Download Date 24/09/2021 12:36:34
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

NORSOK STANDARD R-002 Edition 2, September 2012
NORSOK STANDARD R-002 Edition 2, September 2012 Lifting equipment This NORSOK standard is developed with broad petroleum industry participation by interested parties in the Norwegian petroleum industry and is owned by the Norwegian petroleum industry represented by The Norwegian Oil Industry Association (OLF) and The Federation of Norwegian Industry. Please note that whilst every effort has been made to ensure the accuracy of this NORSOK standard, neither OLF nor The Federation of Norwegian Industry or any of their members will assume liability for any use thereof. Standards Norway is responsible for the administration and publication of this NORSOK standard. Standards Norway Telephone: + 47 67 83 86 00 Strandveien 18, P.O. Box 242 Fax: + 47 67 83 86 01 N-1326 Lysaker Email: [email protected] NORWAY Website: www.standard.no/petroleum Copyrights reserved Foreword 3 Introduction 3 1 Scope 4 2 Normative and informative references 4 2.1 Normative references 4 2.2 Informative references 8 3 Terms, definitions and abbreviations 8 3.1 Terms and definitions 8 3.2 Abbreviations 13 4 General safety requirements 13 4.1 Safety 13 4.2 Fitness for use 13 4.3 Reliability and availability 14 4.4 Principle of safety integration 14 4.5 Inherently safe design measures 14 4.6 Safeguarding and complementary protective measures 14 4.7 Information for use 14 4.8 Strength proportion 14 4.9 Maintenance 15 4.10 Quality management system 15 4.11 Risk assessment 15 4.12 Risk reduction 17 4.13 Documentation of risk assessment 17 4.14 Verification 18 4.15 Qualification -

Standards News Late August 2014 Volume 18, Number 16 Table of Contents Uno, Dos, Tres Documentos Para Revisión Pública
PLASA Standards News Late August 2014 Volume 18, Number 16 Table of Contents Uno, dos, tres documentos para revisión pública.............................................................................................1 Please Donate to the TSP................................................................................................................................ 2 Fifteen Minutes and 36 Seconds of Fame........................................................................................................2 What's an American National Standard anyway?.............................................................................................2 WTO Technical Barrier to Trade Notifications...................................................................................................2 Chile Notification CHL/278............................................................................................................................ 2 Ecuador Notification ECU/71/ECU (ECU/71 , Add.1 , Add.2 , Add.3 , ).........................................................3 Ecuador Notification ECU/226/ECU (ECU/226 )...........................................................................................3 Taiwan Economy Notification TPKM/170.......................................................................................................3 ANSI Public Review Announcements...............................................................................................................4 Due 22 September 2014.............................................................................................................................. -

Foreword Introduction 1 Scope
9/10/2016 ISO 6385:2016(en), Ergonomics principles in the design of work systems Foreword ISO (the International Organization for Standardization) is a worldwide federation of national standards bodies (ISO member bodies). The work of preparing International Standards is normally carried out through ISO technical committees. Each member body interested in a subject for which a technical committee has been established has the right to be represented on that committee. International organizations, governmental and nongovernmental, in liaison with ISO, also take part in the work. ISO collaborates closely with the International Electrotechnical Commission (IEC) on all matters of electrotechnical standardization. The procedures used to develop this document and those intended for its further maintenance are described in the ISO/IEC Directives, Part 1. In particular the different approval criteria needed for the different types of ISO documents should be noted. This document was drafted in accordance with the editorial rules of the ISO/IEC Directives, Part 2 (see www.iso.org/directives). Attention is drawn to the possibility that some of the elements of this document may be the subject of patent rights. ISO shall not be held responsible for identifying any or all such patent rights. Details of any patent rights identified during the development of the document will be in the Introduction and/or on the ISO list of patent declarations received (see www.iso.org/patents). Any trade name used in this document is information given for the convenience of users and does not constitute an endorsement. For an explanation on the meaning of ISO specific terms and expressions related to conformity assessment, as well as information about ISO's adherence to the WTO principles in the Technical Barriers to Trade (TBT) see the following URL: Foreword Supplementary information. -

