecture Notes CSc 165 Lecture Notes 2 - Player Input Handling 2 - Player Input Handling Types of Input Devices Input Handling Goals • Keyboard • Steering Wheel Keep games device-independent o Game shouldn’t contain hard-coded device details • Mouse • Dance Pad o Game shouldn’t fail when a particular device is absent • Joystick (“POV”) • Guitar (allow substitution) • “POV Hat Switch” • WiiMote Keep engine device-independent o Engine components should not contain hard-coded • Gamepad • Kinect device details • Paddle • others? … isolate details in an Input Manager 3 4 CSc 165 Lecture Notes CSc 165 Lecture Notes 2 - Player Input Handling 2 - Player Input Handling Device Abstractions “D-pad” (Directional-pad) Axes Two fundamental device types: Discrete axis devices D-pad o Can have either one or two axes . Button – returns pressed or not pressed Frequently represented as 1.0 or 0.0 Single-axis form: one component; U returns one value: L R . Axis – returns a float .25 D Two types of Axis: .125 .375 Dual axis form: two components; each returns a value: . Continuous: returns a value in a range 1.0 0 .5 e.g. { -1 … 1 } or { 0 … 1 } L N R X: . Discrete: returns a value from a set .875 .625 -1 0 +1 e.g. [ 0, 1 ] or [ -1, 0, 1 ] .75 D N U Can be absolute or relative N UL U UR R DR D DL L Y: -1 0 +1 0 .125 .25 .375 .5 .625 .75 .875 1.0 5 6 CSc 165 Lecture Notes CSc 165 Lecture Notes 2 - Player Input Handling 2 - Player Input Handling Controllers Controller Example: GamePad Most “devices” are really collections : o Keyboard: collection of (e.g.