The Technical Side of Being an Internet Service Provider
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Internet... the Final Frontier. Eine Ethnographie. Schlußbericht Des Projekts 'Interaktionsraum Internet. Netzkultur Und Ne
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Research Papers in Economics econstor www.econstor.eu Der Open-Access-Publikationsserver der ZBW – Leibniz-Informationszentrum Wirtschaft The Open Access Publication Server of the ZBW – Leibniz Information Centre for Economics Helmers, Sabine; Hoffmann, Ute; Hofmann, Jeanette Working Paper Internet... the final frontier: Eine Ethnographie. Schlußbericht des Projekts Interaktionsraum Internet. Netzkultur und Netzwerkorganisation Schriftenreihe der Abteilung Organisation und Technikgenese des Forschungsschwerpunktes Technik-Arbeit-Umwelt am Wissenschaftszentrum Berlin für Sozialforschung, No. FS II 98-112 Provided in cooperation with: Wissenschaftszentrum Berlin für Sozialforschung (WZB) Suggested citation: Helmers, Sabine; Hoffmann, Ute; Hofmann, Jeanette (1998) : Internet... the final frontier: Eine Ethnographie. Schlußbericht des Projekts Interaktionsraum Internet. Netzkultur und Netzwerkorganisation, Schriftenreihe der Abteilung Organisation und Technikgenese des Forschungsschwerpunktes Technik-Arbeit- Umwelt am Wissenschaftszentrum Berlin für Sozialforschung, No. FS II 98-112, http:// hdl.handle.net/10419/49813 Nutzungsbedingungen: Terms of use: Die ZBW räumt Ihnen als Nutzerin/Nutzer das unentgeltliche, The ZBW grants you, the user, the non-exclusive right to use räumlich unbeschränkte und zeitlich auf die Dauer des Schutzrechts the selected work free of charge, territorially unrestricted and beschränkte einfache Recht ein, das ausgewählte Werk im Rahmen within the time limit of the term of the property rights according der unter to the terms specified at → http://www.econstor.eu/dspace/Nutzungsbedingungen → http://www.econstor.eu/dspace/Nutzungsbedingungen nachzulesenden vollständigen Nutzungsbedingungen zu By the first use of the selected work the user agrees and vervielfältigen, mit denen die Nutzerin/der Nutzer sich durch die declares to comply with these terms of use. -

Handling Information Overload on Usenet
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by NORA - Norwegian Open Research Archives UNIVERSITY OF OSLO Department of Informatics Handling Information Overload on Usenet Advanced Caching Methods for News Jan Ingvoldstad Cand Scient Thesis 4th August 2001 Abstract Usenet is the name of a world wide network of servers for group communica- tion between people. From 1979 and onwards, it has seen a near exponential growth in the amount of data transported, which has been a strain on band- width and storage. There has been a wide range of academic research with focus on the WWW, but Usenet has been neglected. Instead, Usenet’s evolu- tion has been dominated by practical solutions. This thesis describes the history of Usenet in a growth perspective, and introduces methods for collection and analysis of statistical data for testing the usefulness of various caching strategies. A set of different caching strategies are proposed and examined in light of bandwidth and storage demands as well as user perceived performance. I have shown that advanced caching methods for news offers relief for reading servers’ storage and bandwidth capacity by exploiting usage patterns for fetching or prefetching articles the users may want to read, but it will not solve the problem of near exponential growth nor the problems of Usenet’s backbone peers. Preface When I first started my studies at the University in Oslo in the autumn of 1991, I thought I was going to be a mathematician, and followed my first class in university level mathematics with vigor. -

