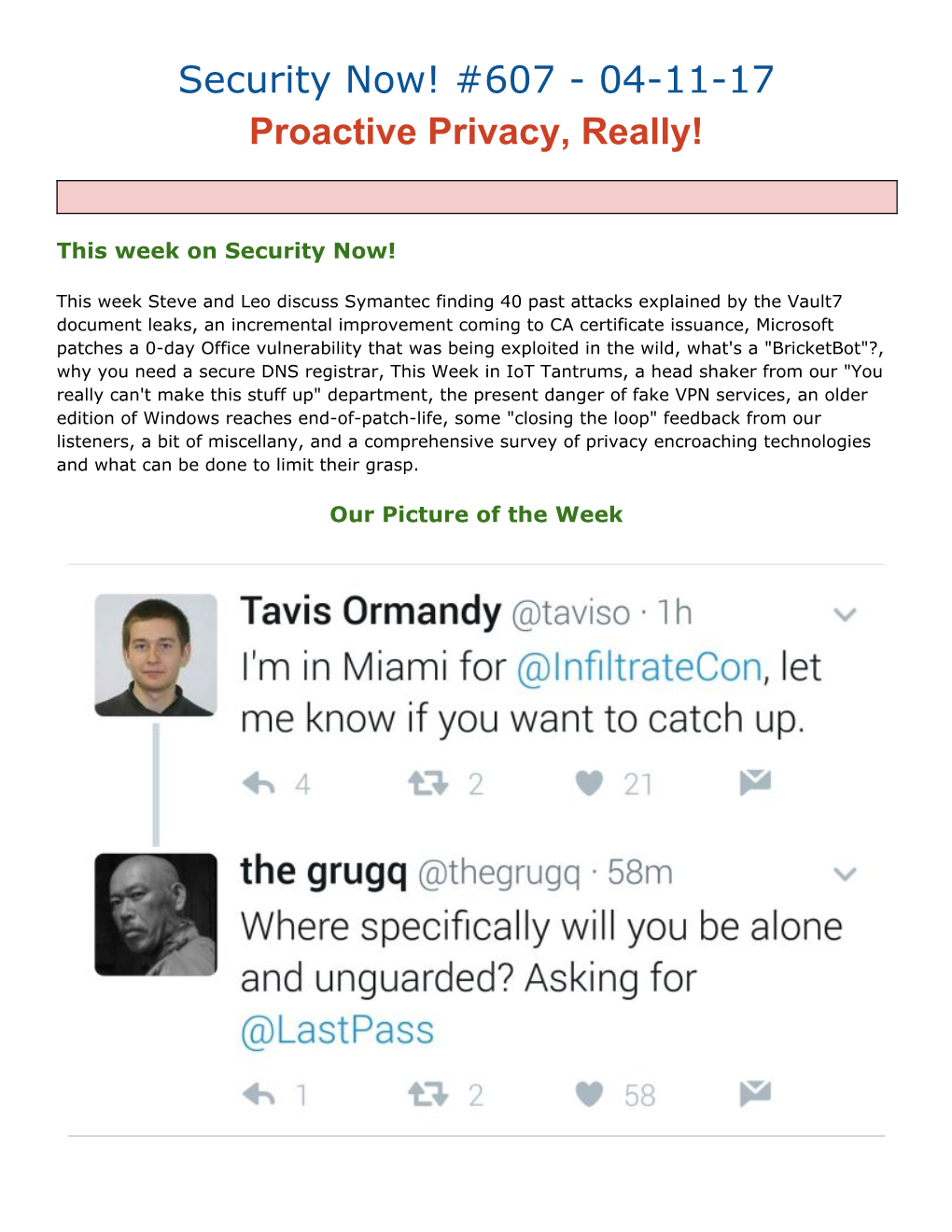
Security Now! #607 - 04-11-17 Proactive Privacy, Really!
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

