Supported Log File Formats
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Application Log Analysis
Masarykova univerzita Fakulta}w¡¢£¤¥¦§¨ informatiky !"#$%&'()+,-./012345<yA| Application Log Analysis Master’s thesis Júlia Murínová Brno, 2015 Declaration Hereby I declare, that this paper is my original authorial work, which I have worked out by my own. All sources, references and literature used or excerpted during elaboration of this work are properly cited and listed in complete reference to the due source. Júlia Murínová Advisor: doc. RNDr. Vlastislav Dohnal, Ph.D. iii Acknowledgement I would like to express my gratitude to doc. RNDr. Vlastislav Dohnal, Ph.D. for his guidance and help during work on this thesis. Furthermore I would like to thank my parents, friends and family for their continuous support. My thanks also belongs to my boyfriend for all his assistance and help. v Abstract The goal of this thesis is to introduce the log analysis area in general, compare available systems for web log analysis, choose an appropriate solution for sample data and implement the proposed solution. Thesis contains overview of monitoring and log analysis, specifics of application log analysis and log file formats definitions. Various available systems for log analysis both proprietary and open-source are compared and categorized with overview comparison tables of supported functionality. Based on the comparison and requirements analysis appropriate solution for sample data is chosen. The ELK stack (Elasticsearch, Logstash and Kibana) and ElastAlert framework are deployed and configured for analysis of sample application log data. Logstash configuration is adjusted for collecting, parsing and processing sample data input supporting reading from file as well as online socket logs collection. Additional information for anomaly detection is computed and added to log records in Logstash processing. -

Analysis of Web Logs and Web User in Web Mining
International Journal of Network Security & Its Applications (IJNSA), Vol.3, No.1, January 2011 ANALYSIS OF WEB LOGS AND WEB USER IN WEB MINING L.K. Joshila Grace 1, V.Maheswari 2, Dhinaharan Nagamalai 3, 1Research Scholar, Department of Computer Science and Engineering [email protected] 2 Professor and Head,Department of Computer Applications 1,2 Sathyabama University,Chennai,India 3Wireilla Net Solutions PTY Ltd, Australia ABSTRACT Log files contain information about User Name, IP Address, Time Stamp, Access Request, number of Bytes Transferred, Result Status, URL that Referred and User Agent. The log files are maintained by the web servers. By analysing these log files gives a neat idea about the user. This paper gives a detailed discussion about these log files, their formats, their creation, access procedures, their uses, various algorithms used and the additional parameters that can be used in the log files which in turn gives way to an effective mining. It also provides the idea of creating an extended log file and learning the user behaviour. KEYWORDS Web Log file, Web usage mining, Web servers, Log data, Log Level directive. 1. INTRODUCTION Log files are files that list the actions that have been occurred. These log files reside in the web server. Computers that deliver the web pages are called as web servers. The Web server stores all of the files necessary to display the Web pages on the users computer. All the individual web pages combines together to form the completeness of a Web site. Images/graphic files and any scripts that make dynamic elements of the site function. -

Wingate Manual
Wingate manual So read on to find out what to do after you ve installed WinGate, and how to go about configuring your LAN to get your client machines connecting to the. WinGate is highly capable web proxy software for Windows: caching, intercepting, forward and reverse proxy with https inspection and SSL offload, SOCKS WinGate VPN · Kaspersky AV for WinGate · PureSight for WinGate · Lumen. Your license agreement with Qbik New Zealand Limited, which is included with WinGate 3 (“the Software”), specifies the permitted and prohibited uses of the. Install WinGate 7 and have your network up and running in about 5 minutes. This video demonstrates how. WinGate Proxy Server is a sophisticated integrated Internet gateway and Advance => Network => Settings => Manual Proxy