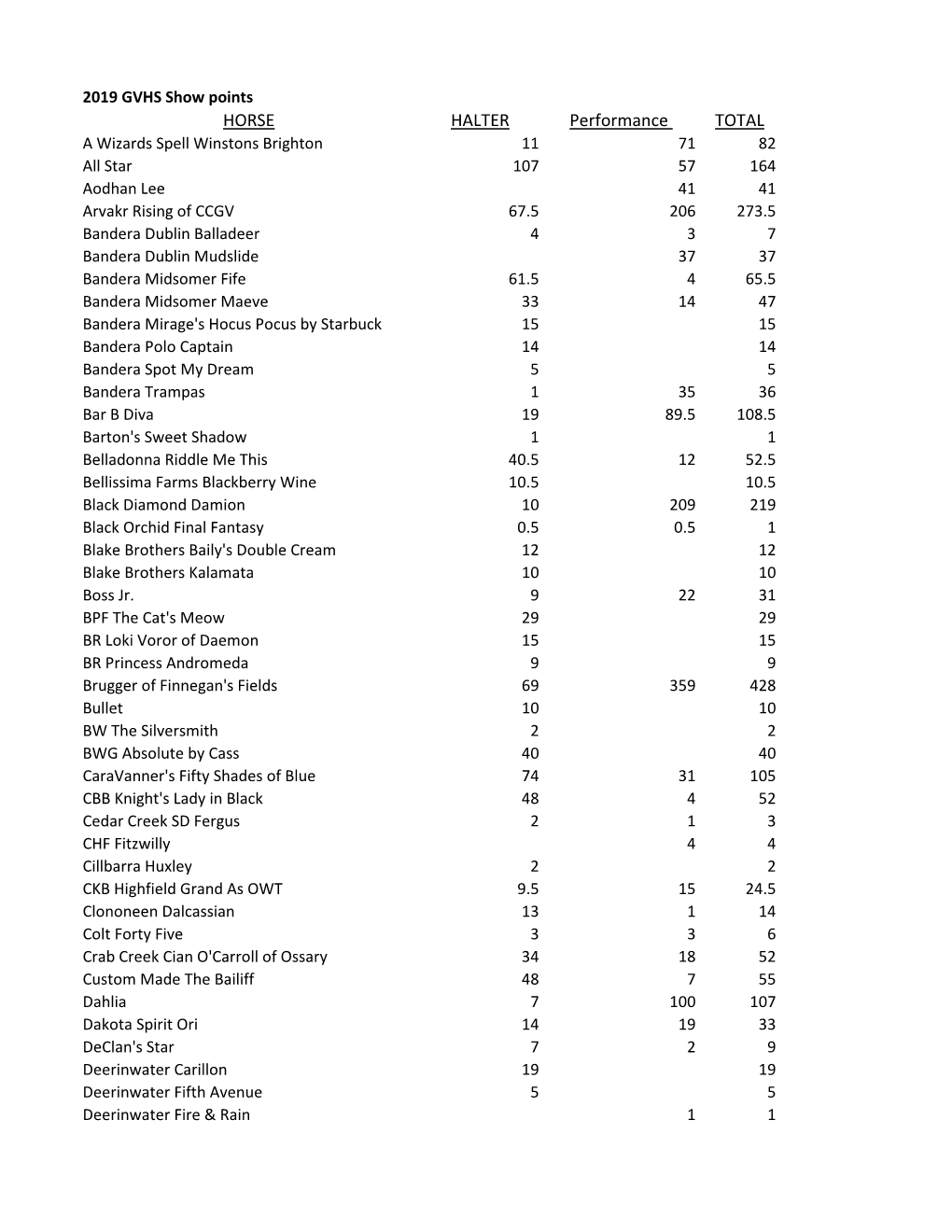
Show Points 2019
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Design of Rijndael: AES - the Advanced Encryption Standard/Joan Daemen, Vincent Rijmen
Joan Daernen · Vincent Rijrnen Theof Design Rijndael AES - The Advanced Encryption Standard With 48 Figures and 17 Tables Springer Berlin Heidelberg New York Barcelona Hong Kong London Milan Paris Springer TnL-1Jn Joan Daemen Foreword Proton World International (PWI) Zweefvliegtuigstraat 10 1130 Brussels, Belgium Vincent Rijmen Cryptomathic NV Lei Sa 3000 Leuven, Belgium Rijndael was the surprise winner of the contest for the new Advanced En cryption Standard (AES) for the United States. This contest was organized and run by the National Institute for Standards and Technology (NIST) be ginning in January 1997; Rij ndael was announced as the winner in October 2000. It was the "surprise winner" because many observers (and even some participants) expressed scepticism that the U.S. government would adopt as Library of Congress Cataloging-in-Publication Data an encryption standard any algorithm that was not designed by U.S. citizens. Daemen, Joan, 1965- Yet NIST ran an open, international, selection process that should serve The design of Rijndael: AES - The Advanced Encryption Standard/Joan Daemen, Vincent Rijmen. as model for other standards organizations. For example, NIST held their p.cm. Includes bibliographical references and index. 1999 AES meeting in Rome, Italy. The five finalist algorithms were designed ISBN 3540425802 (alk. paper) . .. by teams from all over the world. 1. Computer security - Passwords. 2. Data encryption (Computer sCIence) I. RIJmen, In the end, the elegance, efficiency, security, and principled design of Vincent, 1970- II. Title Rijndael won the day for its two Belgian designers, Joan Daemen and Vincent QA76.9.A25 D32 2001 Rijmen, over the competing finalist designs from RSA, IBl\!I, Counterpane 2001049851 005.8-dc21 Systems, and an English/Israeli/Danish team. -

Productivity Revisited: Shifting Paradigms in Analysis and Policy
Productivity Revisited Productivity Revisited Shifting Paradigms in Analysis and Policy Ana Paula Cusolito and William F. Maloney © 2018 International Bank for Reconstruction and Development / The World Bank 1818 H Street NW, Washington, DC 20433 Telephone: 202-473-1000; Internet: www.worldbank.org Some rights reserved 1 2 3 4 21 20 19 18 This work is a product of the staff of The World Bank with external contributions. The fi ndings, interpretations, and conclusions expressed in this work do not necessarily refl ect the views of The World Bank, its Board of Execu- tive Directors, or the governments they represent. The World Bank does not guarantee the accuracy of the data included in this work. The boundaries, colors, denominations, and other information shown on any map in this work do not imply any judgment on the part of The World Bank concerning the legal status of any territory or the endorsement or acceptance of such boundaries. Nothing herein shall constitute or be considered to be a limitation upon