Salesforce Shield
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IBM Cloud Unit 2016 IBM Cloud Unit Leadership Organization
IBM Cloud Technical Academy IBM Cloud Unit 2016 IBM Cloud Unit Leadership Organization SVP IBM Cloud Robert LeBlanc GM Cloud Platform GM Cloud GM Cloud Managed GM Cloud GM Cloud Object Integration Services Video Storage Offering Bill Karpovich Mike Valente Braxton Jarratt Line Execs Line Execs Marie Wieck John Morris GM Strategy, GM Client Technical VP Development VP Service Delivery Business Dev Engagement Don Rippert Steve Robinson Harish Grama Janice Fischer J. Comfort (GM & CTO) J. Considine (Innovation Lab) Function Function Leadership Leadership VP Marketing GM WW Sales & VP Finance VP Human Quincy Allen Channels Resources Steve Cowley Steve Lasher Sam Ladah S. Carter (GM EcoD) GM Design VP Enterprise Mobile GM Digital Phil Gilbert Phil Buckellew Kevin Eagan Missions Missions Enterprise IBM Confidential IBM Hybrid Cloud Guiding Principles Choice with! Hybrid ! DevOps! Cognitive Powerful, Consistency! Integration! Productivity! Solutions! Accessible Data and Analytics! The right Unlock existing Automation, tooling Applications and Connect and extract workload in the IT investments and composable systems that insight from all types right place and Intellectual services to increase have the ability to of data Property speed learn Three entry points 1. Create! 2. Connect! 3. Optimize! new cloud apps! existing apps and data! any app! 2016 IBM Cloud Offerings aligned to the Enterprise’s hybrid cloud needs IBM Cloud Platform IBM Cloud Integration IBM Cloud Managed Offerings Offerings Services Offerings Mission: Build true cloud platform -
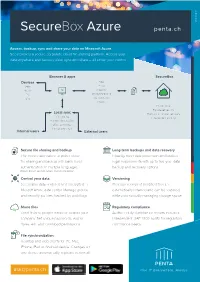
Securebox Azure
General Electronics E-Commerce General Web General General General Electronics General Location Electronics E-Commerce Electronics Electronics Arrows General Web Electronics E-Commerce E-Commerce E-Commerce Web Location GeneraE-Col mmerce Weather Web Arrows WeWeb b Electronics Location Weather Miscellaneous Location Arrows Location Location Arrows Arrows Miscellaneous Electronics E-Commerce Arrows Weather Weather Weather Miscellaneous Web 28/03/2019 Weather SecureBox Azure penta.ch General Miscellaneous Access, backup, sync and share your data on Microsoft Azure SecureBox is a secure corporate cloud file sharing platform. Access your data anywhere and backup, view, sync and share – all under your control. Miscellaneous E-Commerce Browser & apps General SecureBox Devices Files Tablet Email Mobile Calendar PC Word processing Mac Spreadsheets Miscellaneous Photos Private cloud Bank-level security Local sync Backups & disaster recovery File sharing Independent auditing Password protection Editing permissions Link expiry dates Internal users External users SecureLo filecati sharingon and backup Long-term backups and data recovery The secure alternative to public cloud Instantly meet data protection and backup file sharing and backup with bank-level legal requirements with up to five-year data authentication. In multiple languages. backup and recovery options. English, French, German, Italian, Spanish and Arabic Web Control your data Versioning SecureBox data is stored and encrypted in Previous version of modified files are Microsft Azure data center. Manage groups automatically retained and can be restored, and security policies, backed by audit logs. while automatically managing storage space. Share files Regulatory compliance Send Arrolinks to wspeople inside or outside your Auditor-ready compliance reports included. company. Set unique passwords, expiry IndependentElec ISAEtr onic3402 auditss for regulatory dates, edit and download permissions. -

