The Malware Book 2016
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Identifying Threats Associated with Man-In-The-Middle Attacks During Communication Between a Mobile Device and the Back End Server in Mobile Banking Applications
IOSR Journal of Computer Engineering (IOSR-JCE) e-ISSN: 2278-0661, p- ISSN: 2278-8727Volume 16, Issue 2, Ver. IX (Mar-Apr. 2014), PP 35-42 www.iosrjournals.org Identifying Threats Associated With Man-In-The-Middle Attacks during Communication between a Mobile Device and the Back End Server in Mobile Banking Applications Anthony Luvanda1,*Dr Stephen Kimani1 Dr Micheal Kimwele1 1. School of Computing and Information Technology, Jomo Kenyatta University of Agriculture and Technology, PO Box 62000-00200 Nairobi Kenya Abstract: Mobile banking, sometimes referred to as M-Banking, Mbanking or SMS Banking, is a term used for performing balance checks, account transactions, payments, credit applications and other banking transactions through a mobile device such as a mobile phone or Personal Digital Assistant (PDA). Mobile banking has until recently most often been performed via SMS or the Mobile Web. Apple's initial success with iPhone and the rapid growth of phones based on Google's Android (operating system) have led to increasing use of special client programs, called apps, downloaded to the mobile device hence increasing the number of banking applications that can be made available on mobile phones . This in turn has increased the popularity of mobile device use in regards to personal banking activities. Due to the characteristics of wireless medium, limited protection of the nodes, nature of connectivity and lack of centralized managing point, wireless networks tend to be highly vulnerable and more often than not they become subjects of attack. This paper proposes to identify potential threats associated with communication between a mobile device and the back end server in mobile banking applications. -

MALWARE ACTIVITY DETECTION THROUGH BROWSER EXTENSION Jayanth Betha1, Prakash Andavolu2, Mariyala V V Gupta3 Department of Computer Science and Engineering, St
MALWARE ACTIVITY DETECTION THROUGH BROWSER EXTENSION Jayanth Betha1, Prakash Andavolu2, Mariyala V V Gupta3 Department of Computer Science and Engineering, St. Martin’s Engineering College, India. Abstract stretch out beyond the contaminated PC. A The drastic growth in Internet users and Malware infection may aim to damage the files Digital assets worldwide has created on storage devices; however, a keylogger is opportunities for cybercriminals to break utilized to take individual data, such as email into systems. The massive increase in ID's or passwords. While there are numerous malware and cybercrime is seen all over the approaches used to secure against keyloggers, globe; people have become more dependent this study mainly focuses on the detection of on the web environment. Malware (Malicious keyloggers. This research report will provide an Software), is a software that opens the door in-depth study on types of secretly monitoring for cybercriminals to access sensitive malware (keyloggers). A browser based solution information from the computing devices. In (browser extension) is needed to detect and alert the current technology-dependent world, the user about the keyloggers. attacks upon sensitive user information have In today’s technology-dependent world, continued to grow over time steadily. A attacks upon sensitive user information have common threat to data security is Malware. continued to evolve steadily over time. A Symantec discovered more than 430 million common threat to data security is Malware. new unique pieces of malware in 2015, up 36 According to (Symantec’s 2016 Internet percent from the year before. The objective of Security Threat Report. (n.d.). -