or waiver of the privileges and immu- nities of The World Bank, all of which are specifi cally reserved. Rights and Permissions This work is available under the Creative Commons Attribution 3.0 IGO license (CC BY 3.0 IGO) http:// creativecommons.org/licenses/by/3.0/igo. Under the Creative Commons Attribution license, you are free to copy, distribute, transmit, and adapt this work, including for commercial purposes, under the following conditions: Attribution—Please cite the work as follows: Cusolito, Ana Paula, and William F. Maloney. 2018. Productivity Revisited: Shifting Paradigms in Analysis and Policy. -

U.S. Department of Transportation Federal
U.S. DEPARTMENT OF ORDER TRANSPORTATION JO 7340.2E FEDERAL AVIATION Effective Date: ADMINISTRATION July 24, 2014 Air Traffic Organization Policy Subject: Contractions Includes Change 1 dated 11/13/14 https://www.faa.gov/air_traffic/publications/atpubs/CNT/3-3.HTM A 3- Company Country Telephony Ltr AAA AVICON AVIATION CONSULTANTS & AGENTS PAKISTAN AAB ABELAG AVIATION BELGIUM ABG AAC ARMY AIR CORPS UNITED KINGDOM ARMYAIR AAD MANN AIR LTD (T/A AMBASSADOR) UNITED KINGDOM AMBASSADOR AAE EXPRESS AIR, INC. (PHOENIX, AZ) UNITED STATES ARIZONA AAF AIGLE AZUR FRANCE AIGLE AZUR AAG ATLANTIC FLIGHT TRAINING LTD. UNITED KINGDOM ATLANTIC AAH AEKO KULA, INC D/B/A ALOHA AIR CARGO (HONOLULU, UNITED STATES ALOHA HI) AAI AIR AURORA, INC. (SUGAR GROVE, IL) UNITED STATES BOREALIS AAJ ALFA AIRLINES CO., LTD SUDAN ALFA SUDAN AAK ALASKA ISLAND AIR, INC. (ANCHORAGE, AK) UNITED STATES ALASKA ISLAND AAL AMERICAN AIRLINES INC. UNITED STATES AMERICAN AAM AIM AIR REPUBLIC OF MOLDOVA AIM AIR AAN AMSTERDAM AIRLINES B.V. NETHERLANDS AMSTEL AAO ADMINISTRACION AERONAUTICA INTERNACIONAL, S.A. MEXICO AEROINTER DE C.V. AAP ARABASCO AIR SERVICES SAUDI ARABIA ARABASCO AAQ ASIA ATLANTIC AIRLINES CO., LTD THAILAND ASIA ATLANTIC AAR ASIANA AIRLINES REPUBLIC OF KOREA ASIANA AAS ASKARI AVIATION (PVT) LTD PAKISTAN AL-AAS AAT AIR CENTRAL ASIA KYRGYZSTAN AAU AEROPA S.R.L. ITALY AAV ASTRO AIR INTERNATIONAL, INC. PHILIPPINES ASTRO-PHIL AAW AFRICAN AIRLINES CORPORATION LIBYA AFRIQIYAH AAX ADVANCE AVIATION CO., LTD THAILAND ADVANCE AVIATION AAY ALLEGIANT AIR, INC. (FRESNO, CA) UNITED STATES ALLEGIANT AAZ AEOLUS AIR LIMITED GAMBIA AEOLUS ABA AERO-BETA GMBH & CO., STUTTGART GERMANY AEROBETA ABB AFRICAN BUSINESS AND TRANSPORTATIONS DEMOCRATIC REPUBLIC OF AFRICAN BUSINESS THE CONGO ABC ABC WORLD AIRWAYS GUIDE ABD AIR ATLANTA ICELANDIC ICELAND ATLANTA ABE ABAN AIR IRAN (ISLAMIC REPUBLIC ABAN OF) ABF SCANWINGS OY, FINLAND FINLAND SKYWINGS ABG ABAKAN-AVIA RUSSIAN FEDERATION ABAKAN-AVIA ABH HOKURIKU-KOUKUU CO., LTD JAPAN ABI ALBA-AIR AVIACION, S.L. -

A CELEBRATION of BURGUNDY an Auction of Finest & Rarest Wines
