PLA-S-07: Productivity/Management Software Technology Component Standard Strategic: Microsoft Office XP
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mariana Dias Comunidades Suprabentónicas Do Almeida Mediterrâneo Batial: Influência De Factores Ambientais Na Diversidade E Estrutura Da Comunidade
Universidade de Aveiro Departamento de Biologia 201 7 MARIANA DIAS COMUNIDADES SUPRABENTÓNICAS DO ALMEIDA MEDITERRÂNEO BATIAL: INFLUÊNCIA DE FACTORES AMBIENTAIS NA DIVERSIDADE E ESTRUTURA DA COMUNIDADE DEEP - SEA SUPRABENTHOS ACROSS THE MEDITERRANEAN: THE INFLUENCE OF ENVIRONMENTAL DRIVERS ON BIODIVERSITY AND COMMUNITY STRUCTURE Universidade de Aveiro Departamento de Biologia 201 7 MARIANA DIAS COMUNIDADES SUPRABENTÓNICAS DO ALMEIDA MEDITERRÂNEO BATIAL: INFLUÊNCIA DE FACTORES AMBIENTAIS NA DIVE RSIDADE E ESTRUTURA DA COMUNIDADE DEEP - SEA SUPRABENTHOS ACROSS THE MEDITERRANEAN: THE INFLUENCE OF ENVIRONMENTAL DRIVERS ON BIODIVERSITY AND COMMUNITY STRUCTURE Tese apresentada à Universidade de Aveiro para cumprimento dos requisitos necessários à obt enção do grau de Doutor em Biologia, realizada sob a orientação científica da Professora Doutora Maria Marina Ribeiro Pais da Cunha, Professora Auxiliar do Departamento de Biologia da Universidade de Aveiro e co - orientação do Doutor Joan Baptista Claret Co mpany, I nvestigador Sénior do Institute of Marine Sciences, Espanha e do Doutor Nikolaos Lampadariou, I nvestigador do Hellenic Center for Marine Research , Grécia. Apoio financeiro da Fundação para a Ciência e a Tecnologia (FCT) e do Fundo Social Eur opeu (FSE) no âmbito do III Quadro Comunitário de Apoio , bolsa de referência (SFRH/BD/69450/2010) , e dos projetos: - DESEAS (EEC DG Fisheries Study Contract 2000/39) - RECS (REN2002 - 04556 - C02 - 01) - BIOFUN (CTM2007 - 28739 - E) - PROMETEO (CTM2007 - 66 316 - C02/MA R) - DOSMARES (CTM2010 -

Mercury User Manual Version 10.0 Mercury User Manual
Mercury User Manual Version 10.0 Mercury User Manual All rights reserved. No parts of this work may be reproduced in any form or by any means - graphic, electronic, or mechanical, including photocopying, recording, taping, or information storage and retrieval systems - without the written permission of the publisher. Products that are referred to in this document may be either trademarks and/or registered trademarks of the respective owners. The publisher and the author make no claim to these trademarks. While every precaution has been taken in the preparation of this document, the publisher and the author assume no responsibility for errors or omissions, or for damages resulting from the use of information contained in this document or from the use of programs and source code that may accompany it. In no event shall the publisher and the author be liable for any loss of profit or any other commercial damage caused or alleged to have been caused directly or indirectly by this document. Printed: Mai 2018 Mercury Manual Contents I Table of Contents 1 Introduction 10 2 Requirements 10 3 Installation & Licensing 11 4 Principles 13 4...1....Components.................... ........................................................................................................ 13 4...2....The...... .Standard.............. ..Application................. .................................................................................... 13 4...3....Input........ .Interface.............. .In... .Detail......... ...................................................................................... -