Best Practice Human Factors Guidance for Control Room/HMI Design
Highways Consultancy Group - Highways Research Group Best Practice Human Factors Guidance for Control Room/HMI Design Contract Reference: 2/1308 Task Reference: 166(1308)MOTT Project Sponsor: Stuart White Date: November 2010 Executive Summary Control room, plant and equipment design can have a huge impact on human performance. Designing tasks, equipment and work stations to suit the user can reduce human error, accidents and ill-health. Failure to observe human factors principles can have serious consequences for individuals and for the whole organisation. Effective consideration of human factors will make work safer, healthier and more productive. The fundamental and consistent philosophy of human factors is to ensure that the human element, or user, is of principle concern within the design process. This approach promotes the inclusion of user (and operator) needs, capabilities, limitations and goals into the design process. This document contains guidance to summarise the best practice human factors approach to system/product design and development, within the general project lifecycle, in order to provide support to Highways Agency in creating more cost effective and usable designs. This guidance should prove useful to both Highways Agency project sponsors/managers and human factors specialists involved in Highways Agency system/product design and development projects. This document also contains a simple flowchart and checklist to allow the reader to determine whether the guidance is relevant to their project, and if so, which parts of the guidance should be focused on. The guidance presented in this document provides some simple steps that you can include within the project plan and supports the reader in this through raising a number of questions for consideration. -

STAATSCOURANT 2016 Officiële Uitgave Van Het Koninkrijk Der Nederlanden Sinds 1814
Nr. 59791 10 november STAATSCOURANT 2016 Officiële uitgave van het Koninkrijk der Nederlanden sinds 1814. Nieuwe normen NEN Overzicht van nieuwe publicaties van het Nederlands Normalisatie-Instituut, inclusief de Europese normen, in de periode van 10 oktober 2016 tot en met 3 november 2016. De normbladen kunnen worden besteld bij NEN-Klantenservice, tel. 015-2690391, waar men ook met vragen terecht kan. Tevens kunnen de genoemde normen via internet besteld worden (www.nen.nl). Correspondentieadres: Postbus 5059, 2600 GB Delft. Document number Title AgroFood & Consument NEN-EN-ISO 11210:2016 en Sieraden – Bepaling van het platinagehalte in platinalegeringen voor sieraden – Gravimetrische methode na precipitatie van diammoniumhexachloroplatinaat NEN-EN-ISO 11426:2016 en Sieraden – Bepaling van het goudgehalte in goudlegeringen voor sieraden – Cupel- leermethode (gloeiproef) NEN-EN-ISO 11427:2016 en Sieraden – Bepaling van het zilvergehalte in zilverlegeringen voor sieraden – Volumetrische (potentiometrische) methode met gebruik van kaliumbromide NEN-EN-ISO 11490:2016 en Sieraden – Bepaling van het palladiumgehalte in palladiumlegeringen voor sieraden – Gravimetrische methode met dimethylglyoxime NEN-EN-ISO 11494:2016 en Sieraden – Bepaling van het platinagehalte in platinalegeringen voor sieraden – ICP-OES methode met yttrium als intern standaardelement NEN-EN-ISO 11495:2016 en Sieraden – Bepaling van het palladiumgehalte in palladiumlegeringen voor sieraden – ICP-OES methode met yttrium als intern standaardelement NEN-EN 12945:2014+A1:2016 en Kalkmeststoffen – Bepaling van de neutraliserende waarde – Titrimetrische methode NEN-EN 13451-1:2011+A1:2016 en Zwembaduitrusting – Deel 1: Algemene veiligheidseisen en beproevingsmethoden NEN-EN 13451-11:2016 Ontw. en Zwembaduitrusting – Deel 11: Aanvullende specifieke veiligheidseisen en beproe- vingsmethoden voor beweegbare zwembadbodems en beweegbare schotten Commentaar voor: 2016-12-12 NEN-EN 14974:2016 Ontw. -

