Note Su Oracle Solaris 10 9/10 • Settembre 2010 Indice
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Techniques for Authoring Complex XML Documents Vincent Quint, Irène Vatton
Techniques for Authoring Complex XML Documents Vincent Quint, Irène Vatton To cite this version: Vincent Quint, Irène Vatton. Techniques for Authoring Complex XML Documents. Proceedings of the 2004 ACM symposium on Document Engineering, DocEng 2004, Oct 2004, MilWaukee, WI, United States. pp.115-123, 10.1145/1030397.1030422. inria-00423365 HAL Id: inria-00423365 https://hal.inria.fr/inria-00423365 Submitted on 9 Oct 2009 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Techniques for Authoring Complex XML Documents Vincent Quint Irene` Vatton INRIA Rhone-Alpesˆ INRIA Rhone-Alpesˆ 655 avenue de l’Europe 655 avenue de l’Europe 38334 Saint Ismier Cedex, France 38334 Saint Ismier Cedex, France [email protected] [email protected] ABSTRACT 1. INTRODUCTION This paper reviews the main innovations of XML and con- Authoring techniques for structured documents consti- siders their impact on the editing techniques for structured tuted an active research area during the second half of the documents. Namespaces open the way to compound docu- 80’s and the early 90’s [10]. Several experimental systems ments; well-formedness brings more freedom in the editing such as Grif [7] and Rita [6] were developed and a few pro- task; CSS allows style to be associated easily with structured duction tools resulted from that work. -

Oracle Solaris 10 910 Release Notes
Oracle® Solaris 10 9/10 Release Notes Part No: 821–1839–11 September 2010 Copyright © 2010, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related software documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are “commercial computer software” or “commercial technical data” pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms setforth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). Oracle America, Inc., 500 Oracle Parkway, Redwood City, CA 94065. -
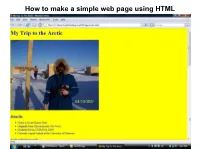
How to Make a Simple Web Page Using HTML
How to make a simple web page using HTML Introduction to HTML HTML For this class, you will have to create a web page using HTML Joke: (from http://www.w3schools.com/html/html_layout.asp): Student: How do you spell HTML? HTML stands for Hyper Text Markup Language Used to create web pages Made up of Tags - commands enclosed in < and >, example <HTML> Opening tag: <HTML> Closing tag: </HTML> HTML page “skeleton” <HTML> - opening HTML tag <HEAD> <TITLE>Page Title</TITLE> </HEAD> <BODY> Page Body </BODY> </HTML> - closing HTML TAG Not all tags need a closing tag, but its always safer to include it An html document should end with the extension “.html” or “.htm” As I will demonstrate, an html document can be written using notepad; no special software is needed HTML Tags First tag: <HTML> First tag in document Tag tells the Internet browser that it is reading an HTML document Without it, the browser would think it was viewing a text document Closed at end of document with </HTML> tag All content of web page is between <HTML> and </HTML> Can think of the <HTML> tag as being a container, since it “holds” the entire content of the web page between the <HTML> and </HTML> tags HTML Tags Next tag: <HEAD> Think of it as a container for aspects of the page that aren't part of the “meat” of the page For the purposes of this intro, will look at the <TITLE> tag and <META name=“description” content=”...”> tag that go within the <HEAD> container; that is, between the <HEAD> and </HEAD> tags Closed with </HEAD> tag <TITLE> Tag Belongs inside the <HEAD> container; -

Transforming Library Service Through Information Commons Case Studies for the Digital Age
TRANSFORMING LIBRARY SERVICE THROUGH INFORMATION COMMONS Case Studies for the Digital Age D. Russell Bailey and Barbara Gunter Tierney TRANSFORMING LIBRARY SERVICE THROUGH INFORMATION COMMONS Case Studies for the Digital Age D. Russell Bailey and Barbara Gunter Tierney AMERICAN LIBRARY ASSOCIATION Chicago 2008 While extensive effort has gone into ensuring the reliability of information appearing in this book, the publisher makes no warranty, express or implied, on the accuracy or reliability of the information, and does not assume and hereby disclaims any liability to any person for any loss or damage caused by errors or omissions in this publication. Composition in Berkeley and Antique Olive typefaces using InDesign on a PC platform. The paper used in this publication meets the minimum requirements of American National Standard for Information Sciences—Permanence of Paper for Printed Library Materials, ANSI Z39.48-1992. Library of Congress Cataloging-in-Publication Data Bailey, D. Russell. Transforming library service through information commons : case studies for the digital age / D. Russell Bailey and Barbara Gunter Tierney. p. cm. Includes bibliographical references and index. ISBN-13: 978-0-8389-0958-4 (alk. paper) ISBN-10: 0-8389-0958-2 (alk. paper) 1. Information commons. I. Tierney, Barbara. II. Title. ZA3270.B35 2008 025.5'23—dc22 2007040040 Copyright © 2008 by the American Library Associ ation. All rights reserved except those which may be granted by Sections 107 and 108 of the Copyright Revision Act of 1976. ISBN-13: 978-0-8389-0958-4 -