Google Is a Strong Performer in Enterprise Public Cloud Platforms Excerpted from the Forrester Wave™: Enterprise Public Cloud Platforms, Q4 2014 by John R
FOR CIOS DECEMBER 29, 2014 Google Is A Strong Performer In Enterprise Public Cloud Platforms Excerpted From The Forrester Wave™: Enterprise Public Cloud Platforms, Q4 2014 by John R. Rymer and James Staten with Peter Burris, Christopher Mines, and Dominique Whittaker GOOGLE, NOW A FULL-SERVICE PLATFORM, IS RUNNING TO CATCH THE LEADERS Since our last analysis, Google has made significant improvements to its cloud platform — adding an IaaS service, innovated with new big data solutions (based on its homegrown dremel architecture), and added partners. Google is popular among web developers — we estimate that it has between 10,000 and 99,000 customers. But Google Cloud Platform lacks several key certifications, monitoring and security controls, and application services important to CIOs and provided by AWS and Microsoft.1 Google has also been slow to position its cloud platform as the home for applications that want to leverage the broad set of Google services such as Android, AdSense, Search, Maps, and so many other technologies. Look for that to be a key focus in 2015, and for a faster cadence of new features. Forrester Wave™: Enterprise Public Cloud Forrester Wave™: Enterprise Public Cloud Platforms For CIOs, Q4 ‘14 Platforms For Rapid Developers, Q4 ‘14 Risky Strong Risky Strong Bets Contenders Performers Leaders Bets Contenders Performers Leaders Strong Strong Amazon Web Services MIOsoft Microsoft Salesforce Cordys* Mendix MIOsoft Salesforce (Q2 2013) OutSystems OutSystems Google Mendix Acquia Current Rackspace* IBM Current offering (Q2 2013) offering Cordys* (Q2 2013) Engine Yard Acquia CenturyLink Google, with a Forrester score of 2.35, is a Strong Performer in this Dimension Data GoGrid Forrester Wave. -

Mimioclassroom User Guide for Windows
MimioClassroom User Guide For Windows mimio.com © 2012 Sanford, L.P. All rights reserved. Revised 12/4/2012. No part of this document or the software may be reproduced or transmitted in any form or by any means or translated into another language without the prior written consent of Sanford, L.P. Mimio, MimioClassroom, MimioTeach, MimioCapture, MimioVote, MimioView, MimioHub, MimioPad, and MimioStudio are registered marks in the United States and other countries. All other trademarks are the property of their respective holders. Contents About MimioClassroom 1 MimioStudio 1 MimioTeach 1 Mimio Interactive 1 MimioCapture 2 Mimio Capture Kit 2 MimioVote 2 MimioView 2 MimioPad 2 Minimum System Requirements 2 Using this Guide 3 MimioStudio 7 About MimioStudio 7 About MimioStudio Notebook 7 About MimioStudio Tools 7 About MimioStudio Gallery 9 Getting Started with MimioStudio 9 Accessing MimioStudio Notebook 9 Accessing MimioStudio Tools 10 Accessing MimioStudio Gallery 10 Using MimioStudio Notebook 10 Working with Pages 11 Creating an Activity 14 Creating an Activity - Step 1: Define 14 Creating an Activity - Step 2: Select 14 Creating an Activity - Step 3: Refine 15 Creating an Activity - Step 4: Review 16 Working with an Activity 17 Writing an Objective 17 Attaching Files 18 Using MimioStudio Tools 18 Creating Objects 18 Manipulating Objects 21 Adding Actions to Objects 25 Using MimioStudio Gallery 26 iii Importing Gallery Items into a Notebook 27 Customizing the Content of the Gallery 27 Exporting a Gallery Folder to a Gallery File 29 Working -

Wandisco Fusion® Microsoft Azure Data Box
WANDISCO FUSION® MICROSOFT AZURE DATA BOX Use WANdisco Fusion with Data Box for bulk transfer of changing data WANdisco Fusion is the only solution that enables Microsoft customers to use the bulk transfer capabilities of the Azure Data Box to transfer static and changing Guaranteed data consistency information from Big Data applications to Azure Cloud with guaranteed data consistency. Users can continue to Take advantage of the storage on Azure Data Box for write to their local cluster while the Azure Data Box is in bulk data transfer while continuing to write to a local transit so when the Azure Data Box is subsequently being cluster and replicate those changes while the Azure uploaded, any changes are replicated to the Azure Cloud Data Box is uploaded to the Azure Cloud. with guaranteed consistency. Easy and intuitive step-by-step operation • Applications write to Azure Data Box using the same API that they use to interact with the Azure Cloud. No downtime and • WANdisco Fusion for Azure Data Box requires no change to applications which can continue to use the no business disruption API as they would normally. Write data to a local HDFS-compatible endpoint • Replication is continuous and recovers from on-premises and replicate to a storage location in intermittent network or system failures automatically. Microsoft Azure with no modification or disruption to applications on-premises. AZURE 2 STORAGE Cost saving MICROSOFT 1 3 AZURE DATA BOX Avoid the high network costs common to large scale data transfers and benefit from a range of FUSION applications available in Azure Cloud. -

