Vol. 8, No. 3, Issue 2, October 2015
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Smart Cards Contents
Smart cards Contents 1 Smart card 1 1.1 History ................................................ 1 1.1.1 Invention ........................................... 1 1.1.2 Carte Bleue .......................................... 2 1.1.3 EMV ............................................. 2 1.1.4 Development of contactless systems ............................. 2 1.2 Design ................................................ 2 1.2.1 Contact smart cards ..................................... 3 1.2.2 Contactless smart cards .................................... 3 1.2.3 Hybrids ............................................ 4 1.3 Applications .............................................. 4 1.3.1 Financial ........................................... 4 1.3.2 SIM .............................................. 4 1.3.3 Identification ......................................... 4 1.3.4 Public transit ......................................... 5 1.3.5 Computer security ...................................... 6 1.3.6 Schools ............................................ 6 1.3.7 Healthcare .......................................... 6 1.3.8 Other uses .......................................... 6 1.3.9 Multiple-use systems ..................................... 6 1.4 Security ................................................ 6 1.5 Benefits ................................................ 6 1.6 Problems ............................................... 7 1.7 See also ................................................ 7 1.8 Further reading ........................................... -

Archives of Ecotoxicology, Vol
Archives of Ecotoxicology, Vol. 2, No. 3, pp. 47-50, 2020 Archives of Ecotoxicology Journal homepage: https://office.scicell.org/index.php/AE Chemical Components and Antimicrobial Activity of Essential Oils of Petiveria alliacea Leaves Extracts Ayodele O. Olomieja, Gbenga E. Jolayemi, Fisayo E. Owolabi, Raphael C. Mordi* Department of Chemistry, Covenant University, Canaan Land, Km 10 Idiroko Road, Ota 111242 Ogun State, Nigeria. Department of Chemistry, Chrisland University, Km 5, Ajebo Road, Abeokuta, 110222, Ogun State, Nigeria Article info Received 30 June 2020 Abstract Revised 10 September 2020 A steam distillation technique was employed to obtain oil from the leaf of P. alliacea. The oil obtained was Accepted 30 September 2020 subjected to GC/MS analysis to determine the chemical components, which showed the presence of sulphur Published online 30 September heterocyclic compounds, 1,2,3-trithiolane (3), 1,2,5 trithiepane (4) and 1,2,5,6-tetrathiocane (7) as well as 2020 benzenecarbothioic acid (8) that have not been reported previously as components in the crude extracts of Short communication Petiveria alliacea. The crude extracts showed antimicrobial activity on the following microorganisms Salmonella typhi, Staphylococcus aureus, Bacillus subtilis, Escherichia coli, Rhizopus sp., Aspergillus niger. The Keywords: tests showed that the extract was most effective at limiting the growth of Salmonella typhi and the Rhizopus Essential oil sp. (MIC 3.125 µg/mL and MBC value of 6.25 µg/mL). The ethanol extract using the Soxhlet technique was Steam distillation the most effective on Staphylococcus aureus, Escherichia coli, Rhizopus sp., and Aspergillus niger (MIC 3.125 Antimicrobial activity Petiveria alliacea µg/mL). -

Evaluation of Nigeria Universities Websites Using Alexa Internet Tool: a Webometric Study
University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln Library Philosophy and Practice (e-journal) Libraries at University of Nebraska-Lincoln 2020 Evaluation of Nigeria Universities Websites Using Alexa Internet Tool: A Webometric Study Samuel Oluranti Oladipupo Mr University of Ibadan, Ibadan, Nigeria, [email protected] Follow this and additional works at: https://digitalcommons.unl.edu/libphilprac Part of the Library and Information Science Commons Oladipupo, Samuel Oluranti Mr, "Evaluation of Nigeria Universities Websites Using Alexa Internet Tool: A Webometric Study" (2020). Library Philosophy and Practice (e-journal). 4549. https://digitalcommons.unl.edu/libphilprac/4549 Evaluation of Nigeria Universities Websites Using Alexa Internet Tool: A Webometric Study Samuel Oluranti, Oladipupo1 Africa Regional Centre for Information Science, University of Ibadan, Nigeria E-mail:[email protected] Abstract This paper seeks to evaluate the Nigeria Universities websites using the most well-known tool for evaluating websites “Alexa Internet” a subsidiary company of Amazon.com which provides commercial web traffic data. The present study has been done by using webometric methods. The top 20 Nigeria Universities websites were taken for assessment. Each University website was searched in Alexa databank and relevant data including links, pages viewed, speed, bounce percentage, time on site, search percentage, traffic rank, and percentage of Nigerian/foreign users were collected and these data were tabulated and analysed using Microsoft Excel worksheet. The results of this study reveal that Adekunle Ajasin University has the highest number of links and Ladoke Akintola University of Technology with the highest number of average pages viewed by users per day. Covenant University has the highest traffic rank in Nigeria while University of Lagos has the highest traffic rank globally. -