SATURDAY, MARCH 28, 2015 A CELEBRATION OF BURGUNDY An Auction of Finest & Rarest Wines 8:30AM AT TRU RESTAURANT TRU Restaurant 676 N. St. Clair Street Chicago Those bidding or sending inquiries should refer to this auction as Sale #1503 “MCKINLEY” Lots 1 - 1440 HART DAVIS HART WINE CO. 1511 W. 38TH STREET, CHICAGO, IL 60609 tel: 312.482.9996 fax: 312.335.9096 www.hdhwine.com Table of Contents Letter from the CEO 3 HDH Event: Fête des Chablis 4 HDH Event: A Celebration of Burgundy 5 HDH Retail Selections 6 Lots 1 - 1440 7-122 Index of Wines 123-168 Grower Index 131-140 Half-Bottle & Large Format Index 140-142 OWC Index 142-143 Ullage, Bottle Size Descriptions & Abbreviations Used in this Catalog; Our Auction Venue: TRU Restaurant 145 Procedures for Bidding & Payment 146 Conditions of Sale 147 Collection, Delivery & Storage 148 About HDH & How to Sell your Wines with HDH 150 Delivery & Collection Instructions Form 151 Absentee Bidding Form 153-154 Upcoming Auction Dates: May 16, 2015 June 27, 2015 September 19, 2015 Photo Pictured on Front Cover: “Savigny-les-Beaune” by Michel Joly Photo Pictured on Back Cover: “Le Montrachet” by Michel Joly March 2015 On behalf of the entire HDH team, I want to thank our bidders and consignors who participated in the February 13th auction, our fi rst of 2015. The auction was full of impressive consignments and we saw record demand and strong results in nearly every category. It’s only because of your interest and support that we are able to bring you auctions of this caliber, and we sincerely thank you. -

Catalog, Make This One of the Best Sales in Which I Have Been Involved in My 30 Year Career in the Wine Business
An Auction of Finest & Rarest Wines Saturday, April 8 at 9:00 am At the Chicago Athletic Association 12 South Michigan Avenue, Chicago Those bidding or sending inquiries should refer to this auction as Sale #0604 “MIA” March, 2006 Dear Client: In 2005 I began a partnership with long time auction experts Michael Davis and Paul Hart, forming Hart Davis Hart Wine Co. with a shared goal to create the best and most trusted venue in the United States for buying and selling fine and rare wine. We are deeply gratified by the response that we have received among collectors and restaurateurs worldwide. Here are some of the highlights of our first year: • $9.5 million of wine sold at auction • 97% of auction lots sold • Bids received from 36 states and 14 countries. • Our September 2005 auction broke the record for the largest wine auction ever held in Chicago, besting auctions held by Christie’s, Sotheby’s and Davis & Co.! We proceeded to shatter this record once again in November. 2006 promises to be even more exciting. Our first auction in January sold 96% of the lots offered totaling more than $2.1 million. The wines in our extraordinary April auction, as showcased in this catalog, make this one of the best sales in which I have been involved in my 30 year career in the wine business. Within these pages, you will find consignments of impeccable provenance from some of the most important collectors in the world. I hope that I will see you at the auction on April 8th. -

Identifying Open Research Problems in Cryptography by Surveying Cryptographic Functions and Operations 1
