Revealing How Linux Kernel Put User at Risk
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
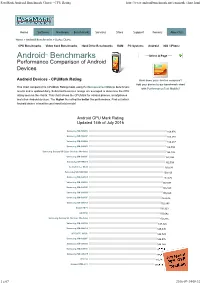
Passmark Android Benchmark Charts - CPU Rating
PassMark Android Benchmark Charts - CPU Rating http://www.androidbenchmark.net/cpumark_chart.html Home Software Hardware Benchmarks Services Store Support Forums About Us Home » Android Benchmarks » Device Charts CPU Benchmarks Video Card Benchmarks Hard Drive Benchmarks RAM PC Systems Android iOS / iPhone Android TM Benchmarks ----Select A Page ---- Performance Comparison of Android Devices Android Devices - CPUMark Rating How does your device compare? Add your device to our benchmark chart This chart compares the CPUMark Rating made using PerformanceTest Mobile benchmark with PerformanceTest Mobile ! results and is updated daily. Submitted baselines ratings are averaged to determine the CPU rating seen on the charts. This chart shows the CPUMark for various phones, smartphones and other Android devices. The higher the rating the better the performance. Find out which Android device is best for your hand held needs! Android CPU Mark Rating Updated 14th of July 2016 Samsung SM-N920V 166,976 Samsung SM-N920P 166,588 Samsung SM-G890A 166,237 Samsung SM-G928V 164,894 Samsung Galaxy S6 Edge (Various Models) 164,146 Samsung SM-G930F 162,994 Samsung SM-N920T 162,504 Lemobile Le X620 159,530 Samsung SM-N920W8 159,160 Samsung SM-G930T 157,472 Samsung SM-G930V 157,097 Samsung SM-G935P 156,823 Samsung SM-G930A 155,820 Samsung SM-G935F 153,636 Samsung SM-G935T 152,845 Xiaomi MI 5 150,923 LG H850 150,642 Samsung Galaxy S6 (Various Models) 150,316 Samsung SM-G935A 147,826 Samsung SM-G891A 145,095 HTC HTC_M10h 144,729 Samsung SM-G928F 144,576 Samsung -

Presentación De Powerpoint
Modelos compatibles de Imóvil No. Marca Modelo Teléfono Versión del sistema operativo 1 360 1501_M02 1501_M02 Android 5.1 2 100+ 100B 100B Android 4.1.2 3 Acer Iconia Tab A500 Android 4.0.3 4 ALPS (Golden Master) MR6012H1C2W1 MR6012H1C2W1 Android 4.2.2 5 ALPS (Golden Master) PMID705GTV PMID705GTV Android 4.2.2 6 Amazon Fire HD 6 Fire HD 6 Fire OS 4.5.2 / Android 4.4.3 7 Amazon Fire Phone 32GB Fire Phone 32GB Fire OS 3.6.8 / Android 4.2.2 8 Amoi A862W A862W Android 4.1.2 9 amzn KFFOWI KFFOWI Android 5.1.1 10 Apple iPad 2 (2nd generation) MC979ZP iOS 7.1 11 Apple iPad 4 MD513ZP/A iOS 7.1 12 Apple iPad 4 MD513ZP/A iOS 8.0 13 Apple iPad Air MD785ZP/A iOS 7.1 14 Apple iPad Air 2 MGLW2J/A iOS 8.1 15 Apple iPad Mini MD531ZP iOS 7.1 16 Apple iPad Mini 2 FE276ZP/A iOS 8.1 17 Apple iPad Mini 3 MGNV2J/A iOS 8.1 18 Apple iPhone 3Gs MC132ZP iOS 6.1.3 19 Apple iPhone 4 MC676LL iOS 7.1.2 20 Apple iPhone 4 MC603ZP iOS 7.1.2 21 Apple iPhone 4 MC604ZP iOS 5.1.1 22 Apple iPhone 4s MD245ZP iOS 8.1 23 Apple iPhone 4s MD245ZP iOS 8.4.1 24 Apple iPhone 4s MD245ZP iOS 6.1.2 25 Apple iPhone 5 