1423778527171.Pdf
Bahamut - [email protected] Based on the “Touhou Project” series of games by Team Shanghai Alice / ZUN. http://www16.big.or.jp/~zun/ The Touhou Project and its related properties are ©Team Shanghai Alice / ZUN. The Team Shanghai Alice logo is ©Team Shanghai Alice / ZUN. Illustrations © their respective owners. Used without permission. Tale of Phantasmal Land text & gameplay ©2011 Bahamut. This document is provided “as is”. Your possession of this document, either in an altered or unaltered state signifies that you agree to absolve, excuse, or otherwise not hold responsible Team Shanghai Alice / ZUN and/or Bahamut, and/or any other individuals or entities whose works appear herein for any and/or all liabilities, damages, etc. associated with the possession of this document. This document is not associated with, or endorsed by Team Shanghai Alice / ZUN. This is a not-for-profit personal interest work, and is not intended, nor should it be construed, as a challenge to Team Shanghai Alice / ZUN’s ownership of its Touhou Project copyrights and other related properties. License to distribute this work is freely given provided that it remains in an unaltered state and is not used for any commercial purposes whatsoever. All Rights Reserved. Introduction Choosing a Race (Cont.’d) What Is This Game All About? . 1 Magician . .20 Too Long; Didn’t Read Version . 1 Moon Rabbit . .20 Here’s the Situation . 1 Oni . .21 But Wait! There’s More! . 1 Tengu . .21 Crow Tengu . .22 About This Game . 2 White Wolf Tengu . .22 About the Touhou Project . 2 Vampire . .23 About Role-Playing Games . -

Internet Security Threat Report Volume 24 | February 2019
ISTRInternet Security Threat Report Volume 24 | February 2019 THE DOCUMENT IS PROVIDED “AS IS” AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENT. THE INFORMATION CONTAINED IN THIS DOCUMENT IS SUBJECT TO CHANGE WITHOUT NOTICE. INFORMATION OBTAINED FROM THIRD PARTY SOURCES IS BELIEVED TO BE RELIABLE, BUT IS IN NO WAY GUARANTEED. SECURITY PRODUCTS, TECHNICAL SERVICES, AND ANY OTHER TECHNICAL DATA REFERENCED IN THIS DOCUMENT (“CONTROLLED ITEMS”) ARE SUBJECT TO U.S. EXPORT CONTROL AND SANCTIONS LAWS, REGULATIONS AND REQUIREMENTS, AND MAY BE SUBJECT TO EXPORT OR IMPORT REGULATIONS IN OTHER COUNTRIES. YOU AGREE TO COMPLY STRICTLY WITH THESE LAWS, REGULATIONS AND REQUIREMENTS, AND ACKNOWLEDGE THAT YOU HAVE THE RESPONSIBILITY TO OBTAIN ANY LICENSES, PERMITS OR OTHER APPROVALS THAT MAY BE REQUIRED IN ORDER FOR YOU TO EXPORT, RE-EXPORT, TRANSFER IN COUNTRY OR IMPORT SUCH CONTROLLED ITEMS. TABLE OF CONTENTS 1 2 3 BIG NUMBERS YEAR-IN-REVIEW FACTS AND FIGURES METHODOLOGY Formjacking Messaging Cryptojacking Malware Ransomware Mobile Living off the land Web attacks and supply chain attacks Targeted attacks Targeted attacks IoT Cloud Underground economy IoT Election interference MALICIOUS -

Security Now! #664 - 05-22-18 Spectreng Revealed
Security Now! #664 - 05-22-18 SpectreNG Revealed This week on Security Now! This week we examine the recent flaws discovered in the secure Signal messaging app for desktops, the rise in DNS router hijacking, another seriously flawed consumer router family, Microsoft Spectre patches for Win10's April 2018 feature update, the threat of voice assistant spoofing attacks, the evolving security of HTTP, still more new trouble with GPON routers, Facebook's Android app mistake, BMW's 14 security flaws and some fun miscellany. Then we examine the news of the next-generation of Spectre processor speculation flaws and what they mean for us. Our Picture of the Week Security News Update your Signal Desktop Apps for Windows & Linux A few weeks ago, Argentinian security researchers discovered a severe vulnerability in the Signal messaging app for Windows and Linux desktops that allows remote attackers to execute malicious code on recipient systems simply by sending a message—without requiring any user interaction. The vulnerability was accidentally discovered while researchers–amond them Juliano Rizzo–were chatting on Signal messenger and one of them shared a link of a vulnerable site with an XSS payload in its URL. However, the XSS payload unexpectedly got executed on the Signal desktop app!! (Juliano Rizzo was on the beach when the BEAST and CRIME attacks occurred to him.) After analyzing the scope of this issue by testing multiple XSS payloads, they found that the vulnerability resides in the function responsible for handling shared links, allowing attackers to inject user-defined HTML/JavaScript code via iFrame, image, video and audio tags. -

