Bank Card Fraud in Spain1
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

How Mpos Helps Food Trucks Keep up with Modern Customers
FEBRUARY 2019 How mPOS Helps Food Trucks Keep Up With Modern Customers How mPOS solutions Fiserv to acquire First Data How mPOS helps drive food truck supermarkets compete (News and Trends) vendors’ businesses (Deep Dive) 7 (Feature Story) 11 16 mPOS Tracker™ © 2019 PYMNTS.com All Rights Reserved TABLEOFCONTENTS 03 07 11 What’s Inside Feature Story News and Trends Customers demand smooth cross- Nhon Ma, co-founder and co-owner The latest mPOS industry headlines channel experiences, providers of Belgian waffle company Zinneken’s, push mPOS solutions in cash-scarce and Frank Sacchetti, CEO of Frosty Ice societies and First Data will be Cream, discuss the mPOS features that acquired power their food truck operations 16 23 181 Deep Dive Scorecard About Faced with fierce eTailer competition, The results are in. See the top Information on PYMNTS.com supermarkets are turning to customer- scorers and a provider directory and Mobeewave facing scan-and-go-apps or equipping featuring 314 players in the space, employees with handheld devices to including four additions. make purchasing more convenient and win new business ACKNOWLEDGMENT The mPOS Tracker™ was done in collaboration with Mobeewave, and PYMNTS is grateful for the company’s support and insight. PYMNTS.com retains full editorial control over the findings presented, as well as the methodology and data analysis. mPOS Tracker™ © 2019 PYMNTS.com All Rights Reserved February 2019 | 2 WHAT’S INSIDE Whether in store or online, catering to modern consumers means providing them with a unified retail experience. Consumers want to smoothly transition from online shopping to browsing a physical retail store, and 56 percent say they would be more likely to patronize a store that offered them a shared cart across channels. -

PCI) PIN Transaction Security (PTS) Point of Interaction (POI
Payment Card Industry (PCI) PIN Transaction Security (PTS) Point of Interaction (POI) Modular Security Requirements Version 3.0 April 2010 Document Changes Date Version Description February 2010 3.x RFC version April 2010 3.0 Public release Payment Card Industry PTS POI Security Requirements v3.0 April 2010 Copyright 2010 PCI Security Standards Council LLC Page i Table of Contents Document Changes ..................................................................................................................... i About This Document ............................................................................................................... iv Purpose.....................................................................................................................................iv Scope of the Document.............................................................................................................iv Main Differences from Previous Version................................................................................... v Process Flow for PTS Approval ................................................................................................vi Foreword ................................................................................................................................... vii Evaluation Domains .................................................................................................................vii Device Management ................................................................................................................vii -

2011 Holiday Strategy Guide Part2
Holiday Coffee Outline Select your ten best customers/friends. Call and use this script……. How would you like to get anything you want from Mary Kay at Half Price? Well, it’s easy and it’s fun. Have a Holiday Shopping Coffee, Invite as many women as you would like and when we sell at least $200.00 you can order anything you want for half price! All you have to prepare is Coffee and Dessert! Set a Date and Time: Which would be better for you ________or______? How to display products…. Arrive with each holiday fragrance collection in a separate bags. Put them out in a festive bag or decorative box to display them. Have one display table with all items on it. Also have 3-4 gift ideas already made up to display. (Snowman Soup, Coffee and Cream, Kissable Lips etc.) Also have a small bowl with coffee beans for cleansing your nose between fragrances. When Guests Arrive….. Do Satin Hands on every guest. (Make sure you have Fragrance Free option available). Give each guest a pen, sales ticket, Wish List, Skin Care Profile & Look Book. Take each fragrance out of the individual bag and describe and romance it, one collection at a time. Explain fragrance layering and give prices. Have cotton balls sprayed and wrapped in netting so are not spraying every different fragrance into the air. Have a Gift with purchase offer for that event only. Very Important to say during your presentation: When you see something you would like, just write it on your sale ticket. -

Failing Function Codes, Failing Items, and Symbolic Frus
Power Systems Failing function codes, failing items, and symbolic FRUs IBM Power Systems Failing function codes, failing items, and symbolic FRUs IBM Note Before using this information and the product it supports, read the information in “Safety notices” on page v, “Notices” on page 283, the IBM Systems Safety Notices manual, G229-9054, and the IBM Environmental Notices and User Guide, Z125–5823. This edition applies to IBM Power Systems™ servers that contain the POWER9™ processor and to all associated models. © Copyright IBM Corporation 2018. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Safety notices ................................. v Failing function codes, failing items, and symbolic FRUs .............. 1 Failing function codes ................................ 1 Failing items .................................. 158 Symbolic FRUs .................................. 177 Notices ................................... 283 Accessibility features for IBM Power Systems servers ..................... 284 Privacy policy considerations ............................. 285 Trademarks ................................... 286 Electronic emission notices .............................. 286 Class A Notices................................. 286 Class B Notices................................. 290 Terms and conditions................................ 293 © Copyright IBM Corp. 2018 iii iv Safety notices Safety notices may be printed throughout this guide: v DANGER notices -

