Study on ID Documents” Author: WP3 Editors: Dr
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Electronic Identification (E-ID)
EXPLAINING INTERNATIONAL IT APPLICATION LEADERSHIP: Electronic Identification Daniel Castro | September 2011 Explaining International Leadership: Electronic Identification Systems BY DANIEL CASTRO SEPTEMBER 2011 ITIF ALSO EXTENDS A SPECIAL THANKS TO THE SLOAN FOUNDATION FOR ITS GENEROUS SUPPORT FOR THIS SERIES. SEPTEMBER 2011 THE INFORMATION TECHNOLOGY & INNOVATION FOUNDATION | SEPTEMBER 2011 PAGE II TABLE OF CONTENTS Executive Summary ........................................................................................................ V Introduction..................................................................................................................... 1 Background ....................................................................................................................... 1 Box 1: Electronic Passports ............................................................................................. 3 Terminology and Technology ........................................................................................... 3 Electronic Signatures, Digital Signatures and Digital Certificates ............................... 3 Identification, Authentication and Signing ................................................................ 4 Benefits of e-ID Systems ............................................................................................ 5 Electronic Identification Systems: Deployment and Use .............................................. 6 Country Profiles ............................................................................................................. -

The Case of the National Identity Card in the UK Paul Beynon-Davies University of Wales, Swansea, [email protected]
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by AIS Electronic Library (AISeL) Association for Information Systems AIS Electronic Library (AISeL) European Conference on Information Systems ECIS 2005 Proceedings (ECIS) 2005 Personal Identification in the Information Age: The Case of the National Identity Card in the UK Paul Beynon-Davies University of Wales, Swansea, [email protected] Follow this and additional works at: http://aisel.aisnet.org/ecis2005 Recommended Citation Beynon-Davies, Paul, "Personal Identification in the Information Age: The asC e of the National Identity Card in the UK" (2005). ECIS 2005 Proceedings. 27. http://aisel.aisnet.org/ecis2005/27 This material is brought to you by the European Conference on Information Systems (ECIS) at AIS Electronic Library (AISeL). It has been accepted for inclusion in ECIS 2005 Proceedings by an authorized administrator of AIS Electronic Library (AISeL). For more information, please contact [email protected]. PERSONAL IDENTIFICATION IN THE INFORMATION AGE: THE CASE OF THE NATIONAL IDENTITY CARD IN THE UK Paul Beynon-Davies, European Business Management School, University of Wales Swansea, Singleton Park, Swansea, UK, [email protected] Abstract The informatics infrastructure supporting the Information Society requires the aggregation of data about individuals in electronic records. Such data structures demand that individuals be uniquely identified and this is critical to the necessary processes of authentication, identification and enrolment associated with the use of e-Business, e-Government and potentially e-Democracy systems. It is also necessary to the representation of human interactions as data transactions supporting various forms of governance structure: hierarchies, markets and networks. -

The Portuguese and the European Citizen Cards
Contributions to governmental eID platforms: The Portuguese and the European Citizen Cards Master’s Thesis Manuel Fernando V. Preliteiro Contributions to governmental eID platforms: The Portuguese and the European Citizen Cards THESIS regarding the research leading to the attainment of the degree of MASTER in Computer Science Engineering - Computation and Intelligent Systems by Manuel Fernando V. Preliteiro RELiablE And SEcure Computation Group Departamento de Informática MULTICERT Universidade da Beira Interior Rua Sidónio Pais Covilhã, Portugal Porto, Portugal www.di.ubi.pt www.multicert.com Copyright © 2009 by Manuel Fernando V. Preliteiro. All rights reserved. No part of this publication can be reproduced, stored in a retrieval system, or transmitted, in any form or by any means, electronic, mechanical, photocopying, recording, or otherwise, without the previous written permission of the author. Cover image: Universidade da Beira Interior Heraldry. Contributions to governmental eID platforms: The Portuguese and the European Citizen Cards Author: Manuel Fernando V. Preliteiro Student Id: m1244 Email: [email protected] Abstract This thesis presents two main levels contributions. The first contribution lies in the context of the STORK project. As a first step to the design of an integrated, uniform and secure European eID platform, a feasibility study was conducted and a small demonstrator was developed as a proof of concept. As a result of such task, several STORK deliverables were submitted along a contribution for the Porvoo Group regarding the current state of eID across Europe. This work also benefits the second contribution. Second, it is introduced a new middleware solution for the Portuguese Elec- tronic Citizen Card. -

