Lecture-W01-2.Pdf (PDF)
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Identifying Threats Associated with Man-In-The-Middle Attacks During Communication Between a Mobile Device and the Back End Server in Mobile Banking Applications
IOSR Journal of Computer Engineering (IOSR-JCE) e-ISSN: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 2, Ver. IX (Mar-Apr. 2014), PP 35-42 www.iosrjournals.org Identifying Threats Associated With Man-In-The-Middle Attacks during Communication between a Mobile Device and the Back End Server in Mobile Banking Applications Anthony Luvanda1,*Dr Stephen Kimani1 Dr Micheal Kimwele1 1. School of Computing and Information Technology, Jomo Kenyatta University of Agriculture and Technology, PO Box 62000-00200 Nairobi Kenya Abstract: Mobile banking, sometimes referred to as M-Banking, Mbanking or SMS Banking, is a term used for performing balance checks, account transactions, payments, credit applications and other banking transactions through a mobile device such as a mobile phone or Personal Digital Assistant (PDA). Mobile banking has until recently most often been performed via SMS or the Mobile Web. Apple's initial success with iPhone and the rapid growth of phones based on Google's Android (operating system) have led to increasing use of special client programs, called apps, downloaded to the mobile device hence increasing the number of banking applications that can be made available on mobile phones . This in turn has increased the popularity of mobile device use in regards to personal banking activities. Due to the characteristics of wireless medium, limited protection of the nodes, nature of connectivity and lack of centralized managing point, wireless networks tend to be highly vulnerable and more often than not they become subjects of attack. This paper proposes to identify potential threats associated with communication between a mobile device and the back end server in mobile banking applications. -

MALWARE ACTIVITY DETECTION THROUGH BROWSER EXTENSION Jayanth Betha1, Prakash Andavolu2, Mariyala V V Gupta3 Department of Computer Science and Engineering, St
MALWARE ACTIVITY DETECTION THROUGH BROWSER EXTENSION Jayanth Betha1, Prakash Andavolu2, Mariyala V V Gupta3 Department of Computer Science and Engineering, St. Martin’s Engineering College, India. Abstract stretch out beyond the contaminated PC. A The drastic growth in Internet users and Malware infection may aim to damage the files Digital assets worldwide has created on storage devices; however, a keylogger is opportunities for cybercriminals to break utilized to take individual data, such as email into systems. The massive increase in ID's or passwords. While there are numerous malware and cybercrime is seen all over the approaches used to secure against keyloggers, globe; people have become more dependent this study mainly focuses on the detection of on the web environment. Malware (Malicious keyloggers. This research report will provide an Software), is a software that opens the door in-depth study on types of secretly monitoring for cybercriminals to access sensitive malware (keyloggers). A browser based solution information from the computing devices. In (browser extension) is needed to detect and alert the current technology-dependent world, the user about the keyloggers. attacks upon sensitive user information have In today’s technology-dependent world, continued to grow over time steadily. A attacks upon sensitive user information have common threat to data security is Malware. continued to evolve steadily over time. A Symantec discovered more than 430 million common threat to data security is Malware. new unique pieces of malware in 2015, up 36 According to (Symantec’s 2016 Internet percent from the year before. The objective of Security Threat Report. (n.d.). -

Adware-Searchsuite
McAfee Labs Threat Advisory Adware-SearchSuite June 22, 2018 McAfee Labs periodically publishes Threat Advisories to provide customers with a detailed analysis of prevalent malware. This Threat Advisory contains behavioral information, characteristics and symptoms that may be used to mitigate or discover this threat, and suggestions for mitigation in addition to the coverage provided by the DATs. To receive a notification when a Threat Advisory is published by McAfee Labs, select to receive “Malware and Threat Reports” at the following URL: https://www.mcafee.com/enterprise/en-us/sns/preferences/sns-form.html Summary Detailed information about the threat, its propagation, characteristics and mitigation are in the following sections: Infection and Propagation Vectors Mitigation Characteristics and Symptoms Restart Mechanism McAfee Foundstone Services The Threat Intelligence Library contains the date that the above signatures were most recently updated. Please review the above mentioned Threat Library for the most up to date coverage information. Infection and Propagation Vectors Adware-SearchSuite is a "potentially unwanted program" (PUP). PUPs are any piece of software that a reasonably security- or privacy-minded computer user may want to be informed of and, in some cases, remove. PUPs are often made by a legitimate corporate entity for some beneficial purpose, but they alter the security state of the computer on which they are installed, or the privacy posture of the user of the system, such that most users will want to be aware of them. Mitigation Mitigating the threat at multiple levels like file, registry and URL could be achieved at various layers of McAfee products. Browse the product guidelines available here (click Knowledge Center, and select Product Documentation from the Support Content list) to mitigate the threats based on the behavior described in the Characteristics and symptoms section. -

