W Shekatkar Committee Report W Atmanirbhar Bharat Abhiyan W
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Comparative Analysis of NLP Models for Google Meet Transcript Summarization
EasyChair Preprint № 5404 Comparative Analysis of NLP models for Google Meet Transcript Summarization Yash Agrawal, Atul Thakre, Tejas Tapas, Ayush Kedia, Yash Telkhade and Vasundhara Rathod EasyChair preprints are intended for rapid dissemination of research results and are integrated with the rest of EasyChair. April 28, 2021 Comparative Analysis of NLP models for Google Meet Transcript Summarization Yash Agrawal1,a) Atul Thakre1,b) Tejas Tapas1,c) Ayush Kedia1,d) Yash Telkhade1,e) Vasundhara Rathod1,f) 1) Computer Science & Engineering, Shri Ramdeobaba College of Engineering and Management, Nagpur, India a) [email protected] , +91 7083645470 b) [email protected] , +91 8956758226 c) [email protected] , +918380073925 d) [email protected] , +91 8459811323 e) [email protected] , +91 9021067230 f) [email protected], +918055225407 Abstract. Manual transcription and summarization is a cumbersome process necessitating the development of an efficient automatic text summarization technique. In this study, a Chrome extension is used for making the process of transcription hassle- free. It uses the text summarization technique to generate concise and succinct matter. Also, the tool is accessorized using Google Translation, to convert the processed text into users' desired language. This paper illustrates, how captions can be traced from the online meetings, corresponding to which, meeting transcript is sent to the backend where it is summarized using an NLP model. It also walks through three different NLP models and presents a comparative study among them. The NLTK model utilizes the sentence ranking technique for extractive summarization. Word Embedding model uses pre-trained Glove Embeddings for extractive summarization. The T5 model performs abstractive summarization using transformer architecture. -

Quick Deployment Guide for Enabling Remote Working with Hangouts Meet
Enabling Remote Working with Hangouts Meet and Hangouts Chat: A quick deployment guide Work Transformation: Productivity & Collaboration Contents About this guide 2 1. Requirements 4 1.1 General requirements 4 1.2 Network requirements 4 1.3 Optimize Meet traffic for remote workers 5 2. Set up G Suite 7 2.1 Enroll in G Suite 7 2.2 Verify your domain 12 2.3 Provision your users 14 Step 1: Open the user management interface 14 Step 2: Download the CSV template file 15 Step 3: Add your users to the CSV template 16 Step 4: Upload the CSV file and provision your users 17 Troubleshooting upload errors 17 2.4 Distribute user credentials 18 2.5 Disable out-of-scope G Suite applications 19 2.6 Configure Meet 20 2.7 Configure Chat 22 2.8 Securing your setup 22 3. Appendix: User guide 22 3.1 Documentation hub 22 3.2 Meet/Calendar integrations 23 Schedule your meetings with Google Calendar 23 Deploy the Microsoft Outlook Meet plug-in 24 1 About this guide Highlights To provide companies with a deployment plan and guide to quickly Purpose enable remote working using Google Meet and Google Chat. Intended IT administrators audience Key That the audience has the required access and rights documented in the assumptions general requirements. This document provides guidance for quickly bootstrapping your company with the adoption of Hangouts Meet (for video conferencing) and Hangouts Chat (for instant messaging). Since Hangouts Meet and Hangouts Chat are part of the G Suite offering, this guide will walk you through the steps required to create a G Suite account, configure the billing, create the users, secure your setup, and teach your users how to use the communication suite. -

Everyone's Guide to Bypassing Internet Censorship
EVERYONE’S GUIDE TO BY-PASSING INTERNET CENSORSHIP FOR CITIZENS WORLDWIDE A CIVISEC PROJECT The Citizen Lab The University of Toronto September, 2007 cover illustration by Jane Gowan Glossary page 4 Introduction page 5 Choosing Circumvention page 8 User self-assessment Provider self-assessment Technology page 17 Web-based Circumvention Systems Tunneling Software Anonymous Communications Systems Tricks of the trade page 28 Things to remember page 29 Further reading page 29 Circumvention Technologies Circumvention technologies are any tools, software, or methods used to bypass Inter- net filtering. These can range from complex computer programs to relatively simple manual steps, such as accessing a banned website stored on a search engine’s cache, instead of trying to access it directly. Circumvention Providers Circumvention providers install software on a computer in a non-filtered location and make connections to this computer available to those who access the Internet from a censored location. Circumvention providers can range from large commercial organi- zations offering circumvention services for a fee to individuals providing circumven- tion services for free. Circumvention Users Circumvention users are individuals who use circumvention technologies to bypass Internet content filtering. 4 Internet censorship, or content filtering, has become a major global problem. Whereas once it was assumed that states could not control Internet communications, according to research by the OpenNet Initiative (http://opennet.net) more than 25 countries now engage in Internet censorship practices. Those with the most pervasive filtering policies have been found to routinely block access to human rights organi- zations, news, blogs, and web services that challenge the status quo or are deemed threatening or undesirable. -