Component Model Based Testing
UniTESK: Component Model Based Testing Alexander K. Petrenko1, Victor Kuliamin1 and Andrey Maksimov1 1 Institute for System Programming of Russian Academy of Sciences (petrenko, kuliamin, andrew)@ispras.ru Abstract. UniTESK is a testing technology based on formal models or formal specifications of requirements to the behavior of software and hardware com- ponents. The most significant applications of UniTESK in industrial projects are described, the experience is summarized, and the prospective directions to the Component Model Based Testing development are estimated. Keywords. Specification, verification, model-based testing, automated test generation Key terms. SoftwareSystem, FormalMethod, SpecificationProcess, Verifica- tionProcess 1 Introduction Model Based testing (MBT) is a rapidly developing domain of software engineering. One of the reasons for such rapid development is the fact that MBT is at the intersec- tion of various other domains of software engineering. In particular, those domains include methods for defining, formalization and modeling of requirements, methods for analysis of both formal specification and formal models as well as the software code, methods for abstraction level control, model transformation and many other software engineering domains. It provides MBT with the ability to quickly adopt the recent achievements proved to be useful in joint domains, in particular, in methods of static analysis and mixed static/dynamic analysis. However, there is no market-ready well-established MBT tool that could be recommended for use in wide range of soft- ware development and testing projects. To further develop MBT, we should first ana- lyze the experience gained in the last 15-20 years in this domain. This should help to identify some common problems and focus on their solutions. -
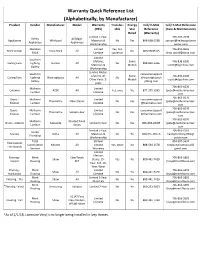
Warranty Quick Reference List (Alphabetically, by Manufacturer)
Warranty Quick Reference List (Alphabetically, by Manufacturer) Product Vendor Manufacturer Model Warranty Transfer- Energy Cell/ E-Mail Cell/ E-Mail Reference (YRS) able Star Reference (Care & Maintenance) Rated (Warranty) Limited 1-Year, 706-267-7098 Kelley All Major Appliances Whirlpool Materials & No Yes 866-698-2538 zachary@kelleyappliance Appliances Appliances Workmanship center.com Meridian Limited Yes, first 706-855-0603 Brick Veneer Boral Brick All No 800-5BORAL5 Brick Lifetime successor [email protected] Limited Southern Lifetime, Some 706-836-6200 Ceiling Fans Lighting Hunter All No 888-830-1326 Materials & Models [email protected] Gallery Workmanship Limited Motor: Southern consumersupport Lifetime, All Some 706-836-6200 Ceiling Fans Lighting Westinghouse All No @westinghouseli Other Parts: 2- Models [email protected] Gallery ghting.com years 706-863-6070 Mulherin Limited Columns AZEK All Yes, once No 877-275-2935 /pete@mulherinlumber. Lumber Lifetime com 706-863-6070 Doors - Mulherin Limited consumersupport ThermaTru Fiber-Classic No Yes /pete@mulherinlumber. Exterior Lumber Lifetime @thermatru.com com 706-863-6070 Doors - Mulherin Limited consumersupport ThermaTru Smooth-Star No Yes /pete@mulherinlumber. Exterior Lumber Lifetime @thermatru.com com 706-863-6070 Mulherin Molded Panel Doors - Interior Masonite Limited 1-Year No Yes 800-663-DOOR /pete@mulherinlumber. Lumber Series com Limited 5-Year, 706-863-2110 Hardy Faucets Delta All Materials & No No 800-345-DELTA hardyplumbing1961@ Plumbing Workmanship yahoo.com -

Vysoké Učení Technické V Brně Brno University of Technology
VYSOKÉ UČENÍ TECHNICKÉ V BRNĚ BRNO UNIVERSITY OF TECHNOLOGY FAKULTA INFORMAČNÍCH TECHNOLOGIÍ ÚSTAV POČÍTAČOVÝCH SYSTÉMŮ FACULTY OF INFORMATION TECHNOLOGY DEPARTMENT OF COMPUTER SYSTEMS OPERAČNÍ SYSTÉM PRO ŘÍZENÍ VESTAVĚNÝCH APLIKACÍ OPERATING SYSTEM FOR EMBEDDED APPLICATIONS CONTROL BAKALÁŘSKÁ PRÁCE BACHELOR‘S THESIS AUTOR PRÁCE TOMÁŠ KOLARÍK AUTHOR VEDOUCÍ PRÁCE Ing. VÁCLAV ŠIMEK SUPERVISOR BRNO 2009 Abstrakt Práce se zabývá výběrem operačního systému pro vestavěnou řídící jednotku parního sterilizátoru obsluhující barevný displej s dotekovým panelem. Na teoretické úrovni se zabývá architekturou vestavěných systémů a operačních systémů. U nich je pozornost soustředěna na správu procesů. Dále se zabývá přístrojem, pro nějž je vybírán operační systém, důvody pro jeho zavedení, jeho výhodami a nevýhodami v řídícím systému. Pak je součástí práce přehled a rozdělení OS do kategorií podle způsobu použití. A blíže jsou popsány dva open source operační systémy eCos a FreeRTOS. Z nich byl následně kód FreeRTOSe upraven z překladače GCC na překladač IAR. Poslední část práce popisuje architekturu a funkcionalitu vytvořené ukázkové aplikace. Ta pomocí dotekového panelu a barevného displeje umožňuje kreslit barevné nákresy, které se dají pomocí sériové komunikace přenášet do počítače. Abstract This thesis deals with selection of operating system for embedded control unit of steam sterilizer with color touch screen. Theoretical part of the thesis deals with the architecture of embedded systems and operating systems with focus on process management. In addition, the thesis deals with a device for which the operating system is selected, the reason for its implementation, advantages and disadvantages in the control system. The thesis also contains categorization of operating systems by way of use. Of these, two open source operating systems eCos and FreeRTOS are described more thoroughly. -

