Rockwell / Allen-Bradley PLC-2/30 Programming Manual (Pdf)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Historic Touring Car Challenge Is a Series of Invitation Races for Touring Cars That Competed During the Period 1966 to 1990 Inclusive
2018 Series Regulations for the Historic Touring Car Challenge Supported by The Historic Touring Car Challenge is a series of invitation races for Touring Cars that competed during the period 1966 to 1990 inclusive. Specific requirements are covered under ‘Eligibility’ below. The Historic Sports Car Club will be the organising club. There will be five rounds of the HTCC in 2018: May 4th – 6th Donington Historic Festival 60 mins June 2nd - 3rd Thruxton 50th Anniversary 2 x 30 mins July 20th – 22nd Silverstone Classic 45 mins August 27th Oulton Park Gold Cup 50 mins October 19th – 21st Algarve Classic Festival 120 mins RACE DETAILS Each race will be for two (or exceptionally one) driver entries, open strictly by the invitation of Motor Racing Legends, to drivers of all nationalities holding a minimum of a National ‘A’ or International Historic race licence. For UK races, a minimum of a National ‘B’ will be acceptable. Each race will feature a compulsory pit stop and driver change where relevant. The car must be at rest for a minimum of 60 seconds during the pit stop. Any car failing to make a pit stop will be excluded from the results. Any car failing to make a pit stop within the pit window will incur a Drive-Through penalty. The exception to this rule will be the Algarve Classic Festival meeting. Separate pit-stop regulations will be published for this race. ELIGIBILITY The Historic Touring Car Challenge is open to Touring Cars complying with the following FIA regulations: Group A from 1st January 1982 to 31st December 1990; Group 2 from 1st January 1966 to 31st December 1981; Group 5 from 1st January 1966 to 31st December 1969; All cars must conform to the relevant sections Appendix ‘J’ of the International Sporting Code of the period; and to technical requirements of the current Appendix ‘K’ of the International Sporting Code. -

Karting Technical Regulations
RÈGLEMENT TECHNIQUE TECHNICAL REGULATIONS RÈGLEMENT TECHNIQUE DE KARTING KARTING TECHNICAL REGULATIONS Article 1 : Classification et Définitions Article 1: Classification and Definitions Article 2 : Prescriptions Générales Article 2: General Prescriptions Article 3 : Sécurité des Karts et des Équipements Article 3: Safety of Karts and Equipment Article 4 : Prescriptions Générales pour les Karts du Groupe 1 Article 4: General Prescriptions for Group 1 Karts Article 5 : Prescriptions Générales pour les Karts du Groupe 2 Article 5: General Prescriptions for Group 2 Karts Article 6 : Prescriptions Générales pour les Karts du Groupe 3 Article 6: General Prescriptions for Group 3 Karts Article 7 : Supprimé Article 7: Deleted Article 8 : Supprimé Article 8: Deleted Article 9 : Règlement Spécifique Superkart Article 9: Specific Regulations for Superkart Article 10 : Supprimé Article 10: Deleted Article 11 : Supprimé Article 11: Deleted Article 12 : Règlement Spécifique KZ2 & KZ1 Article 12: Specific Regulations for KZ2 & KZ1 Article 13 : Supprimé Article 13: Deleted Article 14 : Supprimé Article 14: Deleted Article 15 : Supprimé Article 15: Deleted Article 16 : Supprimé Article 16: Deleted Article 17: Règlement Spécifique Kart électrique Article 17: Specific Regulations for Electrical Kart Article 18 : Règlement Spécifique OK2 Article 18: Specific Regulations for OK Article 19 : Règlement Spécifique OK-Junior Article 19: Specific Regulations for OK-Junior Article 20 : Supprimé Article 20: Deleted Article 21 : Supprimé Article 21: Deleted Article -

