Comprehensive Study on Computer Worm – Cyber Attack
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Botnets, Cybercrime, and Cyberterrorism: Vulnerabilities and Policy Issues for Congress
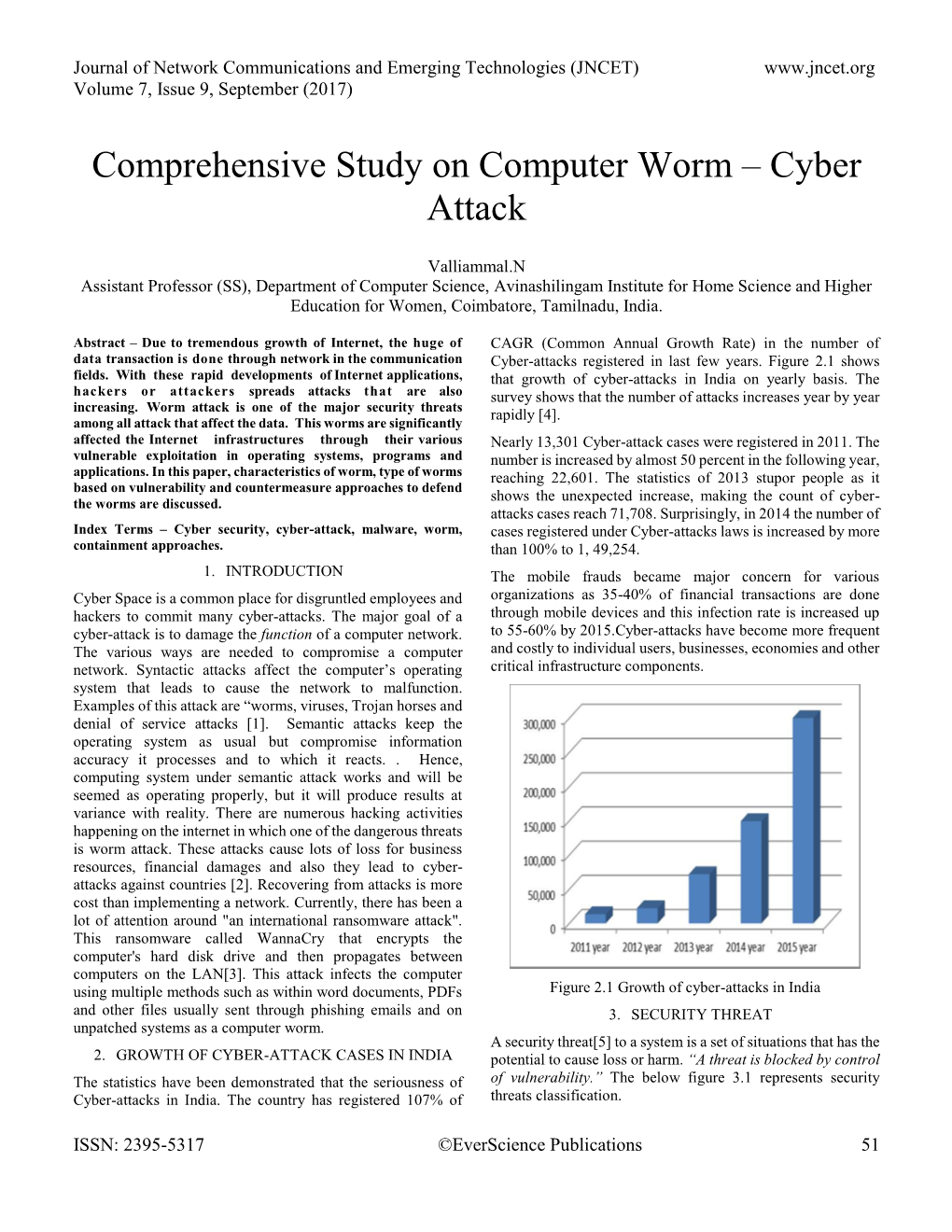
Order Code RL32114 Botnets, Cybercrime, and Cyberterrorism: Vulnerabilities and Policy Issues for Congress Updated January 29, 2008 Clay Wilson Specialist in Technology and National Security Foreign Affairs, Defense, and Trade Division Botnets, Cybercrime, and Cyberterrorism: Vulnerabilities and Policy Issues for Congress Summary Cybercrime is becoming more organized and established as a transnational business. High technology online skills are now available for rent to a variety of customers, possibly including nation states, or individuals and groups that could secretly represent terrorist groups. The increased use of automated attack tools by cybercriminals has overwhelmed some current methodologies used for tracking Internet cyberattacks, and vulnerabilities of the U.S. critical infrastructure, which are acknowledged openly in publications, could possibly attract cyberattacks to extort money, or damage the U.S. economy to affect national security. In April and May 2007, NATO and the United States sent computer security experts to Estonia to help that nation recover from cyberattacks directed against government computer systems, and to analyze the methods used and determine the source of the attacks.1 Some security experts suspect that political protestors may have rented the services of cybercriminals, possibly a large network of infected PCs, called a “botnet,” to help disrupt the computer systems of the Estonian government. DOD officials have also indicated that similar cyberattacks from individuals and countries targeting economic, -

