SAS and UNIX: Techniques for Developing Your Toolbox
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

HEP Computing Part I Intro to UNIX/LINUX Adrian Bevan
HEP Computing Part I Intro to UNIX/LINUX Adrian Bevan Lectures 1,2,3 [email protected] 1 Lecture 1 • Files and directories. • Introduce a number of simple UNIX commands for manipulation of files and directories. • communicating with remote machines [email protected] 2 What is LINUX • LINUX is the operating system (OS) kernel. • Sitting on top of the LINUX OS are a lot of utilities that help you do stuff. • You get a ‘LINUX distribution’ installed on your desktop/laptop. This is a sloppy way of saying you get the OS bundled with lots of useful utilities/applications. • Use LINUX to mean anything from the OS to the distribution we are using. • UNIX is an operating system that is very similar to LINUX (same command names, sometimes slightly different functionalities of commands etc). – There are usually enough subtle differences between LINUX and UNIX versions to keep you on your toes (e.g. Solaris and LINUX) when running applications on multiple platforms …be mindful of this if you use other UNIX flavours. – Mac OS X is based on a UNIX distribution. [email protected] 3 Accessing a machine • You need a user account you should all have one by now • can then log in at the terminal (i.e. sit in front of a machine and type in your user name and password to log in to it). • you can also log in remotely to a machine somewhere else RAL SLAC CERN London FNAL in2p3 [email protected] 4 The command line • A user interfaces with Linux by typing commands into a shell. -

Useful Tai Ls Dino
SCIENCE & NATURE Useful Tails Materials Pictures of a possum, horse, lizard, rattlesnake, peacock, fish, bird, and beaver What to do 1. Display the animal pictures so the children can see them. 2. Say the following sentences. Ask the children to guess the animal by the usefulness of its tail. I use my tail for hanging upside down. (possum) I use my tail as a fly swatter. (horse) When my tail breaks off, I grow a new one. (lizard) I shake my noisy tail when I am about to strike. (rattlesnake) My tail opens like a beautiful fan. (peacock) I use my tail as a propeller. I cannot swim without it. (fish) I can’t fly without my tail. (bird) I use my powerful tail for building. (beaver) More to do Ask the children if they can name other animals that have tails. Ask them how these animals’Downloaded tails might by [email protected] useful. from Games: Cut out the tailsProFilePlanner.com of each of the animals. Encourage the children to pin the tails on the pictures (like “Pin the Tail on the Donkey”). Dotti Enderle, Richmond, TX Dino Dig Materials Plastic or rubber dinosaurs or bones Sand Wide-tip, medium-sized paintbrushes Plastic sand shovels Small plastic buckets Clipboards Paper Pencil or pens 508 The GIANT Encyclopedia of Preschool Activities for Four-Year-Olds Downloaded by [email protected] from ProFilePlanner.com SCIENCE & NATURE What to do 1. Beforehand, hide plastic or rubber dinosaurs or bones in the sand. 2. Give each child a paintbrush, shovel, and bucket. 3. -

LS-90 Operation Guide
Communicating Thermostat - TheLS-90 has 2 RTM-1 radio ports. These allow your thermostat to communicate with other systems. Depending on your area Power Company, programs may be available to connect your thermostat to power grid status information. This can make it easy for you to moderate your energy use at peak hours and use power when it is less expensive. The RTM-1 ports also allow you to connect yourLS-90 to your home WiFi network. This can give you access to your home’s HVAC system even when you are away. It can also give you access to web based efficient energy management sites that RTM-1 port can help you save money and protect the environment. Customer support:877-254-5625 or www.LockStateConnect.com PG 20 PG 1 LS-90 Operation Guide top cover The LS-90 programmable communicating Wire thermostat operates via a high-quality, easy- terminals Power Grid Reset to-use touch screen. To program or adjust status button your LS-90, simply touch your finger or the indicators Home stylus firmly to the screen. The screen will button SAVE NORMAL automatically light up and you will hear a ENERGY $0.05 KW H FAN 12:30pm “beep.” The screen will respond differently to 5/25 WED different types of touches, so you may want Control o TARGET bar to experiment with both your finger and with F 77o Save TEMP Power the stylus, which is included with the LS-90, Energy HUMI D button HVAC 23% Button STATUS Power Status Normal $.05/kW to see what works best for you. -