International Journal of Grid and Distributed Computing Vol. 10, No. 11 (2017), pp.79-98 http://dx.doi.org/10.14257/ijgdc.2017.10.11.08 Identifying Open Research Problems in Cryptography by Surveying Cryptographic Functions and Operations 1 Rahul Saha1, G. Geetha2, Gulshan Kumar3 and Hye-Jim Kim4 1,3School of Computer Science and Engineering, Lovely Professional University, Punjab, India 2Division of Research and Development, Lovely Professional University, Punjab, India 4Business Administration Research Institute, Sungshin W. University, 2 Bomun-ro 34da gil, Seongbuk-gu, Seoul, Republic of Korea Abstract Cryptography has always been a core component of security domain. Different security services such as confidentiality, integrity, availability, authentication, non-repudiation and access control, are provided by a number of cryptographic algorithms including block ciphers, stream ciphers and hash functions. Though the algorithms are public and cryptographic strength depends on the usage of the keys, the ciphertext analysis using different functions and operations used in the algorithms can lead to the path of revealing a key completely or partially. It is hard to find any survey till date which identifies different operations and functions used in cryptography. In this paper, we have categorized our survey of cryptographic functions and operations in the algorithms in three categories: block ciphers, stream ciphers and cryptanalysis attacks which are executable in different parts of the algorithms. This survey will help the budding researchers in the society of crypto for identifying different operations and functions in cryptographic algorithms. Keywords: cryptography; block; stream; cipher; plaintext; ciphertext; functions; research problems 1. Introduction Cryptography [1] in the previous time was analogous to encryption where the main task was to convert the readable message to an unreadable format. -

The Design of Rijndael
Information Security and Cryptography The Design of Rijndael AES - The Advanced Encryption Standard Bearbeitet von Joan Daemen, Vincent Rijmen 1. Auflage 2002. Buch. xvii, 238 S. Hardcover ISBN 978 3 540 42580 9 Format (B x L): 15,5 x 23,5 cm Gewicht: 563 g Weitere Fachgebiete > EDV, Informatik > Datenbanken, Informationssicherheit, Geschäftssoftware > Informations- und Kodierungstheorie schnell und portofrei erhältlich bei Die Online-Fachbuchhandlung beck-shop.de ist spezialisiert auf Fachbücher, insbesondere Recht, Steuern und Wirtschaft. Im Sortiment finden Sie alle Medien (Bücher, Zeitschriften, CDs, eBooks, etc.) aller Verlage. Ergänzt wird das Programm durch Services wie Neuerscheinungsdienst oder Zusammenstellungen von Büchern zu Sonderpreisen. Der Shop führt mehr als 8 Millionen Produkte. Contents 1. The Advanced Encryption Standard Process .............. 1 1.1 IntheBeginning... .................................... 1 1.2 AES:ScopeandSignificance............................. 1 1.3 StartoftheAESProcess................................ 2 1.4 TheFirstRound....................................... 3 1.5 Evaluation Criteria . 4 1.5.1 Security . 4 1.5.2 Costs . 4 1.5.3 Algorithm and Implementation Characteristics . 4 1.6 Selection of Five Finalists . 5 1.6.1 The Second AES Conference . 5 1.6.2 The Five Finalists . 