TT8800 OPT – Installation and Service Manual
TT8800 Outdoor Payment Terminal Installation and Service Manual November 2020 * TT8800 OPT shown as mounted inside optional supporting cabinet Rugged. Purposeful. Effective. For any questions, technical or otherwise, please contact us: ttfuel.com [email protected] +61 8 8215 5000 For the latest documentation and product updates, visit our Resource Centre: ttfuel.com/resources Table of Contents 1. Introduction................................................................................................................................ 1 1.1 Site Specific Information ........................................................................................................................ 1 1.2 TT8800 OPT Specifications .................................................................................................................. 1 1.3 Referenced Documents ......................................................................................................................... 3 2. Installation ................................................................................................................................. 4 2.1 Standards and Safety............................................................................................................................ 4 2.2 Applicable Standards ............................................................................................................................ 4 2.3 Safety Issues .......................................................................................................................................... -

Liebert® Datamate™ System Design Catalog TABLE of CONTENTS
Liebert® DataMate™ System Design Catalog 1.5-ton to 3-ton (5-kW to 10.5-kW) Capacity, Air, Water/Glycol, Chilled Water; 50 and 60 Hz The information contained in this document is subject to change without notice and may not be suitable for all applications. While every precaution has been taken to ensure the accuracy and completeness of this document, Vertiv assumes no responsibility and disclaims all liability for damages resulting from use of this information or for any errors or omissions. Refer to other local practices or building codes as applicable for the correct methods, tools, and materials to be used in performing procedures not specifically described in this document. The products covered by this instruction manual are manufactured and/or sold by Vertiv. This document is the property of Vertiv and contains confidential and proprietary information owned by Vertiv. Any copying, use or disclosure of it without the written permission of Vertiv is strictly prohibited. Names of companies and products are trademarks or registered trademarks of the respective companies. Any questions regarding usage of trademark names should be directed to the original manufacturer. Technical Support Site If you encounter any installation or operational issues with your product, check the pertinent section of this manual to see if the issue can be resolved by following outlined procedures. Visit https://www.Vertiv.com/en-us/support/ for additional assistance. Vertiv | Liebert® DataMate™ System Design Catalog TABLE OF CONTENTS 1 Introduction 1 1.1 Designed -

Gift Product-4Page Catalog Copy
Customer Order Sheet Bill To: Address: Meaningful Gifts City, St, Zip: Ph ( ) Fax ( ) 1-866-ZORBITZ Buyers Name: E-mail: that Give Back 1-866-967-2489 Ship To: 323-571-4944 Address: Fax: 323-571-0866 City, St, Zip: www.wholesale.zorbitz.net Ship Date: [email protected] Credit Card: Type: Number: P.O. Number Exp: 3 Digit: Bill Address: Sales Rep Item Description Qty Cost Total Item Description Qty Cost Total Subtotal __________ Total US$ __________ Special Instructions Minimum order US $100, reorder US $75. We accept Visa, MasterCard, and American Express. Initial orders must be paid prior to shipping. Customers will be charged on shipment of items. Back orders will be shipped within 90 days. There are no refunds. Exchanges and merchandise credit only. Credits are valid for 90 days. By signing here below buyer acknowledges the terms and conditions and is therefore responsible for payment. Visit www.wholesale.zorbitz.net for details Buyer: Date: l Gemston 12 Lucky Magnetic Bracelets ea es Wine Charm Treasuresbracelets R Decals $3.99 each From The Earth $4.50 each From The Water $1.50 each Identify your Glass Stackable NEW Reusable! Generic UPC R s $2.50 each #600-17250 Generic UPC #1390-16000 eal Pearl #2217 35 pc Display 36pc Display 8 11200 01391 8 Generic UPC 7 Styles, 5 of each 6 Styles, 6 of each #2750-17700 NEW 8 11200 01390 1 36 pc Display Additional Styles Available Wax Seal Bracelets recycled CelebrateNecklaces $3.99 each Bangles $4.50 each energybracelet Generic UPC NEW #2700-16000 36 pc Display 6 of each 6 Styles, $4.50 -