Security Analysis of IP-Cameras Group DS101F21
Security Analysis of IP-cameras Aalborg University Group DS101F21 Software 10: "Security Analysis of Abstract: This project is about a security analysis of IP-cameras" IP-cameras and developing a solution to improve the security through automated firmware updates. We found it implausible to Group DS101F21 perform automated testing on firmware images to detect known vulnerabilities May 28, 2021 through the analysis. The solution developed through this project is an automated update framework that Semester: relies on the device manufacturers to develop 10. semester and maintain firmware updates for the Project theme: devices. Through said updates, the overall Security security of their devices would increase, but Project duration: only if the end-user applies the updates. We 1/02/2021 - 28/05/2021 propose a solution that can automate and ECTS: streamline the update process on IP-cameras 30 from multiple manufactures. Supervisor: The overall conclusion of this project is that René Rydhof Hansen the current approach to firmware [email protected] development, distribution, and consumption Danny Bøgsted Poulsen are all contributing factors to the security of [email protected] IP-cameras in general. The solution Authors: Thomas Lundsgaard Kammersgaard developed in this project automates the [email protected] update process for IP-cameras produced by Thue Vestergaard Iversen Hikvision and Herospeed. This is done by [email protected] selecting the correct firmware and making sensible choices such as calculating checksum matches, performing backups and reapplying user configurations. Number of pages: 84 Everyone is permitted to copy and distribute verbatim copies of this document. Preface This report was written by two Software students from group DS101F21 at Aalborg University during their 10th semester in Software Engineering. -

Comprehensive Guide to a Professional Blog Site: a Wordpress Example
Comprehensive Guide to a Professional Blog Site: A WordPress Example by Michael K. Bergman September 2005 Michael K. Bergman is a co-founder, chief technology officer, and chairman of About BrightPlanet Corporation. He is also the lead project coordinator for the DiDia (document Mike intelligence, document information automation) open source project. Mike’s software management experience includes products in Internet search tools, data warehousing, bioinformatics, accounting, finance, management, planning, electronic mapping and technical areas. He is the author of an award-winning Internet search tutorial and the definitive deep Web white paper, among other publications. He is acknowledged as an expert in search, information theory, and document content. Mike’s current musings may be found on his Web blog site, http://mkbergman.com. © Copyright 2005. All rights reserved. Do not reproduce without permission. Gone beyond Blogger? Want to really be aggressive in functionality and scope of SUMMARY content for your personal, professional or corporate blog? If so, this Comprehensive Guide to a Professsional Blog Site may be useful to you. This Guide is the result of 350 hrs of learning and experimentation to test the boundaries of blog functionality, scope and capabilities. I myself began this process as a total newbie about six months ago – which likely shows in gaps and naïveté – but I have been aggressive in documenting as I have gone. The learning from my professional blog journey, still ongoing, is reflected in these pages. This Guide addresses about 100 individual “how to” blogging topics and lessons, all geared to the content-focused and not occasional blogger. More than 140 citations, 80 of which are unique, are provided to other experts with guidance for all of us. -

Firefox Hacks Is Ideal for Power Users Who Want to Maximize The
Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader Firefox Hacks is ideal for power users who want to maximize the • Reviews effectiveness of Firefox, the next-generation web browser that is quickly • Errata gaining in popularity. This highly-focused book offers all the valuable tips • Academic and tools you need to enjoy a superior and safer browsing experience. Learn how to customize its deployment, appearance, features, and functionality. Firefox Hacks By Nigel McFarlane Publisher: O'Reilly Pub Date: March 2005 ISBN: 0-596-00928-3 Pages: 398 Table of • Contents • Index • Reviews Reader • Reviews • Errata • Academic Copyright Credits About the Author Contributors Acknowledgments Preface Why Firefox Hacks? How to Use This Book How This Book Is Organized Conventions Used in This Book Using Code Examples Safari® Enabled How to Contact Us Got a Hack? Chapter 1. Firefox Basics Section 1.1. Hacks 1-10 Section 1.2. Get Oriented Hack 1. Ten Ways to Display a Web Page Hack 2. Ten Ways to Navigate to a Web Page Hack 3. Find Stuff Hack 4. Identify and Use Toolbar Icons Hack 5. Use Keyboard Shortcuts Hack 6. Make Firefox Look Different Hack 7. Stop Once-Only Dialogs Safely Hack 8. Flush and Clear Absolutely Everything Hack 9. Make Firefox Go Fast Hack 10. Start Up from the Command Line Chapter 2. Security Section 2.1. Hacks 11-21 Hack 11. Drop Miscellaneous Security Blocks Hack 12. Raise Security to Protect Dummies Hack 13. Stop All Secret Network Activity Hack 14. -