6 1.7 The Second Round . 7 1.8 The Selection . 7 2. Preliminaries ............................................. 9 2.1 FiniteFields........................................... 10 2.1.1 Groups, Rings, and Fields . 10 2.1.2 Vector Spaces . 11 2.1.3 Fields with a Finite Number of Elements . 13 2.1.4 Polynomials over a Field . 13 2.1.5 Operations on Polynomials . 14 2.1.6 Polynomials and Bytes . 15 2.1.7 Polynomials and Columns . 16 2.2 LinearCodes .......................................... 17 2.2.1 Definitions . -

Statistical Cryptanalysis of Block Ciphers
STATISTICAL CRYPTANALYSIS OF BLOCK CIPHERS THÈSE NO 3179 (2005) PRÉSENTÉE À LA FACULTÉ INFORMATIQUE ET COMMUNICATIONS Institut de systèmes de communication SECTION DES SYSTÈMES DE COMMUNICATION ÉCOLE POLYTECHNIQUE FÉDÉRALE DE LAUSANNE POUR L'OBTENTION DU GRADE DE DOCTEUR ÈS SCIENCES PAR Pascal JUNOD ingénieur informaticien dilpômé EPF de nationalité suisse et originaire de Sainte-Croix (VD) acceptée sur proposition du jury: Prof. S. Vaudenay, directeur de thèse Prof. J. Massey, rapporteur Prof. W. Meier, rapporteur Prof. S. Morgenthaler, rapporteur Prof. J. Stern, rapporteur Lausanne, EPFL 2005 to Mimi and Chlo´e Acknowledgments First of all, I would like to warmly thank my supervisor, Prof. Serge Vaude- nay, for having given to me such a wonderful opportunity to perform research in a friendly environment, and for having been the perfect supervisor that every PhD would dream of. I am also very grateful to the president of the jury, Prof. Emre Telatar, and to the reviewers Prof. em. James L. Massey, Prof. Jacques Stern, Prof. Willi Meier, and Prof. Stephan Morgenthaler for having accepted to be part of the jury and for having invested such a lot of time for reviewing this thesis. I would like to express my gratitude to all my (former and current) col- leagues at LASEC for their support and for their friendship: Gildas Avoine, Thomas Baign`eres, Nenad Buncic, Brice Canvel, Martine Corval, Matthieu Finiasz, Yi Lu, Jean Monnerat, Philippe Oechslin, and John Pliam. With- out them, the EPFL (and the crypto) would not be so fun! Without their support, trust and encouragement, the last part of this thesis, FOX, would certainly not be born: I owe to MediaCrypt AG, espe- cially to Ralf Kastmann and Richard Straub many, many, many hours of interesting work. -

Understanding How to Prevent Sensitive Data Exposure
Understanding how to prevent Sensitive Data Exposure Dr Simon Greatrix Just Trust The Internet! • Lots of free advice • Opinions to suit all tastes • Also has pictures of cats! • Not responsible for the collapse of civilization (so far) • Google has excellent branding Top tips for a successful presentation! (according to the internet) • Start with a joke • Imagine the audience naked • Avoid showing emotion • Use images to jazz things up Obligatory famous historical data breaches ● 200,000 BCE to 6000 BCE : Tribal life with no privacy at all ● 600 BCE to 400CE: Ancient City culture view privacy as a bad thing ● 75 CE to 800 CE: There is no word for “privacy” in classical nor medieval“Where Latin