Illegal File Sharing & the Film Industry
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

The New England College of Optometry Peer to Peer (P2P) Policy
The New England College of Optometry Peer To Peer (P2P) Policy Created in Compliance with the Higher Education Opportunity Act (HEOA) Peer-to-Peer File Sharing Requirements Overview: Peer-to-peer (P2P) file sharing applications are used to connect a computer directly to other computers in order to transfer files between the systems. Sometimes these applications are used to transfer copyrighted materials such as music and movies. Examples of P2P applications are BitTorrent, Gnutella, eMule, Ares Galaxy, Megaupload, Azureus, PPStream, Pando, Ares, Fileguri, Kugoo. Of these applications, BitTorrent has value in the scientific community. For purposes of this policy, The New England College of Optometry (College) refers to the College and its affiliate New England Eye Institute, Inc. Compliance: In order to comply with both the intent of the College’s Copyright Policy, the Digital Millennium Copyright Act (DMCA) and with the Higher Education Opportunity Act’s (HEOA) file sharing requirements, all P2P file sharing applications are to be blocked at the firewall to prevent illegal downloading as well as to preserve the network bandwidth so that the College internet access is neither compromised nor diminished. Starting in September 2010, the College IT Department will block all well-known P2P ports on the firewall at the application level. If your work requires the use of BitTorrent or another program, an exception may be made as outlined below. The College will audit network usage/activity reports to determine if there is unauthorized P2P activity; the IT Department does random spot checks for new P2P programs every 72 hours and immediately blocks new and emerging P2P networks at the firewall. -

IBM Cloud Unit 2016 IBM Cloud Unit Leadership Organization
IBM Cloud Technical Academy IBM Cloud Unit 2016 IBM Cloud Unit Leadership Organization SVP IBM Cloud Robert LeBlanc GM Cloud Platform GM Cloud GM Cloud Managed GM Cloud GM Cloud Object Integration Services Video Storage Offering Bill Karpovich Mike Valente Braxton Jarratt Line Execs Line Execs Marie Wieck John Morris GM Strategy, GM Client Technical VP Development VP Service Delivery Business Dev Engagement Don Rippert Steve Robinson Harish Grama Janice Fischer J. Comfort (GM & CTO) J. Considine (Innovation Lab) Function Function Leadership Leadership VP Marketing GM WW Sales & VP Finance VP Human Quincy Allen Channels Resources Steve Cowley Steve Lasher Sam Ladah S. Carter (GM EcoD) GM Design VP Enterprise Mobile GM Digital Phil Gilbert Phil Buckellew Kevin Eagan Missions Missions Enterprise IBM Confidential IBM Hybrid Cloud Guiding Principles Choice with! Hybrid ! DevOps! Cognitive Powerful, Consistency! Integration! Productivity! Solutions! Accessible Data and Analytics! The right Unlock existing Automation, tooling Applications and Connect and extract workload in the IT investments and composable systems that insight from all types right place and Intellectual services to increase have the ability to of data Property speed learn Three entry points 1. Create! 2. Connect! 3. Optimize! new cloud apps! existing apps and data! any app! 2016 IBM Cloud Offerings aligned to the Enterprise’s hybrid cloud needs IBM Cloud Platform IBM Cloud Integration IBM Cloud Managed Offerings Offerings Services Offerings Mission: Build true cloud platform -
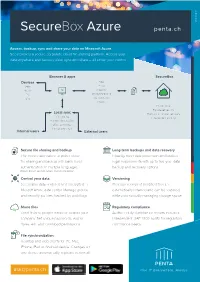
Securebox Azure
General Electronics E-Commerce General Web General General General Electronics General Location Electronics E-Commerce Electronics Electronics Arrows General Web Electronics E-Commerce E-Commerce E-Commerce Web Location GeneraE-Col mmerce Weather Web Arrows WeWeb b Electronics Location Weather Miscellaneous Location Arrows Location Location Arrows Arrows Miscellaneous Electronics E-Commerce Arrows Weather Weather Weather Miscellaneous Web 28/03/2019 Weather SecureBox Azure penta.ch General Miscellaneous Access, backup, sync and share your data on Microsoft Azure SecureBox is a secure corporate cloud file sharing platform. Access your data anywhere and backup, view, sync and share – all under your control. Miscellaneous E-Commerce Browser & apps General SecureBox Devices Files Tablet Email Mobile Calendar PC Word processing Mac Spreadsheets Miscellaneous Photos Private cloud Bank-level security Local sync Backups & disaster recovery File sharing Independent auditing Password protection Editing permissions Link expiry dates Internal users External users SecureLo filecati sharingon and backup Long-term backups and data recovery The secure alternative to public cloud Instantly meet data protection and backup file sharing and backup with bank-level legal requirements with up to five-year data authentication. In multiple languages. backup and recovery options. English, French, German, Italian, Spanish and Arabic Web Control your data Versioning SecureBox data is stored and encrypted in Previous version of modified files are Microsft Azure data center. Manage groups automatically retained and can be restored, and security policies, backed by audit logs. while automatically managing storage space. Share files Regulatory compliance Send Arrolinks to wspeople inside or outside your Auditor-ready compliance reports included. company. Set unique passwords, expiry IndependentElec ISAEtr onic3402 auditss for regulatory dates, edit and download permissions. -