Online Identifiers in Everyday Life
© 2010 by Benjamin M. Gross. All rights reserved. ONLINE IDENTIFIERS IN EVERYDAY LIFE BY BENJAMIN M. GROSS DISSERTATION Submied in partial fulfillment of the requirements for the degree of Doctor of Philosophy in Library and Information Science in the Graduate College of the University of Illinois at Urbana-Champaign, 2010 Urbana, Illinois Doctoral Commiee: Associate Professor Michael Twidale, Chair Professor Geof Bowker, University of Pisburgh Professor Chip Bruce Associate Professor Ann Bishop Abstract Identifiers are an essential component of online communication. Email addresses and instant messenger usernames are two of the most common online identi- fiers. is dissertation focuses on the ways that social, technical and policy fac- tors affect individual’s behavior with online identifiers. Research for this dissertation was completed in two parts, an interview-based study drawn from two populations and an examination of the infrastructure for managing identifiers in two large consumer services. e exploratory study ex- amines how individuals use online identifiers to segment and integrate aspects of their lives. e first population is drawn from employees of a financial ser- vice firm with substantial constraints on communication in the workplace. e second population is drawn from a design firm with minimal constraints on com- munication. e two populations provide the opportunity to explore the social, technical, and policy issues that arise from diverse communication needs, uses, strategies, and technologies. e examination of systems focuses on the infras- tructure that Google and Yahoo! provide for individuals to manage their iden- tifiers across multiple services, and the risks and benefits of employing single sign-on systems. -

PKI Endbericht 24.05.13 12:28
PKI Endbericht 24.05.13 12:28 Startseite Über uns Endbericht (Hyper-)Texte Allerlei Interaktionen Sitemap Internet... the Final Frontier: eine Ethnographie Captain's Log Kulturraum Internet Regierende Techniken und Techniken des Regierens: zur Politik im Netz Hello Usenet - Good-bye? Über das Rauschen eines Mediums 'Last Chance for Common Sense': Interaktionsraum Internet in der Zusammenschau Literaturliste Akronyme und Abkürzungen Zusammenfassung Das im Herbst 1998 abgeschlossene Forschungsprojekt "Interaktionsraum Internet" hat sich mit den konstitutiven Merkmalen der Netzkultur und Netzwerkorganisation beschäftigt. Im Vordergrund des Interesses stand das dynamische Zusammenspiel technischer und gesellschaftlicher Konventionen in der Organisation wie auch im Wandel des Netzes. Die ethnographisch angeleitete Binnenperspektive auf das Internet konzentrierte sich auf drei ausgewählte Bereiche, um Prozesse der Institutionenbildung und die Formen ihrer Transformation zu studieren: die hegemoniale Betriebstechnik der Netzknoten (UNIX), die grundlegende Übertragungstechnik im Netz (das Internet Protokoll IP) und einen populären Kommunikationsdienst (Usenet). Der Schlußbericht des Projekts enthält die Ergebnisse der drei Untersuchungsstränge. Gezeigt wird anhand der Entwicklung in den drei Feldern, daß sich der Wandel des Netzes weder beliebig noch anarchisch vollzieht. Das dezentral organisierte Internet beruht vielmehr auf technisch wie http://duplox.wzb.eu/endbericht/index.html Seite 1 von 7 PKI Endbericht 24.05.13 12:28 organisatorisch verteilten Formen der Koordination, in denen individuelle Handlungspräferenzen kollektiv definitionsmächtig werden. Abstract The research project "Interaktionsraum Internet", which completed its mission in Autumn 1998, studied the constitutive features of network culture and network organization. Special emphasis was given to the dynamic interplay of technical and social conventions regarding both the Net's organization as well as its change. -
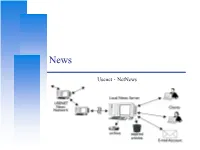
Usenet、Netnews
News Usenet、NetNews Computer Center, CS, NCTU Computer Center, News outline Introduction • History of netnews • History of newsgroups • News operations Transfer protocol • NNTP – Network News Transfer Protocol News softwares • Reader: tin • Server: INN – InterNet News 2 Introduction to News Computer Center, CS, NCTU Computer Center, Introduction to news (1) Usenet is a worldwide distributed Internet discussion system. • The initial Internet community • Like bulletin board systems (BBS) • Hybrid between e-mail and web forums • Absence of a central server and dedicated administrator The format and transmission of Usenet articles is similar to that of Internet e-mail messages. Usenet has significant cultural importance in the networked world • FAQ, spam. 4 Computer Center, CS, NCTU Computer Center, Introduction to news (2) Spamming: In 1994, advertisers began broadcasting messags to all newsgroups at once. Usenet has diminished in importance with respect to Internet forums, blogs, and mailing lists. Google made efforts to buy archive of Usenet newsgroups to attempt to create a complete one. Google has a web search interface and also allows newsgroup posting. • http://groups.google.com Usenet is a “must-have” resource? Year 1996 1997 1998 1999 2000 2001 2002 2003 Daily Vol. (GB) 4.5 9 12 26 82 181 257 492 Year 2004 2005 2006 2007 2008 2009 2010 2011 Daily Vol. (TB) 1 1.52 2.27 2.95 3.07 4.65 5.42 7.52 5 Computer Center, CS, NCTU Computer Center, Introduction to news (3) 6 Computer Center, CS, NCTU Computer Center, History (1) Origins -