MD297ZP iOS 6.0 26 Apple iPhone 5 MD298ZP/A iOS 8.1 27 Apple iPhone 5 MD298ZP/A iOS 7.1.1 28 Apple iPhone 5c MF321ZP/A iOS 7.1.2 29 Apple iPhone 5c MF321ZP/A iOS 8.1 30 Apple iPhone 5s MF353ZP/A iOS 8.0 31 Apple iPhone 5s MF353ZP/A iOS 8.4.1 32 Apple iPhone 5s MF352ZP/A iOS 7.1.1 33 Apple iPhone 6 MG492ZP/A iOS 8.1 34 Apple iPhone 6 MG492ZP/A iOS 9.1 35 Apple iPhone 6 Plus MGA92ZP/A iOS 9.0 36 Apple iPhone 6 Plus MGAK2ZP/A iOS 8.0.2 37 Apple iPhone 6 Plus MGAK2ZP/A iOS 8.1 -

Phone Compatibility
Phone Compatibility • Compatible with iPhone models 4S and above using iOS versions 7 or higher. Last Updated: February 14, 2017 • Compatible with phone models using Android versions 4.1 (Jelly Bean) or higher, and that have the following four sensors: Accelerometer, Gyroscope, Magnetometer, GPS/Location Services. • Phone compatibility information is provided by phone manufacturers and third-party sources. While every attempt is made to ensure the accuracy of this information, this list should only be used as a guide. As phones are consistently introduced to market, this list may not be all inclusive and will be updated as new information is received. Please check your phone for the required sensors and operating system. Brand Phone Compatible Non-Compatible Acer Acer Iconia Talk S • Acer Acer Jade Primo • Acer Acer Liquid E3 • Acer Acer Liquid E600 • Acer Acer Liquid E700 • Acer Acer Liquid Jade • Acer Acer Liquid Jade 2 • Acer Acer Liquid Jade Primo • Acer Acer Liquid Jade S • Acer Acer Liquid Jade Z • Acer Acer Liquid M220 • Acer Acer Liquid S1 • Acer Acer Liquid S2 • Acer Acer Liquid X1 • Acer Acer Liquid X2 • Acer Acer Liquid Z200 • Acer Acer Liquid Z220 • Acer Acer Liquid Z3 • Acer Acer Liquid Z4 • Acer Acer Liquid Z410 • Acer Acer Liquid Z5 • Acer Acer Liquid Z500 • Acer Acer Liquid Z520 • Acer Acer Liquid Z6 • Acer Acer Liquid Z6 Plus • Acer Acer Liquid Zest • Acer Acer Liquid Zest Plus • Acer Acer Predator 8 • Alcatel Alcatel Fierce • Alcatel Alcatel Fierce 4 • Alcatel Alcatel Flash Plus 2 • Alcatel Alcatel Go Play • Alcatel Alcatel Idol 4 • Alcatel Alcatel Idol 4s • Alcatel Alcatel One Touch Fire C • Alcatel Alcatel One Touch Fire E • Alcatel Alcatel One Touch Fire S • 1 Phone Compatibility • Compatible with iPhone models 4S and above using iOS versions 7 or higher. -
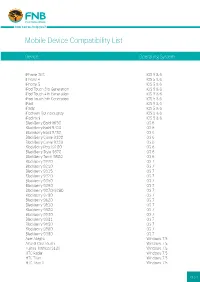
Mobile Device Compatibility List
Mobile Device Compatibility List Device Operating System iPhone 3GS IOS 5 & 6 iPhone 4 IOS 5 & 6 iPhone 5 IOS 5 & 6 iPod Touch 3rd Generation IOS 5 & 6 iPod Touch 4th Generation IOS 5 & 6 iPod Touch 5th Generation IOS 5 & 6 iPad IOS 5 & 6 iPad2 IOS 5 & 6 iPad with Retina display IOS 5 & 6 iPad mini IOS 5 & 6 BlackBerry Bold 9650 OS 6 BlackBerry Bold 9700 OS 6 BlackBerry Bold 9780 OS 6 BlackBerry Curve 9300 OS 6 BlackBerry Curve 9330 OS 6 BlackBerry Pearl 9100 OS 6 BlackBerry