3 Comparing Block-Based and Text-Based Programming in High
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Machine That Builds Itself: How the Strengths of Lisp Family
Khomtchouk et al. OPINION NOTE The Machine that Builds Itself: How the Strengths of Lisp Family Languages Facilitate Building Complex and Flexible Bioinformatic Models Bohdan B. Khomtchouk1*, Edmund Weitz2 and Claes Wahlestedt1 *Correspondence: [email protected] Abstract 1Center for Therapeutic Innovation and Department of We address the need for expanding the presence of the Lisp family of Psychiatry and Behavioral programming languages in bioinformatics and computational biology research. Sciences, University of Miami Languages of this family, like Common Lisp, Scheme, or Clojure, facilitate the Miller School of Medicine, 1120 NW 14th ST, Miami, FL, USA creation of powerful and flexible software models that are required for complex 33136 and rapidly evolving domains like biology. We will point out several important key Full list of author information is features that distinguish languages of the Lisp family from other programming available at the end of the article languages and we will explain how these features can aid researchers in becoming more productive and creating better code. We will also show how these features make these languages ideal tools for artificial intelligence and machine learning applications. We will specifically stress the advantages of domain-specific languages (DSL): languages which are specialized to a particular area and thus not only facilitate easier research problem formulation, but also aid in the establishment of standards and best programming practices as applied to the specific research field at hand. DSLs are particularly easy to build in Common Lisp, the most comprehensive Lisp dialect, which is commonly referred to as the “programmable programming language.” We are convinced that Lisp grants programmers unprecedented power to build increasingly sophisticated artificial intelligence systems that may ultimately transform machine learning and AI research in bioinformatics and computational biology. -

The Book of Apigee Edge Antipatterns V2.0
The Book of Apigee Edge Antipatterns Avoid common pitfalls, maximize the power of your APIs Version 2.0 Google Cloud Privileged and confidential. apigee 1 Contents Introduction to Antipatterns 3 What is this book about? 4 Why did we write it? 5 Antipattern Context 5 Target Audience 5 Authors 6 Acknowledgements 6 Edge Antipatterns 1. Policy Antipatterns 8 1.1. Use waitForComplete() in JavaScript code 8 1.2. Set Long Expiration time for OAuth Access and Refresh Token 13 1.3. Use Greedy Quantifiers in RegularExpressionProtection policy 16 1.4. Cache Error Responses 19 1.5. Store data greater than 512kb size in Cache 24 1.6. Log data to third party servers using JavaScript policy 27 1.7. Invoke the MessageLogging policy multiple times in an API proxy 29 1.8. Configure a Non Distributed Quota 36 1.9. Re-use a Quota policy 38 1.10. Use the RaiseFault policy under inappropriate conditions 44 1.11. Access multi-value HTTP Headers incorrectly in an API proxy 49 1.12. Use Service Callout policy to invoke a backend service in a No Target API proxy 54 Google Cloud Privileged and confidential. apigee 2 2. Performance Antipatterns 58 2.1. Leave unused NodeJS API Proxies deployed 58 3. Generic Antipatterns 60 3.1. Invoke Management API calls from an API proxy 60 3.2. Invoke a Proxy within Proxy using custom code or as a Target 65 3.3. Manage Edge Resources without using Source Control Management 69 3.4. Define multiple virtual hosts with same host alias and port number 73 3.5. -