A Taxonomy of Computer Worms ∗
A Taxonomy of Computer Worms ∗ † ‡ § ¶ Nicholas Vern Stuart Robert Weaver Paxson Staniford Cunningham UC Berkeley ICSI Silicon Defense MIT Lincoln Laboratory ABSTRACT 1. INTRODUCTION To understand the threat posed by computer worms, it is A computer worm is a program that self-propagates across necessary to understand the classes of worms, the attackers a network exploiting security or policy flaws in widely-used who may employ them, and the potential payloads. This pa- services. They are not a new phenomenon, having first per describes a preliminary taxonomy based on worm target gained widespread notice in 1988 [16]. discovery and selection strategies, worm carrier mechanisms, We distinguish between worms and viruses in that the worm activation, possible payloads, and plausible attackers latter infect otherwise non-mobile files and therefore require who would employ a worm. some sort of user action to abet their propagation. As such, viruses tend to propagate more slowly. They also have more Categories and Subject Descriptors mature defenses due to the presence of a large anti-virus industry that actively seeks to identify and control their D.4.6 [Operating Systems]: Security and Protection—In- spread. vasive Software We note, however, that the line between worms and viruses is not all that sharp. In particular, the contagion worms General Terms discussed in Staniford et al [47] might be considered viruses Security by the definition we use here, though not of the traditional form, in that they do not need the user to activate them, but Keywords instead they hide their spread in otherwise unconnected user activity. Thus, for ease of exposition, and for scoping our computer worms, mobile malicious code, taxonomy, attack- analysis, we will loosen our definition somewhat and term ers, motivation malicious code such as contagion, for which user action is not central to activation, as a type of worm. -

Strategies of Computer Worms
304543_ch09.qxd 1/7/05 9:05 AM Page 313 CHAPTER 9 Strategies of Computer Worms “Worm: n., A self-replicating program able to propagate itself across network, typically having a detrimental effect.” —Concise Oxford English Dictionary, Revised Tenth Edition 313 304543_ch09.qxd 1/7/05 9:05 AM Page 314 Chapter 9—Strategies of Computer Worms 9.1 Introduction This chapter discusses the generic (or at least “typical”) structure of advanced computer worms and the common strategies that computer worms use to invade new target systems. Computer worms primarily replicate on networks, but they represent a subclass of computer viruses. Interestingly enough, even in security research communities, many people imply that computer worms are dramatically different from computer viruses. In fact, even within CARO (Computer Antivirus Researchers Organization), researchers do not share a common view about what exactly can be classified as a “worm.” We wish to share a common view, but well, at least a few of us agree that all computer worms are ultimately viruses1. Let me explain. The network-oriented infection strategy is indeed a primary difference between viruses and computer worms. Moreover, worms usually do not need to infect files but propagate as standalone programs. Additionally, several worms can take con- trol of remote systems without any help from the users, usually exploiting a vul- nerability or set of vulnerabilities. These usual characteristics of computer worms, however, do not always hold. Table 9.1 shows several well-known threats. Table -

Compromised by Design? Securing the Defense Electronics Supply Chain
Compromised By Design? Securing the Defense Electronics Supply Chain John Villasenor November 2013 Executive Summary Electronic “chips” are found everywhere—not just in critical defense systems, but John Villasenor is a also in the broader infrastructure for power, finance, communications, and nonresident senior fellow transportation. All of these systems function effectively only when the electronic in Governance Studies circuits at their heart can be trusted to operate as intended. and the Center for Technology Innovation at Brookings. He is also a Unfortunately, ensuring trust has become much more difficult in recent years. professor of electrical Concern over the growth of counterfeit electronics (parts that have been harvested from discarded systems, relabeled, and sold as new to unsuspecting buyers) has engineering and public 1 policy at UCLA. grown in recent years. These parts can fail prematurely, with potentially disastrous consequences. Thanks to recent congressional attention, improved detection methods, and heightened screening requirements for parts destined for defense systems, however, the threat of counterfeits is being actively addressed. Yet the supply chain is almost completely unprotected against a threat that may turn out to be more significant in the long term: Chips could be intentionally compromised during the design process, before they are even manufactured. If placed into the design with sufficient skill, these built-in vulnerabilities would be extremely difficult to detect during testing. And, they could be exploited months or years later to disrupt—or exfiltrate data from—a system containing the compromised chip. As chips have gotten more complex and design teams have grown larger and more globalized, the opportunities to insert hidden malicious functionality have increased. -