A Crawler-Based Study of Spyware on the Web
A Crawler-based Study of Spyware on the Web Alexander Moshchuk, Tanya Bragin, Steven D. Gribble, and Henry M. Levy Department of Computer Science & Engineering University of Washington {anm, tbragin, gribble, levy}@cs.washington.edu Abstract servers [16]. The AOL scan mentioned above has provided simple summary statistics by directly examining desktop in- Malicious spyware poses a significant threat to desktop fections [2], while a recent set of papers have considered security and integrity. This paper examines that threat from user knowledge of spyware and its behavior [6, 29]. an Internet perspective. Using a crawler, we performed a In this paper we change perspective, examining the na- large-scale, longitudinal study of the Web, sampling both ture of the spyware threat not on the desktop but from an executables and conventional Web pages for malicious ob- Internet point of view. To do this, we conduct a large-scale jects. Our results show the extent of spyware content. For outward-looking study by crawling the Web, downloading example, in a May 2005 crawl of 18 million URLs, we found content from a large number of sites, and then analyzing it spyware in 13.4% of the 21,200 executables we identified. to determine whether it is malicious. In this way, we can At the same time, we found scripted “drive-by download” answer several important questions. For example: attacks in 5.9% of the Web pages we processed. Our analy- sis quantifies the density of spyware, the types of of threats, • How much spyware is on the Internet? and the most dangerous Web zones in which spyware is • Where is that spyware located (e.g., game sites, chil- likely to be encountered. -
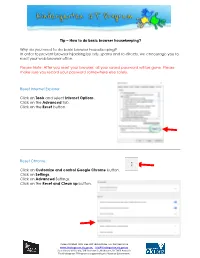
Tip – How to Do Basic Browser Housekeeping?
Tip – How to do basic browser housekeeping? Why do you need to do basic browser housekeeping? In order to prevent browser hijacking by ads, spams and re-directs, we encourage you to reset your web browser often. Please Note: After you reset your browser, all your saved password will be gone. Please make sure you record your password somewhere else safely. _______________________________________________________________________________________ Reset Internet Explorer Click on Tools and select Internet Options . Click on the Advanced tab. Click on the Reset button. _______________________________________________________________________________________ Reset Chrome Click on Customize and control Google Chrome button. Click on Settings . Click on Advanced Settings. Click on the Reset and Clean up button. Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Firefox In the address bar of the FireFox type in about:support and hit Enter. Click Refresh Firefox… button. A window will appear showing the details of this action. Click Refresh Firefox button. _______________________________________________________________________________________ Clear website data in Safari Click on Safari tab and select Preferences… Click Privacy tab. Click Manage Website Data… Click on Remove All . Phone: (03) 8664 7001 Free Call: 1800 629 835 Fax: (03) 9639 2175 www.kindergarten.vic.gov.au [email protected] State Library of Victoria, 328 Swanston St, Melbourne, VIC 3000 Australia The Kindergarten IT Program is supported by the Victorian Government. Reset Edge Click on Settings and More button. -

COVID-19 Updates and Resources for Local Governments G Tuesday, March 23, 2021 Welcome Greeting
COVID-19 Updates and Resources for Local Governments g Tuesday, March 23, 2021 Welcome Greeting Kayla Rosen Departmental Analyst, Community Engagement and Finance, Department of Treasury 2 Tools and Resources for Local Governments: 11th Webinar Tuesday, March 23, 2021 – 2 p.m. – 3 p.m. I. Welcome & Introductions Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury I. Treasury Update a. CARES Act Grant b. FDCVT Grant c. Overviews of Recreational Marijuana Payments d. American Rescue Plan Eric Bussis, Chief Economist and Director of the Office of Revenue and Tax Analysis, Michigan Department of Treasury I. Cybersecurity for Local Governments Derek Larson, Acting Deputy Chief Security Officer, Department of Technology, Management and Budget (DTMB) I. Question and Answer II. Closing Remarks Heather Frick, Bureau Director, Bureau of Local Government and School Services, Michigan Department of Treasury 3 Welcome & Introductions Heather Frick Bureau Director, Bureau of Local Government and School Services, Department of Treasury 4 Treasury Local Government Funding Update Eric Bussis Chief Economist and Director Office of Revenue and Tax Analysis Michigan Department of Treasury 5 Treasury Update • CARES Act Grant • FDCVT Grant Agenda • Overviews of Recreational Marijuana Payments • American Rescue Plan 6 First Responder Hazard Pay Premiums Program (FRHPPP) • Payments made to 740 applicants, supporting approximately 37,500 first responders • 97 applications were selected for further federal -