EVALUATION of HIDDEN MARKOV MODEL for MALWARE BEHAVIORAL CLASSIFICATION By
EVALUATION OF HIDDEN MARKOV MODEL FOR MALWARE BEHAVIORAL CLASSIFICATION By Mohammad Imran A research thesis submitted to the Department of Computer Science, Capital University of Science & Technology, Islamabad in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY IN COMPUTER SCIENCE DEPARTMENT OF COMPUTER SCIENCE CAPITAL UNIVERSITY OF SCIENCE & TECHNOLOGY ISLAMABAD October 2016 Copyright© 2016 by Mr. Mohammad Imran All rights reserved. No part of the material protected by this copyright notice may be reproduced or utilized in any form or any means, electronic or mechanical, including photocopying, recording or by any information storage and retrieval system, without the permission from the author. To my parents and family Contents List of Figures iv List of Tablesv Abbreviations vi Publications vii Acknowledgements viii Abstractx 1 Introduction1 1.1 What is malware?............................1 1.2 Types of malware............................3 1.2.1 Virus...............................3 1.2.2 Worm..............................3 1.2.3 Trojan horse...........................3 1.2.4 Rootkit.............................4 1.2.5 Spyware.............................4 1.2.6 Adware.............................4 1.2.7 Bot................................4 1.3 Malware attack vectors.........................5 1.3.1 Use of vulnerabilities......................5 1.3.2 Drive-by downloads.......................5 1.3.3 Social engineering........................5 1.4 Combating malware: Malware analysis................5 1.4.1 Static analysis..........................6 1.4.2 Dynamic analysis........................9 1.4.3 Hybrid analysis......................... 12 1.5 Combating malware: Malware detection and classification...... 12 1.6 Observations from the literature.................... 13 1.7 Problem statement........................... 15 1.8 Motivation................................ 15 1.8.1 Why malware analysis?..................... 16 1.8.2 Why Hidden Markov Model?................ -

3/16/2020 Testout Labsim
3/16/2020 TestOut LabSim 8.4 Web Application Attacks As you study this section, answer the following questions: What are two ways that drive-by download attacks occur? Which countermeasures can be used to eliminate buffer overflow attacks? How can cross-site scripting (XSS) be used to breach the security of a web user? What is the best method for preventing SQL injection attacks? What are some types of header manipulation? Which mitigation practices help to protect internet-based activities from web application attacks? In this section, you will learn to: Prevent cross-site scripting Key terms for this section include the following: Term Definition Drive-By Download An attack where software or malware is downloaded and installed without explicit consent from the user. Typosquatting/URL Hijacking An attack that occurs when an attacker registers domain names that correlate to common typographical errors made by users when trying to access a legitimate website. Buffer Overflow An attack that exploits an operating system or an application that does not properly enforce boundaries for how much and what type of data can be inputted. An attack that exploits a computational operation by a running process that results in a numeric value that exceeds the maximum size of the integer type used to store it in Integer Overflow memory. Cross-Site Scripting (XSS) An attack that injects scripts into webpages. Cross-Site Request Forgery A type of malicious exploit whereby unauthorized commands are transmitted from the user to a website that currently trusts the user by way of authentication, cookies, etc. (CSRF/XSRF) LDAP Injection An attack that uses LDAP statements with arbitrary commands to exploit web-based applications with access to a directory service. -

A Case Study in DNS Poisoning
A wrinkle in time: A case study in DNS poisoning Harel Berger Amit Z. Dvir Moti Geva Abstract—The Domain Name System (DNS) provides a trans- lation between readable domain names and IP addresses. The DNS is a key infrastructure component of the Internet and a prime target for a variety of attacks. One of the most significant threat to the DNS’s wellbeing is a DNS poisoning attack, in which the DNS responses are maliciously replaced, or poisoned, by an attacker. To identify this kind of attack, we start by an analysis of different kinds of response times. We present an analysis of typical and atypical response times, while differentiating between the different levels of DNS servers’ response times, from root servers down to internal caching servers. We successfully identify empirical DNS poisoning attacks based on a novel method for DNS response timing analysis. We then present a system we developed to validate our technique that does not require any changes to the DNS protocol or any existing network equipment. Our validation system tested data from different architectures including LAN and cloud environments and real data from an Internet Service Provider (ISP). Our method and system differ from most other DNS poisoning detection methods and achieved high detection rates exceeding 99%. These findings suggest that when used in conjunction with other methods, they can considerably enhance the accuracy of these methods. I. INTRODUCTION Fig. 1. DNS hierarchy example The Domain Name System (DNS) [1], [2] is one of the best known protocols in the Internet. Its main function is to trans- late human-readable domain names into their corresponding following steps. -