Spectator Event Schedule
Charlotte SpeedTour Charlotte Motor Speedway, Concord, NC March 18-21, 2021 Track Length: 2.28 miles Friday, March 19 12:15pm-1:15pm Lunch Break – Car Show Laps & 7:00am - 3:00pm ........................................... Ticket Sales Open Track Touring – See Registration 8:00am Groups 1, 2, 3, 4 .................................... Miata Practice 1:15pm All Stock Cars ....................................... Feature Race 1 8:30am Groups 5a, 6, 7, 9, 10GT, 12a .......................... Practice 1:45pm Groups 1, 2, 3, 4, ........................ Miata Feature Race 2 9:00am Groups 8, 12b ................................................. Practice 2:15pm Groups 5a, 6, 7, 9, 10GT, 12a .............. Feature Race 2 9:30am All Stock Cars .................................................. Practice 2:45pm Groups 8, 12b ...................................... Feature Race 2 10:00am Groups 1, 2, 3, 4 ................................ Miata Practice 2 3:15pm All Stock Cars ....................................... Feature Race 2 10:30am Groups 5a, 6, 7, 9, 10GT, 12a...................... Practice 2 3:45pm Trans Am ........................................... Qualifying 60min 11:00am Groups 8, 12b ............................................ Practice 2 11:30am All Stock Cars ............................................. Practice 2 Sunday, March 21 12:00pm Trans Am ............................ Optional Testing 1 30min 7:00am – 12:00pm ......................................... Ticket Sales open 12:30pm-1:30pm Lunch Break – 9:00am ENDURO 70 min Track Touring -

Icebreaker, Road Race Style
ICEBREAKER, ROAD RACE STYLE p Friday, April 24 – Saturday, April 25, 2015 Thompson Speedway Motorsports Park ICEBREAKER, ROAD RACE STYLE EVENT DATES: Friday, April 24 – Saturday, April 25, 2015 TRACK: Thompson Speedway Motorsports Park (CT) TRACK WEBSITE: ww.thompsonspeedway.com TRACK PHONE: (860) 923-2280 COURSE CONFIGURATION: 1.7-mile (LONG COURSE) PROMOTER: OTB Promotions, Inc. EVENT WEBSITE: www.otbpromos.net OTB PHONE: (860) 460-0930 EVENT: The ICEBREAKER, Road Race Style is a racing event, conducted by OTB Promotions, Inc. The event will be governed by the information in these supplemental regulations. The Chief Steward has the authority to enforce such regulations and track rules. Their interpretation shall be final and may not be protested. EVENT HASHTAG: #IcebreakerRRS SCHEDULE (Subject to Change) Monday, February 15 9:00 a.m. Early Bird Registration Opens Sunday, March 15 5:00 p.m. Early Bird Registration Closes Wednesday, April 15 5:00 p.m. Online Registration Closes. Full payment due. Thursday, April 23 5:00 p.m. 8:00 p.m. Registration 5:00 p.m. 9:00 p.m. Tech Inspection 5:00 p.m. 10:00 p.m. Garage Open Friday, April 24 6:00 a.m. 10:00 p.m. Garage Open 7:00 a.m. 7:00 p.m. Registration 7:30 a.m. Flag Meeting (Classroom) 8:00 a.m. Tech Inspection Open 8:00 a.m. Driver’s Meeting (Garage) 9:00 a.m. 12:15 a.m. Practice 12:15 p.m. 1:15 p.m. Lunch 12:30 p.m. Driver’s Meeting (Garage; for late arrivals) 1:15 p.m. -

Touring Car Racing - Overview Touring Car Racing Is an Auto Racing Competition of Advanced Racing Cars