Criminal Background Check Procedures
Shaping the future of international education New Edition Criminal Background Check Procedures CIS in collaboration with other agencies has formed an International Task Force on Child Protection chaired by CIS Executive Director, Jane Larsson, in order to apply our collective resources, expertise, and partnerships to help international school communities address child protection challenges. Member Organisations of the Task Force: • Council of International Schools • Council of British International Schools • Academy of International School Heads • U.S. Department of State, Office of Overseas Schools • Association for the Advancement of International Education • International Schools Services • ECIS CIS is the leader in requiring police background check documentation for Educator and Leadership Candidates as part of the overall effort to ensure effective screening. Please obtain a current police background check from your current country of employment/residence as well as appropriate documentation from any previous country/countries in which you have worked. It is ultimately a school’s responsibility to ensure that they have appropriate police background documentation for their Educators and CIS is committed to supporting them in this endeavour. It is important to demonstrate a willingness and effort to meet the requirement and obtain all of the paperwork that is realistically possible. This document is the result of extensive research into governmental, law enforcement and embassy websites. We have tried to ensure where possible that the information has been obtained from official channels and to provide links to these sources. CIS requests your help in maintaining an accurate and useful resource; if you find any information to be incorrect or out of date, please contact us at: [email protected]. -

Convergence of Government Programs with Other Card Sectors
DOCUMENT SECURITY ISSUES Part of a Series of Datacard Group White Papers for the Secure Document Issuer CONVERGENCE OF GOVERNMENT PROGRAMS WITH OTHER CARD SECTORS Overview Unprecedented growth in the demand for optimum national security throughout the globe has resulted in an expanding electronic identity document industry with smart technology leading the field. The rapid development of e-passports and identity card schemes is, perhaps, mirrored only by the 1990s smart card boom in the financial sector, which spawned the plastic card. National and international security is driving change with processes and technologies to enhance the security of documents. Many technologies are converging in the use and application of identification cards. MARCH 2007 CONVERGENCE OF GOVERNMENT PROGRAMS WITH OTHER CARD SECTORS Developments in Passport Security Machine-readable passports (MRPs) have been in circulation since the 1980s as hand-written passports became less secure in terms of data matching and being open to counterfeiting. Most are standardized by the International Civil Aviation Organisation (ICAO) document 9303, with a special machine readable zone providing the passport holder’s personal information including name, passport number, check digits, nationality, date of birth and sex. The passport expiration date and personal ID number, where applicable, can also be read. Between 2003 and 2006 the United States progressively introduced regulations making MRPs mandatory for anyone entering the US under the Visa Waiver Scheme. This means faster processing at immigration and secure matching of data. Since their introduction, MRPs are evolving to accommodate chip technology and biometric information – particularly since the ICAO recommendations are for biometrics using facial recognition technology and high capacity contactless integrated circuit chips. -

Royal Holloway University of London
Review and Analysis of Current and Future European e-ID Schemes Siddhartha Arora Technical Report RHUL-MA-2008-07 15 January 2008 Royal Holloway University of London Department of Mathematics Roal Holloway, University of London Egham, Surrey TW20 0EX, England http://www.rhul.ac.uk/mathematics/techreports Review and Analysis of Current and Future European e-ID Card Schemes Siddhartha ARORA – [email protected] Supervisor: Dr. Michael J Ganley Royal Holloway, University of London Submitted as part of the requirements for the award of the MSc in Information Security of the University of London. Note: After submission of this document, minor typographical changes were made on August 3rd 2007. CONTENTS 1. EXECUTIVE SUMMARY 6 2. INTRODUCTION 7 2.1 SCOPE & OBJECTIVES 8 2.1.1 SCOPE RELATING TO E-ID CARDS 8 2.1.2 PROJECT OBJECTIVES 8 2.1.3 OUT OF SCOPE 8 2.2 MOTIVATION FOR E-ID CARD IMPLEMENTATIONS 9 2.2.1 E-GOVERNMENT SERVICES 9 2.3 INFORMATION SECURITY & E-ID CARDS 10 3. INTRODUCING IDENTITY 12 3.1 IDENTITY 12 3.2 ALLEGIANCE, CITIZENSHIP & NATIONALITY 13 3.3 IDENTITY DOCUMENTS 14 3.3.1 THE PASSPORT 14 3.3.2 SEED IDENTITY DOCUMENTS 15 3.4 THE ELECTRONIC IDENTITY (E-ID) 15 3.5 THE NATIONAL E-ID CARD 16 3.5.1 SECURE SIGNATURE CREATION DEVICES (SSCD) 17 4. E-ID CARD APPLICATIONS 18 4.1 APPLICATION USERS 18 4.2 BASE FUNCTIONALITY 18 4.3 GOVERNMENT APPLICATIONS 18 4.3.1 DEPLOYED E-GOVERNMENT APPLICATIONS 19 4.3.2 NON-GOVERNMENTAL AND OTHER APPLICATIONS 21 4.4 POSSIBLE FUTURE/OTHER APPLICATIONS 21 4.4.1 IDENTITY MIXER 22 5. -