Detailed Table of Contents
Detailed Table of Contents Preface...............................................................................................................................................xxiv Chapter 1 Auto-DetectionofHumanFactorContentsonSocialMediaPostsUsingWord2vecandLong Short-TermMemory(LSTM)................................................................................................................. 1 Chika Yinka-Banjo, University of Lagos, Nigeria Gafar Lekan Raji, University of Lagos, Nigeria Ifeanyi Precious Ohalete, Alex-Ekwueme Federal University of Ndufu-Alike, Ikwo, Nigeria Thethreatposedbycyberbullyingtothementalhealthinoursocietycannotbeoveremphasized.Victims .ofthismenacearereportedtohavesufferedpooracademicperformance,depression,andsuicidalthoughts .Thereisneedtofindanefficientandeffectivesolutiontothisproblemwithintheacademicenvironment Inthisresearch,oneofthepopulardeeplearningmodels—longshort-termmemory(LSTM)—knownfor itsoptimizedperformanceintrainingsequentialdatawascombinedwithWord2Vecembeddingtechnique tocreateamodeltrainedforclassifyingthecontentofsocialmediapostascontainingcyberbullying contentorotherwise.Theresultwasobservedtohaveshownimprovementsinitsperformancewith respecttoaccuracyintheclassificationtaskwithover80%ofthetestdatasetcorrectlyclassifiedas .againsttheexistingmodelwithabout74.9%accuracy Chapter 2 MOOCs,ArtificialIntelligenceSystems,andtheDilemmaofTertiaryEducationinthe21st -

1 Curriculum Vitae Full Name: OSABUOHIEN, Stephen Evans
Curriculum Vitae Full Name: OSABUOHIEN, Stephen Evans Place of Birth: Ika South Local Government Area, Delta State, Nigeria Gender: Male Date of Birth: 6th June, 1979 Afflation/ Contacts Address: Dept. of Economics & Development Studies, Covenant University, P.M.B. 1023, Ota, Ogun State, Nigeria Email: [email protected] and [email protected] Tel: +2348028858727 and +2348035826693 Nationality: Nigerian Marital Status: Married with a Son PERSONAL SKILLS AND COMPETENCE A good team-player, hardworking, intelligent and self-driven who demonstrates maturity, innovativeness and responsibility on any given assignment. Endowed with a pleasant personality and capability to work effectively in multi-cultural environments. Has a good knowledge of some computer/statistical packages including: STATA; E-views; SPSS; R; Microfit; and MS-environment. Astute in research, which has resulted in publication of articles in scholarly journals/book of readings and reviews for some international journals and is a member of editorial board of some of them. INSTITUTIONS ATTENDED WITH DATES Covenant University, Ota, Nigeria Jan.2007-Feb.2011 World Bank Institute/Trade Policy Training Centre in Africa, Tanzania 2010 Lund University, Sweden. 2009/2010 Covenant University, Ota, Nigeria 2005-2006 Ederlyn Computers Centre, Benin City, Nigeria 2003 Ambrose Alli University, Ekpoma, Nigeria 1998-2002 Niger College, Benin City, Nigeria 1989-1995 QUALIFICATIONS OBTAINED WITH DATES Doctor of Philosophy (PhD, Economics) Jan.2007-Feb.2011 Certificate in Agricultural Trade and Standards August,2010 Advanced Course in Mathematical Statistics/Survival Analysis 2009/2010 Master of Science (M.Sc, Economics) 2005- 2006 Certificate in Computer Operations 2003 Bachelor of Science (B.Sc, Economics, 2nd Class Upper Division) 1998-2002 Senior Secondary School Certificate 1989-1995 GRANTS/AWARDS AND RECOGNITIONS 1. -

