Guia+Opnewblood.Pdf
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Twitter 101 Useful Tools and Resources Toby Greenwalt, Theanalogdivide.Com on Twitter: @Theanalogdivide
Twitter 101 Useful Tools and Resources Toby Greenwalt, theanalogdivide.com On Twitter: @theanalogdivide So you’ve created a Twitter account, entered your profile information, and uploaded a photo. Now what? Here are a few tools for making the most of your time with the service. You’ll be one of the shining Twitteratti before you know it! Finding Friends and Followers Twitter works best when you have a healthy crowd to talk to and share ideas with. Here’s a few suggestions for expanding your network. If you build it, they will come: Many people will find your account by virtue of their own searches. Be warned that not all of these people are actually interested in what you have to say, or are possibly even real people. Raid your address book: Twitter can scan your address book to see if any of your contacts are on the service. This is a quick and easy way to see who’s out there. The Kevin Bacon method: Once you’ve found a few friends, you can look at their friends, and their friends, and their friends… Discover the tangled web we, um, tweave! Lists: Similar to the Twibes and WeFollow directories listed below, Lists are user-compiled directories of Tweet- ers based around a well defined subject. How many lists are there for your community? Search Tools If you’ve gone through your immediate contacts, there are a few web tools for finding like minds. Twitter Grader (grader.twitter.com): Once you’ve found out your grade, click on the Elite buttons to find out who the BTOCs (Big Twitterers on Campus) are. -

Twitter Para Quien No Usa Twitter
Twitter ...para quien no usa Twitter Juan Diego Polo autor de wwwhatsnew.com descárgate este libro en www.bubok.com © Juan Diego Polo García 2009 [email protected] Licencia de uso Creative Commons, publicable, copiable, distribuíble de cualquier modo, NO editable, NO comercial, con obligación de citar al autor y la dirección http://wwwhatsnew.com Las marcas y logotipos aquí mostrados son marcas registradas y propiedad de sus respectivas compañías y sólo son usadas como referencia. Este libro es una publicación independiente y no está afiliada, autorizada, esponsorizada, o de cualquier otra manera aprobada por Twitter o cualquiera de las empresas nombradas en sus páginas. 1ª Edición Diseño de Portada: Lucas García - www.socialmood.com Impreso en España / Printed in Spain Impreso por Bubok 1 Índice de Contenido 1 - INTRODUCCIÓN..........................................................................5 1.1 - QUÉ ES TWITTER..............................................................................6 1.2 - QUIÉN ESCRIBE EN TWITTER............................................................10 1.3 - QUÉ SE PUEDE ESCRIBIR EN TWITTER...............................................13 1.4 - CÓMO SE DIVULGAN ENLACES EN TWITTER.......................................16 1.5 - CÓMO SE ENVÍAN MENSAJES A OTROS USUARIOS DE TWITTER............18 1.6 - CÓMO PUEDEN CLASIFICARSE LOS MENSAJES....................................22 2 - PARA QUÉ PODEMOS USAR TWITTER...........................................26 2.2 - PARA ENCONTRAR CLIENTES............................................................36 -

Social Media Compendium Oktober 2009
Social Media Compendium Oktober 2009 COMMUNITY PLATFORMS / SOCIAL NETWORKS NICHED COMMUNITIES BLOG PLATFORMS BLOG COMMUNITIES & TOOLS / FORUM BLOG SEARCH COMMENT / REPUTATION MICROMEDIA / MICROBLOGGING SOCIAL BOOKMARKING CROWDSOURCED CONTENT CUSTOMER SERVICE, REVIEWS TEXT & PRESENTATION PUBLISHING & SHARING IMAGE SHARING & HOSTING IMAGE SEARCH IMAGE EDITING MUSIC SHARING & STREAMING VIDEO PUBLISHING & SHARING INSTRUCTIONAL & EDUCATIONAL VIDEOS VIDEO SEARCH ENGINES VIDEO STREAMING FEEDS / NEWS AGGREGATOR SOCIAL AGGREGATOR / PROFILE MANAGER LOCATION!BASED EVENTS DIRECT COMMUNICATION "IM / SMS / VOICE# WIKIS COLLABORATIVE PLATFORMS PRODUCTIVITY TOOLS INFORMATION DATABASES / MONITORING MEDIA & COMMUNICATION BLOGS SEARCH ENGINES REAL!TIME SEARCH by Matthieu Hartig ■ [email protected] ■ @matthartig COMMUNITY PLATFORMS / SOCIAL NETWORKS facebook.com (2) Facebook is the world’s largest free-access social networking website. Users can join networks organized by city, workplace, school, and region to connect and interact with other people. People can also add friends and send them messages, and update their personal pro"les to notify friends. hi5.com (43) hi5 is an international social network with a local #avor. It enables members to stay connect- ed, share their lives, and learn what’s happening around them – through customizable pro"le pages, messaging, unlimited photo storage, hundreds of OpenSocial applications and more. friendster.com (117) Founded in 2002, Friendster is one of the web’s older social networking services. Adults, 16 and up can join and connect with friends, family, school, groups, activities and interests. $e site currently has over 50 million users. Over 90% of Friendster’s tra%c comes from Asia. tagged.com (109) Protecting the safety of their users is what makes Tagged di&erent from other social network- ing sites. -