Launch Innovative Products Faster with Red Hat and Alibaba Cloud
LAUNCH INNOVATIVE PRODUCTS FASTER WITH RED HAT AND ALIBABA CLOUD PARTNER BRIEF FAST INNOVATION AND AGILE DEPLOYMENT ARE CRITICAL FOR SUCCESS Worldwide, organizations face increasing competition as digital technologies continue to disrupt industries. To remain successful, they must differentiate themselves with compelling products while also controlling costs. However, if it takes too long to develop and launch new products, the business is likely to miss market opportunities and become less competitive. By 2020, In addition, many companies are adopting multicloud strategies to reduce risk. Yet choosing the 83% right set of cloud providers and services from the large number available — and then connecting of enterprise workloads will them into existing on-premise and cloud-based infrastructure — can be overwhelming. run on cloud infrastructure, Red Hat and Alibaba Cloud deliver the modern cloud foundation and innovative application develop- with 41% running on public ment technologies you need to quickly create high-value products, monitor and manage expenses, 1 cloud infrastructure. and mitigate technological risk. Red Hat and Alibaba Cloud BUILD A FLEXIBLE APPLICATION ENVIRONMENT provide a modern cloud foun- Red Hat and Alibaba Cloud combine production-grade open source software, global cloud infra- dation and innovative applica- structure, and advanced machine learning and big data capabilities into a high-performance, adapt- tion development technologies able platform for application development and deployment. A leading public cloud service provider, to help you build and launch Alibaba Cloud operates 18 datacenters globally. These datacenters are connected by fast networks compelling products quickly to provide a unified experience — no matter where you are or which datacenter you connect to. -

Lock-Free Collaboration Support for Cloud Storage Services With
Lock-Free Collaboration Support for Cloud Storage Services with Operation Inference and Transformation Jian Chen, Minghao Zhao, and Zhenhua Li, Tsinghua University; Ennan Zhai, Alibaba Group Inc.; Feng Qian, University of Minnesota - Twin Cities; Hongyi Chen, Tsinghua University; Yunhao Liu, Michigan State University & Tsinghua University; Tianyin Xu, University of Illinois Urbana-Champaign https://www.usenix.org/conference/fast20/presentation/chen This paper is included in the Proceedings of the 18th USENIX Conference on File and Storage Technologies (FAST ’20) February 25–27, 2020 • Santa Clara, CA, USA 978-1-939133-12-0 Open access to the Proceedings of the 18th USENIX Conference on File and Storage Technologies (FAST ’20) is sponsored by Lock-Free Collaboration Support for Cloud Storage Services with Operation Inference and Transformation ⇤ 1 1 1 2 Jian Chen ⇤, Minghao Zhao ⇤, Zhenhua Li , Ennan Zhai Feng Qian3, Hongyi Chen1, Yunhao Liu1,4, Tianyin Xu5 1Tsinghua University, 2Alibaba Group, 3University of Minnesota, 4Michigan State University, 5UIUC Abstract Pattern 1: Losing updates Alice is editing a file. Suddenly, her file is overwritten All studied This paper studies how today’s cloud storage services support by a new version from her collaborator, Bob. Sometimes, cloud storage collaborative file editing. As a tradeoff for transparency/user- Alice can even lose her edits on the older version. services friendliness, they do not ask collaborators to use version con- Pattern 2: Conflicts despite coordination trol systems but instead implement their own heuristics for Alice coordinates her edits with Bob through emails to All studied handling conflicts, which however often lead to unexpected avoid conflicts by enforcing a sequential order. -
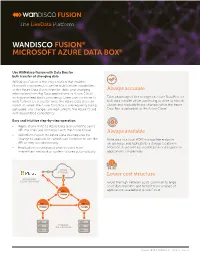
Wandisco Fusion® Microsoft Azure Data Box®
FUSION WANDISCO FUSION® MICROSOFT AZURE DATA BOX® Use WANdisco Fusion with Data Box for bulk transfer of changing data WANdisco Fusion is the only solution that enables Microsoft customers to use the bulk transfer capabilities of the Azure Data Box to transfer static and changing Always accurate information from Big Data applications to Azure Cloud with guaranteed data consistency. Users can continue to Take advantage of the storage on Azure Data Box for write to their local cluster while the Azure Data Box is in bulk data transfer while continuing to write to a local transit so when the Azure Data Box is subsequently being cluster and replicate those changes while the Azure uploaded, any changes are replicated to the Azure Cloud Data Box is uploaded to the Azure Cloud. with guaranteed consistency. Easy and intuitive step-by-step operation • Applications write to Azure Data Box using the same API that they use to interact with the Azure Cloud. Always available • WANdisco Fusion for Azure Data Box requires no change to applications which can continue to use the Write data to a local HDFS-compatible endpoint API as they would normally. on-premises and replicate to a storage location in • Replication is continuous and recovers from Microsoft Azure with no modification or disruption to intermittent network or system failures automatically. applications on-premises. AZURE 2 STORAGE Lower cost structure MICROSOFT 1 3 AZURE DATA BOX Avoid the high network costs common to large scale data transfers and benefit from a range of applications available in Azure Cloud. FUSION FUSION FUSION HADOOP ON-PREMISES Copyright © 2018 WANdisco, Inc. -