The First Program: Little Crab
CHAPTER 2 The first program: Little Crab topics: writing code: movement, turning, reacting to the screen edges concepts: source code, method call, parameter, sequence, if-statement In the previous chapter, we discussed how to use existing Greenfoot scenarios: We created objects, invoked methods, and played a game. Now we want to start to make our own game. 2.1 The Little Crab scenario The scenario we use for this chapter is called little-crab. You will find this scenario in the book-scenarios folder. The scenario you see should look similar to Figure 2.1. Exercise 2.1 Start Greenfoot and open the little-crab scenario. Place a crab into the world and run the program (click the Run button). What do you observe? (Remember: If the class icons on the right appear striped, you have to compile the project first.) On the right you see the classes in this scenario (Figure 2.2). We notice that there are the usual Greenfoot Actor and World classes, and subclasses called CrabWorld and Crab. The hierarchy (denoted by the arrows) indicates an is-a relationship (also called inher- itance): A crab is an actor, and the CrabWorld is a world. Initially, we will work only with the Crab class. We will talk a little more about the CrabWorld and Actor classes later on. If you have just done the exercise above, then you know the answer to the question “What do you observe?” It is: “nothing.” M02_KOLL4292_02_SE_C02.indd 17 2/3/15 7:39 PM 18 | Chapter 2 ■ The first program: Little Crab Figure 2.1 The Little Crab scenario Figure 2.2 The Little Crab classes The crab does not do anything when Greenfoot runs. -

INTRODUCTION to PL/1 PL/I Is a Structured Language to Develop Systems and Applications Programs (Both Business and Scientific)
INTRODUCTION TO PL/1 PL/I is a structured language to develop systems and applications programs (both business and scientific). Significant features : v Allows Free format v Regards a program as a continuous stream of data v Supports subprogram and functions v Uses defaults 1 Created by Sanjay Sinha Building blocks of PL/I : v Made up of a series of subprograms and called Procedure v Program is structured into a MAIN program and subprograms. v Subprograms include subroutine and functions. Every PL/I program consists of : v At least one Procedure v Blocks v Group 2 Created by Sanjay Sinha v There must be one and only one MAIN procedure to every program, the MAIN procedure statement consists of : v Label v The statement ‘PROCEDURE OPTIONS (MAIN)’ v A semicolon to mark the end of the statement. Coding a Program : 1. Comment line(s) begins with /* and ends with */. Although comments may be embedded within a PL/I statements , but it is recommended to keep the embedded comments minimum. 3 Created by Sanjay Sinha 2. The first PL/I statement in the program is the PROCEDURE statement : AVERAGE : PROC[EDURE] OPTIONS(MAIN); AVERAGE -- it is the name of the program(label) and compulsory and marks the beginning of a program. OPTIONS(MAIN) -- compulsory for main programs and if not specified , then the program is a subroutine. A PL/I program is compiled by PL/I compiler and converted into the binary , Object program file for link editing . 4 Created by Sanjay Sinha Advantages of PL/I are : 1. Better integration of sets of programs covering several applications. -