Internet Servisi Usenet
Internet servisi dr Dušan Ljubičić Beogradska akademija poslovnih i umetničkih strukovnih studija Usenet Usenet • 1980.g razvili studenti univerziteta Duke i S.Karolina • Naziv Usenet dolazi od User Network • Javna diskusija o različitim temama u vidu tekstualnih poruka 3/29/2020 Internet servisi – dr Dušan Ljubičić 2 Usenet • Vrsta oglasne table gde svako može da iznese svoje stavove i ideje, postavi pitanje, dobije odgovor na postavljeno pitanje, podeli svoje znanje i iskustvo sa drugima… • Svetska zajednica ljudi koji razmenjuju ideje i informacije 3/29/2020 Internet servisi – dr Dušan Ljubičić 3 Diskusione grupe u Usenet mreži • Skladišta na Usenet serverima • Sadrže datoteke koje grupisane u diskusione grupe • Naziv grupe ukazuje na tematiku i zato se zovu i tematske grupe, interesne grupe i grupe 3/29/2020 Internet servisi – dr Dušan Ljubičić 4 Poruka (post, artikal) • Diskusione grupe su adresa na koju korisnici šalju svoje poruke • Poruka (artikal, post), je u obliku teksta ili u binarnom formatu (sve što nije tekst, audio, video, softver…) • Proces slanja poruke naziva se posting • Poruka istovremeno može da se pošalje na adresu više diskusionih grupa • Danas postoji preko 100 000 diskusionih grupa 3/29/2020 Internet servisi – dr Dušan Ljubičić 5 Nazivi diskusionih grupa • Ime diskusione grupe počinje sa prefiksom koji ukazuje na najširu tematiku, npr. comp za kompjutere • U nastavku posle tačke dolazi naziv podgrupe, npr. software (comp.software) • Daljom podelom bi grupa comp.software.windows • sci.psychology, sci.research, soc.college.org, soc.culture.african, talk.religion, talk.politics... 3/29/2020 Internet servisi – dr Dušan Ljubičić 6 Hijerarhije diskusionih grupa • Početno ime grupe (npr. -