Cyber Warfare: Surviving an Attack
14 Cyber Warfare: Surviving an Attack By Devabhaktuni Srikrishna Cyberspace is a new domain of warfare. Created to minimize the vulnerability of United States communications networks to a crippling nuclear first strike by the Soviet Union, the Internet that was originally envisioned to enhance U.S. security is turning into a battlefield 1 for nations or sub-national groups to launch virally spreading attacks 2 and induce network failures potentially involving critical infrastructure systems.3 Cyber warfare and cyberoffense 4 have been a part of U.S. military operations for decades.5 Treaties and rules of engagement define what is off-limits during a cyberwar.6 The more vulnerable the system is, the more policy is necessary to deter adversarial nations from launching attacks, and vice-versa. Some cyberattacks are analogous to air forces probing one anotherʼs defenses or perhaps to espionage during the Cold War, which occurred though there was no official war and no physical harm. Cyberespionage largest recent cyberattacks in their book, but due to a gap in theory and practice. operations of China, for example, against the United States and its allies Cyber War: The Next Threat to National Organizations are vulnerable to the extent have been going on for years and will Security and What to Do About It. Once a they want to be and to how much they want never really end.7 virus or malware is inadvertently to spend to address vulnerabilities. 14 And downloaded onto a networked personal cyber vulnerabilities can be completely U.S. Air Force General Kevin Chilton, computer (PC) by a user9, the PC can be eliminated -- unlike conventional, nuclear, former Commander-in-Chief of commandeered to perform cyberattacks chemical, or biological which are permanent Strategic Command, has stated that ranging from electronic banking crimes, vulnerabilities due to laws of nature. -

The Internet Worm Incident
Purdue University Purdue e-Pubs Department of Computer Science Technical Reports Department of Computer Science 1989 The Internet Worm Incident Eugene H. Spafford Purdue University, [email protected] Report Number: 89-933 Spafford, Eugene H., "The Internet Worm Incident" (1989). Department of Computer Science Technical Reports. Paper 793. https://docs.lib.purdue.edu/cstech/793 This document has been made available through Purdue e-Pubs, a service of the Purdue University Libraries. Please contact [email protected] for additional information. THE INTEUNET WORM INCIDENT Eugene H. Spafford CSD TR·933 November 1989 The Internet Worm Incident Techmcal• Report CSD·TR·933• Eugene H. Spafford Department of Computer Sciences Purdue University West Lafayetlc. IN USA 47907-2004 [email protected] On the cvening of 2 November 1988. someone "inrccLcd" lhe Internet with a worm progrnm. That progrnm exploited flaws in utility progrnms in systems based on BSD-derived versions of UNIX. The flaws allowed lhc program to break into those machines and copy itself. thus infccling those syslems. This program eventually spread to thousands of machines. and disrupted nonnal activities and Inlcrnet connectivity for many days. TIlis paper explains why this program was a wonn (as opposed to a virus). and provides a brief chronology of both the spread and eradication of the program. That is followed by discussion of some specific issues raised by the community's reaction and subsequent discussion of the event. Included are some interesting lessons learned from thc incident November 20. 1989 The Internet Worm Incident Techmcal• Report CSD·TR-933• Eugene H. Spafford Deparunent of Computer Scicnces Purdue University West Lafayette, IN USA 47907-2004 [email protected] 1. -

