Twitter and Friendfeed
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Principles, Models, and Methods for the Characterization and Analysis of Lurkers in Online Social Networks
Principles, models, and methods for the characterization and analysis of lurkers in online social networks Roberto Interdonato, Andrea Tagarelli DIMES Dept., Università della Calabria, Italy The 2015 IEEE/ACM International Conference on Advances in Social Networks Analysis and Mining Lurking in OSNs: Principles, Models, and Methods Lurking in OSNs: Principles, Models, and Methods Lurk(er): what meanings Lurking in OSNs: Principles, Models, and Methods “Lurker”: let’s google it … Lurking in OSNs: Principles, Models, and Methods Lurk(er): what meanings Lurking in OSNs: Principles, Models, and Methods Outline 1. Lurking in online communities 2. Modeling lurking behaviors Topology-driven lurking definition The issue of controversial definitions Lurking and online behavioral 3. Lurker ranking methods models 4. Experimental evaluation The opportunity of de-lurking Static scenarios Dynamic scenarios 5. Applications to other domains Vicariously learning Lurking in social trust contexts 6. Delurking via Targeted Influence Maximization The DEvOTION algorithm 7. Conclusion and future work Lurking in OSNs: Principles, Models, and Methods LURKING IN ONLINE COMMUNITIES Lurking in OSNs: Principles, Models, and Methods The 1:9:90 rule of participation inequality (1/3) Arthur, C. (2006). What is the 1% rule? In: The guardian. UK: Guardian News and Media. Lurking in OSNs: Principles, Models, and Methods The 1:9:90 rule of participation inequality (2/3) • [Nonnecke & Preece, 2000] Email-based discussion lists: • 77 online health support groups and 21 online technical support groups • 46% of the health support group members and 82% of the technical support group members are lurkers • [Swartz, 2006] On Wikipedia: over 50% of all the edits are done by only 0.7% of the users • [van Mierlo, 2014] On four DHSNs (AlcoholHelpCenter, DepressionCenter, PanicCenter, and StopSmokingCenter): • 63,990 users, 578,349 posts • Lurkers account for 1.3% (n=4668), Contributors for 24.0% (n=88,732), and Superusers for 74.7% (n=276,034) of content Nonnecke, B., Preece, J. -

To Make Claims About Or Even Adequately Understand the "True Nature" of Organizations Or Leadership Is a Monumental Task
BooK REvrnw: HERE CoMES EVERYBODY: THE PowER OF ORGANIZING WITHOUT ORGANIZATIONS (Clay Shirky, Penguin Press, 2008. Hardback, $25.95] -CHRIS FRANCOVICH GONZAGA UNIVERSITY To make claims about or even adequately understand the "true nature" of organizations or leadership is a monumental task. To peer into the nature of the future of these complex phenomena is an even more daunting project. In this book, however, I think we have both a plausible interpretation of organ ization ( and by implication leadership) and a rare glimpse into what we are becoming by virtue of our information technology. We live in a complex, dynamic, and contingent environment whose very nature makes attributing cause and effect, meaning, or even useful generalizations very difficult. It is probably not too much to say that historically the ability to both access and frame information was held by the relatively few in a system and structure whose evolution is, in its own right, a compelling story. Clay Shirky is in the enviable position of inhabiting the domain of the technological elite, as well as being a participant and a pioneer in the social revolution that is occurring partly because of the technologies and tools invented by that elite. As information, communication, and organization have grown in scale, many of our scientific, administrative, and "leader-like" responses unfortu nately have remained the same. We find an analogous lack of appropriate response in many followers as evidenced by large group effects manifested through, for example, the response to advertising. However, even that herd like consumer behavior seems to be changing. Markets in every domain are fragmenting. -