Station Debian 9 - Applications
station Debian 9 - Applications Tux the Penguin by Carlos Pardo J'utilise Linux non par satisfaction philosophique, mais pour trois raisons : ça marche, ça marche à chaque fois, et ça marche à chaque fois de la même manière. Kha. station Debian 9 - Applications édition 56 du 04/12/17 stef [@|.]genesix.org CC-by-nc-sa : Paternité, pas d'utilisation commerciale, partage des conditions initiales à l'identique. page 1 sur 54 Indice Validation Objet 1 10/09/17 Édition initiale sr 43 12/10/17 Bon pour diffusion sr 50 14/11/17 Ajout d’applications, améliorations diverses sr 55 04/12/17 Corrections diverses sr 56 Étapes de mise à jour du tableau d'historique. Avant toute modification du document : – Positionner le curseur sur l'avant dernière ligne du tableau (celle au dessus de « Édition courante ») ; – Créer une nouvelle ligne dans le tableau ; – Sélectionner et copier la dernière ligne, de « Validation » à « Email » (tout sauf la première colonne) ; – Positionner le curseur sur l'avant dernière ligne, dans la colonne « Validation » ; – Coller ; Reporter l'indice de la dernière ligne dans la nouvelle ligne. Impression 14/10/17 - 15:47 Édition SR56- 367:02:39 « Be seeing you » Number six, The prisoner - « I have been studying how I may compare this prison where I live unto the world » - Richard II, Act V station Debian 9 - Applications édition 56 du 04/12/17 stef [@|.]genesix.org CC-by-nc-sa : Paternité, pas d'utilisation commerciale, partage des conditions initiales à l'identique. page 2 sur 54 Table des matières Généralités 1 Choix des logiciels.....................................................................................................................................6 -

IM Interview with Brian King August 8, 2007 Olivia Ryan: When Did You
IM Interview with Brian King August 8, 2007 Olivia Ryan: When did you begin using computers and how did you get interested in computers? Brian King: I was a late starter. I had little interest as a child and teenager, preferring outdoor pursuits. Even during my first degree course in college, my only exposure was to use PCs to write a few essays. My interest arose when I realised my initial qualification did not give me any career options I particularly liked, so I started looking elsewhere. Olivia Ryan: Have you had formal computer training? Brian King: Yes. My second college course, a post-graduate, was a higher diploma in Information Technology; an intensive 1 year computer science course. My initial degree was Politics and History. Olivia Ryan: When did you begin contributing to open source projects and how did you first connect to open source? Brian King: My first exposure to open source was in 1999, with the Mozilla project. My employer at the time, XML Workshop (http://www.xmlw.ie) chose the source to build children's learning software. I started communicating with Mozilla developers (then at Netscape) and other volunteers via mailing lists and IRC. This was one of the first 3rd party applications, back in the day when the Platform was, how should I say, less than stable. Olivia Ryan: What Mozilla projects have you worked on and in what capacities have you worked? Brian King: I started contributing front-end code, XUL/JavaScript/CSS, to the Editor module (Mozilla Composer at the time). Apart from that, I have contributed nothing to the core base. -

Essentials of Scientific Computing} \Author{Kevin Cooper}
Essentials of Scientific Computing Kevin Cooper October 19, 2016 2 Copyright c Kevin Cooper 2016 Contents 0 Introduction 7 0.1 Example – the problem . .8 1 Networking Concepts 11 1.1 Background . 12 1.1.1 Ethernet . 14 1.1.2 Colors . 15 1.2 Packets and the TCP/IP Suite . 16 1.3 Public Key Encryption . 21 1.4 Running commands on a remote computer . 21 1.5 File transfer . 24 1.5.1 Basic FTP commands . 25 2 The World Wide Web 29 2.1 The Browser . 29 2.1.1 Browser Motivation . 30 2.1.2 URLs . 31 2.1.3 Local Customization . 33 2.1.4 Editing Web Pages Using a Browser . 36 2.2 Markup Languages . 44 2.3 Hypertext Markup Language . 45 2.3.1 HTML Principles . 46 2.3.2 Links to external objects . 48 2.3.3 Tables . 49 2.4 Cascading Style Sheets . 50 2.4.1 Style Sheet Properties . 52 2.4.2 Style Classes . 54 2.4.3 Style IDs . 55 2.4.4 Pseudo-classes . 56 2.5 MathML . 58 2.5.1 MathML Syntax . 60 2.5.2 MathML Alignments . 65 2.6 SVG . 68 3 4 CONTENTS 3 LATEX 77 3.1 Starting a document . 78 3.2 Commands and Environments . 79 3.3 Headings . 80 3.4 Mathematical Typesetting . 81 3.4.1 Math Mode . 81 3.4.2 Math Notation . 82 3.4.3 Alignment . 84 3.5 Font modifications . 88 3.6 Counting . 89 3.7 Lists . 91 3.8 Boxes, Glue, and Space . -

