Satisfying Disclosure Restrictions with Synthetic Data Sets
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Foundations of Bayesian Learning from Synthetic Data
Foundations of Bayesian Learning from Synthetic Data Harrison Wilde Jack Jewson Sebastian Vollmer Chris Holmes Department of Statistics Barcelona GSE Department of Statistics, Department of Statistics University of Warwick Universitat Pompeu Fabra Mathematics Institute University of Oxford; University of Warwick The Alan Turing Institute Abstract (Dwork et al., 2006), to define working bounds on the probability that an adversary may identify whether a particular observation is present in a dataset, given There is significant growth and interest in the that they have access to all other observations in the use of synthetic data as an enabler for machine dataset. DP’s formulation is context-dependent across learning in environments where the release of the literature; here we amalgamate definitions regard- real data is restricted due to privacy or avail- ing adjacent datasets from Dwork et al. (2014); Dwork ability constraints. Despite a large number of and Lei (2009): methods for synthetic data generation, there are comparatively few results on the statisti- Definition 1 (("; δ)-differential privacy) A ran- cal properties of models learnt on synthetic domised function or algorithm K is said to be data, and fewer still for situations where a ("; δ)-differentially private if for all pairs of adjacent, researcher wishes to augment real data with equally-sized datasets D and D0 that differ in one another party’s synthesised data. We use observation and all S ⊆ Range(K), a Bayesian paradigm to characterise the up- dating of model parameters when learning Pr[K(D) 2 S] ≤ e" × Pr [K (D0) 2 S] + δ (1) in these settings, demonstrating that caution should be taken when applying conventional learning algorithms without appropriate con- Current state-of-the-art approaches involve the privati- sideration of the synthetic data generating sation of generative modelling architectures such as process and learning task at hand. -

Synthpop: Bespoke Creation of Synthetic Data in R
synthpop: Bespoke Creation of Synthetic Data in R Beata Nowok Gillian M Raab Chris Dibben University of Edinburgh University of Edinburgh University of Edinburgh Abstract In many contexts, confidentiality constraints severely restrict access to unique and valuable microdata. Synthetic data which mimic the original observed data and preserve the relationships between variables but do not contain any disclosive records are one possible solution to this problem. The synthpop package for R, introduced in this paper, provides routines to generate synthetic versions of original data sets. We describe the methodology and its consequences for the data characteristics. We illustrate the package features using a survey data example. Keywords: synthetic data, disclosure control, CART, R, UK Longitudinal Studies. This introduction to the R package synthpop is a slightly amended version of Nowok B, Raab GM, Dibben C (2016). synthpop: Bespoke Creation of Synthetic Data in R. Journal of Statistical Software, 74(11), 1-26. doi:10.18637/jss.v074.i11. URL https://www.jstatsoft. org/article/view/v074i11. 1. Introduction and background 1.1. Synthetic data for disclosure control National statistical agencies and other institutions gather large amounts of information about individuals and organisations. Such data can be used to understand population processes so as to inform policy and planning. The cost of such data can be considerable, both for the collectors and the subjects who provide their data. Because of confidentiality constraints and guarantees issued to data subjects the full access to such data is often restricted to the staff of the collection agencies. Traditionally, data collectors have used anonymisation along with simple perturbation methods such as aggregation, recoding, record-swapping, suppression of sensitive values or adding random noise to prevent the identification of data subjects. -