Lakeridge Health Uses Trend Micro™ Messaging and Web Security for Comprehensive Gateway Web Threat Protection
Securing Your Web World Lakeridge Health Uses Trend Micro™ Messaging and Web Security for Comprehensive Gateway Web Threat Protection Lakeridge Health (LH) serves a community of more than 500,000 residents within an area of 19,000 square kilometers in Ontario. IT must build in security to protect the mission-critical infrastructure that spans the 25 hospitals, clinics, and administrative sites. A recent escalation in web threats, including web-based phishing and malware as well as the spam emails that deliver links to these threats, called for a combination of Trend Micro messaging and web solutions supported by the Trend Micro Smart Protection Network. ESCALATING WEB THREATS “ Trend Micro messaging and Over the years, LH has tried many web security builds up our alternatives in its search for the best possible security. When web threats began defenses where they can to increase, LH’s user help desk was flooded do the most good—right at with complaints about spyware and other the edge of our network. infections. Unsatisfied with its previously These solutions have proven deployed products and lack of support from the vendor, LH evaluated four other security invaluable for fighting the vendors including Trend Micro. constantly evolving web After identifying Trend Micro as the winner of its security “bake off,” LH deployed multiple threats.” layers of Trend Micro protection. Trend Micro gateway protection blocks web-based threats by introducing messaging and web defense right at the network perimeter: — Peter Hastie, IT Systems Consultant • Trend Micro InterScan™ Messaging Security blocks emails threats, including spam, Lakeridge Health (LH), phishing, and malware, and offers content filtering to enforce compliance and prevent Ontario, Canada data leaks. -
Lecture Three Systems Systems
Complex Complex Sociotechnical Press... Sociotechnical Lecture Three Systems Systems Stories of Complex Sociotechnical Systems: Measuring Measuring Measurement, Mechanisms, and Meaning Happiness Happiness Some motivation Some motivation Measuring emotional Measuring emotional Lipari Summer School, Summer, 2012 content content Data sets Data sets Analysis I “Social Scientists wade into the Tweet Analysis Songs Songs Prof. Peter Dodds Blogs stream” by Greg Miller, Blogs Tweets Science, 333, 1814–1815, 2011 [15] Tweets Positivity Bias Positivity Bias Department of Mathematics & Statistics | Center for Complex Systems | “Does a Nation’s Mood Lurk in Its Songs and Vermont Advanced Computing Center | University of Vermont References I References Blogs?” by Benedict Carey New York Times, August 2009. () I More here: http://www.uvm.edu/∼pdodds/research/ () Licensed under the Creative Commons Attribution-NonCommercial-ShareAlike 3.0 License. 1 of 83 4 of 83 Complex Complex Outline Sociotechnical Happiness: Sociotechnical Systems Systems Measuring Measuring Measuring Happiness Happiness Happiness Some motivation Some motivation Some motivation Measuring emotional Measuring emotional content content Measuring emotional content Data sets Data sets Data sets Analysis Analysis Songs Songs Blogs Blogs Tweets Tweets Analysis Positivity Bias Positivity Bias Songs References References Blogs Tweets Bentham: Jefferson: Positivity Bias Socrates et al.: hedonistic . the pursuit of eudaimonia [8] calculus happiness References 2 of 83 6 of 83 Complex Complex -

Éric FREYSSINET Lutte Contre Les Botnets
THÈSE DE DOCTORAT DE L’UNIVERSITÉ PIERRE ET MARIE CURIE Spécialité Informatique École doctorale Informatique, Télécommunications et Électronique (Paris) Présentée par Éric FREYSSINET Pour obtenir le grade de DOCTEUR DE L’UNIVERSITÉ PIERRE ET MARIE CURIE Sujet de la thèse : Lutte contre les botnets : analyse et stratégie Présentée et soutenue publiquement le 12 novembre 2015 devant le jury composé de : Rapporteurs : M. Jean-Yves Marion Professeur, Université de Lorraine M. Ludovic Mé Enseignant-chercheur, CentraleSupélec Directeurs : M. David Naccache Professeur, École normale supérieure de thèse M. Matthieu Latapy Directeur de recherche, UPMC, LIP6 Examinateurs : Mme Clémence Magnien Directrice de recherche, UPMC, LIP6 Mme Solange Ghernaouti-Hélie Professeure, Université de Lausanne M. Vincent Nicomette Professeur, INSA Toulouse Cette thèse est dédiée à M. Celui qui n’empêche pas un crime alors qu’il le pourrait s’en rend complice. — Sénèque Remerciements Je tiens à remercier mes deux directeurs de thèse. David Naccache, officier de réserve de la gendarmerie, contribue au développement de la recherche au sein de notre institution en poussant des personnels jeunes et un peu moins jeunes à poursuivre leur passion dans le cadre académique qui s’impose. Matthieu Latapy, du LIP6, avec qui nous avions pu échanger autour d’une thèse qu’il encadrait dans le domaine difficile des atteintes aux mineurs sur Internet et qui a accepté de m’accueillir dans son équipe. Je voudrais remercier aussi, l’ensemble de l’équipe Réseaux Complexes du LIP6 et sa responsable d’équipe actuelle, Clémence Magnien, qui m’ont accueilli à bras ouverts, accom- pagné à chaque étape et dont j’ai pu découvrir les thématiques et les méthodes de travail au fil des rencontres et des discussions. -