COMPILED BY : - GAUTAM SINGH STUDY MATERIAL – SPORTS 0 7830294949 Touring Car Racing - Overview Touring car racing is an auto racing competition of advanced racing cars. This sport is very popular in many countries like Argentina, Australia, Brazil, Britain, Germany, Sweden and Norway. However, its speed cannot be compared with Formula One. The touring car series consists of one or more endurance races with time duration of 3-24 hours. Basically, the event starts with a standard body shell but racing equipment like engines, suspension, brakes, wheels, and tires are permitted. Races of touring cars are conducted on road courses and street circuits. There is a very little technical difference between racing cars and touring cars. A casual observer can never point out the difference between the two. Touring cars come from family cars like sedans, hatchbacks and do not support high technical level. Just like any other racing game, all the riders participating in this game focus on covering the road track within the shortest time span and be the first one to win the game. The riders have to be quick and sharp as there can be a margin of less than one-tenth of a second between the first three finishers. History The British Touring Car (BTC) Championship, commonly known as touring car series, was founded in 1958 as British Saloon Car Championship and was renamed in 1987. This car racing series is conducted every year in the UK and is governed by the TCA. THANKS FOR READING – VISIT OUR WEBSITE www.educatererindia.com COMPILED BY : - GAUTAM SINGH STUDY MATERIAL – SPORTS 0 7830294949 The Touring Car Series Championship is following numerous national and international regulations like FIA Group 2, FIA Group 1, FIA Super Touring and FIA Super 2000. -

S.V.R.A Coronado Speed Festival S.V.R.A
S.V.R.A Coronado Speed Festival S.V.R.A PROVISIONAL SCHEDULE Naval Air Station North Island SVRA Sprint Race Series September 18-20, 2015 Race Group 1: Small bore prod. Sports cars and sedans. (SVRA Gr.1) Race Group 2: Formula Ford and Formula B cars. SVRA Gr.2 Race Group 3: World Sports Cars, GT, Prototype and Can-Am Cars 1960-1979 (SVRA Gr. 5+7) Race Group 4: Big Bore Production and Sports Cars through 1972. (SVRA Gr. 6.) Race Group 5: Medium bore Production and Sports cars prior 1972 (SVRA Gr. 3+4) Race Group 6: Series Production Sports Cars and Sedans prior to 1979. (SVRA Gr. 8.) Race Group 7: Wings and Slicks Formula cars. (SVRA Gr.9.) Race Group 8: Historic Stock cars. (SVRA Gr. 10- SC1/2/3.) Race Group 9: Pre war Sports cars and Formula cars Race group 10: Historic Trans Am cars Thursday, September 17 Sunday, September 20 12.00 noon – 5.00 pm Paddock Open for Participant Set-up. 8.00 am - 1.00 pm Registration open 12.00 noon – 5.00 pm Registration open 8.00 am Group 1 warm up 20 min. 12.00 noon -- 5.00 pm Tech 8.20 am Group 2 Friday, September 18 8.40 am Group 3 7.00 am – 5.00 pm Registration open. 9.00 am Group 4 7.00 am – 5 pm Tech Inspection. 9.20 am Group 5 12.00 Mandatory drivers meeting 9.40 am Group 6 1.00 pm Race group 1 Untimed Practice 25 min 10.00 am Break - BMW hot laps 1.25 pm Race group 2 10.15 am Group 7 1.50 pm Race group 3 10.35 am Group 8 2.15 pm Race group 4 10.55 am Group 9 2.40 pm Race group 5 11.15 am Group 10 3.05 pm Race group 6 11.35 am Break – BMW hot laps 3.30 pm Race group 7 3.55 pm Race group 8 11.50 am – 12.50 pm Lunch break 4.20 pm Race group 9 12.10 pm – 12.50 pm Pre Grid Ceremonies w/ H T/A on grid 4.45 pm Race group 10 Saturday, September 19 12.50 pm Group 10 HTA Trophy race 25 min 7.00 am – 4.00pm Registration open. -

