Iptables Stateful Firewall and Nat Routing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Wingate Manual
Wingate manual So read on to find out what to do after you ve installed WinGate, and how to go about configuring your LAN to get your client machines connecting to the. WinGate is highly capable web proxy software for Windows: caching, intercepting, forward and reverse proxy with https inspection and SSL offload, SOCKS WinGate VPN · Kaspersky AV for WinGate · PureSight for WinGate · Lumen. Your license agreement with Qbik New Zealand Limited, which is included with WinGate 3 (“the Software”), specifies the permitted and prohibited uses of the. Install WinGate 7 and have your network up and running in about 5 minutes. This video demonstrates how. WinGate Proxy Server is a sophisticated integrated Internet gateway and Advance => Network => Settings => Manual Proxy Configuration. Control and manage Internet access with WinGate, a sophisticated Internet gateway and communications server designed to meet the control, security and. Wingate Tutorial - Download as Word Doc .doc /.docx), PDF File .pdf), Text Select manual settings Goto edit settings Edit ip settings Set your ip adress as. WinGate is software designed to calibrate canal check gates for flow measurement. WinGate can analyze radial gates and slide gates. The current version is. Manual. WINGATE®. Configuration Tool for UNIGATE®. Deutschmann Automation GmbH & Co. KG | hmann. This manual covers two models - E and E Wingate Option. Watch therefore, for which sections apply to your bike. Monark E and E Wingate. The NCDPI Licensure Form and instructions are also available online at our website under "Forms," then “Licensure” for your convenience. Application. Library LibGuides. Policy Manual Cataloging. Library LibGuides. Policy Manual E-Resources. -

Protokollsupport
Reference Guide WinRoute Pro 4.1 SE För version 4.1 Build 22 och sinare Tiny Software Inc. Contents Innehållsförteckning Läs mig först 2 Beskrivning av WinRoute 5 WinRoute sammanfattning...................................................................................... 6 Omfattande protokollsupport .................................................................................. 9 NAT-router............................................................................................................ 10 Introduktion i NAT .................................................................................... 11 Hur NAT fungerar...................................................................................... 12 WinRoutes struktur .................................................................................... 13 Att ställa in NAT på båda gränssnitten ...................................................... 15 Portmappning - paketbefordran ................................................................. 18 Portmappning för system med flera hem (flera IP-adresser)...................... 21 Multi-NAT ................................................................................................. 22 Gränssnittstabell......................................................................................... 24 VPN-support .............................................................................................. 24 Brandvägg med paketfilter.................................................................................... 25 Översikt -
Abusing Transparent Proxies with Flash V2.00
Abusing Transparent Proxies with Flash v2.00 By Robert Auger PayPal Information Risk Management AppSec DC November 2009 The OWASP Foundation http://www.owasp.org Overview What are transparent and intercepting proxies? When are transparent proxies used? How do they operate? Brief intro to the SOP Flash and the socket policy The abuse case Solutions and mitigations Conclusions OWASP 2 What are transparent and intercepting proxies? Explicit Proxy: A proxy explicitly configured by a client or user system. Also known as a classic web proxy. Transparent Proxy: Proxy which is NOT explicitly configured by the client machine. Intercepting Proxy: A more intrusive version of a transparent proxy. May modify traffic. OWASP 3 When are transparent proxies used? OWASP 