A Study on Advanced Botnets Detection in Various Computing Systems Using Machine Learning Techniques
SJIF Impact Factor: 7.001| ISI I.F.Value:1.241| Journal DOI: 10.36713/epra2016 ISSN: 2455-7838(Online) EPRA International Journal of Research and Development (IJRD) Volume: 5 | Issue: 12 | December 2020 - Peer Reviewed Journal A STUDY ON ADVANCED BOTNETS DETECTION IN VARIOUS COMPUTING SYSTEMS USING MACHINE LEARNING TECHNIQUES K. Vamshi Krishna Assistant Professor, Department of Computer Science and Engineering, Narasaraopet Engineering College, Narasaraopet, Guntur, India Article DOI: https://doi.org/10.36713/epra5902 ABSTRACT Due to the rapid growth and use of Emerging technologies such as Artificial Intelligence, Machine Learning and Internet of Things, Information industry became so popular, meanwhile these Emerging technologies have brought lot of impact on human lives and internet network equipment has increased. This increment of internet network equipment may bring some serious security issues. A botnet is a number of Internet-connected devices, each of which is running one or more bots.The main aim of botnet is to infect connected devices and use their resource for automated tasks and generally they remain hidden. Botnets can be used to perform Distributed Denial-of-Service (DDoS) attacks, steal data, send spam, and allow the attacker to access the device and its connection. In this paper we are going to address the advanced Botnet detection techniques using Machine Learning. Traditional botnet detection uses manual analysis and blacklist, and the efficiency is very low. Applying machine learning to batch automatic detection of botnets can greatly improve the efficiency of detection. Using machine learning to detect botnets, we need to collect network traffic and extract traffic characteristics, and then use X-Means, SVM algorithm to detect botnets. -
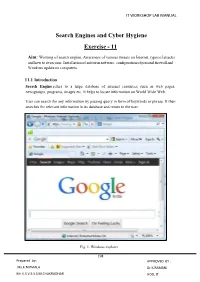
Search Engines and Cyber Hygiene Exercise - 11
IT WORKSHOP LAB MANUAL Search Engines and Cyber Hygiene Exercise - 11 Aim: Working of search engine, Awareness of various threats on Internet, types of attacks and how to overcome. Installation of antivirus software, configuration of personal firewall and Windows update on computers. 11.1 Introduction Search Engine refers to a huge database of internet resources such as web pages, newsgroups, programs, images etc. It helps to locate information on World Wide Web. User can search for any information by passing query in form of keywords or phrase. It then searches for relevant information in its database and return to the user. Fig. 1. Windows explorer 198 Prepared by: APPROVED BY : Ms.K.NIRMALA Dr.K.RAMANI Mr.V.S.V.S.S.S.M.CHAKRADHAR HOD, IT IT WORKSHOP LAB MANUAL Search Engine Components Generally there are three basic components of a search engine as listed below: 1. Web Crawler 2. Database 3. Search Interfaces Web crawler It is also known as spider or bots. It is a software component that traverses the web to gather information. Database All the information on the web is stored in database. It consists of huge web resources. Search Interfaces This component is an interface between user and the database. It helps the user to search through the database. Search Engine Working Web crawler, database and the search interface are the major component of a search engine that actually makes search engine to work. Search engines make use of Boolean expression AND, OR, NOT to restrict and widen the results of a search. Following are the steps that are performed by the search engine: The search engine looks for the keyword in the index for predefined database instead of going directly to the web to search for the keyword. -