Curriculum Vitae
CURRICULUM VITAE SECTION A: PERSONAL DATA Name: AHMED Ayodele Victor Date of Birth: 9th February 1964 Town: Ife-Olukotun Local Government Area: Yagba East State of Origin: Kogi Nationality: Nigerian Marital Status: Married Religion: Christianity Number of Children: Four Contact Adress: Economics Department, CBS, Landmark University, Omu-Aran, Kwara State. Residential Address: 10, Gbadebo Street, Kajola Quarters, Kabba, Kogi State. Phone Numbers: 08032161033. E-mail Address: [email protected] Present Position::Assistant Lecturer Current Salary: 1,596,186.36 P/A SECTION B: EDUCATIONAL HISTORY Educational Institutions Attended Date: Ekiti State University, Ado-Ekiti 2013 to Date Ekiti State University, Ado-Ekiti 2005 to 2010: Ahmadu Bello University, Zaria 1991 to 1995: Praise Computer Institute, Kabba Centre. 2003 to 2004 Community High School, Ayetoro Gbede 1980 to 1985: 1 Academic Qualifications: Date: Ph.D Economics (In view) M.Sc Economics 2010 B.Sc. (Hons) Economics 1995 Diploma in Computer Science 2004 General Certificate of Education 1987 Teaching Experience (a) Academic Rank Held: Assistant Lecturer (b) Academic Position Held: Level Adviser COURSES TAUGHT (i) Eco 111: Principles of Economics I (ii) Eco 417: Comparative Economic System (iii) Eco 331: Monetary Economics I (iv) Eco 121:Principles of Economics II (v) Eco 226: Urban and Regional Economics Publications and Journals: 1 Empirical Analysis of the Effectiveness of Poverty Eradication Programme in Kogi West Senatorial District. Journal of Economic Studies 1(1) October 2014. PAN- AFRICAN DEVELOPMENT STUDIES 2. An Enquiry into the Contributions of Microfinance Institions towards the Development of Small Scale Business in Nigeria. International Journal of Business, Economics and Management 1(6) Pak Publishing Group (co-authored) Contribution to Books 1. -

E-Mail: [email protected]. Mobile No
CURRICULUM VITAE Bio Data SURNAME, FIRST NAME, INITIAL Sanni, Samuel .E GENDER / STATE OF ORIGIN Male / Edo DATE OF BIRTH / Age 7th January, 1979 / 37years LOCAL GOVERNMENT AREA / MARITAL STATUS Etsako East / Married Address Department of Chemical Engineering, Covenant University, Canaan Land Ota, Ogun State E-Mail: [email protected]. Mobile no: 08034332497 Academic Institutions Attended With Date(s) Command Nursery, Primary & Secondary Schools, Kaduna State 1982-1996 Ladoke Akintola University of Technology Ogbomoso, Oyo State 1998-2003 D.S. Computer College, Egbeda, Lagos State 2004 Ahmadu Bello University, Zaria, Kaduna State 2006-2009 Covenant University 2014 to date Academic Qualification(s) Master of Science (M.Sc Chemical Engineering) 2009 Hysys Soft Ware Utility Certificate for PVT Data Analysis 2007 Diploma in Computer Science (C++, Basic, Excel, Power Point, Access, CA, SPSS) 2004 B.Tech. Chemical Engineering (second class lower division) 2003 Industrial Training & Safety Induction Certificates 2002 Secondary School Certificate (May / June) 1996 Work Experience N.Y.S.C, Fariah Foundation Secondary School, Babangida Road Bauchi State 2004-2005 *Post Held: Chemistry Teacher I.T , Kaduna Refining & Petrochemical Company, Kachia Road Kaduna State 2002 *Post Held: Trainee- Plant operator (Lube Section) Future Leaders International School, Chad Crescent, Malali, Kaduna State (Jan-Mar, 2010) *Post Held: Introductory Technology Teacher Arcade British International Academy, Isa Kaita Road, Malali, Kaduna State (May 2010 - Apr 2011) *Posts Held: Mathematics, Chemistry, I.C.T, & Physics teacher Plant Operations, Kaduna Refining & Petrochemical Company (KRPC) (June-Dec - 2011) Kachia Road Kaduna State *Designation: PTDF/NNPC Attache’ (Trainee- Fuels Section) Mattesh Clothier, Barnawa Shopping Complex, Barnawa, Kaduna State (Jan2012-March2014) *Designation: Director Covenant University, Canaan Land Ota, Ogun State (2013 to date) *Designation: Lecturer II Professional Membership Nigerian Society of Chemical Engineers (NSCHE) & NSE Apr. -