Perceptions and Expressions of Social Presence During Conversations on Twitter
PERCEPTIONS AND EXPRESSIONS OF SOCIAL PRESENCE DURING CONVERSATIONS ON TWITTER A Thesis by KELLY MARIE PRITCHETT Submitted to the Office of Graduate Studies of Texas A&M University in partial fulfillment of the requirements for the degree of MASTER OF SCIENCE December 2011 Major Subject: Agricultural Leadership, Education, and Communications Perceptions and Expressions of Social Presence During Conversations on Twitter Copyright 2011 Kelly Marie Pritchett PERCEPTIONS AND EXPRESSIONS OF SOCIAL PRESENCE DURING CONVERSATIONS ON TWITTER A Thesis by KELLY MARIE PRITCHETT Submitted to the Office of Graduate Studies of Texas A&M University in partial fulfillment of the requirements for the degree of MASTER OF SCIENCE Approved by: Co-Chairs of Committee, Traci L. Naile Theresa Pesl Murphrey Committee Member R. Daniel Lineberger Head of Department, Jack Elliot December 2011 Major Subject: Agricultural Leadership, Education, and Communications iii ABSTRACT Perceptions and Expressions of Social Presence During Conversations on Twitter. (December 2011) Kelly Marie Pritchett, B.S., Texas A&M University Co-Chairs of Advisory Committee: Dr.Traci L. Naile Dr.Theresa Pesl Murphrey Computer-mediated environments such as social media create new social climates that impact communication interactions in un-mediated environments. This study examined social variables during conversations on Twitter through a qualitative document analysis that coded messages into affective, interactive or cohesive categories. Perceived social presence, participant satisfaction, and relationships between social presence and satisfaction among Twitter users during streaming conversations were examined through an online questionnaire that was created using qualtrics.com and made available to respondents over a one-week period. The researcher concluded that most social variables in the Twitter conversations of this study fall into the interactive social presence category. -

Brizzly / Samjshah
Brizzly / samjshah http://brizzly.com/ Search Twitter or find people you follow samjshah help settings contact logout Tip: typing 'j' and 'k' scrolls tweets up and down. Home Results for "#needaredstamp" Save this search Trends and news Profile Mentions samjshah finish answering the question! Add another Twitter acct #needaredstamp [esp. in calc when asking to find eqn of tan line... students will stop after finding deriv.] Direct messages about 9 minutes ago via Brizzly Inbox #thoushallnot why? mathheadinc 0÷5≠ the empty set #needaredstamp Sent Xmas why? about 5 hours ago via TweetDeck Reply Retweet Create a direct message Avatar why? Copenhagen why? Lists mathheadinc 88÷0≠88 #needaredstamp about 5 hours ago via TweetDeck Reply Retweet #uksnow why? Add a new list RATM why? mathheadinc √(3^2+7^2) ≠ 10 #needaredstamp Iron Man 2 why? about 7 hours ago via TweetDeck Reply Retweet #omgfacts why? Collier why? nyates314 Yes indeed! RT @k8nowak @dgreenedcp @jbrtva @SweenWSweens That is a three part question, ? NOT multiple choice #needaredstamp about 7 hours ago via Power Twitter Reply Retweet Do you like Brizzly? Tell your friends & followers, and include an invitation. druinok Remember the example that we did in class that I told you to STAR and study? This is why! #needaredstamp about 7 hours ago via web Reply Retweet druinok I am totally cracking up at the #needaredstamp posts - you guys rock!!! Just what I needed this last week of school :) about 7 hours ago via web Reply Retweet k8nowak So embarrassing. So true. RT @SweenWSweens: That is a three part question, NOT multiple choice #needaredstamp about 7 hours ago via Brizzly Reply Retweet dgreenedcp @jbrtva RT @SweenWSweens That is a three part question, NOT multiple choice #needaredstamp // Snif. -