Top 50 Twitter Terms
NetLingo Top 50 Twitter Terms 1. @reply - A way to say something directly back to another person on Twitter @username, so it’s public for all to see 2. #word - When you put a hashtag before a word, it adds and sorts tweets into a category to display what's trending 3. bieber baiting - Using Justin Bieber’s name in posts to drive traffic to your online accounts (it’s actually illegal) 4. blogosphere - The shared space of blogs, crogs, flogs, microblogs, moblogs, placeblogs, plogs, splogs, vlogs 5. digital dirt - Unflattering information you may have written on social networking sites that can later haunt you 6. DM - Direct Message, a message between only you and the person you are sending it to, it is considered private 7. flash mob - A large group of people who gather suddenly in a public place, do something, then quickly disperse 8. FOMO - Fear Of Missing Out, online junkies paying partial attention to everything while scrolling through feeds 9. hashtag - When the hash sign (#) is added to a word or phrase, it lets users search for tweets similarly tagged 10. hashtag activism - Using Twitter's hashtags for Internet activism, for example #metoo #occupywallstreet 11. HT - Hat Tip, it’s an abbreviation you use to attribute a link to one of your tweeps 12. indigenous content - User-generated content created by the digital natives for themselves 13. influencer - Active Twitter users who have influence on others due to their large number of followers 14. Larry the Bird - The name of the Twitter bird, in honor of the Celtics basketball legend Larry Bird 15. -

Social Media Why You Should Care What Is Social Media? Social Network
Social Media Why You Should Care IST 331 - Olivier Georgeon, Frank Ritter 31 oct 15 • eMarketer (2007) estimated by 2011 one-half Examples of all Internet users will use social networking • Facebook regulary. • YouTube • By 2015, 75% use • Myspace • Twitter • Del.icio.us • Digg • Etc… 2 What is Social Media? Social Network • Social Network • Online communities of people who share • User Generated Content (UGC) interests and activities, • Social Bookmarking • … or who are interested in exploring the interests and activities of others. • Examples: Facebook, MySpace, LinkedIn, Orkut • Falls to analysis with tools in Ch. 9 3 4 User Generated Content (UGC) Social Bookmarking • A method for Internet users to store, organize, search, • or Consumer Generated Media (CGM) and manage bookmarks of web pages on the Internet with the help of metadata. • Based on communities; • Defined: Media content that is publicly – The more people who bookmark a piece of content, the more available and produced by end-users (user). value it is determined to have. • Examples: Digg, Del.icio.us, StumbleUpon, and reddit….and now combinations • Usually supported by a social network • Examples: Blogs, Micro-blogs, YouTube video, Flickr photos, Wiki content, Facebook wall posts, reddit, Second Life… 5 6 Social Media Principles Generate an activity stream • Automatic • Who you are – Google History, Google Analytics – Personalization • Blog • Who you know • Micro-blog – Browse network – Twitter, yammer, identi.ca • What you do • Mailing groups – Generate an activity stream -

Security and Online Social Networks
Security and Online Social Networks Javier Echaiz and Jorge Ardenghi Laboratorio de Investigaci´on de Sistemas Distribuidos (LISiDi), Departamento de Ciencias e Ingenier´ıa de la Computaci´on Tel´efono: +54 291 4595135, Fax: +54 291 4595136 Universidad Nacional del Sur, Bah´ıa Blanca (8000), Argentina {je,jra}@cs.uns.edu.ar, WWW home page: http://lisidi.cs.uns.edu.ar Abstract. In the last few years we have witnessed a sustained rise in the popularity of online Social Network Sites (SNSs) such as Twitter, Facebook, Myspace, Flickr, LinkedIn, FriendFeed, Google Friend Con- nect, Yahoo! Groups, etc., which are some of the most visited websites worldwide. However, since they are are easy to use and the users are often not aware of the nature of the access of their profiles, they often reveal information which should be kept away from the public eyes. As a result, these social sites may originate security related threats for their members. This paper highlights the benefits of safe use of SNSs and emphasizes the most important threats to members of SNSs. Moreover, we will show the main factors behind these threats. Finally we present policy and technical recommendations in order to improve security without compromising the benefits of information sharing through SNSs. Keywords: Online Social Network, Privacy, Profile squatting, Identity threat, Image Tagging and Cross-profiling. 1 Introduction The advent of the Internet has given rise to many forms of online sociality, from the old e-mail and Usenet services to the more recent instant messaging (IM), blogging, and online social services. Among these, the technological phenomenon that has acquired the greatest popularity in this 21st century is the latter, the Social Networking Sites (SNSs). -