Igneous Backup with Microsoft Azure Data Box Executive Overview the Benefits of Cloud Backup, Including Scalability, Accessibility, and Agility, Are Immense
SOLUTION GUIDE Igneous Backup with Microsoft Azure Data Box Executive Overview The benefits of cloud backup, including scalability, accessibility, and agility, are immense. However, significant challenges lie in effectively deploying cloud backups for enterprise. To help enterprises harness the value of cloud backup while overcoming the challenges of massive scale, Igneous Unstructured Data Management as-a-Service and Microsoft Azure Data Box combine to offer an integrated solution that accelerates data migration from network attached storage (NAS) to Microsoft Azure Storage, and manages ongoing replication and tiering to cloud. With backup environments, the challenge of using public cloud is often seeding the initial backup before doing incrementals. Azure Data Box provides an economical way to transport those initial backups (often called “level- 0’s”) into Azure Storage without worrying about network bandwidth between your on-premises environment and Azure Storage. Igneous Unstructured Data Management as-a-Service solution, built for managing file-based backups, provides native integration with Azure Storage, including the Azure Data Box. Together, Igneous and Azure allow you to backup unstructured data stored on your primary network attached storage (NAS) file systems, efficiently move large amounts of data to Azure Storage, and protect and manage your data with tiering and replication to cloud. Microsoft Azure Data Box provides a secure, tamper-resistant method for quick and simple transfer of your data to Azure. Use Azure Data Box service when you want to transfer large amounts of data to Azure but are limited by time, network availability, or costs. Azure Data Box is supported by Igneous as a method to support transfers or initial sync to Azure Storage. -

Opentext Extended ECM for Salesforce Solution Overview
Solution overview OpenText Extended ECM for Salesforce brings content management to your CRM processes Improve customer insight and streamline sales Simplify the Every organization seeks to increase agility and productivity by information extracting the maximum value from its processes and content. management landscape by However, knowledge workers in marketing, sales and services unifying CRM are only as good as the information they can efficiently access. ™ ® and ERP with ECM OpenText Extended ECM for Salesforce bridges the silos created Avoid by disparate applications in marketing, sales and services to pull miscommunication structured and unstructured information together seamlessly and and improve customer present the complete picture to users who need it. experience Bringing CRM and ECM together rapidly and seamlessly Accelerate sales One of the most pressing challenges of Salesforce customers is to connect their CRM cycles by sharing and application to other systems and improve adoption. Integrating content management and reusing best practice adding value to CRM applications is a top priority for many Salesforce users. materials With Extended ECM for Salesforce, OpenText is delivering on this demand. Extended ECM for Salesforce connects Salesforce cloud services to the Extended ECM Platform and surfaces Reduce risk and enterprise content management capabilities and content inside the Salesforce user interface. deploy flexibly The solution builds upon the OpenText Extended ECM 20.2 platform, developed in a cloud-native architecture that allows cusomers the choice of where to deploy from on- premises to hyperscaler platforms. The new architecture allows customers to deploy and upgrade faster, allowing end users faster access to new features. The core capabilites of the Extended ECM platform include document management, records management, 1/3 capturing, archiving and workflow and collaboration, making them available to Salesforce users. -