Shell Variables
Shell Using the command line Orna Agmon ladypine at vipe.technion.ac.il Haifux Shell – p. 1/55 TOC Various shells Customizing the shell getting help and information Combining simple and useful commands output redirection lists of commands job control environment variables Remote shell textual editors textual clients references Shell – p. 2/55 What is the shell? The shell is the wrapper around the system: a communication means between the user and the system The shell is the manner in which the user can interact with the system through the terminal. The shell is also a script interpreter. The simplest script is a bunch of shell commands. Shell scripts are used in order to boot the system. The user can also write and execute shell scripts. Shell – p. 3/55 Shell - which shell? There are several kinds of shells. For example, bash (Bourne Again Shell), csh, tcsh, zsh, ksh (Korn Shell). The most important shell is bash, since it is available on almost every free Unix system. The Linux system scripts use bash. The default shell for the user is set in the /etc/passwd file. Here is a line out of this file for example: dana:x:500:500:Dana,,,:/home/dana:/bin/bash This line means that user dana uses bash (located on the system at /bin/bash) as her default shell. Shell – p. 4/55 Starting to work in another shell If Dana wishes to temporarily use another shell, she can simply call this shell from the command line: [dana@granada ˜]$ bash dana@granada:˜$ #In bash now dana@granada:˜$ exit [dana@granada ˜]$ bash dana@granada:˜$ #In bash now, going to hit ctrl D dana@granada:˜$ exit [dana@granada ˜]$ #In original shell now Shell – p. -

Useful Commands in Linux and Other Tools for Quality Control
Useful commands in Linux and other tools for quality control Ignacio Aguilar INIA Uruguay 05-2018 Unix Basic Commands pwd show working directory ls list files in working directory ll as before but with more information mkdir d make a directory d cd d change to directory d Copy and moving commands To copy file cp /home/user/is . To copy file directory cp –r /home/folder . to move file aa into bb in folder test mv aa ./test/bb To delete rm yy delete the file yy rm –r xx delete the folder xx Redirections & pipe Redirection useful to read/write from file !! aa < bb program aa reads from file bb blupf90 < in aa > bb program aa write in file bb blupf90 < in > log Redirections & pipe “|” similar to redirection but instead to write to a file, passes content as input to other command tee copy standard input to standard output and save in a file echo copy stream to standard output Example: program blupf90 reads name of parameter file and writes output in terminal and in file log echo par.b90 | blupf90 | tee blup.log Other popular commands head file print first 10 lines list file page-by-page tail file print last 10 lines less file list file line-by-line or page-by-page wc –l file count lines grep text file find lines that contains text cat file1 fiel2 concatenate files sort sort file cut cuts specific columns join join lines of two files on specific columns paste paste lines of two file expand replace TAB with spaces uniq retain unique lines on a sorted file head / tail $ head pedigree.txt 1 0 0 2 0 0 3 0 0 4 0 0 5 0 0 6 0 0 7 0 0 8 0 0 9 0 0 10 -

Official Standard of the Portuguese Water Dog General Appearance
Page 1 of 3 Official Standard of the Portuguese Water Dog General Appearance: Known for centuries along Portugal's coast, this seafaring breed was prized by fishermen for a spirited, yet obedient nature, and a robust, medium build that allowed for a full day's work in and out of the water. The Portuguese Water Dog is a swimmer and diver of exceptional ability and stamina, who aided his master at sea by retrieving broken nets, herding schools of fish, and carrying messages between boats and to shore. He is a loyal companion and alert guard. This highly intelligent utilitarian breed is distinguished by two coat types, either curly or wavy; an impressive head of considerable breadth and well proportioned mass; a ruggedly built, well-knit body; and a powerful, thickly based tail, carried gallantly or used purposefully as a rudder. The Portuguese Water Dog provides an indelible impression of strength, spirit, and soundness. Size, Proportion, Substance: Size - Height at the withers - Males, 20 to 23 inches. The ideal is 22 inches. Females, 17 to 21 inches. The ideal is 19 inches. Weight - For males, 42 to 60 pounds; for females, 35 to 50 pounds. Proportion - Off square; slightly longer than tall when measured from prosternum to rearmost point of the buttocks, and from withers to ground. Substance - Strong, substantial bone; well developed, neither refined nor coarse, and a solidly built, muscular body. Head: An essential characteristic; distinctively large, well proportioned and with exceptional breadth of topskull. Expression - Steady, penetrating, and attentive. Eyes - Medium in size; set well apart, and a bit obliquely. -
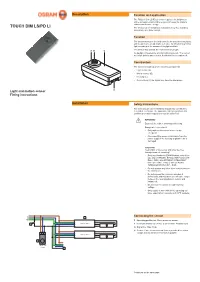
Mounting Instructions OSRAM Sensor Touch DIM LS/PD LI Light And
Description Function and application The TOUCH DIM LS/PD LI sensor regulates the brightness at the workplace and in office areas to increase the working comfort and to save energy. TOUCH DIM LS/PD LI The sensor can be installed in luminaires (e.g. floor standing luminaires) or in false ceilings. Function The sensor measures the brightness in the area to be regulated and keeps this to an adjustable set value by introducing artificial light according to the amount of daylight available. A B C The sensor also detects the movements of people. As daylight increases the artificial light is reduced . The sensor no longer detects any motions, it switches the luminaires off. Construction The sensor is made up of the following components: • Light sensor (A) • Motion sensor (B) • Housing (C) • Connections (D) for signal line, zero line and phase D Light and motion sensor Fitting instructions Installation Safety instructions The sensor must only be installed and put into operation by a qualified electrician. The applicable safety regulations and accident prevention regulations must be observed. WARNING! Exposed, live cables or damaged housing. Danger of electric shock! • Only work on the sensor when it is de- energized. • Disconnect the sensor or luminaire from the power supply if the housing or plastic lens is damaged. CAUTION! Destruction of the sensor and other devices through incorrect mounting! • Only use electronic OSRAM ballast coils of the type QUICKTRONIC INTELLIGENT DALI (QTi DALI…DIM), HALOTRONIC INTELLIGENT DALI (HTi DALI…DIM) or OPTOTRONIC INTELLIGENT DALI (OT…DIM). • Do not operate any other other control units on the control line. -

