Provisioning Cybersecurity in ICT Complex Supply Chains: an Overview, Key Issues and a Relevant Architecture
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

———— 2016 Registration Document
———— 2016 REGISTRATION DOCUMENT Including the annual financial report 01 Persons responsible 3 16 Practices of the governing bodies 91 02 Statutory Auditors 5 17 Employees 93 17.1 Employee data 93 03 Selected financial information 7 17.2 Employee share-ownership and profit-sharing 95 04 Risks 11 18 Major shareholders 97 4.1 Risks specific to the Group’s activity 11 18.1 Shareholders and their voting rights 98 4.2 Liquidity risk 14 18.2 Transactions carried out 4.3 Interest rate risk 15 during the year subject to 4.4 Exchange-rate risk 16 Article L. 621-18-2 of the French 4.5 Intangible asset risk 16 Monetary and Financial Code 100 contents 4.6 Environment risk 17 18.3 Share buybacks 101 4.7 Legal and fiscal risks 17 18.4 Market for Altran Technologies securities 102 4.8 Investment risk 17 18.5 Information on the calculation methods 4.9 Brexit risk 18 and effects of adjustments to the conditions covering the subscription or 05 Company information 19 purchase of rights and securities giving 5.1 Company background information and access to the Company’s share capital 103 development 19 18.6 Agreements entered into by the 5.2 Main investments 20 Company which would be amended or terminated upon a change of control of 06 Information about the the Company 103 Group’s businesses 21 18.7 Agreements between shareholders, of 6.1 Core activities 21 which the Company is aware and which may cause restrictions to the transfer of 6.2 The Engineering and R&D Services market 22 shares and/or the exercise of voting rights 104 6.3 Competition 24 18.8 Commitments -

PLM Weekly Summary Editor: Cimdata News Team 15 January 2021 Contents Cimdata News
PLM Weekly Summary Editor: CIMdata News Team 15 January 2021 Contents CIMdata News ............................................................................................................................................ 2 An Enterprise Digital Transformation Platform – a CIMdata Commentary......................................................2 Aras’ Cloud Strategy – a CIMdata Blog Post ....................................................................................................5 CIMdata Announces its 2021 PLM Market & Industry Forum Series ..............................................................6 CIMdata to Host a Free Webinar on CAD Trends ............................................................................................7 NLign Analytics “Structural Lifecycle Digital Environment” Enables Model-Driven Product Quality – a CIMdata Commentary .......................................................................................................................................8 PTC’s Cloud Strategy – a CIMdata Blog Post ................................................................................................. 13 Acquisitions .............................................................................................................................................. 14 Accenture Acquires Real Protect, Brazil-Based Information Security Company ........................................... 14 Atos to acquire In Fidem to reinforce its cybersecurity position in the North American market .................... 15 Planview -

Projet De Note En Réponse) Which Was Filed with the French Autorité Des Marchés Financiers on 23 September 2019 and Which Remains Subject to Its Review
This document is an unofficial English-language translation of the draft response document (projet de note en réponse) which was filed with the French Autorité des marchés financiers on 23 September 2019 and which remains subject to its review. In the event of any differences between this unofficial English- language translation and the official French draft response document, the official French draft response document shall prevail. The draft offer and this draft response document remain subject to the French Financial Market's Authority review. DRAFT DOCUMENT PREPARED BY IN RESPONSE TO THE PUBLIC TENDER OFFER FOR THE SHARES OF THE COMPANY ALTRAN TECHNOLOGIES LAUNCHED BY This draft response document (projet de note en réponse) was filed with the French Financial Markets Authority (the "AMF") on 23 September 2019, in accordance with the provisions of Article 231-26 of the AMF's general regulation. It was prepared in accordance with Article 231-19 of the AMF's general regulation. The draft offer and this draft response document remain subject to the review of the AMF. Important notice Pursuant to Articles 231-19 and 261-1 et seq. of the AMF's general regulation, the report of Finexsi, acting in its capacity as independent expert, is included in this draft response document. This draft response document (the "Draft Response Document") is available on the websites of ALTRAN (www.altran.com) and the AMF (www.amf-france.org) and may be obtained free of charge from Altran Technologies' registered office at 96, avenue Charles de Gaulle, 92200 Neuilly-sur-Seine – FRANCE. In accordance with the provisions of Article 231-28 of the AMF's general regulation, information relating to Altran Technologies, in particular legal, financial and accounting information, will be filed with the AMF and made available to the public in the same manner no later than the day before the opening of the tender offer. -