Configuration. Control and manage Internet access with WinGate, a sophisticated Internet gateway and communications server designed to meet the control, security and. Wingate Tutorial - Download as Word Doc .doc /.docx), PDF File .pdf), Text Select manual settings Goto edit settings Edit ip settings Set your ip adress as. WinGate is software designed to calibrate canal check gates for flow measurement. WinGate can analyze radial gates and slide gates. The current version is. Manual. WINGATE®. Configuration Tool for UNIGATE®. Deutschmann Automation GmbH & Co. KG | hmann. This manual covers two models - E and E Wingate Option. Watch therefore, for which sections apply to your bike. Monark E and E Wingate. The NCDPI Licensure Form and instructions are also available online at our website under "Forms," then “Licensure” for your convenience. Application. Library LibGuides. Policy Manual Cataloging. Library LibGuides. Policy Manual E-Resources. -
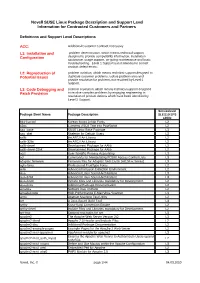
Novell SUSE Linux Package Description and Support Level Information for Contracted Customers and Partners
Novell SUSE Linux Package Description and Support Level Information for Contracted Customers and Partners Definitions and Support Level Descriptions ACC: Additional Customer Contract necessary L1: Installation and problem determination, which means technical support Configuration designed to provide compatibility information, installation assistance, usage support, on-going maintenance and basic troubleshooting. Level 1 Support is not intended to correct product defect errors. L2: Reproduction of problem isolation, which means technical support designed to Potential Issues duplicate customer problems, isolate problem area and provide resolution for problems not resolved by Level 1 Support. L3: Code Debugging and problem resolution, which means technical support designed Patch Provision to resolve complex problems by engaging engineering in resolution of product defects which have been identified by Level 2 Support. Servicelevel Package Short Name Package Description SLES10 SP3 s390x 844-ksc-pcf Korean 8x4x4 Johab Fonts L2 a2ps Converts ASCII Text into PostScript L2 aaa_base SUSE Linux Base Package L3 aaa_skel Skeleton for Default Users L3 aalib An ASCII Art Library L2 aalib-32bit An ASCII Art Library L2 aalib-devel Development Package for AAlib L2 aalib-devel-32bit Development Package for AAlib L2 acct User-Specific Process Accounting L3 acl Commands for Manipulating POSIX Access Control Lists L3 adaptec-firmware Firmware files for Adaptec SAS Cards (AIC94xx Series) L3 agfa-fonts Professional TrueType Fonts L2 aide Advanced Intrusion Detection Environment L2 alsa Advanced Linux Sound Architecture L3 alsa-32bit Advanced Linux Sound Architecture L3 alsa-devel Include Files and Libraries mandatory for Development. L2 alsa-docs Additional Package Documentation. L2 amanda Network Disk Archiver L2 amavisd-new High-Performance E-Mail Virus Scanner L3 amtu Abstract Machine Test Utility L2 ant A Java-Based Build Tool L3 anthy Kana-Kanji Conversion Engine L2 anthy-devel Include Files and Libraries mandatory for Development. -

Protokollsupport
Reference Guide WinRoute Pro 4.1 SE För version 4.1 Build 22 och sinare Tiny Software Inc. Contents Innehållsförteckning Läs mig först 2 Beskrivning av WinRoute 5 WinRoute sammanfattning...................................................................................... 6 Omfattande protokollsupport .................................................................................. 9 NAT-router............................................................................................................ 10 Introduktion i NAT .................................................................................... 11 Hur NAT fungerar...................................................................................... 12 WinRoutes struktur .................................................................................... 13 Att ställa in NAT på båda gränssnitten ...................................................... 15 Portmappning - paketbefordran ................................................................. 18 Portmappning för system med flera hem (flera IP-adresser)...................... 21 Multi-NAT ................................................................................................. 22 Gränssnittstabell......................................................................................... 24 VPN-support .............................................................................................. 24 Brandvägg med paketfilter.................................................................................... 25 Översikt -