Weathertech® International Challenge with Brian Redman July 15 – 18, 2021 Final Schedule (7/12/2021)
WeatherTech® International Challenge with Brian Redman July 15 – 18, 2021 Final Schedule (7/12/2021) Tuesday, July 13, 2021 Friday, July 16, 2021 7:00 AM – 6:00 PM Competitor Registration & Parking 7:00 AM – 4:00 PM Competitor Registration & Parking 7:30 AM – 5:00 PM Technical Inspection (CTECH Scale House) 12 NOON MANDATORY GREEN TEST DRIVERS MEETING (at Victory Lane) QUALIFYING SESSIONS 2 1:00 PM – 5:00 PM Optional GREEN special testing sessions 7:30 AM (see Test Day Schedule) 8:00 AM Group 8 8:25 AM Group 3 Wednesday, July 14, 2021 8:50 AM Group 6 1:00 PM – 7:00 PM Tech Inspection (CTECH Scale House next to Garage) 9:15 AM Group 14 Masters F/1 9:40 AM Group 10 7:00 AM – 6:00 PM Competitor Registration & Parking 10:05 AM Group 9 8:00 AM – 11:40 AM Optional GREEN special testing sessions 10:30 AM Group 2 (See Test Day Schedule) 10:55 AM Group 4 11:20 AM Group 1a 11:40 AM – 12:40 PM Lunch 11:45 AM Group 12 (PreWar/Early PostWar) 12 NOON MANDATORY BLUE TEST DRIVERS MEETING 11:45 AM – 12:55 PM Lunch/Track Touring (at Victory Lane) 12:00 PM MANDATORY DRIVERS MEETING 12:40 PM – 5:45 PM Optional BLUE special testing sessions RA CENTER (see Test Day Schedule) 12:55 PM Group 11 Thursday, July 15, 2021 1:20 PM Group 5 7:00 AM – 5:00 PM Competitor Registration & Parking 1:45 PM Group 7 2:10 PM Group 1b 7:30 AM – 5:00 PM Technical Inspection (CTECH Scale House) QUALIFYING SESSIONS 3 8:00 AM – 10:30 AM Optional BLUE special testing sessions 2:35 PM Group 2 (see Test Day Schedule) 3:00 PM Group 8 10:30 AM Masters E.L. -

Supernationals Xiv – Event Schedule (Overview)
SUPERNATIONALS XIV – EVENT SCHEDULE (OVERVIEW) Sunday, November 14th All Rental Transponders/ Group 1 Returned for Re-Charging (to 12:00pm-6:00pm Big Rig Move-In be collected at scales after Heat 1) 6:00pm – Pit Curfew 12:30pm-12:45pm Drivers’ Meeting (2nd group) 12:55pm-2:05pm Warm-up Sessions (2nd group) Monday, November 15th 2:05pm-4:20pm Qualifying (2nd group) 7:00am-5:00pm General Pit Move-In 2:30pm-5:00pm Grid Label Pickup in Reg for Heats/Group 2 – 12:00pm-6:00pm Registration (in Rotunda) To be announced when ready 8:00pm - Pit Curfew 4:20pm-6:05pm Heat 1 (2nd group) All Rental Transponders/Group 2 Returned for Re-Charging (to Tuesday, November 16th be collected at scales after Heat 1) 8:00am-5:00pm Final Move-in 10:00pm – Pit Curfew 8:00am-6:00pm Registration (in Rotunda) 12:00pm-5:00pm Tire Desk Open Saturday, November 20th 12:00pm-5:00pm Fuel Farm Open 6:30am Gates, Pits & Registration Open 8:00pm - Pit Curfew 6:30am-6:00pm Fuel Farm Open 6:30am-7:30am Rental Transponder Pickup in Reg-1st Group of Wednesday, November 17th Classes 6:00am Gates, Pits & Registration Open (at track) 7:30am-8:40am Warm-up Sessions (1st group) 6:30am-5:00pm Tire Desk Open 8:40am-10:25am Heat 2 (1st group) 6:30am-6:00pm Fuel Farm Open 10:35am-12:20am Heat 3 (1st group) 7:15am-7:45am Drivers Mtg (1st group of classes- 11:30am-12:30am Rental Transponder Pickup in Reg-2nd Group see competition schedule) of Classes 8:00am-11:00am Rental Transponder Pickup in Reg- 12:40am-1:50pm Warm-up Sessions (2nd group) 1st Group of Classes (ALL must be on by 4th practice) -