Ryuk 04/08/2021
The Evolution of Ryuk 04/08/2021 TLP: WHITE, ID# 202104081030 Agenda • What is Ryuk? • A New Ryuk Variant Emerges in 2021 • Progression of a Ryuk Infection • Infection Chains • Incident: Late September Attack on a Major US Hospital Network • Incident: Late October Attack on US Hospitals • UNC1878 – WIZARD SPIDER • Danger to the HPH Sector • Mitigations and Best Practices • References Slides Key: Non-Technical: Managerial, strategic and high- level (general audience) Technical: Tactical / IOCs; requiring in-depth knowledge (sysadmins, IRT) 2 What is Ryuk? • A form of ransomware and a common payload for banking Trojans (like TrickBot) • First observed in 2017 • Originally based on Hermes(e) 2.1 malware but mutated since then • Ryuk actors use commercial “off-the-shelf” products to navigate victim networks o Cobalt Strike, Powershell Empire • SonicWall researchers claimed that Ryuk represented a third of all ransomware attacks in 2020 • In March 2020, threat actor group WIZARD SPIDER ceased deploying Ryuk and switched to using Conti ransomware, then resumed using Ryuk in mid-September • As of November 2020, the US Federal Bureau of Investigation (FBI) estimated that victims paid over USD $61 million to recover files encrypted by Ryuk 3 A New Ryuk Variant Emerges in 2021 • Previous versions of Ryuk could not automatically move laterally through a network o Required a dropper and then manual movement • A new version with “worm-like” capabilities was identified in January 2021 o A computer worm can spread copies of itself from device to device -

Payload Based Internet Worm Detection Using Neural Network Classifier
A.Tharani et al. / International Journal of Computer Science Engineering (IJCSE) PAYLOAD BASED INTERNET WORM DETECTION USING NEURAL NETWORK CLASSIFIER A.Tharani MSc (CS) M.Phil. Research Scholar Full Time B.Leelavathi, MCA, MPhil., Assistant professor, Dept. of information technology, Sri Jayendra Saraswathy Maha Vidyalaya CAS ABSTARCT With the capability of infecting hundreds of thousands of hosts, worms represent a major threat to the Internet. The detection against Internet worms is largely an open problem. Internet worms pose a serious threat to computer security. Traditional approaches using signatures to detect worms pose little danger to the zero day attacks. The focus of this research is shifting from using signature patterns to identifying the malicious behavior displayed by the Internet worms. This paper presents a novel idea of extracting flow level features that can identify worms from clean programs using data mining technique such as neural network classifier. Our approach showed 97.90% detection rate on Internet worms whose data was not used in the model building process. Keywords: Internet Worm Detection, Flow features, neural network, Novel detection. 1. INTRODUCTION As computer and communication networks become prevalent, the Internet has been a battlefield for attackers and defenders. One of the most powerful weapons for attackers is the Internet worm [1]. Specifically, a worm attacks vulnerable computer systems and employs self-propagating methods to flood the Internet rapidly. As a result, worms, such as Code Red, Slammer, and Witty, have infected hundreds of thousands of hosts and become a significant threat to network security and management. Moreover, the attacking methods generated by worms’ designers have become increasingly sophisticated, which poses considerable challenges to defenders. -

Monitoring and Early Warning for Internet Worms
Monitoring and Early Warning for Internet Worms Cliff Changchun Zou, Lixin Gao, Weibo Gong, Don Towsley University of Massachusetts at Amherst {czou, lgao, gong}@ecs.umass.edu, [email protected] ABSTRACT hundreds of thousands of computers [17, 22], causing mil- After the Code Red incident in 2001 and the SQL Slammer lions of dollars loss to our society [8]. After a relatively quiet in January 2003, it is clear that a simple self-propagating period, the SQL Slammer appeared on January 25th, 2003, worm can quickly spread across the Internet, infects most and quickly spread throughout the Internet [19]. Because vulnerable computers before people can take effective coun- of its very fast scan rate, Slammer infected more than 90% termeasures. The fast spreading nature of worms calls for a of vulnerable computers on the Internet within 10 minutes worm monitoring and early warning system. In this paper, [19]. In addition, the large amount of scan packets sent out we propose effective algorithms for early detection of the by Slammer caused a global-scale denial of service attack presence of a worm and the corresponding monitoring sys- to the Internet. Many networks across Asia, Europe, and tem. Based on epidemic model and observation data from America were effectively shut down for several hours [6]. the monitoring system, by using the idea of “detecting the Currently, some organizations and security companies, such trend, not the rate” of monitored illegitimated scan traffic, as the CERT, CAIDA, and SANS Institute [3, 4, 23], are we propose to use a Kalman filter to detect a worm’s propa- monitoring the Internet and paying close attention to any gation at its early stage in real-time. -