Social Media in Government
Social Media in Government Alex Howard Government 2.0 Correspondent O’Reilly Media Agenda • A brief history of social media • e-government, open government & “We government” • The growth and future of “Gov 2.0” What is social media? Try today’s Wikipedia entry: social media is media for social interaction, using highly accessible and scalable publishing techniques A read-write Web Think of it another way: Social media are messages, text, video or audio published on digital platforms that the community to create the content Social media isn’t new • Consider the Internet before the Web (1969- 1991) • Used by military, academia and hackers • Unix-to-Unix Copy (UUCP), Telnet, e-mail Bulletin Board Services (BBS) (1979) Ward Christensen and the First BBS Usenet (1979) • First conceived of by Tom Truscott and Jim Ellis. • Usenet let users post articles or posts to newsgroups. Commercial online services (1979) Online chat rooms (1980) Internet Relay Chat (1988) • IRC was followed by ICQ in the mid- 90s. • First IM program for PCs. World Wide Web (1991) Blogs (1994) • Blogging rapidly grew in use in 1999, when Blogger and LiveJournal launched. Wikis (1994) • Ward Cunningham started development on the first wiki in 1994 and installed it on c2.om in 1995. • Cunningham was in part inspired by Apple’s Hypercard • Cunningham developed Vannevar Bush’s ideas of “allowing users to comment on and change one another’s text” America Online (1995) Social networks (1997) From one to hundreds of millions • Six Degrees was the first modern social network. • Friendster followed in 2002. • MySpace founded in 2003. -

M&A @ Facebook: Strategy, Themes and Drivers
A Work Project, presented as part of the requirements for the Award of a Master Degree in Finance from NOVA – School of Business and Economics M&A @ FACEBOOK: STRATEGY, THEMES AND DRIVERS TOMÁS BRANCO GONÇALVES STUDENT NUMBER 3200 A Project carried out on the Masters in Finance Program, under the supervision of: Professor Pedro Carvalho January 2018 Abstract Most deals are motivated by the recognition of a strategic threat or opportunity in the firm’s competitive arena. These deals seek to improve the firm’s competitive position or even obtain resources and new capabilities that are vital to future prosperity, and improve the firm’s agility. The purpose of this work project is to make an analysis on Facebook’s acquisitions’ strategy going through the key acquisitions in the company’s history. More than understanding the economics of its most relevant acquisitions, the main research is aimed at understanding the strategic view and key drivers behind them, and trying to set a pattern through hypotheses testing, always bearing in mind the following question: Why does Facebook acquire emerging companies instead of replicating their key success factors? Keywords Facebook; Acquisitions; Strategy; M&A Drivers “The biggest risk is not taking any risk... In a world that is changing really quickly, the only strategy that is guaranteed to fail is not taking risks.” Mark Zuckerberg, founder and CEO of Facebook 2 Literature Review M&A activity has had peaks throughout the course of history and different key industry-related drivers triggered that same activity (Sudarsanam, 2003). Historically, the appearance of the first mergers and acquisitions coincides with the existence of the first companies and, since then, in the US market, there have been five major waves of M&A activity (as summarized by T.J.A. -