AS/400 ASCII Work Station Reference Version 3 Publication No
AS/400 SA41-3130-00 ASCII Work Station Reference Version 3 IBM AS/400 SA41-3130-00 ASCII Work Station Reference Version 3 Take Note! Before using this information and the product it supports, be sure to read the general information under “Notices” on page xvii. First Edition (September 1994) This edition applies to the licensed program IBM Operating System/400, (Program 5763-SS1), Version 3 Release 1 Modification 0, and to all subsequent releases and modifications until otherwise indicated in new editions. Make sure you are using the proper edition for the level of the product. | Order publications through your IBM representative or the IBM branch serving your locality. If you live in the United States, Puerto | Rico, or Guam, you can order publications through the IBM Software Manufacturing Company at 800+879-2755. Publications are not stocked at the address given below. A form for reader comments is provided at the back of this publication. If the form has been removed, you can mail your comments to: Attn Department 245 IBM Corporation 3605 Highway 52 N Rochester, MN 55901-9986 USA or you can fax your comments to: United States and Canada: 800+937-3430 Other countries: (+1)+507+253-5192 | If you have access to Internet, you can send your comments electronically to [email protected]; IBMMAIL, to | ibmmail(usib56rz). When you send information to IBM, you grant IBM a non-exclusive right to use or distribute the information in any way it believes appropriate without incurring any obligation to you or restricting your use of it. -
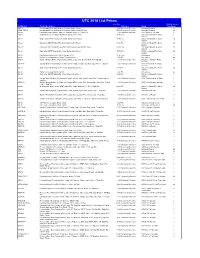
2018 GE Security Price Book
UTC 2018 List Prices List Price Published Lead Part Number Product Description Reference Group Time (Days) 1005-N Mini-Magnapull Pull-Apart Magnetic Contact, Surface Mount. 15.04 Sensors & Detectors Magnapull Contacts 3 1005N-10PKG Mini-Magnapull Pull-Apart Magnetic Contact, Surface Mount. 10-Pack 157.90 Sensors & Detectors Magnapull Contacts 20 1015-N Recessed Contact w/Wire Leads, 1/4” Diameter, White, 3/8” Gap Size 7.83 Sensors & Detectors 1015 Series 1/4” w/Leads 3 103-20 Single Action (SPST) Manual Fire Alarm Station w/Hex Reset 34.96 Fire 103 Series Manual Fire Alarm 3 Stations 103-21 Single Action (DPST) Manual Fire Alarm Station w/Hex Reset 49.80 Fire 103 Series Manual Fire Alarm 20 Stations 103-22 Dual Action (SPST) Manual Fire Alarm Station w/Hex Reset 51.22 Fire 103 Series Manual Fire Alarm 20 Stations 103-22S Dual Action (SPST) Manual Fire Alarm Station w/Hex Reset and NY Stripe 69.68 Fire 103 Series Manual Fire Alarm 20 Stations 103-23 Dual Action (DPST) Manual Fire Alarm Station w/Hex Reset 59.72 Fire 103 Series Manual Fire Alarm 20 Stations 103-25 Red Surface Back Box for 103-20 Through 103-42 25.56 Fire Accessories 3 103-26 Replacement Glass Rod for 103-20 Through 103-60 5.70 Fire Accessories 20 1032-N Surface Miniature Flange Mount Contact w/Wire Leads, Closed Loop, White, 5/8” Gap Size 6.11 Sensors & Detectors 1032 Series Miniature Flange 3 w/Leads 1032W-N Surface Miniature Flange Mount Contact w/Wire Leads, Closed Loop, Wide Gap, White, 1” Gap Size 6.93 Sensors & Detectors 1032 Series Miniature Flange 3 w/Leads 103-31 Single Action (SPST) Manual Fire Alarm Station w/Key Reset 48.40 Fire 103 Series Manual Fire Alarm 20 Stations 103-36 Replacement Glass Rod for 103-31 4.26 Fire Accessories 20 103-42 Dual Action (SPST) Manual Fire Alarm Station w/Key Reset 56.46 Fire 103 Series Manual Fire Alarm 3 Stations 1035-N Surface Mount Miniature Self-Adhesive Contact w/Wire Leads, Closed Loop, White, Closed Loop. -