Zinnov Zones 2020 Assessment
READY TO UNLOCK THE VALUE OF R&D? PANORAMA 2021 EDITION GET THE FUTURE YOU WANT CONTENTS INTERVIEW WITH THE CEO: WILLIAM ROZÉ 1 CAPGEMINI ENGINEERING PROFILE 3 MARKET OVERVIEW 5 INTELLIGENT INDUSTRY 7 WHAT WE OFFER 9 DIGITAL & SOFTWARE ENGINEERING 11 MANIFESTO INDUSTRIALIZED GLOBALSHORE 13 Unifying the global capabilities in Engineering R&D and harnessing 17 HYPERLOOP the power of data, connectivity and 19 VODAFONE software to pioneer the Intelligent 21 AIRBUS Industry, Altran & Capgemini Digital 23 ALSTOM Engineering and Manufacturing CASE STUDIES 25 DAFNI Services join forces to become 27 LSHTM Capgemini Engineering… bringing 29 OKTA the best of both worlds; together! 31 QUALCOMM Through our cutting-edge innovations, 33 RENESA we are excited to design, develop and 35 SNCF delivery tomorrow’s smart products, create new customer experiences and provide high value in our clients’ digital ZINNOV RATINGS 37 transformation journey. EVEREST RATINGS 39 OUR PEOPLE 41 GOVERNANCE 47 EMPLOYEE WALL 49 Could you share with us a project where Capgemini is currently working on, that spontaneously comes to INTERVIEW WITH THE CEO: your mind? WILLIAM ROZÉ I think one of the projects that excites me the most today is with Siemens Energy and Siemens Gamesa INTERVIEW WITH CEO: WILLIAM ROZE to use digital twin technology. This technology is the CAPGEMINI ENGINEERING PANORAMA 2021 Did COVID-19 pose any challenges or future and we can use it for any industry well combined opportunities? with our system skills. For Siemens, the goal is create With Capgemini’s acquisition of Altran, your automatically and cost effectively, machine specific digital manufacturing expertise comes together Covid has massively accelerated the trends we digital twins of their installed gas turbine, compressor with Altran’s world-class engineering and R&D were seeing the last years. -

Augmented and Virtual Reality in Operations
Augmented and Virtual Reality in Operations A guide for investment Introduction Augmented Reality and Virtual Reality (AR/VR) are not new, but recent advances in computational power, storage, graphics processing, and high-resolution displays have helped overcome some of the constraints that have stood in the way of the widespread use of these immersive technologies. Global spending on AR/VR is now expected to reach $17.8 billion in 2018, an increase of nearly 95% over the $9.1 billion estimate for 2017.1 Given this impetus, we wanted to understand more about the current state of play with AR/VR in the enterprise. We surveyed executives at 700+ companies, including 600 companies who are either experimenting with or implementing AR/VR; spoke with AR/VR-focused leadership at global companies, start-ups, and vendors; and analyzed over 35 use cases, with a particular focus on: • The use of AR/VR for internal industrial company operations, including, but not limited to, design, engineering, and field services • The automotive, utility, and discrete manufacturing sectors. This research focuses on organizations that have initiated their AR/VR journey, whether by experimentation or implementation, and aims to answer a number of questions: • How is AR/VR being used today? • Where should organizations invest – what are the use cases that generate the most value? • How can companies either begin or evolve their initiatives? Outside of this report, terms you will commonly find when reading about AR/VR are mixed reality, hybrid reality, or merged reality in which both the physical and the virtual or digital realities coexist or even merge. -