Limite En Questionnaire About the State of Play of Identity Cards
COUNCIL OF Brussels, 31 May 2010 THE EUROPEAN UNION 9949/10 LIMITE FAUXDOC 10 COMIX 373 NOTE from: General Secretariat to: Working Party on Frontiers/False documents - Mixed Committee (EU-Iceland/Liechtenstein/Norway/Switzerland) Prev. doc. 5299/1/10 REV 1 FAUXDOC 2 COMIX 42 Subject: State of play concerning the electronic identity cards in the EU Member States Delegations will find below a compilation of Member States replies to the questionnaire on the state of play concerning the electronic identity cards in the EU Member States, as set out in doc. 5299/1/10 REV 1 FAUXDOC 2 COMIX 42. 9949/10 GG/cr 1 DG H 1 A LIMITE EN QUESTIONNAIRE ABOUT THE STATE OF PLAY OF IDENTITY CARDS 1. Does your country issues identity cards? 2. (if yes) What kind? (traditional or electronic ID, RF chip or Contact chip) What usable data size/capacity? 3. (if not) Has your country planned the issuance of identity cards in the near future? 4. What material is the card constructed from (e.g. polycarbonate)? 5. Does your country issue a card in ICAO TD1 or TD3 format? 6. How are the electronically stored data protected? BAC, EAC? 7. What kind of biometric data are electronically stored in the identity card and by which authorities? 8. Is any other information electronically stored on the identity card, (e.g. certificates)? 9. Does your country have a centralized or decentralized system for the issuance of identity cards and/or storage of biographic or biometric data? 10. How much does the citizen pay for the card? 11. -

Common Reporting Standard
COMMON REPORTING STANDARD TAX IDENTIFICATION NUMBERS LEAFLET Version updated as of October 31th, 2019 Disclaimer: The present informative document, subject to modification, is communicated for information purposes only and has no contractual value. This document is defined based on the information provided by the OECD portal. It contains information that it is the sole responsibility of each country and is (i) of a general nature only and not intended to address the specific circumstances of any particular individual or entity, (ii) not necessarily comprehensive, complete, accurate or up to date,(iii) sometimes linked to external sites over which SG Group has no control and for which SG Group assumes no responsibility and (iv) not professional or legal advice. If you need specific advice, you should always consult a professional tax advisor. TAX IDENTIFICATION NUMBERS This document provides an overview of domestic rules in the countries listed below governing the issuance, structure, use and validity of Tax Identification Numbers (“TIN”) or their functional equivalents. It is split into two sections: Countries that have already published the information on the OECD portal and can 1 be accessed by clicking on the name of the country below Cook Andorra Hungary Malaysia Saudi Arabia Islands Argentina Costa Rica Iceland Malta Seychelles Marshall Aruba Croatia India Islands Singapore Australia Curacao Indonesia Mauritius Slovak Republic Ireland Austria Mexico Cyprus Slovenia Isle of Man Azerbaijan Czech Montserrat Republic South Africa Bahrain -
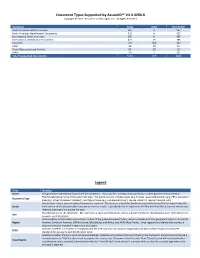
Document Types Supported by Assureid™ V4.4.4260.0 Legend
Document Types Supported by AssureID™ V4.4.4260.0 Copyright © 2016 - AssureTec Technologies, Inc. All Rights Reserved. Summary Total ICAO Non-ICAO North American Driver's Licenses 967 0 967 North American Identification Documents 425 6 419 International Driver's Licenses 387 0 387 International Identification Documents 425 39 386 Passports 743 604 139 Visas 59 49 10 Travel Documents and Permits 83 50 33 Other 103 1 102 Total Supported Documents 3192 749 2443 Legend Term Meaning Issuer The government jurisdiction that issued the document. This could be a country, state, province, or other government jurisdiction The full descriptive name of the document type. The name typically includes issuer (e.g. France), issuer abbreviation (e.g. FRA), document Document Type class (e.g. driver’s license or passport), and type of issue (e.g. commercial driver’s license, under 21, learner’s permit, etc.) Jurisdictions release new versions of documents regularly. The Series is a label that has been assigned by AssureTec to uniquely identify Series each version of the document (also known as series or issue). Typically the Series represents the first year that the document version was released, but that is not always the case The physical size of the document. ID1 represents a card-sized document such as a driver’s license or identification card. ID3 represents a Size passport-sized document Certain editions of AssureID only include a subset of the global document library, which is divided into four geographic regions: NA=North Region America, SA=South America, EMEA=Europe, Middle East, and Africa, and APAC=Asia-Pacific. -