Style 9670 OS 6 BlackBerry Torch 9800 OS 6 Blackberry 9220 OS 7 Blackberry 9310 OS 7 Blackberry 9315 OS 7 Blackberry 9320 OS 7 Blackberry 9350 OS 7 Blackberry 9360 OS 7 Blackberry 9370/9380 OS 7 Blackberry 9790 OS 7 Blackberry 9620 OS 7 Blackberry 9810 OS 7 Blackberry 9900 OS 7 Blackberry 9930 OS 7 Blackberry 9981 OS 7 Blackberry 9850 OS 7 Blackberry 9860 OS 7 Blackberry 9380 OS 7 Acer Allegro Windows 7.5 Alcatel One Touch Windows 7.5 Fujitsu Toshiba IS12T Windows 7.5 HTC Radar Windows 7.5 HTC Titan Windows 7.5 HTC Titan II Windows 7.5 Pg 1/3 Device Operating System Nokia Lumia 510 Windows 7.5 Nokia Lumia 610 Windows 7.5 Nokia Lumia 710 Windows 7.5 Nokia Lumia 800 Windows 7.5 Nokia Lumia 900 Windows 7.5 Samsung Focus 2 Windows 7.5 Samsung Focus S Windows 7.5 Samsung Omnia M Windows 7.5 Super AMOLED Windows 7.5 Samsung Omnia W Windows 7.5 ZTE Orbit (Render) Windows 7.5 ZTE Tania (Spirit) Windows 7.5 HTC Windows Phone 8S Windows 8 HTC Windows Phone 8X Windows 8 Huawei Ascend W1 Windows 8 Nokia Lumia 520 Windows 8 Nokia Lumia 620 Windows 8 Nokia Lumia 720 Windows 8 Nokia -

Fnac Reprise
FNAC REPRISE Liste des smartphones éligibles au programme de reprise au 19/08/2016 ACER LIQUID Z4 APPLE IPHONE 5 BLACK 64GB ACER INCORPORATED LIQUID Z530S APPLE IPHONE 5 WHITE 16GB ACER INCORPORATED LIQUID Z630S APPLE IPHONE 5 WHITE 32GB ALBA ALBA 4.5INCH 5MP 4G 8GB APPLE IPHONE 5 WHITE 64GB ALBA DUAL SIM APPLE IPHONE 5C ALCATEL IDOL 3 8GB APPLE IPHONE 5C BLUE 16GB ALCATEL ONE TOUCH 228 APPLE IPHONE 5C BLUE 32GB ALCATEL ONE TOUCH 903 APPLE IPHONE 5C BLUE 8GB ALCATEL ONE TOUCH 903X APPLE IPHONE 5C GREEN 16GB ALCATEL ONE TOUCH IDOL 2 MINI S APPLE IPHONE 5C GREEN 32GB ALCATEL ONE TOUCH TPOP APPLE IPHONE 5C GREEN 8GB ALCATEL ONETOUCH POP C3 APPLE IPHONE 5C PINK 16GB AMAZON FIRE PHONE APPLE IPHONE 5C PINK 32GB APPLE APPLE WATCH EDITION 42MM APPLE IPHONE 5C PINK 8GB APPLE IPHONE 3G APPLE IPHONE 5C WHITE 16GB APPLE IPHONE 3G BLACK 16GB APPLE IPHONE 5C WHITE 32GB APPLE IPHONE 3G BLACK 8GB APPLE IPHONE 5C WHITE 8GB APPLE IPHONE 3G WHITE 16GB APPLE IPHONE 5C YELLOW 16GB APPLE IPHONE 3GS APPLE IPHONE 5C YELLOW 32GB APPLE IPHONE 3GS 8GB APPLE IPHONE 5C YELLOW 8GB APPLE IPHONE 3GS BLACK 16GB APPLE IPHONE 5S APPLE IPHONE 3GS BLACK 32GB APPLE IPHONE 5S BLACK 16GB APPLE IPHONE 3GS WHITE 16GB APPLE IPHONE 5S BLACK 32GB APPLE IPHONE 3GS WHITE 32GB APPLE IPHONE 5S BLACK 64GB APPLE IPHONE 4 APPLE IPHONE 5S GOLD 16GB APPLE IPHONE 4 BLACK 16GB APPLE IPHONE 5S GOLD 32GB APPLE IPHONE 4 BLACK 32GB APPLE IPHONE 5S GOLD 64GB APPLE IPHONE 4 BLACK 8GB APPLE IPHONE 5S WHITE 16GB APPLE IPHONE 4 WHITE 16GB APPLE IPHONE 5S WHITE 32GB APPLE IPHONE 4 WHITE 32GB APPLE IPHONE -
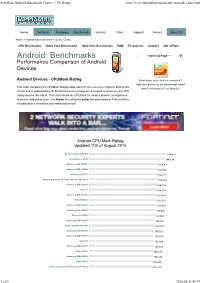
Passmark Android Benchmark Charts - CPU Rating