Decoy Routing: Toward Unblockable Internet Communication
Decoy Routing: Toward Unblockable Internet Communication Josh Karlin Daniel Ellard Alden W. Jackson Christine E. Jones [email protected] [email protected] [email protected] [email protected] Greg Lauer David P. Mankins W. Timothy Strayer [email protected] [email protected] [email protected] Raytheon BBN Technologies an indirect method, such as a proxy server placed out- side of the filtered network. At a high level, this is the Abstract mechanism used by popular services such as Tor [13], Global Pass [4], and anonymizer.com [2]. Clients con- We present decoy routing, a mechanism capable of cir- nect to a server located outside of the filtered network, cumventing common network filtering strategies. Unlike and the server connects to the blacklisted destination on other circumvention techniques, decoy routing does not the client’s behalf. Although these services use differ- require a client to connect to a specific IP address (which ent techniques (VPNs, SOCKS proxies, HTTP proxies, is easily blocked) in order to provide circumvention. We content forwarders) we categorize them collectively as a show that if it is possible for a client to connect to any circumvention proxy or proxy. unblocked host/service, then decoy routing could be used to connect them to a blocked destination without coop- The problem with the proxy approach to circumven- eration from the host. This is accomplished by placing tion is that the adversary can also blacklist the circum- the circumvention service in the network itself – where vention proxy, preventing communication between the a single device could proxy traffic between a significant client and the proxy. -

Real-Time High-Resolution Background Matting
Real-Time High-Resolution Background Matting Shanchuan Lin* Andrey Ryabtsev* Soumyadip Sengupta Brian Curless Steve Seitz Ira Kemelmacher-Shlizerman University of Washington flinsh,ryabtsev,soumya91,curless,seitz,[email protected] Zoom input and background shot Zoom with new background Our Zoom plugin with new background Figure 1: Current video conferencing tools like Zoom can take an input feed (left) and replace the background, often introducing artifacts, as shown in the center result with close-ups of hair and glasses that still have the residual of the original background. Leveraging a frame of video without the subject (far left inset), our method produces real-time, high-resolution background matting without those common artifacts. The image on the right is our result with the corresponding close-ups, screenshot from our Zoom plugin implementation. Abstract ment can enhance privacy, particularly in situations where a user may not want to share details of their location and We introduce a real-time, high-resolution background re- environment to others on the call. A key challenge of this placement technique which operates at 30fps in 4K resolu- video conferencing application is that users do not typically tion, and 60fps for HD on a modern GPU. Our technique is have access to a green screen or other physical props used to based on background matting, where an additional frame of facilitate background replacement in movie special effects. the background is captured and used in recovering the al- pha matte and the foreground layer. The main challenge is While many tools now provide background replacement to compute a high-quality alpha matte, preserving strand- functionality, they yield artifacts at boundaries, particu- level hair details, while processing high-resolution images larly in areas where there is fine detail like hair or glasses in real-time. -

What's New for Google in 2020?
Kevin A. McGrail [email protected] What’s new for Google in 2020? Introduction Kevin A. McGrail Director, Business Growth @ InfraShield.com Google G Suite TC, GDE & Ambassador https://www.linkedin.com/in/kmcgrail About the Speaker Kevin A. McGrail Director, Business Growth @ InfraShield.com Member of the Apache Software Foundation Release Manager for Apache SpamAssassin Google G Suite TC, GDE & Ambassador. https://www.linkedin.com/in/kmcgrail 1Q 2020 STORY TIME: Google Overlords, Pixelbook’s Secret Titan Key, & Googlesplain’ing CES Jan 2020 - No new new hardware was announced at CES! - Google Assistant & AI Hey Google, Read this Page Hey Google, turn on the lights at 6AM Hey Google, Leave a Note... CES Jan 2020 (continued) Google Assistant & AI Speed Dial Interpreter Mode (Transcript Mode) Hey Google, that wasn't for you Live Transcripts Hangouts Meet w/Captions Recorder App w/Transcriptions Live Transcribe Coming Next...: https://mashable.com/article/google-translate-transcription-audio/ EXPERT TIP: What is Clipping? And Whispering! Streaming Games - Google Stadia Android Tablets No more Android Tablets? AI AI AI AI AI Looker acquisition for 2.6B https://www.cloudbakers.com/blog/why-cloudbakers-loves-looker-for-business-intelligence-bi From Thomas Kurian, head of Google Cloud: “focusing on digital transformation solutions for retail, healthcare, financial services, media and entertainment, and industrial and manufacturing verticals. He highlighted Google's strengths in AI for each vertical, such as behavioral analytics for retail, -