Public Sector Social Media Training – 17Th March
Public Sector Social Media Training – 17 th March James Fitzgerald, Social Media Academy Director Agenda 1. Background 2. Social Media Marketing – Disseminate – Engage – Participate 3. Measurement & evaluation metrics My background My background My background My background Social Media Marketing Social Media Objectives Increasing the number of links Raising awareness from quality websites Search engine ranking boost Website traffic Social Media Marketing • A social media strategy can broadly be defined as possessing three parts 1. Dissemination 2. Engagement 3. Participation • The extent to which you perform either will be essentially be dictated by – Overall objectives – Timings – Resources (manpower vs. spend) • In an ideal world you would maximise all three parts, however given potential restrictions, as outlined above, you may begin with the first element and then graduate to include all three • There are few examples of companies exercising all three well and simultaneously Social Media Marketing • There a variety of ways in which you are able to evaluate your social media activity, given the ease of capturing data and usage online • Decide how you wish to evaluate your success based on your overall campaign objectives • If you want to drive people to download a report then you need to plan in advance how this will be recorded? Alternatively if you want to brand awareness how will you measure this? Data Capture? Drive traffic? Improve SEO? • Deciding upon this in advance will not only help determine your overall strategy but will also help demonstrate ROI which actually has value • Typically it makes most sense for internal/ agency marketing personnel to work together on this, i.e. -
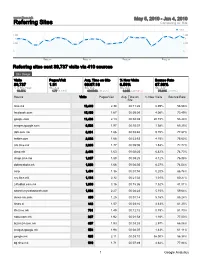
Referring Sites Comparing To: Site
www.time.mk May 5, 2010 - Jun 4, 2010 Referring Sites Comparing to: Site Visits 4,000 4,000 2,000 2,000 0 0 May 10 May 17 May 24 May 31 Referring sites sent 89,737 visits via 410 sources Site Usage Visits Pages/Visit Avg. Time on Site % New Visits Bounce Rate 89,737 1.91 00:07:16 6.59% 67.93% % of Site Total: Site Avg: Site Avg: Site Avg: Site Avg: 10.45% 1.77 (8.19%) 00:05:16 (38.25%) 9.24% (-28.63%) 74.39% (-8.68%) Source Visits Pages/Visit Avg. Time on % New Visits Bounce Rate Site time.mk 16,449 2.30 00:11:26 0.09% 56.56% facebook.com 15,169 1.67 00:05:01 4.06% 73.49% google.com 11,496 2.13 00:04:39 20.79% 58.24% images.google.com 6,566 1.97 00:10:37 1.58% 65.25% 365.com.mk 6,361 1.66 00:03:45 9.75% 77.87% twitter.com 2,892 1.68 00:23:53 4.15% 75.62% srb.time.mk 2,680 1.77 00:05:05 1.53% 72.72% okno.mk 2,446 1.63 00:02:25 6.42% 74.73% shqip.time.mk 1,867 1.80 00:03:25 4.12% 76.38% dobrarabota.mk 1,626 1.66 00:04:03 6.27% 74.54% corp 1,488 1.36 00:01:58 0.20% 86.76% cro.time.mk 1,183 2.32 00:21:32 1.01% 60.27% 24fudbal.com.mk 1,090 3.16 00:15:36 7.52% 41.01% search.mywebsearch.com 1,068 2.27 00:04:22 5.15% 59.64% alexa-mk.com 969 1.25 00:01:14 5.16% 85.24% times.si 842 1.57 00:03:16 4.63% 81.35% life.time.mk 761 1.49 00:12:15 0.79% 81.73% nabu.com.mk 687 1.92 00:01:58 1.16% 77.00% biznis24.com.mk 607 1.93 00:03:33 2.97% 66.06% images.google.mk 558 1.98 00:04:07 1.43% 61.11% google.mk 525 2.11 00:03:10 36.00% 56.38% bg.time.mk 519 1.71 00:07:49 4.62% 77.84% 1 Google Analytics crnobelo.com 519 1.46 00:01:32 0.19% 80.73% mkfondovi.com -