Determining the Causes of Accuvote Optical Scan Voting Terminal Memory Card Failures∗
Determining the Causes of AccuVote Optical Scan Voting Terminal Memory Card Failures∗ Tigran Antonyan Nicolas Nicolaou Alexander A. Shvartsman Therese Smith Computer Science & Engineering, University of Connecticut, Storrs, CT 06269, USA {tigran,nicolas,aas,tms08012}@engr.uconn.edu Abstract 1 Introduction Optical scan (OS) voting systems play an increasing role A number of reports in recent years documented security in the United States elections, with over 40 states deploy- and integrity vulnerabilities associated with electronic ing such systems. The AccuVote optical scanners (AV- election systems (e.g., [24,3, 19, 32, 34, 13, 14, 33, 10, OS) manufactured by ES&S account for over 20% of all 16, 17,7,8]). While it is extremely important to un- OS systems. OS systems typically use removable media derstand and mitigate the risks of misuse and tampering (cards) to provide election-specific programming to the with electronic voting systems, it is also important to en- scanners and to convey precinct election results for cen- sure that the systems are reliable, and when this is not tral tabulation. Several reports document occurrences of the case, to analyze the problems and develop solutions AV-OS memory card failures, with up to 15% of all cards leading to more dependable election systems. failing in some cases. Over 55% of the counties nationwide across more This paper reports on determining the causes of mem- than 40 states incorporated OS election systems for ory card failures that lead to complete loss of data from the November 2008 Presidential Elections, with over the card. An initial experimental analysis identified the 20% of those counties deploying the AccuVote Optical battery discharge as a significant part of the problem. -

Mastercard Rules 7 July 2016
MasterCard Rules 7 July 2016 BM Notices Notices Proprietary Rights The information contained in this document is proprietary and confidential to MasterCard International Incorporated, one or more of its affiliated entities (collectively “MasterCard”), or both. This material may not be duplicated, published, or disclosed, in whole or in part, without the prior written permission of MasterCard. Trademarks Trademark notices and symbols used in this document reflect the registration status of MasterCard trademarks in the United States. Please consult with the Global Customer Service team or the MasterCard Law Department for the registration status of particular product, program, or service names outside the United States. All third-party product and service names are trademarks or registered trademarks of their respective owners. Disclaimer MasterCard makes no representations or warranties of any kind, express or implied, with respect to the contents of this document. Without limitation, MasterCard specifically disclaims all representations and warranties with respect to this document and any intellectual property rights subsisting therein or any part thereof, including but not limited to any and all implied warranties of title, non-infringement, or suitability for any purpose (whether or not MasterCard has been advised, has reason to know, or is otherwise in fact aware of any information) or achievement of any particular result. Without limitation, MasterCard specifically disclaims all representations and warranties that any practice or implementation of this document will not infringe any third party patents, copyrights, trade secrets or other rights. Translation A translation of any MasterCard manual, bulletin, release, or other MasterCard document into a language other than English is intended solely as a convenience to MasterCard customers. -

Card Reader Device Kartenleseanordnung Ensemble De Lecture De Cartes
(19) TZZ Z__T (11) EP 2 075 771 B1 (12) EUROPEAN PATENT SPECIFICATION (45) Date of publication and mention (51) Int Cl.: of the grant of the patent: G07F 7/08 (2006.01) G07F 19/00 (2006.01) 01.07.2015 Bulletin 2015/27 (21) Application number: 08169169.3 (22) Date of filing: 14.11.2008 (54) Card reader device Kartenleseanordnung Ensemble de lecture de cartes (84) Designated Contracting States: • Colston, Scott DE ES FR GB HU IT Dundee, Tayside DD4 7HB (GB) (30) Priority: 20.12.2007 US 4358 (74) Representative: MacLeod, Roderick William NCR Limited (43) Date of publication of application: Intellectual Property Section 01.07.2009 Bulletin 2009/27 Discovery Centre 3 Fulton Road (73) Proprietor: NCR Corporation Dundee Tayside, DD2 4SW (GB) Duluth, GA 30096 (US) (56) References cited: (72) Inventors: WO-A-01/84486 US-A- 5 929 413 • Clark, Barrie US-A1- 2005 116 036 US-A1- 2007 108 278 Dundee, Tayside DD2 5PJ (GB) Note: Within nine months of the publication of the mention of the grant of the European patent in the European Patent Bulletin, any person may give notice to the European Patent Office of opposition to that patent, in accordance with the Implementing Regulations. Notice of opposition shall not be deemed to have been filed until the opposition fee has been paid. (Art. 99(1) European Patent Convention). EP 2 075 771 B1 Printed by Jouve, 75001 PARIS (FR) 1 EP 2 075 771 B1 2 Description the displacement exceeds a predetermined threshold. This may be obtained indirectly, for example, by ascer- [0001] The present invention relates to a card reader taining if the intensity measured by an optical sensor is device.