A Privacy Threat for Internet Users in Internet-Censoring Countries
A Privacy Threat for Internet Users in Internet-censoring Countries Feno Heriniaina R. College of Computer Science, Chongqing University, Chongqing, China Keywords: Censorship, Human Computer Interaction, Privacy, Virtual Private Networks. Abstract: Online surveillance has been increasingly used by different governments to control the spread of information on the Internet. The magnitude of this activity differs widely and is based primarily on the areas that are deemed, by the state, to be critical. Aside from the use of keywords and the complete domain name filtering technologies, Internet censorship can sometimes even use the total blocking of IP addresses to censor content. Despite the advances, in terms of technology used for Internet censorship, there are also different types of circumvention tools that are available to the general public. In this paper, we report the results of our investigation on how migrants who previously had access to the open Internet behave toward Internet censorship when subjected to it. Four hundred and thirty-two (432) international students took part in the study that lasted two years. We identified the most common circumvention tools that are utilized by the foreign students in China. We investigated the usability of these tools and monitored the way in which they are used. We identified a behaviour-based privacy threat that puts the users of circumvention tools at risk while they live in an Internet-censoring country. We also recommend the use of a user-oriented filtering method, which should be considered as part of the censoring system, as it enhances the performance of the screening process and recognizes the real needs of its users. -

U.S. Initiatives to Promote Global Internet Freedom: Issues, Policy, and Technology
U.S. Initiatives to Promote Global Internet Freedom: Issues, Policy, and Technology Patricia Moloney Figliola, Coordinator Specialist in Internet and Telecommunications Policy Kennon H. Nakamura Analyst in Foreign Affairs Casey L. Addis Analyst in Middle Eastern Affairs Thomas Lum Specialist in Asian Affairs September 8, 2010 Congressional Research Service 7-5700 www.crs.gov R41120 CRS Report for Congress Prepared for Members and Committees of Congress U.S. Initiatives to Promote Global Internet Freedom: Issues, Policy, and Technology Summary Modern means of communications, led by the Internet, provide a relatively inexpensive, open, easy-entry means of sharing ideas, information, pictures, and text around the world. In a political and human rights context, in closed societies when the more established, formal news media is denied access to or does not report on specified news events, the Internet has become an alternative source of media, and sometimes a means to organize politically. The openness and the freedom of expression allowed through blogs, social networks, video sharing sites, and other tools of today’s communications technology has proven to be an unprecedented and often disruptive force in some closed societies. Governments that seek to maintain their authority and control the ideas and information their citizens receive are often caught in a dilemma: they feel that they need access to the Internet to participate in commerce in the global market and for economic growth and technological development, but fear that allowing open access to the Internet potentially weakens their control over their citizens. The ongoing situation of Google in China is representative of these issues. -

Google Meet Guide
Google Meet Guide How to Schedule a Meeting (class sessions and office hours) 1. Access Hunter SOE Google Calendar 2. Create a new event and select More Options 3. Click Add Conferencing and then Hangouts Meet 4. Add student myhunter.cuny.edu or huntersoe.org email addresses under Guests 5. Select the paperclip symbol to attach optional documents, presentations, videos, etc. 6. Use the description box for relevant information 7. Click Save and then Send Every person on the guest list will receive an email with the meeting link and all attachments. Scheduled meetings can be accessed from the email link, Google Calendar, or https://meet.google.com. How to Create an Instant Meeting 1. Go to https://meet.google.com 2. Click Start a Meeting > Continue 3. Allow access to camera and microphone 4. Click Start Meeting 5. To add participants: ▪ Manually enter email addresses in the tab ▪ Copy meeting link and send it in an email, Blackboard announcement, or Google Classroom post How to Join a Meeting 1. Click on the meeting link to instantly join or type in the meeting code on https://meet.google.com 2. Allow access to camera and microphone How to Leave a Meeting 1. Press the symbol to exit 2. Click Rejoin to reenter How to Present in a Meeting (PowerPoints, documents, etc.) 1. Open the file(s) before or during the meeting 2. Select Present Now > A window or Entire screen > Share ‘A window’ allows you to present a single file while ‘Entire screen’ allows you to show multiple files on your screen without stopping and starting a new presentation 3. -