Bootstrapping Regression Models
Bootstrapping Regression Models Appendix to An R and S-PLUS Companion to Applied Regression John Fox January 2002 1 Basic Ideas Bootstrapping is a general approach to statistical inference based on building a sampling distribution for a statistic by resampling from the data at hand. The term ‘bootstrapping,’ due to Efron (1979), is an allusion to the expression ‘pulling oneself up by one’s bootstraps’ – in this case, using the sample data as a population from which repeated samples are drawn. At first blush, the approach seems circular, but has been shown to be sound. Two S libraries for bootstrapping are associated with extensive treatments of the subject: Efron and Tibshirani’s (1993) bootstrap library, and Davison and Hinkley’s (1997) boot library. Of the two, boot, programmed by A. J. Canty, is somewhat more capable, and will be used for the examples in this appendix. There are several forms of the bootstrap, and, additionally, several other resampling methods that are related to it, such as jackknifing, cross-validation, randomization tests,andpermutation tests. I will stress the nonparametric bootstrap. Suppose that we draw a sample S = {X1,X2, ..., Xn} from a population P = {x1,x2, ..., xN };imagine further, at least for the time being, that N is very much larger than n,andthatS is either a simple random sample or an independent random sample from P;1 I will briefly consider other sampling schemes at the end of the appendix. It will also help initially to think of the elements of the population (and, hence, of the sample) as scalar values, but they could just as easily be vectors (i.e., multivariate). -

A Survey on Data Collection for Machine Learning a Big Data - AI Integration Perspective
1 A Survey on Data Collection for Machine Learning A Big Data - AI Integration Perspective Yuji Roh, Geon Heo, Steven Euijong Whang, Senior Member, IEEE Abstract—Data collection is a major bottleneck in machine learning and an active research topic in multiple communities. There are largely two reasons data collection has recently become a critical issue. First, as machine learning is becoming more widely-used, we are seeing new applications that do not necessarily have enough labeled data. Second, unlike traditional machine learning, deep learning techniques automatically generate features, which saves feature engineering costs, but in return may require larger amounts of labeled data. Interestingly, recent research in data collection comes not only from the machine learning, natural language, and computer vision communities, but also from the data management community due to the importance of handling large amounts of data. In this survey, we perform a comprehensive study of data collection from a data management point of view. Data collection largely consists of data acquisition, data labeling, and improvement of existing data or models. We provide a research landscape of these operations, provide guidelines on which technique to use when, and identify interesting research challenges. The integration of machine learning and data management for data collection is part of a larger trend of Big data and Artificial Intelligence (AI) integration and opens many opportunities for new research. Index Terms—data collection, data acquisition, data labeling, machine learning F 1 INTRODUCTION E are living in exciting times where machine learning expertise. This problem applies to any novel application that W is having a profound influence on a wide range of benefits from machine learning. -

Synthetic Data Generation with Probabilistic Bayesian Networks
bioRxiv preprint doi: https://doi.org/10.1101/2020.06.14.151084; this version posted September 17, 2020. The copyright holder for this preprint (which was not certified by peer review) is the author/funder. All rights reserved. No reuse allowed without permission. Synthetic data generation with probabilistic Bayesian Networks Grigoriy Gogoshin∗1a, Sergio Branciamore1b, and Andrei S. Rodin∗1c ∗Corresponding authors 1Department of Computational and Quantitative Medicine, Beckman Research Institute, and Diabetes and Metabolism Research Institute, City of Hope National Medical Center, 1500 East Duarte Road, Duarte, CA 91010 USA [email protected] [email protected] [email protected] Abstract Bayesian Network (BN) modeling is a prominent and increasingly popular computational sys- tems biology method. It aims to construct probabilistic networks from the large heterogeneous biological datasets that reflect the underlying networks of biological relationships. Currently, a va- riety of strategies exist for evaluating BN methodology performance, ranging from utilizing artificial benchmark datasets and models, to specialized biological benchmark datasets, to simulation stud- ies that generate synthetic data from predefined network models. The latter is arguably the most comprehensive approach; however, existing implementations are typically limited by their reliance on the SEM (structural equation modeling) framework, which includes many explicit and implicit assumptions that may be unrealistic in a typical biological data analysis scenario. In this study, we develop an alternative, purely probabilistic, simulation framework that more appropriately fits with real biological data and biological network models. In conjunction, we also expand on our current understanding of the theoretical notions of causality and dependence / conditional independence in BNs and the Markov Blankets within. -