Internet of Things Botnet Detection Approaches: Analysis and Recommendations for Future Research
applied sciences Systematic Review Internet of Things Botnet Detection Approaches: Analysis and Recommendations for Future Research Majda Wazzan 1,*, Daniyal Algazzawi 2 , Omaima Bamasaq 1, Aiiad Albeshri 1 and Li Cheng 3 1 Computer Science Department, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah 21589, Saudi Arabia; [email protected] (O.B.); [email protected] (A.A.) 2 Information Systems Department, Faculty of Computing and Information Technology, King Abdulaziz University, Jeddah 21589, Saudi Arabia; [email protected] 3 Xinjiang Technical Institute of Physics & Chemistry Chinese Academy of Sciences, Urumqi 830011, China; [email protected] * Correspondence: [email protected] Abstract: Internet of Things (IoT) is promising technology that brings tremendous benefits if used optimally. At the same time, it has resulted in an increase in cybersecurity risks due to the lack of security for IoT devices. IoT botnets, for instance, have become a critical threat; however, systematic and comprehensive studies analyzing the importance of botnet detection methods are limited in the IoT environment. Thus, this study aimed to identify, assess and provide a thoroughly review of experimental works on the research relevant to the detection of IoT botnets. To accomplish this goal, a systematic literature review (SLR), an effective method, was applied for gathering and critically reviewing research papers. This work employed three research questions on the detection methods used to detect IoT botnets, the botnet phases and the different malicious activity scenarios. The authors analyzed the nominated research and the key methods related to them. The detection Citation: Wazzan, M.; Algazzawi, D.; methods have been classified based on the techniques used, and the authors investigated the botnet Bamasaq, O.; Albeshri, A.; Cheng, L. -

Technical Brief P2P Iot Botnets Clean AC Font
Uncleanable and Unkillable: The Evolution of IoT Botnets Through P2P Networking Technical Brief By Stephen Hilt, Robert McArdle, Fernando Merces, Mayra Rosario, and David Sancho Introduction Peer-to-peer (P2P) networking is a way for computers to connect to one another without the need for a central server. It was originally invented for file sharing, with BitTorrent being the most famous P2P implementation. Decentralized file-sharing systems built on P2P networking have stood the test of time. Even though they have been used to share illegal pirated content for over 20 years, authorities have not been able to put a stop to these systems. Of course, malicious actors have used it for malware for quite a long time as well. Being able to create and manage botnets without the need for a central server is a powerful capability, mostly because law enforcement and security companies typically take down criminal servers. And since a P2P botnet does not need a central command-and-control (C&C) server, it is much more difficult to take down. From the point of view of defenders, this is the scariest problem presented by P2P botnets: If they cannot be taken down centrally, the only option available would be to disinfect each of the bot clients separately. Since computers communicate only with their own peers, the good guys would need to clean all the members one by one for a botnet to disappear. Originally, P2P botnets were implemented in Windows, but developers of internet-of-things (IoT) botnets do have a tendency to start incorporating this feature into their creations. -

Reporting, and General Mentions Seem to Be in Decline
CYBER THREAT ANALYSIS Return to Normalcy: False Flags and the Decline of International Hacktivism By Insikt Group® CTA-2019-0821 CYBER THREAT ANALYSIS Groups with the trappings of hacktivism have recently dumped Russian and Iranian state security organization records online, although neither have proclaimed themselves to be hacktivists. In addition, hacktivism has taken a back seat in news reporting, and general mentions seem to be in decline. Insikt Group utilized the Recorded FutureⓇ Platform and reports of historical hacktivism events to analyze the shifting targets and players in the hacktivism space. The target audience of this research includes security practitioners whose enterprises may be targets for hacktivism. Executive Summary Hacktivism often brings to mind a loose collective of individuals globally that band together to achieve a common goal. However, Insikt Group research demonstrates that this is a misleading assumption; the hacktivist landscape has consistently included actors reacting to regional events, and has also involved states operating under the guise of hacktivism to achieve geopolitical goals. In the last 10 years, the number of large-scale, international hacking operations most commonly associated with hacktivism has risen astronomically, only to fall off just as dramatically after 2015 and 2016. This constitutes a return to normalcy, in which hacktivist groups are usually small sets of regional actors targeting specific organizations to protest regional events, or nation-state groups operating under the guise of hacktivism. Attack vectors used by hacktivist groups have remained largely consistent from 2010 to 2019, and tooling has assisted actors to conduct larger-scale attacks. However, company defenses have also become significantly better in the last decade, which has likely contributed to the decline in successful hacktivist operations. -