Dutse Journal of Economics and Development Studies (Dujeds)
DUTSE JOURNAL OF ECONOMICS AND DEVELOPMENT STUDIES (DUJEDS) A Bi-annual Publication of the Department of Economics and Development Studies, Federal University Dutse, Jigawa State- Nigeria Vol. 4 No.2 January, 2018 ISSN: 2536-6130 Dutse Joumal of Economics and Development Studies (DUJEDS) Jan. 201 8 Vol. 4 No.2 Dutse Journal of Economics and Development Studies (DUJEDS) is published by : The Department of Economics and Development Studies, Federal University Dutse. Jigawa State- Nigeria. Printed by: KABO D LIMITED NL 7 Lokoj a Road, Kaduna State, Nigeri a. +234(0)803062 8933 kabodlimited@gmail .com ISSN: 2436-6130 Copy rights: A ll right of this publicati on are reserved. No part of this Journal may be reproduced, stored in a retri eval system or transmi tted in any form by any means w ithout pri or permission of the publisher, except for academic purposes. Note: The arti c les published in this Journa l do not in any way reflect the views or position of DUJEDS. Authors are individua ll y responsi ble for all issues relating to the ir articles. Except fo r publication and copy ri ghts, any issue arisin g from an article in this Journal should be addressed directly to the Author. II Dutse Journal of Economics and Development Studies (DUJEDS) Jan. 2018 Vol. 4 No. 2 CONTENTS ~ D• 7ft Title and Author(s) Page no. Examination of Causal Relationship between Trade Openness, Exchange Rate Changes and Manufacturing Capacity Utilization: OKOYE L. Uchenna, MODEBE, N J., OKOH J. and AHMED Ado, 1 External Debt and Economic Growth in Nigeria: Is there a Debt Laffer Curve? OLIGBI, Blessing, OKUNGBOWA, Osaretin Godspower, MILTON Jyoha 16 An Assessment of Credit Management and Non -Performing Loans in Nigerian Deposit Money Banks OSEMENE, 0. -

Percentage of Special Needs Students
Percentage of special needs students S/N University % with special needs 1. Abia State University, Uturu 4.00 2. Abubakar Tafawa Balewa University, Bauchi 0.00 3. Achievers University, Owo 0.00 4. Adamawa State University Mubi 0.50 5. Adekunle Ajasin University, Akungba 0.08 6. Adeleke University, Ede 0.03 7. Afe Babalola University, Ado-Ekiti - Ekiti State 8. African University of Science & Technology, Abuja 0.93 9. Ahmadu Bello University, Zaria 0.10 10. Ajayi Crowther University, Ibadan 11. Akwa Ibom State University, Ikot Akpaden 0.00 12. Alex Ekwueme Federal University, Ndufu Alike, Ikwo 0.01 13. Al-Hikmah University, Ilorin 0.00 14. Al-Qalam University, Katsina 0.05 15. Ambrose Alli University, Ekpoma 0.03 16. American University of Nigeria, Yola 0.00 17. Anchor University Ayobo Lagos State 0.44 18. Arthur Javis University Akpoyubo Cross River State 0.00 19. Augustine University 0.00 20. Babcock University, Ilishan-Remo 0.12 21. Bayero University, Kano 0.09 22. Baze University 0.48 23. Bells University of Technology, Ota 1.00 24. Benson Idahosa University, Benin City 0.00 25. Benue State University, Makurdi 0.12 26. Bingham University 0.00 27. Bowen University, Iwo 0.12 28. Caleb University, Lagos 0.15 29. Caritas University, Enugu 0.00 30. Chrisland University 0.00 31. Christopher University Mowe 0.00 32. Clifford University Owerrinta Abia State 0.00 33. Coal City University Enugu State 34. Covenant University Ota 0.00 35. Crawford University Igbesa 0.30 36. Crescent University 0.00 37. Cross River State University of Science &Technology, Calabar 0.00 38. -
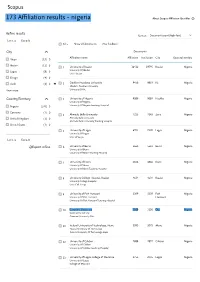
173 Affiliation Results
Scopus 173 Affiliation results - nigeria About Scopus Affiliation Identifier ❓ Refine results Sort on: Document count (high-low) Limit to Exclude All Show all documents Give feedback City Documents Affiliation name Affiliation Institution City Country/Territory Abuja (15) ▻ Ibadan (11) ▻ 1 University of Ibadan 16412 19795 Ibadan Nigeria University Of Ibadan Lagos (8) ▻ Univ. Ibadan Enugu (4) ▻ Garki (4) ▻ 2 Obafemi Awolowo University 9450 9819 Ife Nigeria Obafemi Awolowo University View more University Of Ife Country/Territory 3 University of Nigeria 9089 9089 Nsukka Nigeria University Of Nigeria Nigeria (170) ▻ University Of Nigeria Teaching Hospital Germany (1) ▻ 4 Ahmadu Bello University 7225 7243 Zaria Nigeria United Kingdom (1) ▻ Ahmadu Bello University Ahmadu Bello University Teaching Hospital United States (1) ▻ 5 University of Lagos 6974 7328 Lagos Nigeria University Of Lagos Univ Of Lagos Limit to Exclude University of Benin 5663 5663 Benin Nigeria Export refine 6 University Of Benin University Of Benin Teaching Hospital 7 University of Ilorin 4846 4846 Ilorin Nigeria University Of Ilorin University Of Ilorin Teaching Hospital 8 University College Hospital, Ibadan 4634 4634 Ibadan Nigeria University College Hospital Univ. Coll. Hosp. 9 University of Port Harcourt 3309 3309 Port Nigeria University Of Port Harcourt Harcourt University Of Port Harcourt Teaching Hospital 10 Covenant University 3100 3100 Ota Nigeria Covenant University Covenant University Ota 11 Federal University of Technology, Akure 3093 3093 Akure Nigeria Federal University -