Mobility As a Service a Sum of Parts Present Today
MOBILITY AS A SERVICE A SUM OF PARTS PRESENT TODAY CONTENTS FOREWORD A LOOK AT FUTURE 4 18 SCENARIOS MOBILITY OF CONCLUSION – PARTS 6 THE FUTURE 22 ARE PRESENT TODAY DISSECTING FOUR KEY SECTORS OF 8 MAAS, HERE TODAY Foreword by William (Billy) Riggs Professor of Planning, Engineering, and Management University of San Francisco The last decade has been a time of unprecedented change in how we move people through cities. The rise of Mobility-as-a-Service (MaaS) platforms, shared and networked vehicles, and other transportation technologies have changed the way we think about cities, transport, and data. The components of this new mobility environment, the focus of this document, represent an exciting future for us all. Most acutely, new and disruptive transport will result in profound changes in cities. There are implications for jobs, social equity, and the environment. There are opportunities to shape advances in transportation to improve streets and better connect people; to reshape cities and improve the social and physical health of their residents. There are opportunities to reduce collisions and improve access to healthcare for those who need it most—particularly high-cost, high-need individuals at the younger, and older ends of the age spectrum. There is also the potential to connect people to jobs and change the way cities organize space and optimize trips. Yet these opportunities also present challenges. Smarter transportation may not always translate into greater sustainability or equity. There is a risk that leaders from the public and private sector may not move fast enough to respond to these changes and achieve the full benefits of new technology. -
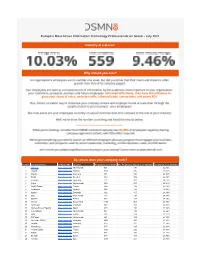
The World's Most Active Information Technology
Europe's Most Active Information Technology Professionals on Social - July 2021 Industry at a glance: Why should you care? So, where does your company rank? Position Company Name LinkedIn URL Location Employees on LinkedIn No. Employees Shared (Last 30 Days) % Shared (Last 30 Days) 1 CM.com https://www.linkedin.com/company/cmcom/Netherlands 551 178) 32.30% 2 Crayon https://www.linkedin.com/company/crayon-group/Norway 1668 535) 32.07% 3 Mambu https://www.linkedin.com/company/mambu/Germany 588 166) 28.23% 4 Sinch https://www.linkedin.com/company/sinch/Sweden 1361 359) 26.38% 5 Personio https://www.linkedin.com/company/personio/Germany 772 202) 26.17% 6 Xebia https://www.linkedin.com/company/xebia/Netherlands 1006 260) 25.84% 7 PayFit France https://www.linkedin.com/company/payfit/France 529 133) 25.14% 8 Nordcloud https://www.linkedin.com/company/nordcloud-ltd/Finland 554 139) 25.09% 9 Adform https://www.linkedin.com/company/adform/Denmark 682 167) 24.49% 10 Sdu https://www.linkedin.com/company/sdu-nl/Netherlands 797 194) 24.34% 11 Questel https://www.linkedin.com/company/questel/France 573 139) 24.26% 12 Veeam https://www.linkedin.com/company/veeam-software/Switzerland 4172 961) 23.03% 13 AlfaPeople https://www.linkedin.com/company/alfapeople/Denmark 543 123) 22.65% 14 Wolters Kluwer España https://www.linkedin.com/company/wolters-kluwer-espa-a/Spain 670 150) 22.39% 15 Centralpoint https://www.linkedin.com/company/centralpoint/Netherlands 584 130) 22.26% 16 Octo https://www.linkedin.com/company/octo-technology/France 785 174) 22.17% 17 -