Open Sisko Final__Thesis.Pdf
THE PENNSYLVANIA STATE UNIVERSITY SCHREYER HONORS COLLEGE DEPARTMENT OF INFORMATION SCIENCE AND TECHNOLOGY THE WAKE OF CYBER-WAREFARE STUDENT NAME JACOB SISKO SPRING 2015 A thesis submitted in partial fulfillment of the requirements for a baccalaureate degree in Security and Risk Analysis with honors in Security and Risk Analysis Reviewed and approved* by the following: Gerald Santoro Senior Lecturer Professor Information Sciences and Technology Thesis Supervisor Edward Glantz Senior Lecturer Professor Information Sciences and Technology Honors Adviser * Signatures are on file in the Schreyer Honors College. i ABSTRACT The purpose of my thesis paper is to explain the significance and inter-relationship of cyber-crime and cyber-warfare. To give my reader a full understanding of the issue, I will begin by explaining the history of the Internet, give a definition of both cyber-crime and cyber-warfare, and then explain how they have impacted the Internet. I will also give examples of a few Chinese hacker groups, and what kind of attacks they have successfully carried out. Then I will talk about how recent attacks have become more sophisticated which are capable of causing more damage. I would also like to discuss how the cyber-warfare has impacted Chinese-US relations, and how it has an impact on the economic ties. Because of the currently capability and potential threat, I will explain why cyber-crime and cyber-warfare are so important to monitor because of the potential damage current and future attacks can cause. ii TABLE OF CONTENTS ACKNOWLEDGEMENTS ......................................................................................... iii Chapter 1 Introduction ................................................................................................. 1 History of the Internet ...................................................................................................... 1 Chapter 2 Cyber-crime – Functions and Capabilities ................................................. -

June 2020 Volume 87 / Number 6
JUNE 2020 VOLUME 87 / NUMBER 6 President Kevin Maher Publisher Frank Alkyer Editor Bobby Reed Reviews Editor Dave Cantor Contributing Editor Ed Enright Creative Director ŽanetaÎuntová Design Assistant Will Dutton Assistant to the Publisher Sue Mahal Bookkeeper Evelyn Oakes ADVERTISING SALES Record Companies & Schools Jennifer Ruban-Gentile Vice President of Sales 630-359-9345 [email protected] Musical Instruments & East Coast Schools Ritche Deraney Vice President of Sales 201-445-6260 [email protected] Advertising Sales Associate Grace Blackford 630-359-9358 [email protected] OFFICES 102 N. Haven Road, Elmhurst, IL 60126–2970 630-941-2030 / Fax: 630-941-3210 http://downbeat.com [email protected] CUSTOMER SERVICE 877-904-5299 / [email protected] CONTRIBUTORS Senior Contributors: Michael Bourne, Aaron Cohen, Howard Mandel, John McDonough Atlanta: Jon Ross; Boston: Fred Bouchard, Frank-John Hadley; Chicago: Alain Drouot, Michael Jackson, Jeff Johnson, Peter Margasak, Bill Meyer, Paul Natkin, Howard Reich; Indiana: Mark Sheldon; Los Angeles: Earl Gibson, Andy Hermann, Sean J. O’Connell, Chris Walker, Josef Woodard, Scott Yanow; Michigan: John Ephland; Minneapolis: Andrea Canter; Nashville: Bob Doerschuk; New Orleans: Erika Goldring, Jennifer Odell; New York: Herb Boyd, Bill Douthart, Philip Freeman, Stephanie Jones, Matthew Kassel, Jimmy Katz, Suzanne Lorge, Phillip Lutz, Jim Macnie, Ken Micallef, Bill Milkowski, Allen Morrison, Dan Ouellette, Ted Panken, Tom Staudter, Jack Vartoogian; Philadelphia: Shaun Brady; Portland: Robert Ham; San Francisco: Yoshi Kato, Denise Sullivan; Seattle: Paul de Barros; Washington, D.C.: Willard Jenkins, John Murph, Michael Wilderman; Canada: J.D. Considine, James Hale; France: Jean Szlamowicz; Germany: Hyou Vielz; Great Britain: Andrew Jones; Portugal: José Duarte; Romania: Virgil Mihaiu; Russia: Cyril Moshkow.