people conceal their ways from one another … ● 1215 CE:there Fourth no Council one will Of ever Lateran rightly makes gain neitherconfession their mandatory due honour nor office nor the justice that is befitting” ● 1450 CE: First use of “privacy” in English. Socrates (470 to 399 BCE) ● 1700 CE: Solo beds ● 1890 CE: First use of “Right To Privacy” What are we actually expected to do? ● The Standards – OWASP – PCI-DSS ● The Tools – Ciphers – Hashes An aside: What is “strong encryption”? Source: https://www.keylength.com Is this really a good idea? https://xkcd.com/538/ Your Personal Information Please don’t send us your personal information. We do not want your personal information. We have a hard enough time keeping track of our own personal information, let alone yours. If you tell us your name, or any identifying information, we will forget it immediately. -

Albania, of the Other Part
L 107/166 EN Official Journal of the European Union 28.4.2009 STABILISATION AND ASSOCIATION AGREEMENT between the European Communities and their Member States, of the one part, and the Republic of Albania, of the other part THE KINGDOM OF BELGIUM, THE CZECH REPUBLIC, THE KINGDOM OF DENMARK, THE FEDERAL REPUBLIC OF GERMANY, THE REPUBLIC OF ESTONIA THE HELLENIC REPUBLIC, THE KINGDOM OF SPAIN, THE FRENCH REPUBLIC, IRELAND, THE ITALIAN REPUBLIC, THE REPUBLIC OF CYPRUS, THE REPUBLIC OF LATVIA, THE REPUBLIC OF LITHUANIA, THE GRAND DUCHY OF LUXEMBOURG, THE REPUBLIC OF HUNGARY, THE REPUBLIC OF MALTA, THE KINGDOM OF THE NETHERLANDS, THE REPUBLIC OF AUSTRIA, THE REPUBLIC OF POLAND, THE PORTUGUESE REPUBLIC, THE REPUBLIC OF SLOVENIA, THE SLOVAK REPUBLIC, THE REPUBLIC OF FINLAND, THE KINGDOM OF SWEDEN, THE UNITED KINGDOM OF GREAT BRITAIN AND NORTHERN IRELAND, Contracting Parties to the Treaty establishing the European Community, the Treaty establishing the European Atomic Energy Community and the Treaty on European Union, hereinafter referred to as the ‘Member States’, and THE EUROPEAN COMMUNITY, THE EUROPEAN ATOMIC ENERGY COMMUNITY, hereinafter referred to as the ‘Community’, of the one part, and THE REPUBLIC OF ALBANIA, hereinafter referred to as ‘Albania’, of the other part, 28.4.2009 EN Official Journal of the European Union L 107/167 CONSIDERING the strong links between the Parties and the values that they share and their desire to strengthen those links and establish a close and lasting relationship based on reciprocity and mutual interest, which -

Evolving S-Boxes with Reduceddifferential Power
Evolving S-Boxes with Reduced Differential Power Analysis Susceptibility Merrielle Spain1 and Mayank Varia2† 1 MIT Lincoln Laboratory,‡ [email protected] 2 Boston University, [email protected] Abstract. Differential power analysis targets S-boxes to break ciphers that resist cryptanalysis. We relax cryptanalytic constraints to lower S-box leakage, as quantified by the transparency order. We apply genetic algorithms to generate 8-bit S-boxes, optimizing transparency order and nonlinearity as in existing work (Picek et al. 2015). We apply multiobjective evolutionary algorithms to