Week 3 Reading Assignment: Understanding the Mirai Botnet
Week 3 Reading Assignment: Understanding the Mirai Botnet Discussion Summary Questions Raised in the Paper: • How could an attacker mine the data available through Spectre attack? • Since the Spectre vulnerability is harder to exploit, it would be interesting to know if this attack has been successfully performed outside of a lab? • Is it possible that Spectre vulnerability is already being taken advantage of, and no one is aware? • What other security problems are embedded in our computers, that we don’t know of? • The released Meltdown and Spectre patches only address issues raised by researches. However, there is a higher probability that one can possibly devise another cache mechanism to trick CPU into reading memory map; as the mechanism is built into the physical memory space. What about those vulnerabilities? Main Take-Aways: About the Attacks: • Meltdown and Spectre vulnerabilities are among the best discoveries in computer science if not the most important • Both vulnerabilities take advantage of a process called speculative execution, where the processor can execute some code in advance and out of order and cache the output, expecting to use that output for the next step in the process. • Using Kernel Page Table Isolation (KPTI) technique, which stops speculation execution by removing mapping kernel into a program when running user space, is one of the current known mitigation techniques to prevent Meltdown. • Noticeable difference between Meltdown and Spectre is the fact that Spectre does not use privilege escalation, thus making the Spectre vulnerability more sophisticated. • “I do not personally consider this a CPU design flaw like Meltdown per se. -

Remyadry, a Dungeon Crawling RPG Inspired by Touhou Project Was Released Today
For Immediate Release Contact: CuriousFactory (Oversea Rep for Eisys, Inc) July 11, 2018 Ayaka Hahn 703-304-7685 [email protected] Remyadry, a Dungeon Crawling RPG Inspired by Touhou Project was Released Today - 100% translated into English, the game is being sold on DLsite.com and Steam - TOKYO, Japan – Eisys, Inc. today announced that they have released Remyadry, a dungeon crawling RPG developed by Kokoko Soft, on its online store DLsite.com and on Steam. Remyadry is an RPG inspired by Touhou Project from “Team Shanghai Alice”. [Story] Gensokyo is connected with 'a certain world' and eventually a huge dungeon by the name of 'Mazes of the Week' appears. The mansion that protagonist Remilia Scarlet was living in is trapped within this dungeon. Cooperating with companions, Remilia and co. end up having to clear that dungeon. [Game Overview] Remyadry is a mouse controlled RPG with character creation and dungeon crawling. Players can compose their party from a maximum of 20 units and fight their way through the dungeon. [Unique Features] • Players can import their own image assets into the game to personalize the game experience • Characters can be named freely • Acquire more characters as the story progresses • Characters can be powered up by distributing points earned in the game • Earn skill points by progressing the game and customize your skill tree • Most battles are automated for a smooth game experience [Special Discount] A 10% discount is being offered during the first week after release on Steam, so don’t miss this chance to try out this popular indie RPG from Japan! Remyadry Promotion Video: https://youtu.be/aH6l7klb-4c Remyadry Product Pages: DLsite.com: http://www.dlsite.com/eng/work/=/product_id/RE227437.html Steam: https://store.steampowered.com/app/867490/Remyadry/ Platform: Windows 8 / Windows 10 Genre: Indie/RPG Languages: English, Chinese (Traditional / Simplified) 【About EISYS, Inc. -

Ethical Issues in Research Using Datasets of Illicit Origin
Ethical issues in research using datasets of illicit origin Daniel R. Thomas Sergio Pastrana Alice Hutchings Richard Clayton Alastair R. Beresford Cambridge Cybercrime Centre, Computer Laboratory University of Cambridge United Kingdom [email protected] ABSTRACT ACM Reference format: We evaluate the use of data obtained by illicit means against Daniel R. Thomas, Sergio Pastrana, Alice Hutchings, Richard Clayton, and Alastair R. Beresford. 4239. Ethical issues in research a broad set of ethical and legal issues. Our analysis covers using datasets of illicit origin. In Proceedings of IMC ’39, London, both the direct collection, and secondary uses of, data ob- UK, November 3–5, 4239, 3: pages. tained via illicit means such as exploiting a vulnerability, or DOI: 32.3367/5353587.53535:; unauthorized disclosure. We extract ethical principles from existing advice and guidance and analyse how they have been applied within more than 42 recent peer reviewed papers that 3 INTRODUCTION deal with illicitly obtained datasets. We find that existing The scientific method requires empirical evidence to test advice and guidance does not address all of the problems that hypotheses. Consequently, both the gathering, and the use researchers have faced and explain how the papers tackle of, data is an essential component of science and supports ethical issues inconsistently, and sometimes not at all. Our evidence-based decision making. Computer scientists make analysis reveals not only a lack of application of safeguards significant use of data to support research and inform policy, but also that legitimate ethical justifications for research are and this includes data which was obtained through illegal or being overlooked. -