Mimioclassroom User Guide for Windows
MimioClassroom User Guide For Windows mimio.com © 2012 Sanford, L.P. All rights reserved. Revised 12/4/2012. No part of this document or the software may be reproduced or transmitted in any form or by any means or translated into another language without the prior written consent of Sanford, L.P. Mimio, MimioClassroom, MimioTeach, MimioCapture, MimioVote, MimioView, MimioHub, MimioPad, and MimioStudio are registered marks in the United States and other countries. All other trademarks are the property of their respective holders. Contents About MimioClassroom 1 MimioStudio 1 MimioTeach 1 Mimio Interactive 1 MimioCapture 2 Mimio Capture Kit 2 MimioVote 2 MimioView 2 MimioPad 2 Minimum System Requirements 2 Using this Guide 3 MimioStudio 7 About MimioStudio 7 About MimioStudio Notebook 7 About MimioStudio Tools 7 About MimioStudio Gallery 9 Getting Started with MimioStudio 9 Accessing MimioStudio Notebook 9 Accessing MimioStudio Tools 10 Accessing MimioStudio Gallery 10 Using MimioStudio Notebook 10 Working with Pages 11 Creating an Activity 14 Creating an Activity - Step 1: Define 14 Creating an Activity - Step 2: Select 14 Creating an Activity - Step 3: Refine 15 Creating an Activity - Step 4: Review 16 Working with an Activity 17 Writing an Objective 17 Attaching Files 18 Using MimioStudio Tools 18 Creating Objects 18 Manipulating Objects 21 Adding Actions to Objects 25 Using MimioStudio Gallery 26 iii Importing Gallery Items into a Notebook 27 Customizing the Content of the Gallery 27 Exporting a Gallery Folder to a Gallery File 29 Working -

Étude De La Pratique Du Téléchargement Légal Et Illégal Sur Internet
Étude de la pratique du téléchargement légal et illégal sur Internet Travail de Bachelor réalisé en vue de l’obtention du Bachelor HES par : Julien MARIETHOZ Conseiller au travail de Bachelor : (David Billard, Professeur HES) Genève, le 12 mai 2010 Haute École de Gestion de Genève (HEG-GE) Informatique de Gestion Déclaration Ce travail de Bachelor est réalisé dans le cadre de l’examen final de la Haute école de gestion de Genève, en vue de l’obtention du titre d’ « informaticien de gestion ». L’étudiant accepte, le cas échéant, la clause de confidentialité. L'utilisation des conclusions et recommandations formulées dans le travail de Bachelor, sans préjuger de leur valeur, n'engage ni la responsabilité de l'auteur, ni celle du conseiller au travail de Bachelor, du juré et de la HEG. « J’atteste avoir réalisé seul le présent travail, sans avoir utilisé des sources autres que celles citées dans la bibliographie. » Fait à Genève, le 12 mai 2010 Julien MARIETHOZ Étude de la pratique du téléchargement légal et illégal sur Internet MARIETHOZ, Julien iv Remerciements Dans le cadre de la réalisation de ce travail, je tiens à remercier tous ceux qui ont pu y contribuer directement ou indirectement : M. David Billard pour son encadrement et ses conseils. Carole, ma femme, qui a pris le temps de s’occuper de notre petit qui est né le jour après la date de début officiel, me permettant de me concentrer sur ce travail. Tous ceux qui ont pris le temps de répondre à mon questionnaire, en me fournissant les données nécessaires à ce rapport. -