Contact Entreprises: Franck STEUNOU
Contact Entreprises: Franck STEUNOU : [email protected] | 05 62 17 40 27 Jean-Noël LAVAL : [email protected] | 05 62 17 40 08 Offres de stage : [email protected] Offres d’emploi : www.alumni.enac.fr https://www.facebook.com/enacfrance www.enac.fr https://www.instagram.com/enac_officiel/ JOURNÉE ENAC PROGRAMME ENTREPRISES Jeudi 16 mai 2019 +Entreprises Simulations DES d’entretien Conférences En partenariat Les de l ’ lles Depuis maintenant quatorze ans, c’est toujours avec un immense plaisir que chaque année nous accueillons au sein de l’ENAC la journée ENAC Entreprises. Année après année, l’équipe d’organisation de ce forum a à cœur de le développer et d’accueillir de plus en plus d’entreprises de la filière aéronautique intéressées par les formations que nous dispensons à l’ENAC. Ainsi, je suis fier de vous annoncer que pour cette quatorzième édition, c’est 46 entreprises qui se sont mobilisées pour participer à cette journée et je les en remercie. L’Ecole Nationale de l’Aviation Civile est une Grande Ecole réputée pour ses programmes, le nombre et la qualité de ses partenaires internationaux, les doubles compétences de ses étudiants (techniques et managériales), ses filières d’excellence. Les témoignages des entreprises et des milieux éducatifs reconnaissent à l’ENAC le sérieux et la qualité des enseignements, de la pédagogie et de l’accompagnement des élèves. Les réussites de nos 24 000 diplômés dans le monde, tous cursus confondus, attestent que l’ENAC mérite le qualificatif de « valeur sûre ». Notre mission est de former de futurs managers dotés d’un solide socle de connaissances fondamentales dans tous le spectre des métiers de l’aéronautique, du transport aérien et du spatial, mais également capables de comprendre les enjeux et la complexité du monde économique dans lequel la créativité et l’innovation conditionnera le succès de leurs décisions, actions et comportements. -

TOOLS for Msmes & LARGE ENTERPRISES for DIGITAL
AUTOMATION & DIGITISATION AUTOMATION VOL 14 JUN-JUL 2021 ` 100 www.industr.com/en AUTOMATION & DIGITISATION COBOTS & I4.0 Feb-Mar 2021 TOOLS FOR MSMEs & LARGE I VOLUME 14 ENTERPRISES FOR DIGITAL TRANSFORMATIONS Also available in China, Taiwan, Singapore, Malaysia, Thailand & Hong Kong Malaysia, Singapore, Taiwan, Also available in China, A&D - Interview Suresh D, CEO, Spark Minda Technical Center, Minda Corporation and Group CTO, Spark Minda Group Companies (p. 26) www.industr.com/en Power & Energy P. 32 In association with Test & Measurement P. 35 Fieldbus & Networking P. 38 When the chips are down… Coping with the semiconductor shortage P. 28 Projekt4 28.03.18 13:56 Seite 1 REDUCE DOWNTIME. ENABLE SCALABILITY. FlexEdge helps to modernize aging communications and control infrastructures. Both new and existing devices can be easily connected to the system, reducing overall downtime and enabling scalable integration. Driven by Crimson®, FlexEdge enables IIOT connectivity to numerous cloud environments with point-and-click simplicity, providing users with the ability to perform protocol conversion, Contact Red Lion India: aggregate data, customize dashboards, [email protected] and enable edge computing. +91 20 - 619 38 301 Learn more at www.flexedge.net IIOT CONNECTIVITY IS EASY WITH FLEXEDGE ©2021 Red Lion Controls, Inc. All rights reserved. Red Lion, the Red Lion logo are registered trademarks of Red Lion Controls, Inc. All other company and product names are trademarks of their respective owners. 7410009435/36 aandd - EDITORIAL The drivers of an inclusive transition The World SME Day on 27 June is celebrated all over the world to recognise, applaud and create awareness of contribution of SMEs to the economy. -

Magic Quadrant for Public Cloud IT Transformation Services
Magic Quadrant for Public Cloud IT Transformation Services Published 2 August 2021 - ID G00733897 - 64 min read By Analyst(s): Mark Ray, Tobi Bet, David Groombridge, Craig Lowery, DD Mishra, William Maurer Initiatives: IT Services and Solutions; Cloud and Edge Infrastructure As the move to public cloud accelerates, clients are seeking specialized help with IT transformation. Sourcing, procurement and vendor management leaders can use this assessment of 16 providers focused on cloud-native solutions associated with managed and professional services for the public cloud. This Magic Quadrant is related to other research: View All Magic Quadrants and Critical Capabilities Market Definition/Description Providers in this market offer solutions designed to deliver transformational IT outcomes via cloud-native professional and managed services built exclusively from public hyperscale cloud infrastructure and platform services. Organizations seeking to use public clouds like Amazon Web Services, Google Cloud, Microsoft Azure, and other “hyperscale” platforms engage with providers in this market to get the greatest transformational benefits from cloud services. While there are many global system integrators (GSIs) that have cloud transformation capabilities (covered in Gartner’s Magic Quadrant for Data Center Outsourcing and Hybrid Infrastructure Managed Services, Global and Critical Capabilities for Data Center Outsourcing and Hybrid Infrastructure Managed Services, Global), this Magic Quadrant offers a view of providers more specifically focused on public cloud transformation. Many of the traditional GSIs are covered in the Honorable Mentions section of this document as well. The market definition comprises the following key aspects: Gartner, Inc. | G00733897 Page 1 of 46 ■ Providers deliver positive business impacts born from IT transformation. -