Sensor Intelligence. from SICK
PRODUCT OVERVIEW Sensor Intelligence. From SICK. Solutions for factory and logistics automation A Technology Leader for More than 60 Years Innovation Leadership What does SICK stand for? Expertise Independence Experience A Technology Leader in Factory and Logistics Automation SICK is one of the world’s leading manufacturers of sensors, safety systems and automatic identification solutions. Our high quality products range from simple sensors and laser-based bar code scanners… to machine vision and safety laser scanners… to complex camera arrays. Our superior technological expertise, broad product line, and vast application experience enables us to continually find new and better ways to help our customers achieve their goals. A Continuous Drive for Innovative Solutions Since its humble beginning 60 years ago, SICK has made research and development a priority and central strategic component -- spending nine percent of revenue on R&D. More than 450 people at SICK are dedicated to R&D, constantly creating new ways to solve customers' applications. 2 SENSORS AND SENSOR SYSTEMS | Sick AUTOMOTIVE INDUSTRY TRANSPORT VEHICLES MACHINE TOOLS SICK always puts you in the fast Sensors ensure safe Cutting edge safety and productivity lane in automotive manufacturing. navigation, e.g. for automated at high speeds. guided vehicles. TRUMPF TEXTILES FOOD BEVERAGES Ensure you stay competitive in Reliable solutions for strict hygienic Ensuring the label matches the the clothing industry. production conditions. contents. COSMETICS PHARMACEUTICALS DRIVE TECHNOLOGY Reliable inspections for the SICK solutions ensure maximum Accurate movements and great beauty industry. precision when health is at stake. power under control. ELECTRONICS TIMBER AND FURNITURE PRINT AND PAPER It is precisely in the smallest of SICK sensors enable detailed Ensuring that printed material passes dimensions that the electronic “senses” precision when thick planks through the machines quickly and automatically ensure best results. -

T EC H N I C a L S P E CIF I CATIO N S ASSA ABLOY Oak Island
T E C H N I C A L S P E CIF I CATIO N S ASSA ABLOY Oak Island OS1000 and OS2000 PART 1 GENERAL 1.01 Section 2.06 Hardware Sectional Doors are to be ASSA ABLOY OAK ISLAND OS1000 Hardware includes minimum 14 gauge galvanized steel center and ASSA BLOY OAK ISLAND OS2000 as manufactured by hinges and minimum 14 gauge galvanized steel roller hinges. All ASSA ABLOY Entrance Systems. Operation to be manual rollers to be 7 ball steel. Galvanized struts (truss bars) supplied on pushup. Mounting to be interior face mounted on a prepared all doors 15’ and wider to prevent deflection no more than 1/120 surface. of the spanned width when in the open position. Interior and 1.02 Quality Assurance exterior lift handles provided. All fasteners are galvanized. All Doors shall be steel sectional overhead type. Each door hardware is covered by a 2-year warranty (OAK ISLAND OS2000) includes sections, brackets, tracks, counter-balance or a 1-year warranty (OAK ISLAND OS1000). mechanisms and hardware to suit the opening and headroom available. 2.07 Spring Counter-balance Extension springs for door counter-balance are mounted and 1.03 Related Work attached to the supporting horizontal angle and back support of the Opening preparation, miscellaneous or structural steel, finish or horizontal track assembly. Each spring shall be equipped with a field painting are in the scope of the work of other entities. device capable of restraining the spring or any part thereof in case of breakage. Torsion springs for door counter-balance are mounted PART 2 PRODUCT on a continuous cross header shaft. -