PassMark Android Benchmark Charts - CPU Rating http://www.androidbenchmark.net/cpumark_chart.html Home Software Hardware Benchmarks Services Store Support Forums About Us Home » Android Benchmarks » Device Charts CPU Benchmarks Video Card Benchmarks Hard Drive Benchmarks RAM PC Systems Android iOS / iPhone Android TM Benchmarks ----Select A Page ---- Performance Comparison of Android Devices Android Devices - CPUMark Rating How does your device compare? Add your device to our benchmark chart This chart compares the CPUMark Rating made using PerformanceTest Mobile benchmark with PerformanceTest Mobile ! results and is updated daily. Submitted baselines ratings are averaged to determine the CPU rating seen on the charts. This chart shows the CPUMark for various phones, smartphones and other Android devices. The higher the rating the better the performance. Find out which Android device is best for your hand held needs! Android CPU Mark Rating Updated 11th of August 2016 Samsung SM-G930W8 189,083 Lemobile Le X520 184,124 Samsung SM-N920P 168,971 Samsung SM-G890A 167,226 Samsung SCV31 166,812 Samsung Galaxy S6 Edge (Various Models) 165,338 Samsung SM-G928V 164,894 HTC 10 164,138 Samsung SM-G930F 163,461 HTC 2PS5200 163,113 Samsung SM-N920V 163,087 Samsung SM-N920T 162,504 Oneplus A3003 159,868 Samsung SM-G935F 159,781 Samsung SM-N920W8 159,160 Samsung SM-G930T 158,021 Samsung SM-G930V 157,587 LG H820 156,995 Samsung SM-G935P 156,823 Cmdc M836 156,217 Samsung SM-G930A 155,820 Xiaomi MI 5 152,639 Samsung Galaxy S6 (Various Models) 152,343 1 -
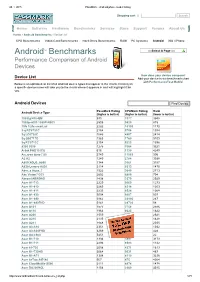
Androidtm Benchmarks
28. 1. 2015 PassMark Android phone model listing Shopping cart | Search Home Software Hardware Benchmarks Services Store Support Forums About Us Home » Android Benchmarks » Device List CPU Benchmarks Video Card Benchmarks Hard Drive Benchmarks RAM PC Systems Android iOS / iPhone TM Select A Page Android Benchmarks Performance Comparison of Android Devices How does your device compare? Device List Add your device to our benchmark chart with PerformanceTest Mobile! Below is an alphabetical list of all Android device types that appear in the charts. Clicking on a specific device name will take you to the charts where it appears in and will highlight it for you. Android Devices Find Device PassMark Rating CPUMark Rating Rank Android Device Type (higher is better) (higher is better) (lower is better) 1005tg N10QM 935 3377 3948 1080pn003 1080PN003 2505 9820 815 1life 1Life.smart.air 2282 10103 1170 3q RC9731C 2154 5756 1394 3q LC0720C 1646 4897 2414 3q QS0717D 1363 1760 3109 3q RC9712C 2154 5223 1396 9300 9300 1275 3364 3321 Alink PAD10 ICS 616 1130 4249 A.c.ryan dyno 7.85 2749 11065 596 A2 A2 1240 2784 3388 A800 XOLO_A800 1344 3661 3157 A830 Lenovo A830 2114 8313 1470 Abs_a Aqua_7 1522 3640 2713 Abc Vision7DCI 2602 6880 704 Abroad ABROAD 1438 3379 2929 Acer A1713 2229 9069 1273 Acer A1810 2265 8314 1203 Acer A1811 2233 8524 1268 Acer