4 How traffic gets to transparent proxies Technologies such as WCCP/GRE/IPTables/IPFW are often used to force/redirect traffic to the transparent proxy The user is unaware this is going on Proxy is typically on a dedicated machine, sometimes deployed on the gateway/router itself Often involves rewriting the packet’s destination to the proxies IP address and port (NAT) Some implementations merely sniff the wire and may not terminate to a service If the proxy is listening on all addresses then rewriting shouldn’t be required, although it is unknown how common this approach is OWASP 5 Common transparent proxy architectures OWASP 6 Approach A: Use the destination IP from the client Proxy server determines destination based on original destination-IP address of client request. In this configuration the transparent proxy routes requests much like a standard router by basing its routing decisions off of the network layer (layer 3). -

Input the Title of Your Manuscript
IJCSNS International Journal of Computer Science and Network Security, VOL.13 No.10, October 2013 69 General IPS: Carapace for Campus Wide Network in Intranet Archana Wankhade†, Premchand Ambhore††, Bandu Meshram††† †Faculty of Engineering, Higher and Technical Education Maharashtra State, 444604 India †† Research Sch0lar, Engineering and Technology GCOE Amravati, Maharashtra State, India †††Faculty of Engineering, Higher and Technical Education Maharashtra State, 444604 India Abstract example, when a file is modified, HIDS will compare the The proposed software architecture is implemented by using the new record with the known attack characters and judge agile software development process. The proposed software for whether they are matching. If matching, HIDS will give an the defence against attacks deals with the attack generation, alarm to the administrator or make a proper response. The attack detection in the intranet and then prevention of attacks. information source of NIDS is the information stream of The attack prevention module is flexible as we can add the rule network. NIDS mainly monitors the corresponding port in the firewall to prevent the any known attack. The software is deployed on our collage campus wide network and tested for the and detects the intrusions in this segment of network. Once intrusion detection and prevention. Due to space problem we an attack is detected, the response module of NIDS will considered two attacks on every packet such as ICMP, UDP and make a response through the mode of inform, alarm, TCP packet. cutting the network connections, etc. Firewall Keywords: technology emerged in the late 1980s when the Internet Smurf, Ping of Death, ICMP Flood, LAND, XMAS, TCP Flood, was a fairly new technology in terms of its global use and Ping Pong Attack Generation, Firewall rules connectivity. -

Index Images Download 2006 News Crack Serial Warez Full 12 Contact
index images download 2006 news crack serial warez full 12 contact about search spacer privacy 11 logo blog new 10 cgi-bin faq rss home img default 2005 products sitemap archives 1 09 links 01 08 06 2 07 login articles support 05 keygen article 04 03 help events archive 02 register en forum software downloads 3 security 13 category 4 content 14 main 15 press media templates services icons resources info profile 16 2004 18 docs contactus files features html 20 21 5 22 page 6 misc 19 partners 24 terms 2007 23 17 i 27 top 26 9 legal 30 banners xml 29 28 7 tools projects 25 0 user feed themes linux forums jobs business 8 video email books banner reviews view graphics research feedback pdf print ads modules 2003 company blank pub games copyright common site comments people aboutus product sports logos buttons english story image uploads 31 subscribe blogs atom gallery newsletter stats careers music pages publications technology calendar stories photos papers community data history arrow submit www s web library wiki header education go internet b in advertise spam a nav mail users Images members topics disclaimer store clear feeds c awards 2002 Default general pics dir signup solutions map News public doc de weblog index2 shop contacts fr homepage travel button pixel list viewtopic documents overview tips adclick contact_us movies wp-content catalog us p staff hardware wireless global screenshots apps online version directory mobile other advertising tech welcome admin t policy faqs link 2001 training releases space member static join health -