Xerox 4850/4890 Highlight Color Laser Printing Systems Messages
XEROX Xerox 4850/4890 HighLight Color Laser Printing Systems Message Guide Version 5.0 November 1994 720P93620 Xerox Corporation 701 S. Aviation Boulevard El Segundo, CA 90245 © 1994 by Xerox Corporation. All rights reserved. Copyright protection claimed includes all forms and matters of copyrightable material and information now allowed by statutory or judicial law or hereinafter granted, including without limitation, material generated from the software programs which are displayed on the screen, such as icons, screen displays, looks, etc. Printed in the United States of America Publication number: 720P93620 Xerox® and all Xerox products mentioned in this publication are trademarks of Xerox Corporation. Products and trademarks of other companies are also acknowledged. Changes are periodically made to this document. Changes, technical inaccuracies, and typographic errors will be corrected in subsequent editions. This document was created on the Xerox 6085 Professional Computer System using VP software. The typefaces used are Optima, Terminal, and monospace. Table of contents Introduction v Conventions v 1. COMPRESS (CP) command messages 1-1 2. Data Capture Utility (DCU) messages 2-1 System failure or reload messages 2-6 3. Disk Save and Restore (DSR) messages 3-1 4. File Conversion Utility (FCU) messages 4-1 5. General floppy utility (FLF) messages 5-1 FLF messages 5-15 6. Forms compilation (FD) messages 6-1 7. Host Interface Processor (HIP) messages 7-1 8. Interpress font utility (IFU) messages 8-1 9. Operating system software (OSS) messages 9-1 OS level 0: Confirmation messages 9-1 OS level 1: Informational messages 9-10 OS level 2: Routine maintenance messages 9-41 OS level 3: Printer problem messages 9-66 OS level 4: System or tape problem messages 9-71 OS level 6: Job integrity problem messages 9-75 OS level 7: System problem messages 9-96 OS level 8: Probable severe software errors 9-101 OS level 9: Probable severe hardware errors 9-107 10. -

Vladimir Yu. Ivanov
Vladimir Yu. Ivanov º +7·924·320·09·34 j 8 [email protected] j vladimir-yu-ivanov Saint Petersburg, Russian Federation SUMMARY Proficient engineer (8+ yoe) with a focus on the EECS. Visited various electronics plants as board bring-up engineer for customer products. Helped robotic startup on the early stages of company formation. Services in HW and SW domains from development to deployment. Main areas of interest: consumer electronics, industrial and mobile robotics, automotive industry, high quality products, mechatronics, cyber-physical systems, technologies impact on human beings and on economics. SKILLS · Computer languages: plain C, C++17 and STL, Python, Bash, TeX, 8-bit assembler. · Development tools: gcc, gdb, Make, CMake, Docker, Vagrant, Ansible, Jenkins, SAST. · Various technologies: TCP/IP, REST, Maxima, Actor Model, deb-packages. · Version control systems: Subversion, Perforce, Git (main). · Software platforms: POSIX, WinAPI, RTOS, ROS, Qt. · Embedded systems: MCU, PLC, PCBA, Buildroot, device drivers, semiconductors, EE-lab equipment. EXPERIENCE TRA robotics June 2017 { present Lead Software Engineer (full-time) Saint Petersburg, Russian Federation · Transnational technological company around Industry 4.0 and smart manufacturing. · Implemented SW for robotic tool controller as a member of multi-domain team. Presented HW and SW design proposals, performed initial SW implementation and controller integration into factory SW ecosystem. Launched 3 kinds of tools: Schunk's jaw-gripper, tool-changer and custom glue-gun. Stack: C++17, CMake, Boost, POCO, CAF, yaml-cpp, Python, PyTest, Bash, Docker, Vagrant, Systemd, Ansible, Doxygen, RPi CM, STM32. · Helped to interview and to on-board 2 candidates for Embedded Engineer team role to cover controller's HW part. -