Wandisco Fusion® Microsoft Azure Data Box
WANDISCO FUSION® MICROSOFT AZURE DATA BOX Use WANdisco Fusion with Data Box for bulk transfer of changing data WANdisco Fusion is the only solution that enables Microsoft customers to use the bulk transfer capabilities of the Azure Data Box to transfer static and changing Guaranteed data consistency information from Big Data applications to Azure Cloud with guaranteed data consistency. Users can continue to Take advantage of the storage on Azure Data Box for write to their local cluster while the Azure Data Box is in bulk data transfer while continuing to write to a local transit so when the Azure Data Box is subsequently being cluster and replicate those changes while the Azure uploaded, any changes are replicated to the Azure Cloud Data Box is uploaded to the Azure Cloud. with guaranteed consistency. Easy and intuitive step-by-step operation • Applications write to Azure Data Box using the same API that they use to interact with the Azure Cloud. No downtime and • WANdisco Fusion for Azure Data Box requires no change to applications which can continue to use the no business disruption API as they would normally. Write data to a local HDFS-compatible endpoint • Replication is continuous and recovers from on-premises and replicate to a storage location in intermittent network or system failures automatically. Microsoft Azure with no modification or disruption to applications on-premises. AZURE 2 STORAGE Cost saving MICROSOFT 1 3 AZURE DATA BOX Avoid the high network costs common to large scale data transfers and benefit from a range of FUSION applications available in Azure Cloud. -

Free Ares 3.0
Free ares 3.0 Ares, free and safe download. Ares latest version: Fast and unlimited P2P file sharing. Ares is a great P2P client Developer. Aresgalaxy | More Programs (3). Ares free download. Licence Free OS Support Windows XP, Windows Vista, Horizon Innovative Xbox modding tool. Ares Gold free download. Get new version of Ares Gold. A free file-sharing program ✓ Free ✓ Updated ✓ Download now. Ares is a P2P file exchange program that, with the passing of time, has established itself as one of the best Ares screenshot 3 Free v MB. Ares. Ares is a free open source file sharing program that enables users to share any digital file including images, audio, video, software, documents. Ares is a free open source file sharing program that enables users to share any digital file including images, audio, video, software, documents, etc. You may. Download Ares Galaxy for Windows. Ares Galaxy is an open source Peer to Peer software which lets you share images, documents, software, audio and video. Download Ares Galaxy for free. A free peer-to-peer (P2P) BitTorrent file sharing client. Ares Galaxy is a free, open source BitTorrent and chat. Ares is a peer to peer file sharing program that enables users to share 0; 3 star. 0; 2 star. 1; 1 star. 0. All Versions. out of 58 votes. 5 star. Download Ares Ares. August, 23rd - % Safe - Open Source. Free Download. ( MB) Safe & Secure Ares Date released: 07 Oct Download Ares Plus Program for the titular P2P network that gives you faster downloads. AresGalaxy is a free open source Filesharing Bittorrent p2p Client with a powerful search, works behind firewalls. -