TRM) Para Telconet Cloud Center
UNIVERSIDAD TÉCNICA PARTICULAR DE LOJA La Universidad Católica de Loja ÁREA TÉCNICA TÍTULO DE INGENIERO EN INFORMÁTICA Definición de un modelo técnico de referencia (TRM) para Telconet Cloud Center. TRABAJO DE TITULACIÓN AUTOR: Cabrera Burgos, Xavier Antonio. DIRECTOR: Cabrera Silva, Armando Augusto, MSc. CENTRO UNIVERSITARIO GUAYAQUIL 2018 Esta versión digital, ha sido acreditada bajo la licencia Creative Commons 4.0, CC BY-NY- SA: Reconocimiento-No comercial-Compartir igual; la cual permite copiar, distribuir y comunicar públicamente la obra, mientras se reconozca la autoría original, no se utilice con fines comerciales y se permiten obras derivadas, siempre que mantenga la misma licencia al ser divulgada. http://creativecommons.org/licenses/by-nc-sa/4.0/deed.es 2018 APROBACIÓN DEL DIRECTOR DEL TRABAJO DE TITULACIÓN MSc. Armando Augusto Cabrera Silva. DOCENTE DE LA TITULACIÓN De mi consideración: El presente trabajo titulación: “Definición de un modelo de referencia técnica (TRM) para Telconet Cloud Center”, realizado por Xavier Antonio Cabrera Burgos ha sido orientado y revisado durante su ejecución, por cuanto se aprueba la presentación del mismo. Loja, agosto de 2018 f) ………………………………………….. MSc. Cabrera Silva, Armando Augusto ii DECLARACIÓN DE AUTORÍA Y CESIÓN DE DERECHOS “Yo, Cabrera Burgos Xavier Antonio declaro ser autor del presente trabajo de titulación: “Definición de un modelo técnico de referencia (TRM) para Telconet Cloud Center” de la Titulación en Informática, siendo el MSc. Armando Augusto Cabrera Silva director del presente trabajo; y eximo expresamente a la Universidad Técnica Particular de Loja y a sus representantes legales de posibles reclamos o acciones legales. Además, certifico que las ideas, conceptos, procedimientos y resultados vertidos en el presente trabajo investigativo, son de mi exclusiva responsabilidad. -

Migration from Windows to Linux for a Small Engineering Firm "A&G Associates"
Rochester Institute of Technology RIT Scholar Works Theses 2004 Migration from Windows to Linux for a small engineering firm "A&G Associates" Trimbak Vohra Follow this and additional works at: https://scholarworks.rit.edu/theses Recommended Citation Vohra, Trimbak, "Migration from Windows to Linux for a small engineering firm A&G" Associates"" (2004). Thesis. Rochester Institute of Technology. Accessed from This Thesis is brought to you for free and open access by RIT Scholar Works. It has been accepted for inclusion in Theses by an authorized administrator of RIT Scholar Works. For more information, please contact [email protected]. Migration from Windows to Linux for a Small Engineering Firm "A&G Associates" (H ' _T ^^L. WBBmBmBBBBmb- Windows Linux by Trimbak Vohra Thesis submitted in partial fulfillment of the requirements for the degree of Master of Science in Information Technology Rochester Institute of Technology B. Thomas Golisano College of Computing and Information Sciences Date: December 2, 2004 12/B2/28B2 14:46 5854752181 RIT INFORMATION TECH PAGE 02 Rochester Institute of Teehnology B. Thomas Golisano College of Computing and Information Sciences Master of Science in Information Technology Thesis Approval Form Student Name: Trimbak Vohra Thesis Title: Migration from Windows to Unux for a Small Engineeriog Firm "A&G Associates" Thesis Committee Name Signature Date Luther Troell luther IrQell, Ph.D ttL ",j7/Uy Chair G. L. Barido Prof. ~~orge Barido ? - Dec:. -cl7' Committee Member Thomas Oxford Mr. Thomas OxfocQ \ 2. L~( Q~ Committee Member Thesis Reproduction Permission Form Rochester Institute of Technology B. Thomas Golisano College of Computing and Information Sciences Master of Science in Information Technology Migration from Windows to Linux for a Small Engineering Firm "A&G Associates" I,Trimbak Vohra, hereby grant permission to the Wallace Library of the Rochester Institute of Technology to reproduce my thesis in whole or in part. -
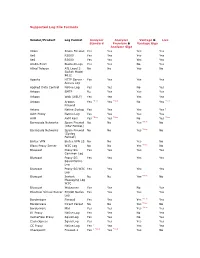