A First Step Into the Bootstrap World
INSTITUTE FOR DEFENSE ANALYSES A First Step into the Bootstrap World Matthew Avery May 2016 Approved for public release. IDA Document NS D-5816 Log: H 16-000624 INSTITUTE FOR DEFENSE ANALYSES 4850 Mark Center Drive Alexandria, Virginia 22311-1882 The Institute for Defense Analyses is a non-profit corporation that operates three federally funded research and development centers to provide objective analyses of national security issues, particularly those requiring scientific and technical expertise, and conduct related research on other national challenges. About This Publication This briefing motivates bootstrapping through an intuitive explanation of basic statistical inference, discusses the right way to resample for bootstrapping, and uses examples from operational testing where the bootstrap approach can be applied. Bootstrapping is a powerful and flexible tool when applied appropriately. By treating the observed sample as if it were the population, the sampling distribution of statistics of interest can be generated with precision equal to Monte Carlo error. This approach is nonparametric and requires only acceptance of the observed sample as an estimate for the population. Careful resampling is used to generate the bootstrap distribution. Applications include quantifying uncertainty for availability data, quantifying uncertainty for complex distributions, and using the bootstrap for inference, such as the two-sample t-test. Copyright Notice © 2016 Institute for Defense Analyses 4850 Mark Center Drive, Alexandria, Virginia 22311-1882 -
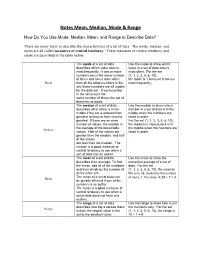
Notes Mean, Median, Mode & Range
Notes Mean, Median, Mode & Range How Do You Use Mode, Median, Mean, and Range to Describe Data? There are many ways to describe the characteristics of a set of data. The mode, median, and mean are all called measures of central tendency. These measures of central tendency and range are described in the table below. The mode of a set of data Use the mode to show which describes which value occurs value in a set of data occurs most frequently. If two or more most often. For the set numbers occur the same number {1, 1, 2, 3, 5, 6, 10}, of times and occur more often the mode is 1 because it occurs Mode than all the other numbers in the most frequently. set, those numbers are all modes for the data set. If each number in the set occurs the same number of times, the set of data has no mode. The median of a set of data Use the median to show which describes what value is in the number in a set of data is in the middle if the set is ordered from middle when the numbers are greatest to least or from least to listed in order. greatest. If there are an even For the set {1, 1, 2, 3, 5, 6, 10}, number of values, the median is the median is 3 because it is in the average of the two middle the middle when the numbers are Median values. Half of the values are listed in order. greater than the median, and half of the values are less than the median. -

Fidelity and Privacy of Synthetic Medical Data Review of Methods and Experimental Results
Fidelity and Privacy of Synthetic Medical Data Review of Methods and Experimental Results June 2021 Ofer Mendelevitch, Michael D. Lesh SM MD FACC, Keywords: synthetic data; statistical fidelity; safety; privacy; data access; data sharing; open data; metrics; EMR; EHR; clinical trials; review of methods; de-identification; re-identification; deep learning; generative models 1 Syntegra © - Fidelity and Privacy of Synthetic Medical Data Table of Contents Table of Contents 2 Abstract 3 1. Introduction 3 1.1 De-Identification and Re-Identification 3 1.2 Synthetic Data 4 2. Synthetic Data in Medicine 5 2.1 The Syntegra Synthetic Data Engine and Medical Mind 6 3. Statistical Fidelity Validation 6 3.1 Record Distance Metric 6 3.2 Visualize and Compare Datasets 7 3.3 Population Statistics 8 3.4 Single Variable (Marginal) Distributions 9 3.5 Pairwise Correlation 10 3.6 Multivariate Metrics 11 3.6.1 Predictive Model Performance 11 3.6.2 Survival Analysis 12 3.6.3 Discriminator AUC 13 3.7 Clinical Consistency Assessment 13 4. Privacy Validation 13 4.1 Disclosure Metrics 13 4.1.1 Membership Inference Test 14 4.1.2 File Membership Hypothesis Test 16 4.1.3 Attribute Inference Test 16 4.2 Copy Protection Metrics 17 4.2.1 Distance to Closest Record - DCR 17 4.2.2 Exposure 18 5. Experimental Results 19 5.1 Datasets 19 5.2 Results 20 5.2.1 Statistical Fidelity 20 5.2.2 Privacy 30 6. Discussion and Analysis 34 6.1 DIG dataset results analysis 34 6.2 NIS dataset results analysis 35 6.3 TEXAS dataset results analysis 35 6.4 BREAST results analysis 36 7. -