IBM Education Assistance for Z/OS V2R1
IBM Education Assistance for z/OS V2R1 Item: ASCII Unicode Option Element/Component: UNIX Shells and Utilities (S&U) Material is current as of June 2013 © 2013 IBM Corporation Filename: zOS V2R1 USS S&U ASCII Unicode Option Agenda ■ Trademarks ■ Presentation Objectives ■ Overview ■ Usage & Invocation ■ Migration & Coexistence Considerations ■ Presentation Summary ■ Appendix Page 2 of 19 © 2013 IBM Corporation Filename: zOS V2R1 USS S&U ASCII Unicode Option IBM Presentation Template Full Version Trademarks ■ See url http://www.ibm.com/legal/copytrade.shtml for a list of trademarks. Page 3 of 19 © 2013 IBM Corporation Filename: zOS V2R1 USS S&U ASCII Unicode Option IBM Presentation Template Full Presentation Objectives ■ Introduce the features and benefits of the new z/OS UNIX Shells and Utilities (S&U) support for working with ASCII/Unicode files. Page 4 of 19 © 2013 IBM Corporation Filename: zOS V2R1 USS S&U ASCII Unicode Option IBM Presentation Template Full Version Overview ■ Problem Statement –As a z/OS UNIX Shells & Utilities user, I want the ability to control the text conversion of input files used by the S&U commands. –As a z/OS UNIX Shells & Utilities user, I want the ability to run tagged shell scripts (tcsh scripts and SBCS sh scripts) under different SBCS locales. ■ Solution –Add –W filecodeset=codeset,pgmcodeset=codeset option on several S&U commands to enable text conversion – consistent with support added to vi and ex in V1R13. –Add –B option on several S&U commands to disable automatic text conversion – consistent with other commands that already have this override support. –Add new _TEXT_CONV environment variable to enable or disable text conversion. -

User Commands Tail ( 1 ) Tail – Deliver the Last Part of a File /Usr/Bin/Tail
User Commands tail ( 1 ) NAME tail – deliver the last part of a file SYNOPSIS /usr/bin/tail [ ± number [lbcr]] [file] /usr/bin/tail [-lbcr] [file] /usr/bin/tail [ ± number [lbcf]] [file] /usr/bin/tail [-lbcf] [file] /usr/xpg4/bin/tail [-f -r] [-c number -n number] [file] /usr/xpg4/bin/tail [ ± number [l b c] [f]] [file] /usr/xpg4/bin/tail [ ± number [l] [f r] ] [file] DESCRIPTION The tail utility copies the named file to the standard output beginning at a designated place. If no file is named, the standard input is used. Copying begins at a point in the file indicated by the -cnumber, -nnumber, or ±number options (if +number is specified, begins at distance number from the beginning; if -number is specified, from the end of the input; if number is NULL, the value 10 is assumed). number is counted in units of lines or byte according to the -c or -n options, or lines, blocks, or bytes, according to the appended option l, b, or c. When no units are specified, counting is by lines. OPTIONS The following options are supported for both /usr/bin/tail and /usr/xpg4/bin/tail. The -r and -f options are mutually exclusive. If both are specified on the command line, the -f option will be ignored. -b Units of blocks. -c Units of bytes. -f Follow. If the input-file is not a pipe, the program will not terminate after the line of the input- file has been copied, but will enter an endless loop, wherein it sleeps for a second and then attempts to read and copy further records from the input-file. -