A1830 3004 9207 507 Acer A1840 3962 23996 267 Acer A1840FHD 5141 28720 58 Acer A101 1577 3758 2586 Acer A110 1964 8623 1822 Acer A200 1559 3822 2621 Acer A210 2135 8315 1428 Acer A211 1848 8130 2035 Acer A3A10 2351 8128 1032 Acer A3A20FHD 3269 11265 428 Acer AA3600 5451 22392 22 Acer B1710 1336 3897 3173 Acer B1711 2293 8583 1142 Acer b1720 2058 4371 1613 Acer B1730HD 3064 9031 487 Acer B1A71 1308 4119 3236 Acer beTouch E140 567 475 4264 Acer CloudMobile S500 2111 4874 1478 Acer DA220HQL 1156 2960 3545 http://www.androidbenchmark.net/device_list.php 1/71 28. -

Manufacturer Device Model Consumers Count Apple Iphone
Manufacturer Device Model Consumers Count Apple iPhone 24,666,239 Apple iPad 13,155,907 samsung SM-J500M 1,079,744 Apple iPod touch 1,070,538 samsung SM-G531H 1,043,553 samsung SM-G935F 1,026,327 samsung SM-T113 894,096 samsung SM-J700M 888,680 motorola MotoG3 860,116 samsung SM-J700F 847,315 samsung SM-G920F 834,655 samsung SM-G900F 827,050 samsung SM-G610F 786,659 HUAWEI ALE-L21 783,180 OPPO A37f 701,488 samsung SM-G955U 699,321 samsung SM-G930F 685,195 samsung SM-J510FN 673,415 samsung SM-G950U 654,635 samsung SM-G530H 651,695 samsung SM-J710F 647,723 motorola Moto G (4) 640,091 samsung SM-T110 627,013 samsung SM-J200G 611,728 OPPO A1601 588,226 samsung SM-G925F 571,858 samsung SM-G930V 557,813 samsung SM-A510F 533,209 ZTE Z981 532,290 samsung GT-I9300 516,580 samsung SM-J320FN 511,109 Xiaomi Redmi Note 4 507,119 samsung GT-I9505 504,325 samsung GT-I9060I 488,253 samsung SM-J120H 472,748 samsung SM-G900V 458,996 Xiaomi Redmi Note 3 435,822 samsung SM-A310F 435,163 samsung SM-T560 435,042 motorola XT1069 433,667 motorola Moto G Play 422,147 LGE LG-K430 406,009 samsung GT-I9500 392,674 Xiaomi Redmi 3S 388,092 samsung SM-J700H 384,922 samsung SM-G532G 384,884 samsung SM-N9005 382,982 samsung SM-G531F 382,728 motorola XT1033 380,899 Generic Android 7.0 374,405 motorola XT1068 373,075 samsung SM-J500FN 372,029 samsung SM-J320M 366,049 samsung SM-J105B 351,985 samsung SM-T230 348,374 samsung SM-T280 347,350 samsung SM-T113NU 341,313 samsung SM-T350 338,525 samsung SM-G935V 337,090 samsung SM-J500F 332,972 samsung SM-J320F 329,165 motorola -

SMART-PHONE SUB-PANEL (April 2013)
W&S Company Limited is one of the top online market research service provider in Vietnam. In 2011, we established our actively managed panel named "Vinaresearch" and it has reached number of over 105,000 members since January 2013. SMART-PHONE SUB-PANEL (April 2013) This sub-panel is based on Single-choice question type with a total of 6,564 respondents from Vinaresearch Panel. Statistical result includes tables in following content: 1. Number of smartphone owners 2. Number of respondents intending to buy smartphone 3. Number of smartphones owned 4. Smartphone's most often using brand 5. Amount of money for buying current smartphone 