Metadefender Core V4.12.2
MetaDefender Core v4.12.2 © 2018 OPSWAT, Inc. All rights reserved. OPSWAT®, MetadefenderTM and the OPSWAT logo are trademarks of OPSWAT, Inc. All other trademarks, trade names, service marks, service names, and images mentioned and/or used herein belong to their respective owners. Table of Contents About This Guide 13 Key Features of Metadefender Core 14 1. Quick Start with Metadefender Core 15 1.1. Installation 15 Operating system invariant initial steps 15 Basic setup 16 1.1.1. Configuration wizard 16 1.2. License Activation 21 1.3. Scan Files with Metadefender Core 21 2. Installing or Upgrading Metadefender Core 22 2.1. Recommended System Requirements 22 System Requirements For Server 22 Browser Requirements for the Metadefender Core Management Console 24 2.2. Installing Metadefender 25 Installation 25 Installation notes 25 2.2.1. Installing Metadefender Core using command line 26 2.2.2. Installing Metadefender Core using the Install Wizard 27 2.3. Upgrading MetaDefender Core 27 Upgrading from MetaDefender Core 3.x 27 Upgrading from MetaDefender Core 4.x 28 2.4. Metadefender Core Licensing 28 2.4.1. Activating Metadefender Licenses 28 2.4.2. Checking Your Metadefender Core License 35 2.5. Performance and Load Estimation 36 What to know before reading the results: Some factors that affect performance 36 How test results are calculated 37 Test Reports 37 Performance Report - Multi-Scanning On Linux 37 Performance Report - Multi-Scanning On Windows 41 2.6. Special installation options 46 Use RAMDISK for the tempdirectory 46 3. Configuring Metadefender Core 50 3.1. Management Console 50 3.2. -
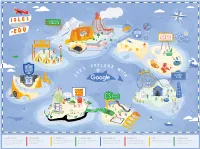
Google for Education National Parks VR Google Expeditions Google Arts & Culture Be Internet Awesome Made with Code CS First Google Science Fair
Google For Education National Parks VR Google Expeditions Google Arts & Culture Be Internet Awesome Made with Code CS First Google Science Fair Learn how tools built for teaching and learning, Discover the hidden worlds of our Take a field trip to virtually anywhere (even Explore works of art and stories from around Teach learners the fundamentals of digital Make the connection between coding and Learn the basics of Computer Science using the Create projects that show how Science, like Classroom, G Suite for Education, and National Parks on ranger-guided trips places school buses can’t go) using immersive the world with 360° tours of exhibits in over 70 safety and citizenship so they can be safe, creativity, empowering girls to engage with block-based programming language, Scratch. Technology, Engineering, and Math can be used Chromebooks, can increase engagement through virtual reality. AR and VR technology. different countries. confident explorers of the online world. technology and bring their ideas to life. to impact the world around us. and inspire curiosity. Google for National Google Google Arts Education Parks VR Expeditions & Culture Discover the hidden worlds of Explore works of art and stories Tools built for teaching and learning. Field trips to virtually anywhere. our National Parks. from around the world. Over 80 million teachers and students around the world Take a ranger-guided journey through the glaciers of What if you could journey to the surface of Mars or From The Metropolitan Museum of Art to Nairobi’s communicate and collaborate using Classroom and Alaska’s Kenai Fjords or get up close with active climb to the top of Machu Picchu without ever leaving Kenya National Archives, Google Arts & Culture offers G Suite for Education, while Chromebooks are the most volcanoes in Hawai’i. -

Blue, Bluej and Greenfoot
Kent Academic Repository Full text document (pdf) Citation for published version Kölling, Michael (2016) Lessons from the Design of Three Educational Programming Environments: Blue, BlueJ and Greenfoot. International Journal of People-Oriented Programming, 4 (1). pp. 5-32. ISSN 2156-1796. DOI https://doi.org/10.4018/IJPOP.2015010102 Link to record in KAR http://kar.kent.ac.uk/56662/ Document Version Publisher pdf Copyright & reuse Content in the Kent Academic Repository is made available for research purposes. Unless otherwise stated all content is protected by copyright and in the absence of an open licence (eg Creative Commons), permissions for further reuse of content should be sought from the publisher, author or other copyright holder. Versions of research The version in the Kent Academic Repository may differ from the final published version. Users are advised to check http://kar.kent.ac.uk for the status of the paper. Users should always cite the published version of record. Enquiries For any further enquiries regarding the licence status of this document, please contact: [email protected] If you believe this document infringes copyright then please contact the KAR admin team with the take-down information provided at http://kar.kent.ac.uk/contact.html International Journal of People-Oriented Programming January-June 2015, Vol. 4, No. 1 Table of Contents SIKONL C I T L V PF EP iv Steve Goschnick, Swinburne University of Technology, Melbourne, Australia Leon Sterling, Swinburne University of Technology, Melbourne, Australia -