Linux Networking 101
The Gorilla ® Guide to… Linux Networking 101 Inside this Guide: • Discover how Linux continues its march toward world domination • Learn basic Linux administration tips • See how easy it can be to build your entire network on a Linux foundation • Find out how Cumulus Linux is your ticket to networking freedom David M. Davis ActualTech Media Helping You Navigate The Technology Jungle! In Partnership With www.actualtechmedia.com The Gorilla Guide To… Linux Networking 101 Author David M. Davis, ActualTech Media Editors Hilary Kirchner, Dream Write Creative, LLC Christina Guthrie, Guthrie Writing & Editorial, LLC Madison Emery, Cumulus Networks Layout and Design Scott D. Lowe, ActualTech Media Copyright © 2017 by ActualTech Media. All rights reserved. No portion of this book may be reproduced or used in any manner without the express written permission of the publisher except for the use of brief quotations. The information provided within this eBook is for general informational purposes only. While we try to keep the information up- to-date and correct, there are no representations or warranties, express or implied, about the completeness, accuracy, reliability, suitability or availability with respect to the information, products, services, or related graphics contained in this book for any purpose. Any use of this information is at your own risk. ActualTech Media Okatie Village Ste 103-157 Bluffton, SC 29909 www.actualtechmedia.com Entering the Jungle Introduction: Six Reasons You Need to Learn Linux ....................................................... 7 1. Linux is the future ........................................................................ 9 2. Linux is on everything .................................................................. 9 3. Linux is adaptable ....................................................................... 10 4. Linux has a strong community and ecosystem ........................... 10 5. -

Practical Linux Examples: Exercises 1
Practical Linux examples: Exercises 1. Login (ssh) to the machine that you are assigned for this workshop (assigned machines: https://cbsu.tc.cornell.edu/ww/machines.aspx?i=87 ). Prepare working directory, and copy data files into the working directory. (Replace “XXXXX” in the commands with your BioHPC User ID ) mkdir /workdir/XXXXX cd /workdir/XXXXX cp /shared_data/Linux_workshop2/* ./ 2. You are given a gzipped gff3 file. Inspect the content in the file. Linux functions: gunzip -c, head, tail, cut, less Inspect the first and last 100 lines of the file, using "head" and "tail" functions to retrieve first and last lines of the file; Retrieve line number 1001 to 2000 from the file and write these lines into a new file " mynew.gtf "; Inspect the columns 2,3,4 and 8 of lines 3901 to 4000, using "cut" function to specify the columns. Compare "cut" with "less -S" function. If you use "less" function, remember to exit "less" by pressing "q". gunzip -c human.gff3.gz | head -n 100 gunzip -c human.gff3.gz | tail -n 100 gunzip -c human.gff3.gz| head -n 2000 | tail -n 1000 > mynew.gtf gunzip -c human.gff3.gz| head -n 4000 | tail -n 100 | cut -f 2-5,8 gunzip -c human.gff3.gz| head -n 4000 | tail -n 100 | less -S 3. Count the number of genes listed in the file. Linux functions: awk, uniq Count the total number of lines in the file using "wc -l" function; Count the number of genes list in the file. First, you need to use "awk" to retrieve lines with the 3rd column value equals "gene", then count these lines with "wc -l"; Count the number for each of the feature categories (genes, exons, rRNA, miRNA, et al.) listed in this GFF3 file. -
Uniq Tablet Ll 12.2” User Manual Version 1.0
Uniq Tablet ll 12.2” User Manual version 1.0 1 This manual was not subject to any language revision. This manual or any part of it may not be copied, reproduced or otherwise distributed without the publisher‘s consent. All rights reserved. Elcom, spoločnosť s ručením obmedzeným, Prešov © ELCOM, spoločnosť s ručením obmedzeným, Prešov, 2017 2 CONTENTS IMPORTANT NOTICES .............................................................................................................04 CONFORMITY DECLARATION .................................................................................................05 KEY LAYOUT AND DEFINITION ...............................................................................................06 USING THE DEVICE ..................................................................................................................07 BEFORE USING THE DEVICE ..................................................................................................10 BEFORE USING THE DEVICE ..................................................................................................10 LOGGING ON TO THE OPERATING SYSTEM ........................................................................10 SWITCHING OFF .......................................................................................................................10 RESTARTING ............................................................................................................................. 11 CONTROLLING .........................................................................................................................