2020 Motorsport Australia Nsw Superkart Championship
2020 MOTORSPORT AUSTRALIA NSW SUPERKART CHAMPIONSHIP K.1 ELIGIBILITY (i) The objective of the championship is to promote and foster the competition of racing cars complying with the Motorsport Australia regulations for Superkarts or who comply with class definition K.2(i). i) Any inspections shall be conducted by the chief scrutineer or his nominee in accordance with the provisions of the Motorsport Australia Manual. K.2 CLASS DEFINITION (i) Eligible classes for the Championship shall be as follows: • 250 International • 250 National & 460cc 4 stroke. • 125 Gearbox • 125 Stock Honda • 125 Rotax Light/Heavy (ii) Each class will be allocated a group for gridding and overall State Title Points being: • Group 1 being 250 International & 250 National & 460cc 4 stroke. • Group 2 being 125 Gearbox & 125 Stock Honda • Group 3 being 125 Rotax Light/Heavy K.3 REGISTRATION (i) To be included in the championship and be eligible to score points in the championship a registration fee must be received by the organisers before the first race meeting that is attended. (ii) The registration fee for the championship shall be $130, which includes membership of the organising club. Current financial 2020 club members are considered as registered for the Championship. 1 (iii) In addition to the registration fee, additional fees may be levied on all competitors to cover specific costs associated with the championship. K.4 CATEGORY ORGANISERS (i) The organisers of the championship shall be the Superkart Club of NSW Inc., herein referred to as “the Organisers". The Championship Manager is John Pellicano. (ii) The organiser’s website is www.superkartsnsw.com.au K.5 POINTSCORE (i) Each Championship round will consist of four (4) sprint races (subject to meeting organiser). -
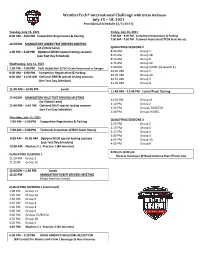
Weathertech® International Challenge with Brian Redman July 15 – 18, 2021 Provisional Schedule (2/2/2021)
WeatherTech® International Challenge with Brian Redman July 15 – 18, 2021 Provisional Schedule (2/2/2021) Tuesday, July 13, 2021 Friday, July 16, 2021 8:00 AM – 6:00 PM Competitor Registration & Parking 7:00 AM – 4:00 PM Competitor Registration & Parking 7:30 AM – 5:00 PM Technical Inspection (CTECH Scale House) 12 NOON MANDATORY GREEN TEST DRIVERS MEETING (at Victory Lane) QUALIFYING SESSIONS 2 1:00 PM – 5:00 PM Optional GREEN special testing sessions 8:00 AM Group 4 (see Test Day Schedule) 8:25 AM Group 1B 8:50 AM Group 6 Wednesday, July 14, 2021 9:15 AM Group 10 1:00 PM – 7:00 PM Tech Inspection (CTECH Scale House next to Garage) 9:40 AM Group 9/MEL (Q session 1) 10:05 AM Group 5 8:00 AM – 6:00 PM Competitor Registration & Parking 10:30 AM Group 1A 8:00 AM – 11:40 AM Optional GREEN special testing sessions 10:55 AM Group 3 (See Test Day Schedule) 11:20 AM Group 8 11:40 AM – 12:40 PM Lunch 11:45 AM – 12:45 PM Lunch/Track Touring 12 NOON MANDATORY BLUE TEST DRIVERS MEETING 12:45 PM Group 11 (at Victory Lane) 1:10 PM Group 2 12:40 PM – 5:45 PM Optional BLUE special testing sessions 1:35 PM Groups 7A/B/C/D (see Test Day Schedule) 2:00 PM Groups 9/MEL Thursday, July 15, 2021 QUALIFYING SESSIONS 3 7:00 AM – 5:00 PM Competitor Registration & Parking 2:25 PM Group 2 2:50 PM Group 4 7:30 AM – 5:00 PM Technical Inspection (CTECH Scale House) 3:15 PM Group 6 3:40 PM Group 3 8:00 AM – 10:30 AM Optional BLUE special testing sessions 4:05 PM Group 10 (see Test Day Schedule) 4:30 PM Group 8 10:30 AM Masters E.L. -