generate a Pareto front. We find a tight relationship where nonlinearity drops substantially before transparency order does, suggesting the difficulty of finding S-boxes with high nonlinearity and low transparency order, if they exist. Additionally, we show that the cycle crossover yields more efficient single objective genetic algorithms for generating S-boxes than the existing literature. We demonstrate this in the first side-by-side comparison of the genetic algorithms of Millan et al. 1999, Wang et al. 2012, and Picek et al. 2015. Finally, we propose and compare several methods for avoiding fixed points in S-boxes; repairing a fixed point after evolution in a way that preserves fitness was superior to including a fixed point penalty in the objective function or randomly repairing fixed points during or after evolution. Keywords: S-box · nonlinearity · transparency order · genetic algorithm · multiobjec- tive evolutionary algorithm · cycle crossover · differential power analysis · cryptanalysis · trade-off · Pareto front 1 Introduction Block ciphers are a versatile, foundational primitive within symmetric-key cryptogra- phy. They underpin symmetric-key encryption schemes [Dwo01], message authentication codes [Dwob], authenticated encryption schemes [Dwoa,Dwo07,Dwo10], and hash func- tions [PGV93, BRSS10]. -

From AES to Dynamic
Khoa học và Công nghệ trong lĩnh vực An toàn thông tin From AES to Dynamic AES Pablo Freyre, Oristela Cuellar, Nelson Díaz and Adrián Alfonso Abstract—The cryptographic algorithm AES Other cryptographic algorithms have been (Advanced Encryption Standard) works with the proposed with dynamic transformations in transformations SubBytes, ShiftRows, terms of greater security in their design. Two MixColumns and AddRoundKey, all of them fixed examples are: the block cipher Twofish [19], and selected a priori. In this paper, we will show resulting a finalist in the AES competition, and dynamic variants of AES, where the new the block cipher Grand Cru [17], submitted to transformations are RandomSubBytes, RandomShiftRows, RandomMixColumns and the NESSIE process. RandomAffineTransfKey. The aim of this paper is to show dynamic Tóm tắt—Thuật toán mã hóa AES (Tiêu chuẩn variants of the block cipher AES, working in all mã hóa nâng cao) bao gồm các phép biến đổi cases with the transformations RandomSubBytes, SubBytes, ShiftRows, MixColumn và RandomShiftRows, RandomMixColumns and AddRoundKey. Tất cả các phép biến đổi này đều RandomAffineTransfKey, which are obtained at cố định và được chọn ưu tiên. Trong bài báo này, random from the set of all its possible choices. nhóm tác giả sẽ trình bày một số biến thể động của AES, trong đó các phép biến đổi mới là We also present the algorithms for the RandomSubBytes, RandomShiftRows, random generation of the dynamic RandomMixColumns và transformations cited above from RandomAffineTransfKey. pseudorandom sequences generated through Keywords—Block cipher; AES; Dynamic transformations. the key schedule of AES or any other pseudorandom number generator, and we Từ khóa—Mã khối; AES; Phép biến đổi động.