Supported Log File Formats
Supported Log File Formats Vendor/Product Log Format Analyzer Analyzer Vantage & Live Standard Premium & Vantage Giga Analyzer Giga 3Com 3Com Firewall Yes Yes Yes Yes 8e6 R2000 Yes Yes Yes Yes 8e6 R3000 Yes Yes Yes Yes Aladin Esafe Blocked Logs Yes Yes No Yes Allied Telesyn ATI Level 3 No No Yes No Switch Model 9812 Apache HTTP Server - Yes Yes Yes Yes Access Log Applied Data Control Native Log Yes Yes No Yes Arkoon SMTP No Yes Yes Yes Arkoon Web (WELF) Yes Yes Yes Yes Arkoon Arkoon Yes *New Yes *New No Yes *New Firewall Astaro Native Syslog Yes Yes Yes Yes 3 Avirt Proxy Native Log Yes Yes Yes Yes AVM AVM Ken! Yes *New Yes *New No Yes *New Barracuda Networks Spam Firewall No No Yes *New No (CSV Format) Barracuda Networks Spam Firewall No No Yes *New No (Syslog Format) Bintec VPN Bintec VPN 25 No No Yes No Bloxx Proxy Server W3C Log No No Yes *New No Bluecoat Proxy SG Yes Yes Yes Yes Common Log Bluecoat Proxy SG Yes Yes Yes Yes Squid Native Log Bluecoat Proxy SG W3C Yes Yes Yes Yes Log Bluecoat Instant No No Yes *New No Messaging Log W3C Bluecoat Websense Yes Yes No Yes BlueReef Virtual Server SQUID Native Yes Yes Yes Yes Log Borderware Firewall Yes Yes Yes *New Yes Borderware Direct Packet No No Yes *New No Borderware Mail Yes Yes Yes *New Yes BT Proxy Native Log Yes Yes No Yes CacheFlow Proxy Squid Log Yes Yes No Yes CacheXpress Squid Log Yes Yes Yes Yes CC Proxy Native Log Yes 1 Yes Yes Yes Checkpoint Firewall-1 Yes 1 *Mod Yes *Mod Yes No Checkpoint Firewall Yes 1 *Mod Yes *Mod Yes No Custom Checkpoint NG Yes 1 *Mod Yes *Mod Yes No CipherTrust -
Penetration Testing, Metasploit Tutorial, Metasploit Hacking,Pentest
Hacking Articles Raj Chandel's Blog Author Web Penetration Testing Penetration Testing Courses We Offer My Books Donate us Penetration Testing Subscribe to Blog via Email Linux Privilege Escalation using Miscongured NSF Enter your email address to Linux Privilege Escalation using Sudo Rights subscribe to this blog and receive Capture NTLM Hashes using PDF (Bad-Pdf) notications of new posts by email. Privilege Escalation in Linux using etc/passwd le Email Address Compressive Guide to File Transfer (Post Exploitation) SUBSCRIBE SNMP Lab Setup and Penetration Testing 6 Ways to Hack SNMP Password Comprehensive Guide to SSH Tunnelling 4 ways to Hack MS SQL Login Password Create PDF in your applications with the Pdfcrowd HTML to PDF API PDFCROWD Nmap Scan with Timing Parameters Comprehensive Guide to Crunch Tool Spawn TTY Shell using Msfvenom (One Liner Payload) 6 Ways to Hack VNC Login Password 6 Ways to Hack PostgresSQL Login 5 Ways to Hack MySQL Login Password Bypass SSH Restriction by Port Relay Generating Scan Reports Using Nmap (Output Scan) Port Scanning using Metasploit with IPTables Understanding Guide to Mimikatz Understanding Guide for Nmap Timing Scan (Firewall Bypass) Understanding Guide for Nmap Ping Scan (Firewall Bypass) Manual Post Exploitation on Windows PC (Network Command) Sessions Command in Metasploit Comprehensive Guide to Nmap Port Status Categories Bind Payload using SFX archive with Trojanizer BackTrack 5 Tutorials Best of Hacking Beginner Guide to IPtables Browser Hacking Post Exploitation Using WMIC (System Command) -

Befsr11ver.2 41Ver.2 U31 User Guide-EU.Qxd
Instant Broadband® Series Cable/DSLRouters Use this guide to install the following products: BEFSR41 ver. 2 EtherFast® Cable/DSL Router with 4-Port Switch BEFSRU31 EtherFast® Cable/DSL Router with USB Port and 3-Port Switch BEFSR11 ver. 2 EtherFast® 1-Port Cable/DSL Router User Guide COPYRIGHT & TRADEMARKS Copyright © 2003 Linksys, All Rights Reserved. Instant Broadband, EtherFast, Linksys, and the Linksys logo are registered trademarks of Linksys Group, Inc. Microsoft, Windows, and the Windows logo are registered trademarks of Microsoft Corporation. All other trademarks and brand names are the property of their respective proprietors. FCC STATEMENT The Instant Broadband EtherFast Cable/DSL Router has been tested and complies with the specifications for a Class B digital device, pursuant to Part 15 of the FCC Rules. These limits are designed to provide reasonable protection against harmful interference in a residential