D2.1 – Dynamic Worker Model
D2.1 – Dynamic worker model D2.1 –Dynamic worker model Empowering and Participatory Adap- tation of Factory Automation to Fit for Workers Abstract Smart factories are characterized by increasing automation and increasing customization. In these dynamic environments flexible and adaptive work organization is crucial, both for productivity and work satisfaction. The Factory2Fit project will support this development by developing adaptation solutions with which people with different skills, capabilities and preferences can be engaged, motivated and pro- ductive members of the work community in manufacturing industries. This deliverable describes the development of a work-related abstract profile of an employee, called Worker Model, and the development of a more dynamic worker model, Adaptive Worker Model. These models include worker characteristics and their relations with task-related, machine-related and contextual characteristics, respectively. Methodologies, standards and theories for user mod- elling development are also introduced in this deliverable. Alongside, this document provides a fur- ther analysis of the wearable measurement equipment that can be used for worker monitoring and the online worker monitoring and off-line measurements acquired from these devices. These meas- urements will be used for the definition of worker characteristics. Furthermore, an analysis of data storage mechanism that will be developed is provided. Keywords: Used Model standards and methodologies, Worker Model, Adaptive Worker Model, worker char- acteristics, -

NORSOK STANDARD R-002 Draft Edition 2, June 2011
NORSOK STANDARD R-002 Draft Edition 2, June 2011 Lifting equipment WARNING The hearing period for this standard is closed and the document is currently being updated based upon the comments that have been received. The draft edition of the standard is made available in the interim period. Please be aware that the final version will contain modifications compared to this draft edition. This NORSOK standard is developed with broad petroleum industry participation by interested parties in the Norwegian petroleum industry and is owned by the Norwegian petroleum industry represented by The Norwegian Oil Industry Association (OLF) and The Federation of Norwegian Industry. Please note that whilst every effort has been made to ensure the accuracy of this NORSOK standard, neither OLF nor The Federation of Norwegian Industry or any of their members will assume liability for any use thereof. Standards Norway is responsible for the administration and publication of this NORSOK standard. Standards Norway Telephone: + 47 67 83 86 00 Strandveien 18, P.O. Box 242 Fax: + 47 67 83 86 01 N-1326 Lysaker Email: [email protected] NORWAY Website: www.standard.no/petroleum Copyrights reserved NORSOK standard R-002 Draft Edition 2, June 2011 Foreword 5 Introduction 5 1 Scope 7 2 Normative and informative references 7 2.1 Normative references 7 2.2 Informative references 9 3 Terms, definitions and abbreviations 10 3.1 Terms and definitions 10 3.2 Abbreviations 13 4 General safety requirements 14 4.1 Safety 14 4.2 Fitness for use 14 4.3 Reliability and availability -
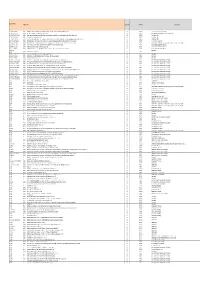
STANDARDS LIST Neu.Xlsx
Document‐Number Published Title Organization Committee Committee Title IEC 100/2536/CD * IEC 63002 2015‐07 IEC 63002, Ed. 1.0: Idenficaon and CommunicaonInteroperability Method for External Power Supplies Used WithPortable Compung Devices (TA 14) IEC IEC/TC 100 Audio, video and multimedia systems and equipment IEC 115/105/CD *IEC/TR 62978 2015‐01 IEC/TR 62978, Ed. 1: Guidelines on Asset Management forHVDC Installaons IEC IEC/TC 115 High Voltage Direct Current (HVDC) transmission for DC voltages above 100 kV IEC 118/29/DPAS* IEC/PAS 62746‐199 2013‐09 System interfaces and communication protocol profiles relevant for systems connected to the smart grid ‐ Open Automated Demand Response (OpenADR 2.0 Profile Specification) IEC IEC/PC 118 Smart grid user interface IEC 118/46/CD *IEC 62746‐10‐2 2014‐12 OASIS Energy Interoperation Version 1.0 Specification IEC IEC/PC 118 Smart grid user interface IEC 118/47/CD * IEC 62746‐10‐1 2015‐01 IEC 62746‐10‐1: Systems interface between customer energymanagement system and the power management system ‐ Part10 ‐1: Open Automated Demand Response (OpenADR 2.0bPro file Specificaon) IEC IEC/PC 118 Smart grid user interface IEC 22H/192/CD * IEC/TS 62040‐4‐1 2015‐04 IEC/TS 62040‐4‐1: Uninterrupble power systems (UPS) ‐ Part 4‐1: Environmental aspects ‐ Product Category Rules (PCR) for life Cycle Assessment and environmental declaraons IEC IEC/SC 22H Uninterruptible power systems (UPS) IEC 3/1224A/CD * IEC 81346‐2 2015‐05 Industrial systems, installaons and equipment and industrialproducts ‐ Structuring principles and reference designaons ‐ Part 2: Classificaon of objects and codes for classes IEC IEC/TC 3 Information structures and elements, identification and marking principles, documentation and graphical symbols IEC 3D/225A/CD * IEC 62656‐5 2014‐03 IEC 62656‐5, Ed. -