Studying Social Tagging and Folksonomy: a Review and Framework
Studying Social Tagging and Folksonomy: A Review and Framework Item Type Journal Article (On-line/Unpaginated) Authors Trant, Jennifer Citation Studying Social Tagging and Folksonomy: A Review and Framework 2009-01, 10(1) Journal of Digital Information Journal Journal of Digital Information Download date 02/10/2021 03:25:18 Link to Item http://hdl.handle.net/10150/105375 Trant, Jennifer (2009) Studying Social Tagging and Folksonomy: A Review and Framework. Journal of Digital Information 10(1). Studying Social Tagging and Folksonomy: A Review and Framework J. Trant, University of Toronto / Archives & Museum Informatics 158 Lee Ave, Toronto, ON Canada M4E 2P3 jtrant [at] archimuse.com Abstract This paper reviews research into social tagging and folksonomy (as reflected in about 180 sources published through December 2007). Methods of researching the contribution of social tagging and folksonomy are described, and outstanding research questions are presented. This is a new area of research, where theoretical perspectives and relevant research methods are only now being defined. This paper provides a framework for the study of folksonomy, tagging and social tagging systems. Three broad approaches are identified, focusing first, on the folksonomy itself (and the role of tags in indexing and retrieval); secondly, on tagging (and the behaviour of users); and thirdly, on the nature of social tagging systems (as socio-technical frameworks). Keywords: Social tagging, folksonomy, tagging, literature review, research review 1. Introduction User-generated keywords – tags – have been suggested as a lightweight way of enhancing descriptions of on-line information resources, and improving their access through broader indexing. “Social Tagging” refers to the practice of publicly labeling or categorizing resources in a shared, on-line environment. -

Applications Log Viewer
4/1/2017 Sophos Applications Log Viewer MONITOR & ANALYZE Control Center Application List Application Filter Traffic Shaping Default Current Activities Reports Diagnostics Name * Mike App Filter PROTECT Description Based on Block filter avoidance apps Firewall Intrusion Prevention Web Enable Micro App Discovery Applications Wireless Email Web Server Advanced Threat CONFIGURE Application Application Filter Criteria Schedule Action VPN Network Category = Infrastructure, Netw... Routing Risk = 1-Very Low, 2- FTPS-Data, FTP-DataTransfer, FTP-Control, FTP Delete Request, FTP Upload Request, FTP Base, Low, 4... All the Allow Authentication FTPS, FTP Download Request Characteristics = Prone Time to misuse, Tra... System Services Technology = Client Server, Netwo... SYSTEM Profiles Category = File Transfer, Hosts and Services Confe... Risk = 3-Medium Administration All the TeamViewer Conferencing, TeamViewer FileTransfer Characteristics = Time Allow Excessive Bandwidth,... Backup & Firmware Technology = Client Server Certificates Save Cancel https://192.168.110.3:4444/webconsole/webpages/index.jsp#71826 1/4 4/1/2017 Sophos Application Application Filter Criteria Schedule Action Applications Log Viewer Facebook Applications, Docstoc Website, Facebook Plugin, MySpace Website, MySpace.cn Website, Twitter Website, Facebook Website, Bebo Website, Classmates Website, LinkedIN Compose Webmail, Digg Web Login, Flickr Website, Flickr Web Upload, Friendfeed Web Login, MONITOR & ANALYZE Hootsuite Web Login, Friendster Web Login, Hi5 Website, Facebook Video -