6. Current smartphone's status 7. Place for buying current smartphone 8. Purchasing time 9. Future smartphone brands 10. Price of future smartphone brands 1. Number of smartphone owners [SA] (n=6,564) Frequency Percent Total 6,564 100.0% Own a smartphone 4,571 69.6% Do not own a smartphone 1,193 30.4% 2. Number of respondents intending to buy smartphone [SA] (n=6,564) Frequency Percent Total 6,564 100.0% Intend to buy 5,820 88.7% Do not intend to buy 744 11.3% 3. Number of smartphones owned [SA] (n=4,571) Frequency Percent Total 4,571 100.0% 1 3,505 76.7% 2 946 20.7% 3 96 2.1% More than 3 24 0.5% 4. Smartphone's most often using brand [SA] (n=4,571) Frequency Percent Total 4,571 100.0% Samsung 1,330 29.1% Apple 1,211 26.5% Nokia 875 19.1% HTC 261 5.7% LG 227 5.0% Sony 223 4.9% Blackberry 202 4.4% Q-mobile 55 1.2% Sky Pantech 37 0.8% Lonovo 32 0.7% HK Phone 26 0.6% Gionee 17 0.4% Mobistar 14 0.3% Viettel 13 -
Retail Branding Marketing Name Device Model AD681H
Retail Branding Marketing Name Device Model AD681H Smartfren Andromax AD681H FJL21 FJL21 T31 Panasonic T31 hws7721g MediaPad 7 Youth 2 3Q OC1020A OC1020A OC1020A 7Eleven IN265 IN265 IN265 A.O.I. ELECTRONICS FACTORY A.O.I. TR10CS1_11 TR10CS1 AG Mobile AG BOOST 2 BOOST2 E4010 AG Mobile AG Flair AG_Flair Flair AG Mobile AG Go Tab Access 2 AG_Go_Tab_Access_2 AG_Go_Tab_Access_2 AG Mobile AG Ultra2 AG_Ultra2 Ultra 2 AG Mobile AG_Go-Tab_Access md789hwag AG Go-Tab Access AG Mobile AG_Tab_7_0 AG_Tab_7_0 AG_Tab_7_0 AG Mobile Boost Boost Boost AG Mobile Chacer Chacer Chacer AG Mobile Freedom Access Freedom_Access Freedom Access AG Mobile Freedom E Freedom_E Freedom E AG Mobile Freedom Plus LTE Freedom_Plus_LTE Freedom Plus LTE AG Mobile Ghost Ghost Ghost AG Mobile Glow Glow Glow AG Mobile HASHTAG Hashtag Hashtag AG Mobile Hype Hype Hype AG Mobile Neon Neon Neon AG Mobile Quest Quest Quest AG Mobile Rage Rage Rage AG Mobile STYLE PLUS STYLE_PLUS STYLE_PLUS AG Mobile Shine Shine Shine AG Mobile Status Status Status AG Mobile Style Style Style AG Mobile Style_2 Style_2 Style 2 AG Mobile Swift Swift Swift AG Mobile Swift_Plus Swift_Plus Swift_Plus AG Mobile ULTRA Ultra Ultra AG Mobile Zenith Zenith Zenith AG Mobile Zone Zone Zone AG Mobile Zoom Zoom Zoom AMTC AMTC MD1001 Tablet MD1001 MD1001 AMTC AMTC MD7008 MD7008A MD7008 AMTC AMTC MD7081 MD7081A MD7081 ANS ANS Trailblazer rugged-smartphone H450R AOC A2272PWHT AOC_WW G2SMNT AOC AOC-A2272PW4T AOC_WW G3SMNTA22 AOC AOC-A2272PW4T AOC_WW G3SMNTA24 AOC AOC-A2472PW4T G3SMNTA24 G3SMNTA24 AT&T 9020A tint8_att -

MOBILE PHONE SUB-PANEL February 2013