Federated Principal Component Analysis
Federated Principal Component Analysis Andreas Grammenos1,3∗ Rodrigo Mendoza-Smith2 Jon Crowcroft1,3 Cecilia Mascolo1 1Computer Lab, University of Cambridge 2Quine Technologies 3Alan Turing Institute Abstract We present a federated, asynchronous, and (ε, δ)-differentially private algorithm for PCA in the memory-limited setting. Our algorithm incrementally computes local model updates using a streaming procedure and adaptively estimates its r leading principal components when only O(dr) memory is available with d being the dimensionality of the data. We guarantee differential privacy via an input-perturbation scheme in which the covariance matrix of a dataset X ∈ Rd×n is perturbed with a non-symmetric random Gaussian matrix with variance in d 2 O n log d , thus improving upon the state-of-the-art. Furthermore, contrary to previous federated or distributed algorithms for PCA, our algorithm is also invariant to permutations in the incoming data, which provides robustness against straggler or failed nodes. Numerical simulations show that, while using limited- memory, our algorithm exhibits performance that closely matches or outperforms traditional non-federated algorithms, and in the absence of communication latency, it exhibits attractive horizontal scalability. 1 Introduction In recent years, the advent of edge computing in smartphones, IoT and cryptocurrencies has induced a paradigm shift in distributed model training and large-scale data analysis. Under this new paradigm, data is generated by commodity devices with hardware limitations and severe restrictions on data- sharing and communication, which makes the centralisation of the data extremely difficult. This has brought new computational challenges since algorithms do not only have to deal with the sheer volume of data generated by networks of devices, but also leverage the algorithm’s voracity, accuracy, and complexity with constraints on hardware capacity, data access, and device-device communication. -

Synthetic Data Sharing and Estimation of Viable Dynamic Treatment Regimes with Observational Data
Synthetic Data Sharing and Estimation of Viable Dynamic Treatment Regimes with Observational Data by Nina Zhou A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy (Biostatistics) in The University of Michigan 2021 Doctoral Committee: Professor Ivo D. Dinov, Co-Chair Professor Lu Wang, Co-Chair Research Associate Professor Daniel Almirall Assistant Professor Zhenke Wu Professor Chuanwu Xi Nina Zhou [email protected] ORCID iD: 0000-0002-1649-3458 c Nina Zhou 2021 ACKNOWLEDGEMENTS Firstly, I would like to express my sincere gratitude to my advisors Dr. Lu Wang and Dr. Ivo Dinov for their continuous support of my Ph.D. study and related research, for their patience, motivation, and immense knowledge. Their guidance helped me in all the time of research and writing of this thesis. Besides my advisors, I am grateful to the the rest of my thesis committee: Dr. Zhenke Wu, Dr. Daniel Almirall and Dr.Chuanwu Xi for their insightful comments and encouragements, but also for the hard question which incented me to widen my research from various perspectives. I would like to thank my fellow doctoral students for their feedback, cooperation and of course friendship. In addition, I would like to express my gratitude to Dr. Kristen Herold for proofreading all my writings. Last but not the least, I would like to thank my family: my parents and grand parents for supporting me spiritually throughout writing this thesis and my life in general. ii TABLE OF CONTENTS ACKNOWLEDGEMENTS :::::::::::::::::::::::::: ii LIST OF FIGURES ::::::::::::::::::::::::::::::: vi LIST OF TABLES :::::::::::::::::::::::::::::::: viii LIST OF ALGORITHMS ::::::::::::::::::::::::::: x ABSTRACT ::::::::::::::::::::::::::::::::::: xi CHAPTER I. -