Instafame: Luxury Selfies in the Attention Economy
Public Culture Instafame: Luxury Selfies in the Attention Economy Alice E. Marwick Empire on top, my Instagram — my watch Five days on my yacht Cash money act up I just Instagram my shit and let them broke haters just watch —Fat Joe, “Instagram That Hoe” Instagram, the mobile photo- sharing application, was pur- chased for $1 billion by Facebook in 2012; it had, at the time, thirteen employees. While a $1 billion valuation is difficult to grasp — that’s more than the New York Times is worth — the purchase is now widely viewed by tech and business analysts as a coup (Indvik 2013). Facebook’s popularity with young, lucrative American consumers has waned as it has grown into an aggregated behemoth of online content, its News Feeds clogged with video game scores, e- commerce purchases, and advertising (Hess 2013). Instagram, despite having far fewer users, is thriv- ing. The site’s top users are a who’s who of pop stars and television celebrities. It is used by 11 percent of American teenagers, was parodied by the popular site CollegeHumor, and is regularly name- checked in hip- hop songs (Madden et al. 2013). With Instagram’s user base of 150 million people comes the possibility of achieving Instafame, the condition of having a relatively great number of follow- ers on the app. While the most followed users are primarily celebrities — the pop star Rihanna, for instance, has 11 million followers — to many Instagram users, gathering thousands, or even hundreds, of followers can be a motivating force. One participant in a Pew Research Center Internet study on online bullying said: Public Culture 27:1 doi 10.1215/08992363-2798379 Copyright 2015 by Duke University Press 137 Published by Duke University Press Public Culture Public Culture “[On Instagram,] people tend to not come off so mean. -
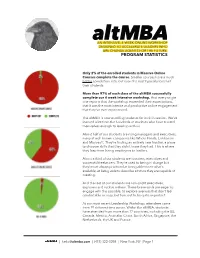
Program Statistics
AN INTENSIVE, 4-WEEK ONLINE WORKSHOP DESIGNED TO ACCELERATE LEADERS WHO ARE CHANGE AGENTS FOR THE FUTURE. PROGRAM STATISTICS Only 2% of the enrolled students in Massive Online Courses complete the course. Smaller courses have a much better completion rate, but even the best typically lose half their students. More than 97% of each class of the altMBA successfully complete our 4 week intensive workshop. And every single one reports that the workshop exceeded their expectations, that it was the most intense and productive online engagement that they’ve ever experienced. The altMBA is now enrolling students for its fifth session. We’ve learned a lot from the hundreds of students who have trusted themselves enough to level up with us. About half of our students are rising managers and executives, many at well-known companies like Whole Foods, Lululemon and Microsoft. They’re finding an entirely new frontier, a place to discover skills that they didn’t know they had. This is where they leap from being employees to leaders. About a third of our students are founders, executives and successful freelancers. They’re used to being in charge but they’re not always practiced at being able to see what’s available, at being able to describe a future they are capable of creating. And the rest of our students are non-profit executives, explorers and ruckus makers. These brave souls are eager to engage with the possible, to explore avenues that don’t feel comfortable or easy, but turn out to be quite important. At our most recent Leadership Workshop, attendees came from 19 different time zones. -

Introduction to Web 2.0 Technologies
Introduction to Web 2.0 Joshua Stern, Ph.D. Introduction to Web 2.0 Technologies What is Web 2.0? Æ A simple explanation of Web 2.0 (3 minute video): http://www.youtube.com/watch?v=0LzQIUANnHc&feature=related Æ A complex explanation of Web 2.0 (5 minute video): http://www.youtube.com/watch?v=nsa5ZTRJQ5w&feature=related Æ An interesting, fast-paced video about Web.2.0 (4:30 minute video): http://www.youtube.com/watch?v=NLlGopyXT_g Web 2.0 is a term that describes the changing trends in the use of World Wide Web technology and Web design that aim to enhance creativity, secure information sharing, increase collaboration, and improve the functionality of the Web as we know it (Web 1.0). These have led to the development and evolution of Web-based communities and hosted services, such as social-networking sites (i.e. Facebook, MySpace), video sharing sites (i.e. YouTube), wikis, blogs, etc. Although the term suggests a new version of the World Wide Web, it does not refer to any actual change in technical specifications, but rather to changes in the ways software developers and end- users utilize the Web. Web 2.0 is a catch-all term used to describe a variety of developments on the Web and a perceived shift in the way it is used. This shift can be characterized as the evolution of Web use from passive consumption of content to more active participation, creation and sharing. Web 2.0 Websites allow users to do more than just retrieve information.