W&S online market research is one of the top online market research service provider in Vietnam. Since 2011, we established our actively managed panel "Vinaresearch" and it has reached the number of over 104,000 members in December, 2012. MOBILE PHONE SUB-PANEL February 2013 This sub-panel publication is based on single-choice and multiple-choice questionnaire types with a total of 5,961 qualified respondents from Vinaresearch Panel. Statistic result includes tables in following content: 1.Type of mobile phone brand using 2.Number of mobile phone owned 3.Purchasing time 4.Mobile phone' status 5.Place for buying mobile phone 6.The reason why choosing the mobile phone brand using 1.Type of mobile phone brand using <SA> n= 5,964 Frequency Percent Total 5,961 100.0% Nokia 2,626 43.9% Samsung 1,311 22.0% Apple 598 10.0% LG 269 4.5% Sony Ecrission 242 4.1% HTC 191 3.2% BlackBerry 179 3.0% Q-mobile / Q-Smart 148 2.5% Others 397 6.9% a. NOKIA mobile phone series using <SA> n = 2,626 Frequency Percent Total 2,626 100.0% Nokia 1280 254 9.7% Nokia C3-00 148 5.6% Nokia X1-01 129 4.9% Nokia Lumia 920 102 3.9% Nokia X2-02 99 3.8% Nokia C5-00.2 84 3.2% Nokia C2-01 82 3.1% Nokia N8 75 2.9% Nokia C2-03 71 2.7% Nokia C2-00 64 2.4% Nokia Asha 311 58 2.2% Nokia Lumia 900 56 2.1% Nokia Lumia 610 52 2.0% Nokia C5-06 52 2.0% Nokia C1-01 51 1.9% Nokia 101 49 1.9% Nokia 6300 49 1.9% Nokia Lumia 800 44 1.7% Nokia 110 40 1.5% Nokia C3-01.5 39 1.5% Nokia E71 37 1.4% a. -

Incompatible Devices – Bringgo China Version 0.2 the Following Is a List of Devices That Are Incompatible with the Bringgo App
Incompatible Devices – BringGo China Version 0.2 The following is a list of devices that are incompatible with the BringGo app: Manufacturer Device Name (Google Play) ASUS ME171– EP71 PadFone 2– A68 ASUS Transformer Pad Infinity– TF700KL PadFone Infinity– A80 PadFone– PadFone COOLPAD Coolpad 7019– 7019_msm7627a FOXCONN INTERNATIONAL ViewSonic-ViewPad4– viewpad4 HOLDINGS LIMITED HTC Hero– hero HTC Desire X– protou Desire VC– primodd HTC Ruby– ruby HTC EVO 3D X515m– shooteru Incredible 2– vivow HTC Butterfly– dlxub1 HTC EVA_UTL– evitautl HTC EVO Design C715e– kingdom HTC One X+– enrc2b EVO Shift 4G– speedy EVO 3D– shooter Desire– bravoc HTC J Butterfly– dlxj Nexus One– passion HTC One VX– totemc2 HTC-PG762– marvelc Sensation 4G– pyramid AT&T HTC One X+– evitareul HTC One V– primoc HTC Velocity 4G– holiday ISW12HT– shooterk Legend– legend ADR6330VW– blissc ISW13HT– valentewx Droid Eris– desirec HTC Incredible E S715e– tagh Desire– bravo HTC One SC– cp2dcg G2– vision Wildfire– buzz Droid Incredible– inc HTC Explorer A310e– pico Aria– liberty ADR6425LVW– vigor Hero– heroc G1– dream myTouch 4G Slide– doubleshot ADR6410LRA– fireball HTC Desire C– golfu HTC J Z321e– valentewxc9 HTC EVO 4G LTE– jewel HTC Desire SV– magnids Droid DNA– dlx Desire S– saga HTC One X– endeavoru Wildfire S– marvel HTC One SV– k2ul HTC Sensation XL with Beats Audio X315e– runnymede Desire HD– ace HTC_X515E– rider myTouch 4G– glacier HTC One XL– evita HTC One V– primou HTC Desire V– primods ADR6325– lexikon HTC Desire C– golfc myTouch 3G Slide– espresso HTC One SV– k2u