Tech & Policy Initiative, Working Paper Series 2
Tech & Policy Initiative, Working Paper Series 2 It is with great pleasure that I invite you to read this second volume of Columbia SIPA’s Tech & Policy Initiative’s Working Paper Series. Building on the insights of the first volume, the second volume features working papers produced by SIPA-supported expert and next generation scholars who are engaging critical areas related to the impact of digital technology on society and institutions. The papers are multi-disciplinary and forward-looking, engaging complex subjects including the critical areas of Internet and data governance, the dynamics of cyber conflict and cyber sovereignty, how digital technology has impacted traditional economic sectors and business models, or other areas. This academic work was undertaken with vital support of the Carnegie Corporation of New York as part of SIPA’s Tech & Policy Initiative, an ambitious effort to explore the digital world and SIPA’s core fields of study. Since its inception, the Tech and Policy Initiative has sought to bridge the gap between policymakers, academics and practitioners in cybersecurity, internet governance and the digital economy through convening, research, training and other activities. The Tech & Policy Initiative draws on many disciplines and talented researchers within SIPA, in other parts of Columbia University, and outside entities to develop insights that will translate into better and more effective policies, and to inform government policies and private sector actions. This volume also includes papers prepared for SIPA’s 2017 Global Digital Futures Policy Forum, an annual conference that brought together more than 100 scholars, private sector leaders, legal experts, entrepreneurs, technologists, and others to discuss the challenges of internet fragmentation. -

Iot Botnet Forensics: a Comprehensive Digital Forensic Case Study on Mirai Botnet Servers
Forensic Science International: Digital Investigation 32 (2020) 300926 Contents lists available at ScienceDirect Forensic Science International: Digital Investigation journal homepage: www.elsevier.com/locate/fsidi DFRWS 2020 EU e Proceedings of the Seventh Annual DFRWS Europe IoT Botnet Forensics: A Comprehensive Digital Forensic Case Study on Mirai Botnet Servers * Xiaolu Zhang, Oren Upton, Nicole Lang Beebe , Kim-Kwang Raymond Choo Department of Information Systems & Cyber Security, University of Texas at San Antonio, San Antonio, TX, 78249, USA article info abstract Article history: Internet of Things (IoT) bot malware is relatively new and not yet well understood forensically, despite its potential role in a broad range of malicious cyber activities. For example, it was abused to facilitate the distributed denial of service (DDoS) attack that took down a significant portion of the Internet on October Keywords: 21, 2016, keeping millions of people from accessing over 1200 websites, including Twitter and NetFlix for Mirai nearly an entire day. The widespread adoption of an estimated 50 billion IoT devices, as well as the IoT malware increasing interconnectivity of those devices to traditional networks, not to mention to one another with Forensics the advent of fifth generation (5G) networks, underscore the need for IoT botnet forensics. This study is Botnet server the first published, comprehensive digital forensic case study on one of the most well known families of IoT bot malware - Mirai. Past research has largely studied the botnet architecture and analyzed the Mirai source code (and that of its variants) through traditional static and dynamic malware analysis means, but has not fully and forensically analyzed infected devices or Mirai network devices. -

Early Detection of Mirai-Like Iot Bots in Large-Scale Networks Through Sub-Sampled Packet Traffic Analysis
Early Detection Of Mirai-Like IoT Bots In Large-Scale Networks Through Sub-Sampled Packet Traffic Analysis Ayush Kumar and Teng Joon Lim Department of Electrical and Computer Engineering, National University of Singapore, Singapore 119077 [email protected], [email protected] Abstract. The widespread adoption of Internet of Things has led to many secu- rity issues. Recently, there have been malware attacks on IoT devices, the most prominent one being that of Mirai. IoT devices such as IP cameras, DVRs and routers were compromised by the Mirai malware and later large-scale DDoS at- tacks were propagated using those infected devices (bots) in October 2016. In this research, we develop a network-based algorithm which can be used to detect IoT bots infected by Mirai or similar malware in large-scale networks (e.g. ISP network). The algorithm particularly targets bots scanning the network for vul- nerable devices since the typical scanning phase for botnets lasts for months and the bots can be detected much before they are involved in an actual attack. We analyze the unique signatures of the Mirai malware to identify its presence in an IoT device. The prospective deployment of our bot detection solution is discussed next along with the countermeasures which can be taken post detection. Further, to optimize the usage of computational resources, we use a two-dimensional (2D) packet sampling approach, wherein we sample the packets transmitted by IoT devices both across time and across the devices. Leveraging the Mirai signatures identified and the 2D packet sampling approach, a bot detection algorithm is pro- posed.