Simulacijski Alati I Njihova Ograničenja Pri Analizi I Unapređenju Rada Mreža Istovrsnih Entiteta
SVEUČILIŠTE U ZAGREBU FAKULTET ORGANIZACIJE I INFORMATIKE VARAŽDIN Tedo Vrbanec SIMULACIJSKI ALATI I NJIHOVA OGRANIČENJA PRI ANALIZI I UNAPREĐENJU RADA MREŽA ISTOVRSNIH ENTITETA MAGISTARSKI RAD Varaždin, 2010. PODACI O MAGISTARSKOM RADU I. AUTOR Ime i prezime Tedo Vrbanec Datum i mjesto rođenja 7. travanj 1969., Čakovec Naziv fakulteta i datum diplomiranja Fakultet organizacije i informatike, 10. listopad 2001. Sadašnje zaposlenje Učiteljski fakultet Zagreb – Odsjek u Čakovcu II. MAGISTARSKI RAD Simulacijski alati i njihova ograničenja pri analizi i Naslov unapređenju rada mreža istovrsnih entiteta Broj stranica, slika, tablica, priloga, XIV + 181 + XXXVIII stranica, 53 slike, 18 tablica, 3 bibliografskih podataka priloga, 288 bibliografskih podataka Znanstveno područje, smjer i disciplina iz koje Područje: Informacijske znanosti je postignut akademski stupanj Smjer: Informacijski sustavi Mentor Prof. dr. sc. Željko Hutinski Sumentor Prof. dr. sc. Vesna Dušak Fakultet na kojem je rad obranjen Fakultet organizacije i informatike Varaždin Oznaka i redni broj rada III. OCJENA I OBRANA Datum prihvaćanja teme od Znanstveno- 17. lipanj 2008. nastavnog vijeća Datum predaje rada 9. travanj 2010. Datum sjednice ZNV-a na kojoj je prihvaćena 18. svibanj 2010. pozitivna ocjena rada Prof. dr. sc. Neven Vrček, predsjednik Sastav Povjerenstva koje je rad ocijenilo Prof. dr. sc. Željko Hutinski, mentor Prof. dr. sc. Vesna Dušak, sumentor Datum obrane rada 1. lipanj 2010. Prof. dr. sc. Neven Vrček, predsjednik Sastav Povjerenstva pred kojim je rad obranjen Prof. dr. sc. Željko Hutinski, mentor Prof. dr. sc. Vesna Dušak, sumentor Datum promocije SVEUČILIŠTE U ZAGREBU FAKULTET ORGANIZACIJE I INFORMATIKE VARAŽDIN POSLIJEDIPLOMSKI ZNANSTVENI STUDIJ INFORMACIJSKIH ZNANOSTI SMJER STUDIJA: INFORMACIJSKI SUSTAVI Tedo Vrbanec Broj indeksa: P-802/2001 SIMULACIJSKI ALATI I NJIHOVA OGRANIČENJA PRI ANALIZI I UNAPREĐENJU RADA MREŽA ISTOVRSNIH ENTITETA MAGISTARSKI RAD Mentor: Prof. -

Lock-Free Collaboration Support for Cloud Storage Services With
Lock-Free Collaboration Support for Cloud Storage Services with Operation Inference and Transformation Jian Chen, Minghao Zhao, and Zhenhua Li, Tsinghua University; Ennan Zhai, Alibaba Group Inc.; Feng Qian, University of Minnesota - Twin Cities; Hongyi Chen, Tsinghua University; Yunhao Liu, Michigan State University & Tsinghua University; Tianyin Xu, University of Illinois Urbana-Champaign https://www.usenix.org/conference/fast20/presentation/chen This paper is included in the Proceedings of the 18th USENIX Conference on File and Storage Technologies (FAST ’20) February 25–27, 2020 • Santa Clara, CA, USA 978-1-939133-12-0 Open access to the Proceedings of the 18th USENIX Conference on File and Storage Technologies (FAST ’20) is sponsored by Lock-Free Collaboration Support for Cloud Storage Services with Operation Inference and Transformation ⇤ 1 1 1 2 Jian Chen ⇤, Minghao Zhao ⇤, Zhenhua Li , Ennan Zhai Feng Qian3, Hongyi Chen1, Yunhao Liu1,4, Tianyin Xu5 1Tsinghua University, 2Alibaba Group, 3University of Minnesota, 4Michigan State University, 5UIUC Abstract Pattern 1: Losing updates Alice is editing a file. Suddenly, her file is overwritten All studied This paper studies how today’s cloud storage services support by a new version from her collaborator, Bob. Sometimes, cloud storage collaborative file editing. As a tradeoff for transparency/user- Alice can even lose her edits on the older version. services friendliness, they do not ask collaborators to use version con- Pattern 2: Conflicts despite coordination trol systems but instead implement their own heuristics for Alice coordinates her edits with Bob through emails to All studied handling conflicts, which however often lead to unexpected avoid conflicts by enforcing a sequential order. -