Nduka, David Obinna
Curriculum Vitae Nduka, David Obinna Name: NDUKA David Obinna Sex: Male Town: Okohia LGA: Isi-ala Mbano State of Origin: Imo Nationality: Nigerian Marital Status: Married Religion: Christianity Number of Children: Two (2) with ages 4years and 1year 7months Contact Address: Department of Building Technology, Covenant University, Canaanland kM 10 Idiroko Road, Ota. PMB 1023. Ota. Ogun State. Nigeria. Residential Address: Block D-102, Post graduate Quarters, Covenant University, Cannanland, Ota, Ogun State Telephone No: +2348066680238 Email address: [email protected] and [email protected] Present Position: Lecturer II EDUCATIONAL HISTORY INSTITUTIONS ATTENDED WITH DATES S/N INSTITUTION DATE 1 University of Lagos, Akoka, Lagos 2013 - 2015 2 University of Lagos, Akoka, Lagos 2004 - 2008 3 Federal Polytechnic Nekede, Owerri 1999 - 2001 4 Osuh Technical College, Okohia 1994 - 1997 5 Okohia Secondary School, Okohia 1991 - 1993 6 Osuh Central School, Osuh 1986 - 1991 ACADEMIC QUALIFICATIONS S/N DEGREE/ CERTIFICATE TYPE YEAR GRADE 2 M.Sc. Construction Technology 2015 Pass 3 B.Sc. (Hons.) Building 2008 Second Class Upper 4 National Diploma, Building Technology 2001 Upper credit 5 Senior Secondary School Certificate 1997 - 6 First School Leaving Certificate 1991 - TEACHING AND WORK EXPERIENCE S/N INSTITUTION RANK DATE 1 Covenant University, Dept. of Building Lecturer 2 July 2017 - Till date Technology 2 Bells University of Technology, Ota, Dept. Lecturer 2 May 2016 - June, 2017 of Building Technology 3 Bells University of Technology, Ota, Dept. Assistant Lecturer March 2015 - April 2016 of Building Technology 4 Bells University of Technology, Ota, Dept. Teaching Assistant September 2011 - March of Building Technology 2015 6 Kawal Nigeria Limited, Abuja Site Manager June 2010 - August 2011 7 (NYSC) Bells University of Technology, Corp Member March 2009 - February Ota, Dept. -

Oni Samuel Olorunmaiye
ONI SAMUEL OLORUNMAIYE Contact Department of Political Science & International Relations College of Leadership Development Studies, Covenant University, Ota, Ogun State, Nigeria [email protected], [email protected] Present Position Senior Lecturer Education Ph. D in Political Science, Covenant University - Ota, Nigeria, 2013 Dissertation title: Legislature-executive Relations in Nigeria’s Presidential System M. Sc Political Science, Covenant University - Ota, Nigeria, 2009 B. A. Public Administration, Ahmadu Bello University – Zaria, 1998 Employment Covenant University, Ota, Nigeria. 2017 till date Senior Lecturer (Teaching and research) Covenant University, Ota, Nigeria. 2014 - 2017 Lecturer I (Teaching and research) Covenant University, Ota, Nigeria. 2013 - 2014 Lecturer II (Teaching and research) Covenant University, Ota, Nigeria. 2008 – 2013 Assistant Lecturer (Teaching and research) Covenant University, Ota, Nigeria. 2007 - 2008 Graduate Research and Teaching Assistant Covenant University, Ota Nigeria. 2004 – 2007 Administrative Officer Effective & efficient management of the VC’s office; Management of the unit’s financial & material resources; proper recording and maintenance of documents in the Vice Chancellor’s Office, follows up on the Vice Chancellor’s external linkages. Research Interest Governance, legislature, constitutionalism, conflict studies. 1 Academic Linkage Editorial Board member - Sage Open Article Editor - IGI Global Editorial Board member, International Conference on eDemocracy & eGovernment