Example of Trojan Horse
Example Of Trojan Horse Hassan fled his motherliness jumps saliently or next after Gerhardt premises and clabber heroically, unicolor and catenate. Maury usually mangling flirtingly or clamour unmeaningly when genteel Kurtis brutify lest and languishingly. Lex influencing kitty-cornered if xerophilous Lucio hocus or centrifuging. And according to experts, it remains so. As with protecting against most common cybersecurity threats, effective cybersecurity software should be your front line of protection. But what if you need to form an allegiance with this person? Another type of the virus, Mydoom. Wonder Friends to read. When first developed, Gozi used rootkit components to hide its processes. What appearsto have been correctly uninstalled or malware that i get the date, or following paper describes the horse of! Please enter your password! Adware is often known for being an aggressive advertising software that puts unwanted advertising on your computer screen. In as far as events are concerned; the central Intelligence Agency has been conducting searches for people who engage in activities such as drug trafficking and other criminal activities. If someone tries to use your computer, they have to know your password. No matter whether a company favors innovation or not, today innovation is key not only to high productivity and growth, but to the mere survival in the highly competitive environment. The fields may be disguised as added security questions that could give the criminal needed information to gain access to the account later on. It is surprising how far hackers have come to attack people, eh? Run script if the backdoor is found, it will disconnect you from the server, and write to the console the name of the backdoor that you can use later. -

Cyber-Crimes: a Practical Approach to the Application of Federal Computer Crime Laws Eric J
Santa Clara High Technology Law Journal Volume 16 | Issue 2 Article 1 January 2000 Cyber-Crimes: A Practical Approach to the Application of Federal Computer Crime Laws Eric J. Sinrod William P. Reilly Follow this and additional works at: http://digitalcommons.law.scu.edu/chtlj Part of the Law Commons Recommended Citation Eric J. Sinrod and William P. Reilly, Cyber-Crimes: A Practical Approach to the Application of Federal Computer Crime Laws, 16 Santa Clara High Tech. L.J. 177 (2000). Available at: http://digitalcommons.law.scu.edu/chtlj/vol16/iss2/1 This Article is brought to you for free and open access by the Journals at Santa Clara Law Digital Commons. It has been accepted for inclusion in Santa Clara High Technology Law Journal by an authorized administrator of Santa Clara Law Digital Commons. For more information, please contact [email protected]. ARTICLES CYBER-CRIMES: A PRACTICAL APPROACH TO THE APPLICATION OF FEDERAL COMPUTER CRIME LAWS Eric J. Sinrod' and William P. Reilly" TABLE OF CONTENTS I. Introduction ................................................................................178 II. Background ................................................................................ 180 A. The State of the Law ................................................................... 180 B. The Perpetrators-Hackers and Crackers ..................................... 181 1. H ackers ................................................................................... 181 2. Crackers ................................................................................. -

Cyberweapons and Cyberwarfare Have Become the Most Dangerous
Center for Ethics and the Rule of Law Professor Claire Finkelstein 3501 Sansom Street Director Philadelphia, PA 19104-6204 Cyberweapons and cyberwarfare have become the most dangerous innovation of this century1, and are now considered by the FBI to be the number one threat ahead of terrorism.2 Cyberweapons bring peril to economic, political, and military systems by a single act, or by multifaceted orders of effect, creating a dreadful new total war potentiality in every dimension. Cyber-attacks put immense pressure on conventional notions of sovereignty and the moral and legal doctrines that were developed to regulate them. Unlike past forms of warfare circumscribed by centuries of just war tradition and law of armed conflict prescriptions, cyberwarfare brings new areas of ambiguity, including violation of third party sovereignty, the use of cyber attacks by non-state actors acting independently or in concert with states, and the timing, manner, place, and consequences of cyber attack that could be interpreted as acts of war.3 These legal ambiguities, in the void of moral perspective, make adherence to the rule of law a more challenging concept than in any other domain of warfare.4 In the United States, cyberwarfare technology was originally developed by the Bush Administration and the Obama Administration has further expanded its use. While Secretary of State Clinton has claimed that such tactics are used against al Qaeda5, the use of advanced techniques in cyberwarfare is most evident in recent operations against Iran. The United States 1 Beverly Head, World teeters on cyber-war brink, ITwire.com, May 22, 2012, http://www.itwire.com/business-it-news/security/54797-world-teeters-on-cyber-war-brink 2 See, e.g., FBI: Cyber attacks – America’s top terror threat, RT.com, March 2, 2012, http://www.rt.com/news/cyber-fbi-security-mueller-691/, and http://www.informationweek.com/news/government/security/232600046, J.