The Emergence of Exploit-As-A-Service
Manufacturing Compromise: The Emergence of Exploit-as-a-Service Chris Grier† Lucas Ballard2 Juan Caballerox Neha Chachra∗ Christian J. Dietrichq Kirill Levchenko∗ Panayiotis Mavrommatis2 Damon McCoyz Antonio Nappax Andreas Pitsillidis∗ Niels Provos2 M. Zubair Rafiquex Moheeb Abu Rajab2 Christian Rossowq Kurt Thomasy Vern Paxson† Stefan Savage∗ Geoffrey M. Voelker∗ y University of California, Berkeley ∗ University of California, San Diego 2 Google International Computer Science Institute x IMDEA Software Institute q University of Applied Sciences Gelsenkirchen z George Mason University ABSTRACT 1. INTRODUCTION We investigate the emergence of the exploit-as-a-service model for In this work we investigate the emergence of a new paradigm: the driveby browser compromise. In this regime, attackers pay for an exploit-as-a-service economy that surrounds browser compromise. exploit kit or service to do the “dirty work” of exploiting a vic- This model follows in the footsteps of a dramatic evolution in the tim’s browser, decoupling the complexities of browser and plugin world of for-profit malware over the last five years, where host com- vulnerabilities from the challenges of generating traffic to a web- promise is now decoupled from host monetization. Specifically, the site under the attacker’s control. Upon a successful exploit, these means by which a host initially falls under an attacker’s control are kits load and execute a binary provided by the attacker, effectively now independent of the means by which an(other) attacker abuses transferring control of a victim’s machine to the attacker. the host in order to realize a profit. This shift in behavior is exem- In order to understand the impact of the exploit-as-a-service plified by the pay-per-install model of malware distribution, where paradigm on the malware ecosystem, we perform a detailed anal- miscreants pay for compromised hosts via the underground econ- ysis of the prevalence of exploit kits, the families of malware in- omy [4, 41]. -

Spyware & Adware Products
AdwareAdware/Spyware/Spyware ProductsProducts && RecommendationsRecommendations UCLAUCLA OfficeOffice ofof InstructionalInstructional DevelopmentDevelopment MikeMike TakahashiTakahashi AgendaAgenda WhatWhat isis AdwareAdware/Spyware/Spyware KnownKnown AdwareAdware/Spyware/Spyware ProductsProducts AntiAnti AdwareAdware/Spyware/Spyware RemovalRemoval ProductProduct ComparisonsComparisons TipsTips && RecommendationsRecommendations AdwareAdware AdwareAdware cancan bebe softwaresoftware thatthat generatesgenerates advertisementsadvertisements suchsuch asas poppop--upup windowswindows oror hotlinkshotlinks onon webweb pages.pages. ItIt maymay addadd linkslinks toto youryour favoritesfavorites andand youryour desktop.desktop. ItIt cancan changechange youryour homehome pagepage andand youryour searchsearch engineengine toto sitessites thatthat earnearn incomeincome fromfrom variousvarious advertisers.advertisers. Source http://www.microsoft.com/windows/ie/community/columns/adware.mspx AdwareAdware ExamplesExamples What?!What?! MyMy computercomputer isis infected!infected! OrOr isis it?it? AdwareAdware ExamplesExamples WellWell--knownknown AdwareAdware ProgramsPrograms toto AvoidAvoid HotbarHotbar (Add(Add--ons)ons) Adds graphical skins to Browser and Email clients Adds toolbars and search button BlockCheckerBlockChecker ClipGenieClipGenie CometComet CursorCursor GatorGator WinFixerWinFixer StumbleUponStumbleUpon WeatherBugWeatherBug SpywareSpyware SpywareSpyware isis computercomputer softwaresoftware thatthat collectscollects -

Not So Secure! Research Report on End-Point Compromises and the Risk to Internet Banking
Not so secure! Research report on end-point compromises and the risk to Internet banking Special research report. August 2016 Internet Banking has grown by leaps and bounds in India. India had over 400 million Internet users by the beginning of 2016 as per a report by IAMAI and IMRB. This is the highest number of Internet banking users in any country. While having a high number of Internet banking users indicates healthy adoption of IT and reduced costs for banks, it also means that this population is vulnerable to cyberthreats which can put their hard-earned money at risk. One of the biggest addressable risks which users face is man-in-the-browser and end-point compromise attacks. “Virtual keyboards are ineffective in preventing the theft of end-user credentials and banks need to look at end point security more holistically. End-point compromise is an attack in which the end user’s computer and, in many cases these days, a browser is compromised using a simple program—generally a browser plugin or browser extension. The program is designed to steal the Internet banking credentials of the end users. Our security research team looked at the Internet banking websites of 26 banks in India. We found that over 21 banks have inadequate mechanisms to detect or prevent attacks which could compromise the end user credentials. This finding has significant implications as the end user is generally gullible, and many users can be made to download a browser extension/plugin which is capable of capturing banking credentials. Mechanisms which are currently prevalent, such as the virtual keyboard, which were long considered a protection against such attacks, were found to be inadequate to prevent these attacks. -