The Best Online Communities
THE Welcome to our annual list of top brand communities. THE BEST COMMUNITIES From July 2020 to Sept 2020, FeverBee analysed hundreds BY PLATFORM BEST ONLINE of communities in a variety of sectors to put together our list of top communities. KHOROS SALESFORCE VERINT COMMUNITIES 1 Atlassian Salesforce: Trailblazers Sophos The criteria to compile these rankings is subjective, but based 2 Sephora Kronos Sage City upon several factors. These include quantity of activity, quality 3 Fitbit Big Commerce Dynamics of activity and management, value to members, value to 4 Digital Ocean Activision Macmillan the organisation, design, superuser programs, and more. 5 Spotify MuleSoft Nordic Semiconductor 2020 6 SAS Hive Titleist While this list focuses on traditional, hosted, brand 7 Alteryx Workfront Appian 8 BT Tableau Texas Instruments By Richard Millington, FeverBee communities, we’ve also included cult brands and 9 Google Local Guides Akamai ARM ‘community-only’ brands which primarily exist only 10 eBay Boomi Technologies (Dell) England Supporters as a community. NOTE: INSIDED VANILLA DISCOURSE We recognise this is not a fully representative list. Non-English speaking communities, private communities, and those on platforms which are less common in the Western 1 Sonos Money Saving Expert Glamour.de world are not represented. 2 hLife Acer Nvidia 3 02.de Gardners World Babypips 4 Ziggo Qualtrics Asana 5 T-Mobile Digital Spy GitHub THE BEST COMMUNITIES 6 KPN Tuenti Schizophrenia BY CATEGORY 7 Tele2 King Plex 8 A1Community Startup Nation Zoom 9 Deezer Vertica Swapd OVERALL B2B B2C NON-PROFIT 10 Zapier Big Green Egg Nature Photographers 1 Atlassian Atlassian Sephora Mayo Clinic 2 Salesforce: Trailblazers Salesforce: Trailblazers Fitbit Inspire 3 Sephora Tableau Apple Breast Cancer 4 Fitbit SAP BT TuDiabetes 5 SAP Kronos Spotify Reachout 6 Kronos Digital Ocean Acer Macmillian 7 Digital Ocean Project Management Institute Etsy Schizophrenia.com THE BEST 8 Apple SAS Blizzard Scope.uk 9 Project Management Institute Service Now Steam Sane Australia MISC. -

Reseller Approved Manufacturer(S)
Reseller Approved Manufacturer(s) 1Plus1 Technology EMC 5X Technology Red Hat, SAP 6D Global Adobe Accelera Solutions AppSense, EMC, HP, Imprivata, Liquidware Labs, Nutanix, Precise Biometrics, Red Hat, ServiceNow, Tintri, Vmware Adaptive Cyber RSA Adapture F5 Aderas, Inc. Delphix Advanced Computer Concepts Adobe, Condusiv, Gigamon, Nimble, RSA, SafeNet, Symantec, Veritas Advanced Market Place HP, Symantec Advanced Network Management F5, Splunk, VMware Advantaged Solutions SAP Affigent, LLC (Formerly TKCIS) Adobe, Axway, QTS, Salesforce.com, SAP Agilet Solutions Symantec Agosto Google Aikya Incorporated Salesforce.com AITS (Advanced IT Services, LLC) Symantec Akira Technologies Adobe Alamo City Engineering Services, Inc Adobe, AvePoint, Avue, HP, IBM, Imperva, Oblong, Precise Biometrics, Socrata, Tripwire Alchemy Technology Group AppSense Alexander Open Systems (AOS) F5 Alliance Technology Group Symantec Allied Network Solutions Adobe, SAP Alpha Sum Business Machines Adobe, Symantec, Veritas Alpha Technologies Tintri AlphaSix Corp (Synnex) Adobe, Arista, Nutanix, Splunk, Qlik Alvarez & Associates Adobe Amerinet of Michigan F5 AnaVation, LLC Salesforce.com Angus-Hamer, Inc. Adobe Apollo (Group) Information Systems Arista, FireEye Applied Engineering Management Carahsoft CON-SKUs Corp/Vizuri Aprisa Technology Adobe, EMC, RSA, Symantec, Veritas, Vmware Aquila HP, FireEye ARH, LLC EMC, F5, Symantec Assurance Data Imperva Atrion Nimble ATSolutions Inc Nimble August Schell ALL Aurora Adobe, Jama, Symantec Aurotech Veritas Avid Systems Good Technology/Blackberry, Precise Biometrics, RSA B7 ALL BAI Federal / Blackwood Associates Inc FireEye, Gigamon, Infoblox, Splunk BCS Systems Kofax Bear Bridge Symantec, Veritas Bear Data F5 Bell Techlogix Symantec, Vmware BizTech Fusion Box Black Box Network Services Certipath Blue Door Networks Splunk Blue Tech Adobe, Jama, SafeNet, Symantec Bluesource Inc Symantec Buchanan & Edwards EMC, F5, SAP Cambridge Computer Services Nimble Carolina Advanced Digital Infoblox Cask, LLC.