RMC 2 Timetable
03-05/06/2021, Vilnius TIMETABLE 3 JUNE, THURSDAY ATTENTION! Personal of the Team can move to the track safely only to evacuate the broken kart. ATTENTION! The engine of the kart can be started before prac�ces at this �me: 09.20 - 09.25 AM 09:30 - 18:00 FREE PRACTICES - (12 min) 12:30 - 13:00 LUNCH BREAK FP1 FP2 FP3 FP4 FP5 Group 1 - BABY G o 1 13:00 14:40 16:20 Group 2 - ART120/BRIGGS JUNIOR/BRIGGS MASTER r up Group 3 - MICRO/ROTAX MICRO/ BRIGGS MINI Group 2 09:30 11:00 13:10 14:50 16:30 Group 4 - OK JUNIOR/ OK/ ROTAX JUNIOR Group 5 - ROTAX DD2/ DD2 MASTERS Group 3 09:45 11:15 13:25 15:05 16:45 Group 6 -MINI/ ROTAX MINI Group 4 10:00 11:30 13:40 15:20 17:00 Group 7 - KZ2/ KZ2 MASTERS Group 5 10:15 11:45 13:55 15:35 17:15 Group 6 10:30 12:00 14:10 15:50 17:30 Group 7 10:45 12:15 14:25 16:05 17:45 ROTAX MAX LITHUANIA CHALLENGE, ROUND 2 Official partner @Spark Energy Bal�c Official partner @Spark Energy Bal�c 03-05/06/2021, Anyksciai TIMETABLE 4 JUNE, FRIDAY ATTENTION! Personal of the Team can move to the track safely only to evacuate the broken kart. ATTENTION! The engine of the kart can be started before prac�ces at this �me: 08.50 - 08.55 AM 09:00 - 13:40 FREE PRACTICES - (12 min) 13:00 - 15:00 SPORTING CHECKS 13:00 - 15:00 DISTRIBUTION and MARKING of TIRES 13:40 - 14:50 LUNCH BREAK 15:00 - 16:30 OFFICIAL PRACTICES (P) 16:30 - 18:35 QUALIFYING (Q) 18:45 - 19:15 BRIEFING of THE TEAMS MANAGERS FP6 FP7 FP8 P1 Group 1 12:00 14:50 16:30 Group 1 - BABY Group 2 09:00 10:30 12:10 15:00 a�er finish Scru�neering (exc. -

Club Racing Board Club Racing Board Minutes
CLUB RACING BOARD CLUB RACING BOARD MINUTES | March 5, 2019 The Club Racing Board met by teleconference on March 5, 2019. Participating were Peter Keane, Chairman; John LaRue, Kevin Fandozzi, Sam Henry, Steve Strickland, Tim Myers, Paula Hawthorne, and Shelly Pritchett, secretary. Also participating were: Bob Dowie, Peter Jankovskis and Marcus Meredith, BoD liaisons; Deanna Flanagan, Director of Road Racing; Rick Harris, Club Racing Technical Manager; and Scott Schmidt, Technical Services Assistant. The following decisions were made: Member Advisory AS 1. #26392 (Jim Wheeler) Request to disable ABS on Spec Mustang Thank you for your letter. The committee American Sedan Advisory Committee recommends a change to the 2020 rules regarding the allowance of ABS braking systems on the Spec Mustang. Exact implementation is to be determined. The committee recognizes the Spec Mustang ABS system does not follow the current philosophy in the area of brake control, but feels it is part of the balance of performance of that particular classification. We are pursuing options for the SMG competitors for the 2020 season. We are committed to maintaining parity amongst the competitors, while encouraging participation with existing cars. We encourage you to continue to support the American Sedan class and appreciate your input. P2 1. #26616 (Formula/Sports Racing Committee) Adjustment of P1-P2 performance gap and P2 balance of performance Thank you for your letter. P2 competitors are advised that as data is collected on additional P2 engine platforms this data will be used to continue the process of adjusting the P1-P2 performance gap and balancing performance within the P2 class.