HZN Oglasnik Za Normativne Dokumente 2
Hrvatski zavod za norme Oglasnik za normativne dokumente 2/2018 veljača, 2018. Oglasnik za normativne dokumente Hrvatskog zavoda za norme sadrži popise hrvatskih norma, nacrta hrvatskih norma, prijedloga za prihvaćanje stranih norma u izvorniku, povučene hrvatske norme, povučene nacrte hrvatskih norma te ispravke, rezultate europske i međunarodne normizacije razvrstane po predmetnom ustroju i obavijesti HZN-a. Tko u popisima normativnih dokumenata koji su objavljeni u ovom Oglasniku otkrije koju grešku, koja može voditi do krive primjene, moli se da o tome neodložno obavijesti Hrvatski zavod za norme, kako bi se mogli otkloniti uočeni propusti. Izdavač: Sadržaj: 1 Rezultati hrvatske normizacije .................................................................................................. A3 1.1 Hrvatske norme ....................................................................................................................................... A3 1. Nacrti hrvatskih norma ............................................................................................................................ A9 1.3 Prijedlozi za prihvaćanje stranih norma u izvorniku ................................................................................ A9 1.4 Povučene hrvatske norme ...................................................................................................................... A14 1.5 Povučeni nacrti hrvatskih norma ............................................................................................................. 1.6 Ispravci -
2013 Outsourcing Directory Company Guide
2013 Outsourcing directory company guide. Mantova, city (1991 pop. See Ecstasy. , CA 92660 US Telephone: 888-823-2848 Fax: 949-752-2329 Email: [email protected] Website: www.adctech.com Contact: Tee Migliori ADCO ADCO Abu Dhabi Company for Onshore Oil Operations ADCO Alcohol and Drug Control Officer ADCO Air Defense Control Center ADCO Alcohol & Drug Control Office ADCO Air Defense Communications Office ADCO Air Defense Coordination Organization  Circuits 2868 Bond Street Rochester Hills, MI 48309 US Telephone: 248-853-6620 Fax: 248-853-6698 Email: [email protected] Website: www.adcocircuits.com Contact: Marc Damman ADMET ADMET Acyclic Diene Metathesis ADMET Absorption, Distribution, Metabolism, Excretion, and Toxicity (drug properties)  Inc. 51 Morgan Drive Norwood, MA 02062 US Telephone: 781-769-0850, ext. He assumed that position on June 25, 2001.  Industries Sdn. Bhd. 8, Solok Rishah 2, Kawasan Perindustrian Silibin Ipoh, Perak, 30100 Malaysia Telephone: +605 5267231 Fax: +605 5268497 Email: [email protected] Website: www.ostrichmedical.com Contact: Jeffrey Choong SMC SMC Saint Mary's College SMC Santa Monica College SMC Solaris Management Console SMC Smooth Muscle Cell SMC Small Magellanic Cloud (also see LMC) SMC Safety Management Certificate (maritime shipping)  Ltd. 330 SMC Drive Somerset, WI 54025 US Telephone: 715-247-3500 Fax: 715-247-4462 Email: [email protected] Website: www.smcltd.com Contact: Barbara Tischart Smiths Medical 5200 Upper Metro Place Suite 200 Dublin, OH 43017 US Telephone: 866-216-8808 Fax: 866-868-1194 Email: [email protected] Website: www.smithsmedicaloem.com Contact: Janet Granzow Solvay Advanced Polymers 4500 McGinnis Ferry Road Alpharetta, GA 30005 US Telephone: 770-772-8760 Email: [email protected] Website: www.solvayspecialtypolymers.com Contact: Customer Service Southmedic Inc. -
Guía Sobre Normalización En La Accesibilidad De Las TIC
Este libro debería ser indexado con los siguientes términos: normalización, estándares, normas, accesibilidad, accesibilidad electrónica, TIC, guía This books should be indexed with these terms: standardisation, standards, accessibility, electronic accessibility, ICT, guide La cita bibliográfica sugerida es: / The suggested citation is: Martínez Normand L., Rodríguez Ascaso A. (2011). Guía sobre normalización en la accesibilidad de las TIC. (J. Reig & R. Tejerina, Eds.). Madrid: CENTAC, Centro Nacional de Tecnologías de la Accesibilidad. Edita: Centac Coordinares de esta edición: Juan Reig Redondo Rosa Tejerina Pérez Equipo editorial de CENTAC: Aurora Bustelo Virginia Guedan Diego Soriano Rosa Tejerina José A. Valverde Para información sobre este libro y las actividades de CENTAC: [email protected] http://www.centac.es Primera Edición: Julio 2011 Diseño y maquetación: www.lafabricagrafica.net Printed in Spain – Impreso en España Depósito Legal: ISBN: 978-84-615-2055-8 La presente publicación pertenece al Centro Nacional de Tecnologías de la Accesibilidad (CENTAC) y está bajo una licencia Reconocimiento-No Comercial 3.0 España de Creative Commons, y por ello está permitido copiar, distribuir y comunicar públicamente esta obra bajo las condiciones siguientes: - Reconocimiento: El contenido de este libro se puede reproducir total o parcialmente por terceros, citando su proceden cia y haciendo referencia expresa tanto a CENTAC como a su sitio web: www.centac.es. Dicho reconocimiento no podrá sugerir en ningún caso que CENTAC presta apoyo a dicho tercero o apoya el uso que hace de su obra. Uso no comercial: El material original y los trabajos derivados pueden ser distribuidos, copiados y exhibidos mientras su uso no tenga fines comerciales. -