Benchmarking Unsupervised Outlier Detection with Realistic Synthetic Data
Benchmarking Unsupervised Outlier Detection with Realistic Synthetic Data GEORG STEINBUSS, Karlsruhe Institute of Technology (KIT), Germany KLEMENS BÖHM, Karlsruhe Institute of Technology (KIT), Germany Benchmarking unsupervised outlier detection is difficult. Outliers are rare, and existing benchmark data contains outliers with various and unknown characteristics. Fully synthetic data usually consists of outliers and regular instance with clear characteristics and thus allows for a more meaningful evaluation of detection methods in principle. Nonetheless, there have only been few attempts to include synthetic data in benchmarks for outlier detection. This might be due to the imprecise notion of outliers or to the difficulty to arrive at a good coverage of different domains with synthetic data. In this work we propose a generic processfor the generation of data sets for such benchmarking. The core idea is to reconstruct regular instances from existing real-world benchmark data while generating outliers so that they exhibit insightful characteristics. This allows both for a good coverage of domains and for helpful interpretations of results. We also describe three instantiations of the generic process that generate outliers with specific characteristics, like local outliers. A benchmark with state-of-the-art detection methods confirms that our generic process is indeed practical. CCS Concepts: • Mathematics of computing ! Distribution functions; • Computing methodologies ! Machine learning algorithms; Anomaly detection. Additional Key Words and Phrases: Outlier Detection, Unsupervised, Benchmark, Synthetic Data. 1 INTRODUCTION Unsupervised outlier detection aims at finding data instances in an unlabeled data set that deviate from most other instances. Such outliers tend to be rare and usually exhibit unknown characteristics. This renders the evaluation of detection performance and hence comparisons of unsupervised outlier-detection methods difficult. -

Common Data Set 2020-2021 University of Pennsylvania
Common Data Set 2020-2021 University of Pennsylvania Table of Contents A General Information page 3 B Enrollment and Persistence 5 C First Time, First Year Admission 8 D Transfer Admission 14 E Academic Offerings and Policies 16 F Student Life 18 G Annual Expenses 20 H Financial Aid 22 I Instructional Faculty and Class Size 28 J Disciplinary Areas of Degrees Conferred 30 Common Data Set Definitions 32 Common Data Set 2020-21 1 25 Jun 2021 Common Data Set 2020-21 2 25 Jun 2021 A. General Information return to Table of Contents A1 Address Information A1 University of Pennsylvania A1 Mailing Address: 1 College Hall, Room 100 A1 City/State/Zip/Country: Philadelphia, PA 19104-6228 A1 Main Phone Number: 215-898-5000 A1 Home Page Address www.upenn.edu A1 Admissions Phone Number: 215-898-7507 A1 Admissions Office Mailing Address: 1 College Hall A1 City/State/Zip/Country: Philadelphia, PA 19104 A1 Admissions Fax Number: 215-898-9670 A1 Admissions E-mail Address: [email protected] A1 Online application www.admissions.upenn.edu A2 Source of institutional control (Check only one): A2 Public A2 Private (nonprofit) x A2 Proprietary A3 Classify your undergraduate institution: A3 Coeducational college A3 Men's college A3 Women's college A4 Academic year calendar: A4 Semester x A4 Quarter A4 Trimester A4 4-1-4 A4 Continuous A5 Degrees offered by your institution: A5 Certificate x A5 Diploma A5 Associate x A5 Transfer Associate A5 Terminal Associate x A5 Bachelor's x A5 Postbachelor's certificate x A5 Master's x A5 Post-master's certificate x A5 Doctoral degree - research/scholarship x A5 Doctoral degree - professional practice x A5 Doctoral degree - other x A5 Doctoral degree -- other Common Data Set 2020-21 3 25 Jun 2021 Common Data Set 2020-21 4 25 Jun 2021 B.