Unicard; National Identity Evolution
The International Journal of Engineering and Science (IJES) || Volume || 9 || Issue || 01 || Series II || Pages || PP 84-102| 2020 || ISSN (e): 2319-1813 ISSN (p): 23-19-1805 Unicard; National Identity Evolution Hussam Elbehiery1, Khaled Elbehiery2 1Computer Networks Department, Ahram Canadian University (ACU), Egypt 2Computer Information Systems Department, DeVry University, USA Corresponding Author:Hussam Elbehiery --------------------------------------------------------ABSTRACT----------------------------------------------------------- The use of information technology in our daily lives has been on the rise. The ordinary governmental based identity system provides a vital foundation of authoritative sources of trust, but they usually focus on delivering official routine services rather than providing a choice of other services, privacy protection, and interoperability. Looking deep into the current identity system, it is widely known that, the identification, verification, and account creation is time consuming and duplicated across multiple systems, as a result, the future should be working towards identity system that demonstrates portability of trust and the ability for individuals to take control of their identity destiny. We are in a desperate need for a new secure electronic identity for citizens in a form "Unicard", a unique identifier used across multiple services, not only the essential services such as electronic passports, driving licenses, issuing citizens personal certificates such as birth certificates, marriage and divorce certificates, government benefits, schooling, healthcare system but also high security access cards such as credit cards. The unicard should be scalable and flexible to accommodate with other services anytime and anywhere that could be beneficial to the citizen such as bank account, mobile phone, utility bills, etc. or it could be necessary for the national security such as credit card, phone records transactions, and more to assure reducing the fraud, identity theft, and terrorism. -
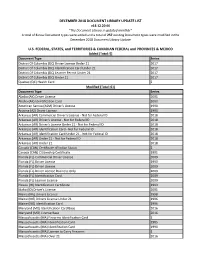
December 2018 Document Library Update List U.S
DECEMBER 2018 DOCUMENT LIBRARY UPDATE LIST v18.12.20.66 *The Document Library is updated monthly* A total of 6 new Document types were added and a total of 257 existing Document types were modified in the December 2018 Document Library Update U.S. FEDERAL, STATES, and TERRITORIES & CANADIAN FEDERAL and PROVINCES & MEXICO Added (Total: 5) Document Type Series District Of Columbia (DC) Driver License Under 21 2017 District Of Columbia (DC) Identification Card Under 21 2017 District Of Columbia (DC) Learner Permit Under 21 2017 District Of Columbia (DC) Under 21 2017 Quebec (QC) Health Card 2 Modified (Total: 61) Document Type Series Alaska (AK) Driver License 2001 Alaska (AK) Identification Card 2000 American Samoa (ASM) Driver's License 1990 Arizona (AZ) Driver License 1990 Arkansas (AR) Commercial Driver's License - Not for Federal ID 2018 Arkansas (AR) Driver's License - Not for Federal ID 2018 Arkansas (AR) Driver's License Under 21 - Not for Federal ID 2018 Arkansas (AR) Identification Card - Not for Federal ID 2018 Arkansas (AR) Identification Card Under 21 - Not for Federal ID 2018 Arkansas (AR) Under 21 - Not for Federal ID 2018 Arkansas (AR) Under 21 2018 Canada (CAN) Certificate of Indian Status 2 Canada (CAN) Citizenship Certificate 1991 Florida (FL) Commercial Driver License 2009 Florida (FL) Driver License 1990 Florida (FL) Driver License 2009 Florida (FL) Driver License Business Only 2009 Florida (FL) Identification Card 2009 Florida (FL) Learner License 2009 Hawaii (HI) Identification Certificate 1993 Idaho (ID) Driver's -
TAX IDENTIFICATION NUMBERS (Tins)
Where to find TINs? en – English TAX IDENTIFICATION NUMBERS (TINs) Subject sheet: where to find TINs? 1. AT – Austria ................................................................................................................................ 2 2. BE – Belgium ............................................................................................................................... 2 3. BG – Bulgaria .............................................................................................................................. 3 4. CY – Cyprus ................................................................................................................................ 6 5. CZ – Czech Republic .................................................................................................................. 7 6. DE – Germany ........................................................................................................................... 10 7. DK – Denmark ........................................................................................................................... 12 8. EE – Estonia .............................................................................................................................. 13 9. EL – Greece .............................................................................................................................. 16 10. ES – Spain .............................................................................................................................. 19 11. FI – Finland