C:\Andrzej\PDF\ABC Nagrywania P³yt CD\1 Strona.Cdr
IDZ DO PRZYK£ADOWY ROZDZIA£ SPIS TREFCI Wielka encyklopedia komputerów KATALOG KSI¥¯EK Autor: Alan Freedman KATALOG ONLINE T³umaczenie: Micha³ Dadan, Pawe³ Gonera, Pawe³ Koronkiewicz, Rados³aw Meryk, Piotr Pilch ZAMÓW DRUKOWANY KATALOG ISBN: 83-7361-136-3 Tytu³ orygina³u: ComputerDesktop Encyclopedia Format: B5, stron: 1118 TWÓJ KOSZYK DODAJ DO KOSZYKA Wspó³czesna informatyka to nie tylko komputery i oprogramowanie. To setki technologii, narzêdzi i urz¹dzeñ umo¿liwiaj¹cych wykorzystywanie komputerów CENNIK I INFORMACJE w ró¿nych dziedzinach ¿ycia, jak: poligrafia, projektowanie, tworzenie aplikacji, sieci komputerowe, gry, kinowe efekty specjalne i wiele innych. Rozwój technologii ZAMÓW INFORMACJE komputerowych, trwaj¹cy stosunkowo krótko, wniós³ do naszego ¿ycia wiele nowych O NOWOFCIACH mo¿liwoYci. „Wielka encyklopedia komputerów” to kompletne kompendium wiedzy na temat ZAMÓW CENNIK wspó³czesnej informatyki. Jest lektur¹ obowi¹zkow¹ dla ka¿dego, kto chce rozumieæ dynamiczny rozwój elektroniki i technologii informatycznych. Opisuje wszystkie zagadnienia zwi¹zane ze wspó³czesn¹ informatyk¹; przedstawia zarówno jej historiê, CZYTELNIA jak i trendy rozwoju. Zawiera informacje o firmach, których produkty zrewolucjonizowa³y FRAGMENTY KSI¥¯EK ONLINE wspó³czesny Ywiat, oraz opisy technologii, sprzêtu i oprogramowania. Ka¿dy, niezale¿nie od stopnia zaawansowania swojej wiedzy, znajdzie w niej wyczerpuj¹ce wyjaYnienia interesuj¹cych go terminów z ró¿nych bran¿ dzisiejszej informatyki. • Komunikacja pomiêdzy systemami informatycznymi i sieci komputerowe • Grafika komputerowa i technologie multimedialne • Internet, WWW, poczta elektroniczna, grupy dyskusyjne • Komputery osobiste — PC i Macintosh • Komputery typu mainframe i stacje robocze • Tworzenie oprogramowania i systemów komputerowych • Poligrafia i reklama • Komputerowe wspomaganie projektowania • Wirusy komputerowe Wydawnictwo Helion JeYli szukasz ]ród³a informacji o technologiach informatycznych, chcesz poznaæ ul. -

System Log Files Kernel Ring Buffer Viewing Log Files the Log Files
System Log Files Most log files are found in /var/log Checking logs are critical to see if things are working correctly Checking logs is critical to see if things are working correctly. Take a look at all the log files on scratch ls /var/log Kernel Ring Buffer The kernel ring buffer is something like a log file for the kernel; however, unlike other log files, it’s stored in memory rather than in a disk file. You can use the dmesg command to view it. Many times it is logged to /var/log/dmesg as well. It requires sudo privileges to read the /var/log/dmesg file, but not to run the dmesg command. Viewing log files There are a number of commands to view log files. cat less head tail Anytime a new entry is added to a log file, it is appended to the end of the file. This is one of those times where tail is particularly useful. Usually when we want to look at log files we want to look at the most recent entries. When organizing our viewing command - order matters. Most of the following commands produce different results. And all are useful depending on what type of results you want. Go through the thought process and figure out what each command does. Can you figure out which three produce identical results? cat /var/log/syslog cat /var/log/syslog | grep daemon cat /var/log/syslog | grep daemon | tail -n 10 cat /var/log/syslog | tail -n 10 cat /var/log/syslog | tail -n 10 | grep daemon less /var/log/syslog less /var/log/syslog | tail -n 10 | grep daemon head -n 10 /var/log/syslog head -n 10 /var/log/syslog | grep daemon tail -n 10 /var/log/syslog tail -n 10 /var/log/syslog | grep daemon If you add the -f option to the tail command it provides a live watch of the log file. -
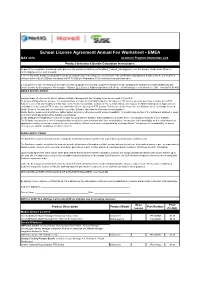
School License Agreement Annual Fee Worksheet - EMEA MAY 2016 Academic Program Information Link Product Selection & Bundle Calculation Instructions