installation. This equipment generates, uses, and can radiate radio fre- quency energy and, if not installed and used according to the instructions, may cause harmful interference to radio communications. However, there is no guarantee that inter- ference will not occur in a particular installation. If this equipment does cause harmful interference to radio or television reception, which is found by turning the equipment off and on, the user is encouraged to try to correct the interference by one or more of the following measures: • Reorient or relocate the receiving antenna • Increase the separation between the equipment -
Internet Security for Beginners: Contents
Internet Security For Beginners: Contents Introduction Programming Languages Command Prompt Batch Programming IP Addresses Port Numbers TCP And UDP Telnet FAQ NetBIOS/SMB Hacking Structured Query Language SQL Injection Trojans Faking/Hiding Extensions Obtaining IP Addresses A Short DoS FAQ A Short Buffer Overflow FAQ Using Password Crackers Proxies And Anonymity Google Hacking Index Browsing Basic NetCat Tutorial Compiling Exploits Using Windows FTP Hacker Community Basic Security Hacker Jargon/Slang FAQ Useful Links Disclaimer Greetz And Fuck Off's INTRODUCTION: Welcome to Internet Security For Beginners, this is the sequel to my "Hacking For n00bs Version 2", I expanded and improved this version, much of this text will be from the prequel to this text. This tutorial will teach you how to break into computers in order to teach you how to prevent such attacks from happening, after all if you know how to attack, you can figure out your own way of defending. Before trying any of the things in this text read the whole thing otherwise you might get confused, this tutorial is for the complete beginner to Internet Security. I hope you enjoy this text! This text was written by Aelphaeis Mangarae. BY READING THIS YOUR AGREEING YOU HAVE READ THE DISCLAIMER AND HAVE AGREED TO EVERYTHING IN IT! PROGRAMMING LANGUAGES: So you want to become a hacker? Well obviously if you’re reading this text, to become a hacker you must learn a programming language, so you can code your own programs and learn about how a computer works so you can repair or restore it. -
Teknik Share Akses Internet
T ekni k Share Akses Internet Onno W. Purbo Salah satu kelebihan utama Internet, sangat di mungkinkan untuk menggunakan satu saluran komunikasi secara bersama & beramai-ramai. Hal ini lebih sulit dilakukan di saluran telepon biasa (suara), memang kita bisa menggunakan PABX, tapi tetap saja hanya satu orang pengguna yang bisa menggunakan pada satu saat. Dalam tulisan ini, saya mencoba menerangkan teknik menggunakan satu saluran akses Internet secara bersama oleh semua komputer di Local Area Network (LAN) menggunakan perangkat lunak Wingate di MS Windows98. Teknik akses bersama ini, sering di sebut juga teknik proxy. Dalam bahasa protokoler di – Departemen Luar Negeri proxy adalah perantara. Jadi ada satu komputer yang menjalankan perangkat lunak proxy & bekerja sebagai perantara bagi komputer lainnya yang berada di belakang komputer proxy tersebut. Wingate di Windows98 bukan satu- satu-nya teknik proxy yang dapat digunakan, kita mengenal banyak perangkat lunak proxy di Windows98 selain Wingate, seperti Winroute dll. Di samping Windows, juga banyak perangkat lunak proxy di Linux seperti ipchains, iptables dll yang juga dapat digunakan untuk mengamankan IntraNet tempat LAN kita berada. Pada kesempatan ini akan dibatasi pembahasan pada Wingate di Windows98 dulu. Gambaran Umum Dalam skenario yang ingin dikembangkan, akses Web dilakukan menggunakan hanya sebuah saluran komunikasi (umumnya digunakan saluran telepon) secara bersama-sama oleh beberapa komputer sekaligus ke Internet. Hal ini dimaksudkan agar biaya telekomunikasi & akses Internet dapat dibagi merata ke semua komputer yang mengakses secara bersama-sama sehingga menjadi lebih murah. Secara sederhana, kita asumsikan biaya akses Internet adalah Rp. 10.000 / jam (ISP + Telkom, kalau pulsa belum naik). Jika satu saluran akses tersebut digunakan bersama- sama oleh lima (5) komputer secara bersamaan, maka sebetulnya beban biaya akses – Internet setiap komputernya adalah Rp.