Para Quien No Usa Twitter
Twitter ...para quien no usa Twitter Juan Diego Polo autor de wwwhatsnew.com descárgate este libro en www.bubok.com © Juan Diego Polo García 2009 [email protected] Licencia de uso Creative Commons, publicable, copiable, distribuíble de cualquier modo, NO editable, NO comercial, con obligación de citar al autor y la dirección http://wwwhatsnew.com Las marcas y logotipos aquí mostrados son marcas registradas y propiedad de sus respectivas compañías y sólo son usadas como referencia. Este libro es una publicación independiente y no está afiliada, autorizada, esponsorizada, o de cualquier otra manera aprobada por Twitter o cualquiera de las empresas nombradas en sus páginas. 1ª Edición Diseño de Portada: Lucas García - www.socialmood.com Impreso en España / Printed in Spain Impreso por Bubok 1 Índice de Contenido 1 - INTRODUCCIÓN..........................................................................5 1.1 - QUÉ ES TWITTER..............................................................................6 1.2 - QUIÉN ESCRIBE EN TWITTER............................................................10 1.3 - QUÉ SE PUEDE ESCRIBIR EN TWITTER...............................................13 1.4 - CÓMO SE DIVULGAN ENLACES EN TWITTER.......................................16 1.5 - CÓMO SE ENVÍAN MENSAJES A OTROS USUARIOS DE TWITTER............18 1.6 - CÓMO PUEDEN CLASIFICARSE LOS MENSAJES....................................22 2 - PARA QUÉ PODEMOS USAR TWITTER...........................................26 2.2 - PARA ENCONTRAR CLIENTES............................................................36 -

Best Free Antivirus Software
BEST FREE ANTIVIRUS SOFTWARE SEPTEMBER 2010 fIrST LOOKS: Lenovo IdeaCentre B500 20 Twitter Tools You Can’t Live Without How to Build a Linux PC for $200 TOP 100 FREE MOBILe APPS • Google Android • Apple iPhone • BlackBerry • Palm • Symbian • Windows Mobile Plus The New BlackBerry Torch 9800 >> september 2010 vol. 29 no. 9 42 COVER STORY The top 100 Free mobile apps The dream of turning your phone into a PC on the go would be nothing without the right apps. In this blockbuster story, we include the best free apps for iPhone, Android, Palm, Symbian, and Windows Mobile phones. You’ll find everything from e-book readers to VoIP. PC MAGAZINE DIGITAL EDITION september 2010 storemags & fantamag - magazines for all 17 23 FIRST LOOKS tech newS 12 hardware 5 Front Side Lenovo IdeaCentre B500 The “Internet kill switch” bill; wood- Ava Direct Nano Cube en iPhone skins; building a $200 Linux PC; the coolest laptop bags. Dell Studio XPS 7100 Acer Aspire AS5741Z-5433 OPINIONS Casio Green Slim XJ-A145U 2 First Word: Plus Quick Looks Lance Ulanoff 36 John C. Dvorak 20 CONSUMER ELECTRONICS 38 Sascha Segan Sony Bravia KDL-55HX800 40 Dan Costa BlackBerry Torch Panasonic Lumix DMC-TS2 SOLUTIONS Plus Quick Looks 64 Top Twitter Tools Want to tweet with the pros? 26 BUSINESS Check out our list of handy Twitter HP Z200 companion apps and services. Imation Defender F200 + Bio 72 security: Free Av Software HP LaserJet Enterprise P3015dn Sure, pay suites are more powerful, but our list of free AV and anti- 30 SOFTWARE malware apps can also get the job Webroot AntiVirus 2011 done. -