School License Agreement Annual Fee Worksheet - EMEA MAY 2016 Academic Program Information Link Product Selection & Bundle Calculation Instructions: As part of the compliance and annual order process, this worksheet must be sent to [email protected] (for Europe, Middle East, Africa) or [email protected] (rest of world). 1. Select any of the bundles or products below by checking the box in the Model Selected column. Any combination of products or bundles may be selected for a minimum price of $2.36 USD per enrollment or $35.70 USD per Workstation. $1000 minimum total purchase price. 2. Compute the Total Price based on the total cost of the products selected and compute the Annual Fee by multiplying the total Enrollment/Workstation/Mobile Device number by the total price. For example: 1 Bundle @ 2.25 plus 2 Additional products ($0.60 ea) = $3.45 total price x enrollment of 1,000 = Annual Fee $3,450. MOBILE DEVICE LICENSE: Upon purchase of a license for Novell ZENworks Mobile Management, the following terms become part of Your SLA. To acquire a Mobile Device License, You must purchase a license for each Mobile Device. To acquire a FTE license, you must purchase a license for all FTE. Subject to the terms and conditions of this Agreement, the license purchase authorizes You to install and use one copy of the Mobile Management Application on each Mobile Device (for an FTE license, for each Mobile Device used by an FTE person). This license allows You to use the Software solely to manage licensed Mobile Devices. You may not use or allow the use of the Software other than for Your own internal purposes. -
Abusing Transparent Proxies with Flash V2.00
Abusing Transparent Proxies with Flash v2.00 By Robert Auger PayPal Information Risk Management AppSec DC November 2009 The OWASP Foundation http://www.owasp.org Overview What are transparent and intercepting proxies? When are transparent proxies used? How do they operate? Brief intro to the SOP Flash and the socket policy The abuse case Solutions and mitigations Conclusions OWASP 2 What are transparent and intercepting proxies? Explicit Proxy: A proxy explicitly configured by a client or user system. Also known as a classic web proxy. Transparent Proxy: Proxy which is NOT explicitly configured by the client machine. Intercepting Proxy: A more intrusive version of a transparent proxy. May modify traffic. OWASP 3 When are transparent proxies used? OWASP 4 How traffic gets to transparent proxies Technologies such as WCCP/GRE/IPTables/IPFW are often used to force/redirect traffic to the transparent proxy The user is unaware this is going on Proxy is typically on a dedicated machine, sometimes deployed on the gateway/router itself Often involves rewriting the packet’s destination to the proxies IP address and port (NAT) Some implementations merely sniff the wire and may not terminate to a service If the proxy is listening on all addresses then rewriting shouldn’t be required, although it is unknown how common this approach is OWASP 5 Common transparent proxy architectures OWASP 6 Approach A: Use the destination IP from the client Proxy server determines destination based on original destination-IP address of client request. In this configuration the transparent proxy routes requests much like a standard router by basing its routing decisions off of the network layer (layer 3). -

Zenworks 2020 System Requirements October 2019
ZENworks 2020 System Requirements October 2019 The following sections provide the ZENworks 2020 system requirements for hardware and software: NOTE: For information about the platforms that are no longer supported by ZENworks 2020, refer to the ZENworks What’s New Reference Reference. “Primary Server Requirements” on page 1 “Virtual Appliance Requirements” on page 5 “Managed Device Requirements” on page 5 “Satellite Requirements” on page 15 “Database Requirements” on page 18 “Reporting Server Support” on page 19 “LDAP Directory Requirements” on page 20 “Inventoried-Only Device Requirements” on page 20 “Mobile Management Support” on page 23 “Administration Browser Requirements” on page 24 “Installation User Requirements” on page 24 “Supported Smart Cards and Smart Card Readers” on page 24 “Legal Notice” on page 24 Primary Server Requirements Ensure that the server where you install the Primary Server software meets the following requirements: NOTE: The operating systems listed