High Spatiotemporal Variability in Meiofaunal Assemblages in Blanes
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Digital.CSIC 1 High spatiotemporal variability in meiofaunal assemblages in Blanes Canyon (NW 2 Mediterranean) subject to anthropogenic and natural disturbances 3 4 Sara Román1*, Ann Vanreusel2, Chiara Romano1,3, Jeroen Ingels4, Pere Puig5, Joan 5 Batista Company5, Daniel Martin1 6 7 8 1 Centre d’Estudis Avançats de Blanes (CEAB-CSIC), c/ Accés a la Cala St. Francesc, 14, E-17300 9 Blanes, Spain. 10 2 Marine Biology Department, Ghent University, Krijgslaan 281 S8, B-90000 Ghent, Belgium. 11 3 Present address : Marine Invertebrate Phylogenetics Lab Scripps Institution of Oceanography, 8750 12 Biological Grade, Hubbs Hall, La Jolla, CA 92037, USA 13 4 Plymouth Marine Laboratory, Prospect Place, West Hoe, PL1 3DH, Plymouth, United Kingdom. 14 5Institut de Ciènces del Mar (ICM-CSIC), 08003 Barcelona (Spain) 15 16 *Corresponding author : sara.romanm@gmail.com 17 18 19 20 1. ABSTRACT 21 We investigated the natural and anthropogenic drivers controlling the spatiotemporal 22 distribution of the meiofauna in the submarine Blanes Canyon, and its adjacent western 23 slope (NW Mediterranean margin of the Iberian Peninsula). We analyzed the 24 relationships between the main sedimentary environmental variables (i.e. grain size, 25 Chl-a, Chl-a:phaeopigments, CPE, organic carbon and total nitrogen) and the density 26 and structure of the meiofaunal assemblages along a bathymetric gradient (from 500 to 27 2000 m depth) in spring and autumn of 2012 and 2013. 28 Twenty-one and 16 major taxa were identified for respectively the canyon and slope, 29 where the assemblages were always dominated by nematodes. -

Role of Spatial Scales and Environmental Drivers in Shaping Nematode Communities in the Blanes Canyon and Its Adjacent Slope
Author’s Accepted Manuscript Role of spatial scales and environmental drivers in shaping nematode communities in the Blanes Canyon and its adjacent slope Sara Román, Lidia Lins, Jeroen Ingels, Chiara Romano, Daniel Martin, Ann Vanreusel www.elsevier.com PII: S0967-0637(18)30323-6 DOI: https://doi.org/10.1016/j.dsr.2019.03.002 Reference: DSRI3012 To appear in: Deep-Sea Research Part I Received date: 5 November 2018 Revised date: 21 February 2019 Accepted date: 4 March 2019 Cite this article as: Sara Román, Lidia Lins, Jeroen Ingels, Chiara Romano, Daniel Martin and Ann Vanreusel, Role of spatial scales and environmental drivers in shaping nematode communities in the Blanes Canyon and its adjacent slope, Deep-Sea Research Part I, https://doi.org/10.1016/j.dsr.2019.03.002 This is a PDF file of an unedited manuscript that has been accepted for publication. As a service to our customers we are providing this early version of the manuscript. The manuscript will undergo copyediting, typesetting, and review of the resulting galley proof before it is published in its final citable form. Please note that during the production process errors may be discovered which could affect the content, and all legal disclaimers that apply to the journal pertain. Role of spatial scales and environmental drivers in shaping nematode communities in the Blanes Canyon and its adjacent slope Sara Romána, Lidia Linsb,c, Jeroen Ingelsd, Chiara Romanoa,e,*, Daniel Martina, Ann Vanreuselb aCentre d’Estudis Avançats de Blanes (CEAB-CSIC), c/ Accés a la Cala St. Francesc, 14, E-17300 Blanes, Spain. -

Xerox Docuprint 96/Docuprint 96MX Laser Printing System Message Guide
Xerox DocuPrint 96/DocuPrint 96MX Laser Printing System Message Guide April 1998 721P85650 Xerox Corporation 701 S. Aviation Boulevard El Segundo, CA 90245 ©1998 by Xerox Corporation. All rights reserved. Copyright protection claimed includes all forms and matters of copyrightable material and information now allowed by statutory or judicial law or hereinafter granted, including without limitation, material generated from the software programs which are displayed on the screen, such as icons, screen displays, looks, etc. Printed in the United States of America. Publication number: 721P85650 Xerox® and all Xerox products mentioned in this publication are trademarks of Xerox Corporation. Products and trademarks of other companies are also acknowledged. Changes are periodically made to this document. Changes, technical inaccuracies, and typographic errors will be corrected in subsequent editions. This document was created on a PC using Frame software. The typeface used is Helvetica. Related publications The Xerox DocuPrint 96/DocuPrint 96MX Laser Printing System Message Guide is part of the eight manual reference set for your laser printing system. The entire reference set is listed in the table below. Several other related documents are also listed for your convenience. For a complete list and description of available Xerox documentation, refer to the Xerox Documentation Catalog (Publication number 610P17417) or call the Xerox Documentation and Software Services (XDSS) at 1-800-327-9753. Table 1. Related Publications Publication Number Xerox