Alt.Am Yellow Netpages™ USENET Newsgroups
Yellow NetPages™ USENET Newsgroups a.bsu – alt.am 81 a.bsu.programming ak.admin alt.1d alt.activism.children Alaskan network news administration. One-dimensional imaging, & the think- Open discussion of political issues a.bsu.religion ing behind it. about children. ak.bushnet.thing a.bsu.talk Alaskan Public Access Networking. alt.2600 alt.activism.d aaa.inu-chan The magazine or the game system. A place to discuss issues in ak.config Inu-chan by Kenso KATO (Moderated) You decide. alt.activism. Alaskan regional heirarchy configura- ab.arnet tion. alt.2600.codez alt.activism.death-penalty No description. For people opposed to capital punish- ab.general ak.test ment. Items of general interest in Alberta, Messages with the beta-nature. alt.2600.crackz Canada. Broken software protection. alt.adjective.noun.verb.verb.verb akr.freenet The penultimate alt group. ab.jobs Discussion about the Akron Regional alt.2600.hackerz Jobs in Alberta, Canada. Free-Net. Just what is so cool about not be able alt.adoption to spell? For those involved with or contemplat- ab.politics akr.internet ing adoption. Discussion of politics in Alberta, Internet access in the Akron, Ohio, alt.2600.hope.announce Canada. area. Hackers on Planet Earth announce- alt.adoption.agency ments. Licensed non-profit adoption agency abg.acf-jugend alabama.announce information. abg.acf-termine Announcements of interest to everyone alt.2600.hope.d in Alabama. (Moderated) Hackers on Planet Earth discussion. alt.aeffle.und.pferdle abg.acf-vor German TV cartoon characters das alabama.config alt.2600.hope.tech Aeffle und das Pferdle. -

Internet... the Final Frontier. an Ethnographic Account. Exploring
A Service of Leibniz-Informationszentrum econstor Wirtschaft Leibniz Information Centre Make Your Publications Visible. zbw for Economics Helmers, Sabine; Hoffmann, Ute; Hofmann, Jeanette Working Paper Internet... the final frontier: an ethnographic account: exploring the cultural space of the Net from the inside WZB Discussion Paper, No. FS II 00-101 Provided in Cooperation with: WZB Berlin Social Science Center Suggested Citation: Helmers, Sabine; Hoffmann, Ute; Hofmann, Jeanette (2000) : Internet... the final frontier: an ethnographic account: exploring the cultural space of the Net from the inside, WZB Discussion Paper, No. FS II 00-101, Wissenschaftszentrum Berlin für Sozialforschung (WZB), Berlin This Version is available at: http://hdl.handle.net/10419/49787 Standard-Nutzungsbedingungen: Terms of use: Die Dokumente auf EconStor dürfen zu eigenen wissenschaftlichen Documents in EconStor may be saved and copied for your Zwecken und zum Privatgebrauch gespeichert und kopiert werden. personal and scholarly purposes. Sie dürfen die Dokumente nicht für öffentliche oder kommerzielle You are not to copy documents for public or commercial Zwecke vervielfältigen, öffentlich ausstellen, öffentlich zugänglich purposes, to exhibit the documents publicly, to make them machen, vertreiben oder anderweitig nutzen. publicly available on the internet, or to distribute or otherwise use the documents in public. Sofern die Verfasser die Dokumente unter Open-Content-Lizenzen (insbesondere CC-Lizenzen) zur Verfügung gestellt haben sollten, If the documents -

Studying Online Newsgroups Danyel Fisher and Christopher Lueg
Appendix Studying Online Newsgroups Danyel Fisher and Christopher Lueg This program posts news to thousands of machines throughout the entire civi lized world. Your message will cost the net hundreds ifnot thousands ofdollars to send everywhere. Please be sure you know what you are doing. Are you absolutely sure that you want to do this? [yIn] Warning message displayed by original "nn" newsgroup program before posting A.1 Introduction Several of the chapters in this volume have discussed studying online newsgroups. The raw data they tap into is commonly available; however, it can be quite a chal lenge to mine that data for useful information. This appendix is meant to serve two purposes. First, it is a basic introduction to the day-to-day structure of Usenet. It emphasises the threading structure of messages, and how those threads relate to news groups; it discusses the hierarchy of group names, and how those hierarchies are formed; and it discusses the life and death of newsgroups. It is meant as a general continuation of Pfaffenberger's chapter (this volume); it also draws on some ofthe information presented by Smith (this volume). Second, it is a technical introduction to dealing with Usenet data. For many pro jects, it is easy enough to track some current messages from Google's "Groups" archive, or to count the number of posters at Netscan (Smith, this volume); however, to actually look at the content ofmessages still requires downloading and reading them all. This section briefly discusses some of the tools that can be useful in downloading and reading Usenet groups.