Microsoft Security Intelligence Report
Microsoft Security Intelligence Report Volume 12 July through December, 2011 www.microsoft.com/sir Microsoft Security Intelligence Report This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. This document is provided “as-is.” Information and views expressed in this document, including URL and other Internet website references, may change without notice. You bear the risk of using it. Copyright © 2012 Microsoft Corporation. All rights reserved. The names of actual companies and products mentioned herein may be the trademarks of their respective owners. JULY–DECEMBER 2011 i Authors Dennis Batchelder David Felstead Ken Malcolmson Tim Rains Microsoft Protection Bing Microsoft Trustworthy Microsoft Trustworthy Technologies Computing Computing Paul Henry Shah Bawany Wadeware LLC Nam Ng Frank Simorjay Microsoft Windows Safety Microsoft Trustworthy Microsoft Trustworthy Platform Nitin Kumar Goel Computing Computing Microsoft Security Joe Blackbird Response Center Mark Oram Holly Stewart Microsoft Malware Microsoft Trustworthy Microsoft Malware Protection Center Jeff Jones Computing Protection Center Microsoft Trustworthy Eve Blakemore Computing Daryl Pecelj Matt Thomlinson Microsoft Trustworthy Microsoft IT Information Microsoft Trustworthy Computing Jimmy Kuo Security and Risk Computing Microsoft Malware Management Joe Faulhaber Protection Center Scott Wu Microsoft Malware Dave Probert Microsoft Malware Protection Center Marc Lauricella Microsoft -

Mobile Banking Adeptness on Man-In-The-Middle and Man-In-The-Browser Attacks
IOSR Journal of Mobile Computing & Application (IOSR-JMCA) e-ISSN: 2394-0050, P-ISSN: 2394-0042.Volume 4, Issue 2 (Mar. - Apr. 2017), PP 13-19 www.iosrjournals.org Mobile Banking Adeptness on Man-In-The-Middle and Man-In-The-Browser Attacks P.S.Jagadeesh Kumar, Wenli Hu, Xianpei Li, Kundan Lal Abstract : A brand new category of perilous threat, asphyxiate the browser behavior in line of attack similar to that of Trojan horses. These immaculate varieties of Trojan horses can acclimatize the banking transaction activities, as they are muddled in browsers on top of mobile banking applications, and exhibit the user's transactions. Primarily, they are man-in-the-middle (MITM) attacks pedestal on users illuminating their testament on a deceptive website and man-in-the-browser (MITB) attacks that modify the exterior of indenture in the user’s browser. Repugnant to phishing attacks which depends upon similar but illusive websites, these malicious attacks cannot be professed by the user, as they are with genuine titivates, the user is desperately logged-in as standard, and consequently, falls prey in losing practical mobile banking utilities. Keywords: Man-In-The-Middle (MITM), Man-In-The-Browser (MITB), Mobile Banking, Phishing Attack I. Introduction Mobile conventional password based consumer substantiation has been a distinguished sanctuary predicament. Even a primordial and tenuously accomplished phishing attack can be effectual for an effortless password thievery. Attributable to accumulate of phishing and connected attacks, susceptible requests such as online banking gradually more desired for more safe and sound authentication substitutes. Their clarifications, typically drop into a collection called two-step verification. -

A Survey on Keylogger: a Malicious Attack
International Journal of Advanced Research in Computer Engineering & Technology (IJARCET) Volume 4 Issue 4, April 2015 A Survey on Keylogger: A malicious Attack NameHemita Pathak, Apurva Pawar, Balaji Patil are depicting working of keylogger. Section V suggests Abstract—Now a days, internet has become part of basic various prevention and detection methods. We enlist different needs for modern society. People are using internet for online applications of keylogger in section VI. Finally, we conclude banking and confidensial information sharing through email our paper in section VII. and chats on social networking sites. Intruters are using malwares to damage systems. Keylogger is one of the harmful II. DIFFERENT PASSWORD ATTACKS malwares. Keylogger tries to obtain private information through monitoring keystroke and communicating this data to For authentication of any system password is first and intruter with malicious intentions. And thus, keylogger is said to foremost step so, passwords play an important role in daily be a main threat for business and personal activities. To prevent life in various computing applications like ATM machines, from huge economical/personal loss, system needs to protect internet services, windows login, authentication in mobiles valuable information from Intruters. But before planning for etc. Intruders/hackers can make system vulnerable, can get prevention it is necessary to be aware of few things like key access of it and can also get valuable information of ours. In logger working. This paper gives a brief description of keylogger, it’s working, prevention detection of key logger and this section we enlisted some of possible password attacks. various applications of key logger.