Seamonkey -...::: SANUX
RReveviisstata LINLINUXUX FFRROONTNT no.no. 0101 RRiivvereraa UrUruguauguayy OOcctubrtubree 20072007 file:///D:/Mis%20Documentos/Loot/LinuxFront/LinuxFront1/Linux%20Front/nro%20pag/pg2.bmp file:///D:/Mis%20Documentos/Loot/LinuxFront/LinuxFront1/Linux%20Front/enc&final/INTRO.png Bienvenidos !!! A Linux Front, la revista de Software Libre y Codigo Abierto de la frontera norte. Esta revista digital es una iniciativa del grupo de usuarios de Linux de la ciudad de Rivera. El grupo esta formado por cuatro estudiantes de informática que tienen como objetivo dar a conocer el software libre de mano de su representante más conocido, GNU/Linux o por medio de la presentación de software libre alternativo al propietario, como OpenOffice.org, GIMP, Gaim y muchos más. Los miembros del FLUG son: Ernesto dos Santos “seto” Alberto Cáseres “beto” Martín Castro “gafo” Wilson Rodríguez “will” y Ógopo, una criatura algo chueca y despistada de origen desconocido (tal vez virus o espía alienígena) la cual fue adoptada como mascota por el grupo. Tambien tenemos a un miembro honorario que es Martin Esteves “MartinE”. El principal hobie en informatica de los miembros es la programación. El FLUG se formo en el encuentro FliSOL realizado en la ciudad de Rivera en la escuela de informática, en el cual nos hicieron una presentación del software librex, instalamos varias distros de GNU/Linux, realizamos conexiones de redes entre Linux y Window$ y un monton de cosas mas. file:///D:/Mis%20Documentos/Loot/LinuxFront/LinuxFront1/Linux%20Front/nro%20pag/pg3.bmp Foto del primer día de vida del FLUG durante el evento FLISOL en la ciudad de rivera, algunos mienbros ya no estan y otros que se adirieron recientemente tampoco. -

A Dokumentum Az Emelt Szintű Érettségi Vizsgán , Valamint A
AZ INFORMATIKAI ALAPISMERETEK VIZSGATÁRGY ÍRÁSBELI ÉS SZÓBELI ÉRETTSÉGI VIZSGÁIHOZ A 2012. ÉV VIZSGAIDŐSZAKAIRA ÉRVÉNYES SZOFTVEREK LISTÁJA A dokumentum az emelt szintű érettségi vizsgán, valamint a kormányhivatalok által szervezett középszintű érettségi vizsgán választható szoftvereket tartalmazza. Az érettségit szervező középiskolák ettől eltérő, saját szoftverlistát hirdethetnek ki. Ebben a szoftverlistában azoknak a szoftvereknek a felsorolása található meg, amelyekkel az érettségi vizsga feladatlapjai közel azonos feltételekkel (nehézség, időigény) oldhatók meg. A lista a helyi lehetőségeknek megfelelően kibővíthető olyan programokkal, amelyek funkcionalitásukban, kezelésükben a megadott programokkal közel azonosak. A lista szűkítése és bővítése az intézményvezető felelősségi körébe tartozik. Minden szoftvercsoportból csak egyetlen szoftvert választhat! Az irodai szoftvercsomag kiválasztásával egyúttal az adatbázis-kezelő programot is meghatározza! FIGYELEM! A középfokú informatikai alapismeretek vizsgák zavartalan lebonyolítása, a vizsgák könnyebb megszervezése, valamint a későbbi reklamációk elkerülése érdekében hangsúlyozottan ajánljuk, hogy az intézményben vizsgát tevő valamennyi vizsgázóval töltessenek ki szoftverválasztásra vonatkozó nyilatkozatot. a) Windows operációs rendszeren Írásbeli és szóbeli vizsgán is használandó szoftverek Szoftverek Szoftvercsoportok MS Windows XP Professional Operációs rendszer MS Windows 7 Enterprise MS Office 2003 Professional MS Office 2007 Enterprise Irodai szoftvercsomag LibreOffice 3.3.4 (MySQL