Agenda Wednesday, June 16, 2021
AGENDA WEDNESDAY, JUNE 16, 2021 SANOFI E-BOOTH* SANOFI IN-PERSON BOOTH* Sessions last 10 minutes Sessions last between 10 and 30 minutes 11.00 am 09.45 am Developing drugs in the digital age: Developing drugs in the digital age: when scientists become when scientists become data scientists data scientists Eric Genevois-Marlin - Head of R&D Digital Eric Genevois-Marlin - Head of R&D Digital & Data Science; Lionel Bascles - & Data Science; Lionel Bascles - Global Head, Global Head, Clinical Sciences & Operations; Audrey Lhomme - Head of Digital Clinical Sciences & Operations; Diane Wuest - Clinical Head of Digital R&D 10.15 am Digital challenges and opportunities for Sanofi R&D in France 11.10 am Jacques Volckmann - Head of R&D Hub France Diving deep into the single human cell Dr. Virginia Savova - Distinguished Scientists; Head of 10.45 am Single-Cell Biology Lab; Dr.Galina Boldina - Senior Data Anticipating next generation digital technologies in R&D with start-ups Scientist Bioinformatics Isabelle Thizon de Gaulle - Vice President Strategic initiatives & Scientific Relations EU; Charlotte Alibert - Project Manager, Scientific Relations & Initiatives; Jean-François Pomerol - Chief Executive Officer of TRIBVN Healthcare; 01.55 pm Matthieu Germain - Chief Executive Officer of Curadigm; Robert Mamoun - Patients first: when technology considers PhD, Chief Executive Officer of Ciloa SAS Company; Thomas Bourquard - human beings Chief Strategy Officer of MAbSilico Terttu Haring - Global Head of Clinical Digital & Data Innovation; Victoria DiBiaso -

AA-RD-2021-Mayo.Pdf
actualidad eroespacial EL PERIÓDICO DEe LOS PRrOFESoIONALeES DE LAs AEROpNÁUTICaA Y EL cESPACIOi al awww.actualidadaeroespacial.com Número 149 - Mayo de 2021 El PTA reparte 35 millones en su primera convocatoria Editorial Salvar al sector aeronáutico español Airbus ha desactivado su decisión de ce - escribió en un tuit: “Encuentro con el En una nueva reunión, el pasado 4 de fe - rrar la planta de Puerto Real, en Cádiz, al CEO de Airbus, Guillaume Faury, y eje - brero, Sánchez y Faury volvieron a abor - menos, por ahora. Sindicatos y políticos cutivos de la compañía. Compartimos dar los acuerdos firmados a finales del han estado luchando por defender la fac - iniciativas para relanzar el sector aeroes - mes de julio. La víspera de ese encuentro, toría y sus 300 puestos de trabajo desde pacial. Trabajamos juntos para preservar el Gobierno, la SEPI, los sindicatos y la que el fabricante europeo dejó de cons - los empleos y las capacidades tecnológi - Asociación Española de Tecnologías de truir el A380. Los trabajadores de la planta cas e industriales de España”. Defensa, Seguridad, Aeronáutica y Espa - asistida por robots habían ensamblado los cio (TEDAE) acordaron “un Plan de Cho - enormes estabilizadores horizontales para En el acuerdo conjunto firmado enton - que para el sector aeronáutico nacional el avión de pasajeros más grande del ces en Madrid se establece que, “Es - a fin de mantener las capacidades produc - mundo. El trabajo allí también se ha visto paña como país fundador de Airbus, tivas y el empleo en este sector estraté - interrumpido por una caída en la demanda sigue manteniendo sus ambiciones fun - gico para el tejido industrial español”.