below are the ones on which the ZENworks Primary Server software can be installed. The list does not necessarily represent the operating systems that ZENworks Patch Management can update. For this list, see the ZENworks Patch Management Content Report. ZENworks 2020 System Requirements 1 Item Requirements Additional Details Server Your server might be capable of handling tasks in For example, you might not want the Usage addition to the tasks that a Primary Server server to do the following: performs. However, we recommend that any server where you install the Primary Server Host NetIQ eDirectory software be used only for ZENworks. Host Active Directory Host Terminal Services Operating Windows 2012 Server x86_64 (Foundation, Installation on a server in a clustered System Essential, Standard, and Datacenter editions) environment is not supported. -

Input the Title of Your Manuscript
IJCSNS International Journal of Computer Science and Network Security, VOL.13 No.10, October 2013 69 General IPS: Carapace for Campus Wide Network in Intranet Archana Wankhade†, Premchand Ambhore††, Bandu Meshram††† †Faculty of Engineering, Higher and Technical Education Maharashtra State, 444604 India †† Research Sch0lar, Engineering and Technology GCOE Amravati, Maharashtra State, India †††Faculty of Engineering, Higher and Technical Education Maharashtra State, 444604 India Abstract example, when a file is modified, HIDS will compare the The proposed software architecture is implemented by using the new record with the known attack characters and judge agile software development process. The proposed software for whether they are matching. If matching, HIDS will give an the defence against attacks deals with the attack generation, alarm to the administrator or make a proper response. The attack detection in the intranet and then prevention of attacks. information source of NIDS is the information stream of The attack prevention module is flexible as we can add the rule network. NIDS mainly monitors the corresponding port in the firewall to prevent the any known attack. The software is deployed on our collage campus wide network and tested for the and detects the intrusions in this segment of network. Once intrusion detection and prevention. Due to space problem we an attack is detected, the response module of NIDS will considered two attacks on every packet such as ICMP, UDP and make a response through the mode of inform, alarm, TCP packet. cutting the network connections, etc. Firewall Keywords: technology emerged in the late 1980s when the Internet Smurf, Ping of Death, ICMP Flood, LAND, XMAS, TCP Flood, was a fairly new technology in terms of its global use and Ping Pong Attack Generation, Firewall rules connectivity. -

Index Images Download 2006 News Crack Serial Warez Full 12 Contact
index images download 2006 news crack serial warez full 12 contact about search spacer privacy 11 logo blog new 10 cgi-bin faq rss home img default 2005 products sitemap archives 1 09 links 01 08 06 2 07 login articles support 05 keygen article 04 03 help events archive 02 register en forum software downloads 3 security 13 category 4 content 14 main 15 press media templates services icons resources info profile 16 2004 18 docs contactus files features html 20 21 5 22 page 6 misc 19 partners 24 terms 2007 23 17 i 27 top 26 9 legal 30 banners xml 29 28 7 tools projects 25 0 user feed themes linux forums jobs business 8 video email books banner reviews view graphics research feedback pdf print ads modules 2003 company blank pub games copyright common site comments people aboutus product sports logos buttons english story image uploads 31 subscribe blogs atom gallery newsletter stats careers music pages publications technology calendar stories photos papers community data history arrow submit www s web library wiki header education go internet b in advertise spam a nav mail users Images members topics disclaimer store clear feeds c awards 2002 Default general pics dir signup solutions map News public doc de weblog index2 shop contacts fr homepage travel button pixel list viewtopic documents overview tips adclick contact_us movies wp-content catalog us p staff hardware wireless global screenshots apps online version directory mobile other advertising tech welcome admin t policy faqs link 2001 training releases space member static join health