Forescout Counteract® Endpoint Support Compatibility Matrix Updated: October 2018
ForeScout CounterACT® Endpoint Support Compatibility Matrix Updated: October 2018 ForeScout CounterACT Endpoint Support Compatibility Matrix 2 Table of Contents About Endpoint Support Compatibility ......................................................... 3 Operating Systems ....................................................................................... 3 Microsoft Windows (32 & 64 BIT Versions) ...................................................... 3 MAC OS X / MACOS ...................................................................................... 5 Linux .......................................................................................................... 6 Web Browsers .............................................................................................. 8 Microsoft Windows Applications ...................................................................... 9 Antivirus ................................................................................................. 9 Peer-to-Peer .......................................................................................... 25 Instant Messaging .................................................................................. 31 Anti-Spyware ......................................................................................... 34 Personal Firewall .................................................................................... 36 Hard Drive Encryption ............................................................................. 38 Cloud Sync ........................................................................................... -
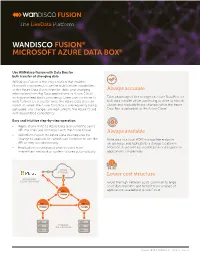
Wandisco Fusion® Microsoft Azure Data Box®
FUSION WANDISCO FUSION® MICROSOFT AZURE DATA BOX® Use WANdisco Fusion with Data Box for bulk transfer of changing data WANdisco Fusion is the only solution that enables Microsoft customers to use the bulk transfer capabilities of the Azure Data Box to transfer static and changing Always accurate information from Big Data applications to Azure Cloud with guaranteed data consistency. Users can continue to Take advantage of the storage on Azure Data Box for write to their local cluster while the Azure Data Box is in bulk data transfer while continuing to write to a local transit so when the Azure Data Box is subsequently being cluster and replicate those changes while the Azure uploaded, any changes are replicated to the Azure Cloud Data Box is uploaded to the Azure Cloud. with guaranteed consistency. Easy and intuitive step-by-step operation • Applications write to Azure Data Box using the same API that they use to interact with the Azure Cloud. Always available • WANdisco Fusion for Azure Data Box requires no change to applications which can continue to use the Write data to a local HDFS-compatible endpoint API as they would normally. on-premises and replicate to a storage location in • Replication is continuous and recovers from Microsoft Azure with no modification or disruption to intermittent network or system failures automatically. applications on-premises. AZURE 2 STORAGE Lower cost structure MICROSOFT 1 3 AZURE DATA BOX Avoid the high network costs common to large scale data transfers and benefit from a range of applications available in Azure Cloud. FUSION FUSION FUSION HADOOP ON-PREMISES Copyright © 2018 WANdisco, Inc. -

Diapositiva 1
TRANSFERENCIA O DISTRIBUCIÓN DE ARCHIVOS ENTRE IGUALES (peer-to-peer) Características, Protocolos, Software, Luis Villalta Márquez Configuración Peer-to-peer Una red peer-to-peer, red de pares, red entre iguales, red entre pares o red punto a punto (P2P, por sus siglas en inglés) es una red de computadoras en la que todos o algunos aspectos funcionan sin clientes ni servidores fijos, sino una serie de nodos que se comportan como iguales entre sí. Es decir, actúan simultáneamente como clientes y servidores respecto a los demás nodos de la red. Las redes P2P permiten el intercambio directo de información, en cualquier formato, entre los ordenadores interconectados. Peer-to-peer Normalmente este tipo de redes se implementan como redes superpuestas construidas en la capa de aplicación de redes públicas como Internet. El hecho de que sirvan para compartir e intercambiar información de forma directa entre dos o más usuarios ha propiciado que parte de los usuarios lo utilicen para intercambiar archivos cuyo contenido está sujeto a las leyes de copyright, lo que ha generado una gran polémica entre defensores y detractores de estos sistemas. Las redes peer-to-peer aprovechan, administran y optimizan el uso del ancho de banda de los demás usuarios de la red por medio de la conectividad entre los mismos, y obtienen así más rendimiento en las conexiones y transferencias que con algunos métodos centralizados convencionales, donde una cantidad relativamente pequeña de servidores provee el total del ancho de banda y recursos compartidos para un servicio o aplicación. Peer-to-peer Dichas redes son útiles para diversos propósitos.