Twitter® Application Development for Dummies‰
™ Making Everything Easier! Twitter ® Application Development Learn to: $response = $twitter->status->update • Turn your ideas into applications ('Developing a killer new Twitter app!'); • Develop apps with a high chance of success • Find out what users are looking for • Make money from your apps Dusty Reagan, @DustyReagan Creator of FriendOrFollow.com Twitter app www.allitebooks.com Get More and Do More at Dummies.com® Start with FREE Cheat Sheets Cheat Sheets include • Checklists • Charts • Common Instructions • And Other Good Stuff! To access the Cheat Sheet created specifically for this book, go to www.dummies.com/cheatsheet/twitterappdev Get Smart at Dummies.com Dummies.com makes your life easier with 1,000s of answers on everything from removing wallpaper to using the latest version of Windows. Check out our • Videos • Illustrated Articles • Step-by-Step Instructions Plus, each month you can win valuable prizes by entering our Dummies.com sweepstakes. * Want a weekly dose of Dummies? Sign up for Newsletters on • Digital Photography • Microsoft Windows & Office • Personal Finance & Investing • Health & Wellness • Computing, iPods & Cell Phones • eBay • Internet • Food, Home & Garden Find out “HOW” at Dummies.com *Sweepstakes not currently available in all countries; visit Dummies.com for official rules. www.allitebooks.com Twitter® Application Development FOR DUMmIES‰ by Dusty Reagan www.allitebooks.com Twitter® Application Development For Dummies® Published by Wiley Publishing, Inc. 111 River Street Hoboken, NJ 07030-5774 www.wiley.com -

HERALD- SPECTATOR I Rihlirsday I)Ccernher 28, 20J7 Niiesheraldspectatoicom - Special Shopping
o HERALD- SPECTATOR I rihLIrsday I)ccernher 28, 20J7 niiesheraLdspectatoicom - Special shopping CHICAGO TRIBUNE trip Best thing I ate ChefVince DiBattista said his favorite local Nues police officers help meal of2017 was the BeefWellington for Two at Swift & Sons in Chicago. Dozens of area childrenpick out area restaurant professionals share their top dish ofthe year. Pages 22-2 5 holiday gifts.Page 4 LOVE ESSENTIALLY Resolutions happen throughout the year New Year's resolutions are great because they give us hope and inspiration and a NILES POLICE DEPARTMENT PHOTO sense ofpurpose. But before you move forward, it's wise to reflect on the past. Officers from the Nues Police Department went Pilossoph, Page 18 shopping with some area children at Walmart in Nues on Dec. 9 as part of the Shop with a Cop" program. Twenty-five children from 15 families were give$100gift cards to the store to use for holiday shopping. SPORTS LIVING Fighting isolation in older adults The number of seniors aging solo is expected to grow to lin 4 of the 76 million baby boomers, prompting researchers and groups BRIAN OMAHONEY/DAILV SOUTNTOWN such as the YMCA and AARP to focus on keeping individuals involved in their commu- nities. Inside A look back at 2017 Area athletic directors reflect on past year, STEVE DEBENPORT/GETTY look ahead to 2018. Pages 35 & 37 SHOUT OUT NILEs HERALD- SPECTATOR nilesheraldspectator.com Brooke Roothaan, long-time librarian Brooke Roothaan, Lincoinwood It'scalled"Jane, the Virgin." Jim Rotche, Generaj Manager Public Library youth and teen There's mystery and drama. -
Social Media Monitoring Tools (SMM)
all about SOCIAL MEDIA * * * * MONITORING TOOLS The explosion of social media has led to a growing and bustling market for social media monitoring tools (SMM). These tools crawl blogs and social networks for brand mentions and enable companies to build communities and engage with their customers. But with hundreds of options for social media monitoring tools out there, the space is cluttered and confusing for professionals investing in the software. What follows is a collection of data from a survey conducted by oneforty that answers questions like “how much do people usually pay for SMM tools?” to “which SMM tool is best?” Who is buying SMM tools? arranged by job title 10% 10% of respondents said that they were a “Marketing Executive.” 10.7% 42.9% 42.9% “Social Media Manager” 10.7% “Small Business Manager” 17.1% 19.3% “Agency Professional” 17.1% “Consultant” 19.3% What factors affect the selection of a SMM tool? Survey participants were asked to rate different factors according to how important that particular factor affected their selection of a SMM tool. On a scale of 1 to 4, with 4 being the most important factor. The data for each “factor” is presented as an average rating. 4 3 2.47 2.33 2.29 2.13 1.82 2 1.42 1.39 1 What metrics Integrations with Ability to Relationship with it offers different social schedule updates the vendor networks Interface Price Firehose access How much do people pay for SMM tools? 2.2% 4.4% 2.2% of respondents say that they spend $10,000/month or more on SMM tools.