Code Girl Tracey Acosta Santa Clara University
Santa Clara University Scholar Commons Computer Engineering Senior Theses Engineering Senior Theses 6-1-2015 Code girl Tracey Acosta Santa Clara University Amanda Holl Santa Clara University Paige Rogalski Santa Clara University Follow this and additional works at: https://scholarcommons.scu.edu/cseng_senior Part of the Computer Engineering Commons Recommended Citation Acosta, Tracey; Holl, Amanda; and Rogalski, Paige, "Code girl" (2015). Computer Engineering Senior Theses. 43. https://scholarcommons.scu.edu/cseng_senior/43 This Thesis is brought to you for free and open access by the Engineering Senior Theses at Scholar Commons. It has been accepted for inclusion in Computer Engineering Senior Theses by an authorized administrator of Scholar Commons. For more information, please contact [email protected]. Code Girl by Tracey Acosta Amanda Holl Paige Rogalski Submitted in partial fulfillment of the requirements for the degrees of Bachelor of Science Computer Science and Engineering Bachelor of Science in Web Design and Engineering School of Engineering Santa Clara University Santa Clara, California June 1, 2015 Code Girl Tracey Acosta Amanda Holl Paige Rogalski Computer Science and Engineering Web Design and Engineering Santa Clara University June 1, 2015 ABSTRACT Despite the growing importance of technology and computing, fewer than 1% of women in college today choose to major in computer science.[1] Educational programs and games created to interest girls in computing, such as Girls Who Code and Made With Code, have been successful in engaging girls with interactive and creative learning environments, but they are too advanced for young girls to benefit from. To address the lack of educational, computer science games designed specifically for young girls, we developed a web-based application called Code Girl for girls age five to eight to customize their own avatar using Blockly, an open-source visual coding editor developed by Google. -

A Block Design for Introductory Functional Programming in Haskell
A Block Design for Introductory Functional Programming in Haskell Matthew Poole School of Computing University of Portsmouth, UK [email protected] Abstract—This paper describes the visual design of blocks for the learner, and to avoid syntax and type-based errors entirely editing code in the functional language Haskell. The aim of the through blocks-based program construction. proposed blocks-based environment is to support students’ initial steps in learning functional programming. Expression blocks and There exists some recent work in representing functional slots are shaped to ensure constructed code is both syntactically types within blocks-based environments. TypeBlocks [9] in- correct and preserves conventional use of whitespace. The design cludes three basic type connector shapes (for lists, tuples aims to help students learn Haskell’s sophisticated type system and functions) which can be combined in any way and to which is often regarded as challenging for novice functional any depth. The prototype blocks editor for Bootstrap [10], programmers. Types are represented using text, color and shape, [11] represents each of the five types of a simple functional and empty slots indicate valid argument types in order to ensure language using a different color, with a neutral color (gray) that constructed code is well-typed. used for polymorphic blocks; gray blocks change color once their type has been determined during program construction. I. INTRODUCTION Some functional features have also been added to Snap! [12] Blocks-based environments such as Scratch [1] and Snap! and to a modified version of App Inventor [13]. [2] offer several advantages over traditional text-based lan- This paper is structured as follows. -

Exploring Student Perceptions About the Use of Visual Programming
Exploring student perceptions about the use of visual programming environments, their relation to student learning styles and their impact on student motivation in undergraduate introductory programming modules Maira Kotsovoulou (BSc, MSc) July 2019 This thesis is submitted in partial fulfilment of the requirements for the degree of Doctor of Philosophy. Department of Educational Research, Lancaster University, UK. Exploring student perceptions about the use of visual programming environments, their relation to student learning styles and their impact on student motivation in undergraduate introductory programming modules Maira Kotsovoulou (BSc, MSc) This thesis results entirely from my own work and has not been offered previously for any other degree or diploma. The word count is 57,743 excluding references. Signature ........................................................ Maira Kotsovoulou (BSc, MSc) Exploring student perceptions about the use of visual programming environments, their relation to student learning styles and their impact on student motivation in undergraduate introductory programming modules Doctor of Philosophy, July 2019 Abstract My research aims to explore how students perceive the usability and enjoyment of visual/block-based programming environments (VPEs), to what extent their learning styles relate to these perceptions and finally to what extent these tools facilitate student understanding of basic programming constructs and impact their motivation to learn programming. My overall methodological approach is a case study that explores the nature of potential benefits to using a VPE in an introductory programming module, within the specific context of an English-speaking institution of higher learning in Southern Europe. Part 1 of this research is a pilot study, which uses participatory action research as a methodological practice to identify which visual programming environment will be selected for the main study. -