A B C Alimentos Y Agricultura Medio Ambiente Construcción
2019-08-29 NORMAS DEROGADAS A AGOSTO 2019 La Dirección de Normalización de INTECO informa a todos sus asociados y público en general que las siguientes normas se encuentran derogadas. Para mayor información pueden comunicarse con Karla Samuels Givans al correo: [email protected] Nota. Si la norma que busca fue derogada en un año anterior al 2014, no aparecerá en la siguiente tabla, para más información favor comunicarse al teléfono 2283-4522 ext. 129, para ser transferido con el coordinador del comité que corresponda. SECTOR A Alimentos y agricultura Número Órgano de estudio: Código de Norma Derogado Código de Norma que la Sustituye Título: Sistemas de gestión de la inocuidad de los alimentos - Requisitos de los 1 CTN 02 SC 01 INTE/ISO/TS 22003:2007 INTE/ISO/TS 22003:2017 organismos que realizan la auditoría y la certificación de sistemas de gestión de inocuidad de los alimentos Café tostado y molido. Método para la determinación del grado de 2 CTN 24 INTE 24-02-02:2011 INTE A79:2017 Enm 1 molienda (tamaño de partícula). Café tostado y molido. Determinación del contenido de azúcares totales 3 CTN 24 INTE 24-02-07:2011 INTE A82:2017 utilizando cromatografía líquida de alto desempeño (HPLC). 4 CTN 24 INTE 24-01-01-2011 INTE A75:2017 Café verde. Requisitos Café Verde. Metodología para el análisis sensorial cuantitativo 5 CTN 24 INTE 24-01-03-2011 INTE A76:2017 descriptivo del café. Sistemas de gestión de la inocuidad de los alimentos. Requisitos para 6 CTN 02 SC 01 INTE/ISO 22000:2005 INTE/ISO 22000:2018 toda organización en la cadena alimentaria.