Conferencing with Google Meet
Conferencing with Google Meet Table of Contents Google Meet 2 Schedule a Google Meet 2 Start a Meeting 4 Conduct a Meeting 6 Present Now 7 Settings 7 People and Chat 8 Record a Meeting 9 Center for Innovation in Teaching and Research !1 Google Meet Google Meet will allow you to conduct HD video conferencing with up to 30 students. Google Meet is fully integrated with our WIU gmail accounts, so you can join meetings directly from a Calendar event or email invite. You also have the ability to allow for non WIU participants. Great for having a guest speaker. Schedule a Google Meet The best way to set up a Google Meet is to schedule one using your Google calendar. Do the following: • Make sure you are logged into your WIU Google account. • Open your Google calendar. • Click on the day you would like to schedule the meeting. • Add a title in the space provided and click More Options. Add title Click More Options • Uncheck the All day check box and set the time you want the meeting to occur. • Under the Event Details, click the Add conferencing drop down and choose Hangouts Meet. A View Details link will appear to the right with info about the meeting, including a direct link. • Use the Add guests section to type in the email addresses of your students to invite them to the meeting. (Note: you can copy all of your student email addresses at once from the CITR Attendance Tracker). • Click Save to save the calendar event and meeting. -
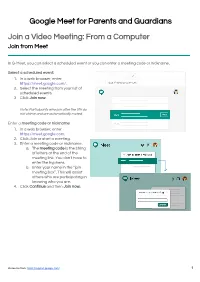
Google Meet for Parents and Guardians Join a Video Meeting: from a Computer Join from Meet
Google Meet for Parents and Guardians Join a Video Meeting: From a Computer Join from Meet In G-Meet, you can select a scheduled event or you can enter a meeting code or nickname. Select a scheduled event: 1. In a web browser, enter https://meet.google.com/. 2. Select the meeting from your list of scheduled events. 3. Click Join now. Note: Participants who join after the 5th do not chime and are automatically muted. Enter a meeting code or nickname: 1. In a web browser, enter https://meet.google.com. 2. Click Join or start a meeting. 3. Enter a meeting code or nickname. a. The meeting code is the string of letters at the end of the meeting link. You don't have to enter the hyphens. b. Enter your name in the “join meeting box”. This will assist others who are participating in knowing who you are. 4. Click Continue and then Join now. Resource from: https://support.google.com/ 1 Join with a meeting link URL Sometimes there isn’t enough time to schedule a meeting. With Google Meet, you can join an impromptu video meeting by clicking the meeting link URL sent to you in a text or email. 1. Click the meeting link sent to you in a chat message or email. 2. Follow the onscreen prompts to join the meeting. An existing participant might need to approve you if you try to join another organization’s meeting or don't have a Google Account. Join without a Google Account You don't need a Google Account to participate in Google Meet video meetings. -

U.S. Initiatives to Promote Global Internet Freedom: Issues, Policy, and Technology
U.S. Initiatives to Promote Global Internet Freedom: Issues, Policy, and Technology Patricia Moloney Figliola, Coordinator Specialist in Internet and Telecommunications Policy Casey L. Addis Analyst in Middle Eastern Affairs Thomas Lum Specialist in Asian Affairs January 3, 2011 Congressional Research Service 7-5700 www.crs.gov R41120 CRS Report for Congress Prepared for Members and Committees of Congress U.S. Initiatives to Promote Global Internet Freedom: Issues, Policy, and Technology Summary Modern means of communications, led by the Internet, provide a relatively inexpensive, open, easy-entry means of sharing ideas, information, pictures, and text around the world. In a political and human rights context, in closed societies when the more established, formal news media is denied access to or does not report on specified news events, the Internet has become an alternative source of media, and sometimes a means to organize politically. The openness and the freedom of expression allowed through blogs, social networks, video sharing sites, and other tools of today’s communications technology has proven to be an unprecedented and often disruptive force in some closed societies. Governments that seek to maintain their authority and control the ideas and information their citizens receive are often caught in a dilemma: they feel that they need access to the Internet to participate in commerce in the global market and for economic growth and technological development, but fear that allowing open access to the Internet potentially weakens their control over their citizens. The ongoing situation of Google in China is representative of these issues. Legislation now under consideration in the 111th Congress would mandate that U.S.