Kednos PL/I for Openvms Systems User Manual
) Kednos PL/I for OpenVMS Systems User Manual Order Number: AA-H951E-TM November 2003 This manual provides an overview of the PL/I programming language. It explains programming with Kednos PL/I on OpenVMS VAX Systems and OpenVMS Alpha Systems. It also describes the operation of the Kednos PL/I compilers and the features of the operating systems that are important to the PL/I programmer. Revision/Update Information: This revised manual supersedes the PL/I User’s Manual for VAX VMS, Order Number AA-H951D-TL. Operating System and Version: For Kednos PL/I for OpenVMS VAX: OpenVMS VAX Version 5.5 or higher For Kednos PL/I for OpenVMS Alpha: OpenVMS Alpha Version 6.2 or higher Software Version: Kednos PL/I Version 3.8 for OpenVMS VAX Kednos PL/I Version 4.4 for OpenVMS Alpha Published by: Kednos Corporation, Pebble Beach, CA, www.Kednos.com First Printing, August 1980 Revised, November 1983 Updated, April 1985 Revised, April 1987 Revised, January 1992 Revised, May 1992 Revised, November 1993 Revised, April 1995 Revised, October 1995 Revised, November 2003 Kednos Corporation makes no representations that the use of its products in the manner described in this publication will not infringe on existing or future patent rights, nor do the descriptions contained in this publication imply the granting of licenses to make, use, or sell equipment or software in accordance with the description. Possession, use, or copying of the software described in this publication is authorized only pursuant to a valid written license from Kednos Corporation or an anthorized sublicensor. -

DUM Č. 1 V Sadě 35. Inf-11 Objektové Programování V Greenfoot
projekt GML Brno Docens DUM č. 1 v sadě 35. Inf-11 Objektové programování v Greenfoot Autor: Lukáš Rýdlo Datum: 08.06.2014 Ročník: studenti semináře Anotace DUMu: Úvodní informace k celé sadě, metodika. Simulace života zajíce v Greenfoot - seznámení s prostředím aplikace a jazykem. Materiály jsou určeny pro bezplatné používání pro potřeby výuky a vzdělávání na všech typech škol a školských zařízení. Jakékoliv další využití podléhá autorskému zákonu. Sada projektů pro výuku programování mírně pokročilých studentů Úvod k sadě DUMů Tato sada DUMů obsahuje tři části a v ní dva projekty vhodné pro mírně pokročilé studenty programování. Části popořadě obsahují projekt simulační hry „Život zajíce“ v jazyce Java a prostře- dí Greenfoot, druhá část obsahuje tutéž simulační hru v jazyce C s využitím grafické (herní) knihov- ny Allegro (a IDE Dev-C) a třetí část je věnována projektu bitmapového konvertoru v jazyce C pro příkazovou řádku. Tyto tři značně nesourodé projekty mají dát možnost šikovnějším studentům programování srovnat různé přístupy a paradigmata i prostředí. Na rozdíl od ustrnulé individuální a systematické výuky jednoho konkrétního jazyka je mají připravit na reálné programátorské úkoly v reálném prostředí, ve kterém programátor musí často volit různé přístupy nebo paradigmata a učit se vhodnější a pro daný úkol lépe použitelnější jazyk, dohledávat si potřebné informace ve zdrojích na internetu a ne- spoléhat jen na naučenou teorii. V DUMech nebude vysvětlena teorie systematicky, ale zásadně pouze s orientací na řešení konkrét- ního problému a také formou odkazů na externí zdroje. Předpokládám, že studenti již ovládají zá- kladní syntax nějakého C-like jazyka a dovedou minimálně pracovat s proměnnými, podmínkami a (vnořenými) cykly, že dovedou sami a bez pomoci řešit jednoduché úkoly, umí program zkompi- lovat a spustit v nějakém IDE.