SNAP Command Line Tutorial
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Network Monitoring & Management Using Cacti
Network Monitoring & Management Using Cacti Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/) Introduction Network Monitoring Tools Availability Reliability Performance Cact monitors the performance and usage of devices. Introduction Cacti: Uses RRDtool, PHP and stores data in MySQL. It supports the use of SNMP and graphics with RRDtool. “Cacti is a complete frontend to RRDTool, it stores all of the necessary information to create graphs and populate them with data in a MySQL database. The frontend is completely PHP driven. Along with being able to maintain Graphs, Data Sources, and Round Robin Archives in a database, cacti handles the data gathering. There is also SNMP support for those used to creating traffic graphs with MRTG.” Introduction • A tool to monitor, store and present network and system/server statistics • Designed around RRDTool with a special emphasis on the graphical interface • Almost all of Cacti's functionality can be configured via the Web. • You can find Cacti here: http://www.cacti.net/ Getting RRDtool • Round Robin Database for time series data storage • Command line based • From the author of MRTG • Made to be faster and more flexible • Includes CGI and Graphing tools, plus APIs • Solves the Historical Trends and Simple Interface problems as well as storage issues Find RRDtool here:http://oss.oetiker.ch/rrdtool/ RRDtool Database Format General Description 1. Cacti is written as a group of PHP scripts. 2. The key script is “poller.php”, which runs every 5 minutes (by default). -

Munin Documentation Release 2.0.44
Munin Documentation Release 2.0.44 Stig Sandbeck Mathisen <[email protected]> Dec 20, 2018 Contents 1 Munin installation 3 1.1 Prerequisites.............................................3 1.2 Installing Munin...........................................4 1.3 Initial configuration.........................................7 1.4 Getting help.............................................8 1.5 Upgrading Munin from 1.x to 2.x..................................8 2 The Munin master 9 2.1 Role..................................................9 2.2 Components.............................................9 2.3 Configuration.............................................9 2.4 Other documentation.........................................9 3 The Munin node 13 3.1 Role.................................................. 13 3.2 Configuration............................................. 13 3.3 Other documentation......................................... 13 4 The Munin plugin 15 4.1 Role.................................................. 15 4.2 Other documentation......................................... 15 5 Documenting Munin 21 5.1 Nomenclature............................................ 21 6 Reference 25 6.1 Man pages.............................................. 25 6.2 Other reference material....................................... 40 7 Examples 43 7.1 Apache virtualhost configuration.................................. 43 7.2 lighttpd configuration........................................ 44 7.3 nginx configuration.......................................... 45 7.4 Graph aggregation -

Automatic Placement of Authorization Hooks in the Linux Security Modules Framework
Automatic Placement of Authorization Hooks in the Linux Security Modules Framework Vinod Ganapathy [email protected] University of Wisconsin, Madison Joint work with Trent Jaeger Somesh Jha [email protected] [email protected] Pennsylvania State University University of Wisconsin, Madison Context of this talk Authorization policies and their enforcement Three concepts: Subjects (e.g., users, processes) Objects (e.g., system resources) Security-sensitive operations on objects. Authorization policy: A set of triples: (Subject, Object, Operation) Key question: How to ensure that the authorization policy is enforced? CCS 2005 Automatic Placement of Authorization Hooks in the Linux Security Modules Framework 2 Enforcing authorization policies Reference monitor consults the policy. Application queries monitor at appropriate locations. Can I perform operation OP? Reference Monitor Application to Policy be secured Yes/No (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) CCS 2005 Automatic Placement of Authorization Hooks in the Linux Security Modules Framework 3 Linux security modules framework Framework for authorization policy enforcement. Uses a reference monitor-based architecture. Integrated into Linux-2.6 Linux Kernel Reference Monitor Policy (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) CCS 2005 Automatic Placement of Authorization Hooks in the Linux Security Modules Framework 4 Linux security modules framework Reference monitor calls (hooks) placed appropriately in the Linux kernel. Each hook is an authorization query. Linux Kernel Reference Monitor Policy (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) (subj.,obj.,oper.) Hooks CCS 2005 Automatic Placement of Authorization Hooks in the Linux Security Modules Framework 5 Linux security modules framework Authorization query of the form: (subj., obj., oper.)? Kernel performs operation only if query succeeds. -
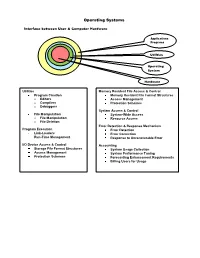
Operating Systems
Operating Systems Interface between User & Computer Hardware Applications Programs Utilities Operating System Hardware Utilities Memory Resident File Access & Control Program Creation Memory Resident File Format Structures o Editors Access Management o Compilers Protection Schemes o Debuggers System Access & Control File Manipulation System-Wide Access o File Manipulation Resource Access o File Deletion Error Detection & Response Mechanism Program Execution Error Detection Link-Loaders Error Correction Run-Time Management Response to Unrecoverable Error I/O Device Access & Control Accounting Storage File Format Structures System Usage Collection Access Management System Performance Tuning Protection Schemes Forecasting Enhancement Requirements Billing Users for Usage Resource Manager O/S KernelKernel I/O Controller Printers, Keyboards, I/O Controller Monitors, Portions of Cameras, the O/S Etc. currently in use Computer Main System Memory Portions of Various I/O Application Devices Programs Currently in use Operating System Data Application Programs I/O Controller Storage Processor Processor Data Processor Processor Operation Allocation of Main Memory is made jointly by both the O/S and Memory Management Hardware O/S controls access to I/O devices by Application Programs O/S controls access to and use of files O/S controls access to and use of the processors, i.e., how much time can be allocated to the execution of a particular Application Program Classification of Operating Systems Interactive O/S Keyboard & Monitor Access to O/S Immediate, -

Masked Graph Modeling for Molecule Generation ✉ Omar Mahmood 1, Elman Mansimov2, Richard Bonneau 3 & Kyunghyun Cho 2
ARTICLE https://doi.org/10.1038/s41467-021-23415-2 OPEN Masked graph modeling for molecule generation ✉ Omar Mahmood 1, Elman Mansimov2, Richard Bonneau 3 & Kyunghyun Cho 2 De novo, in-silico design of molecules is a challenging problem with applications in drug discovery and material design. We introduce a masked graph model, which learns a dis- tribution over graphs by capturing conditional distributions over unobserved nodes (atoms) and edges (bonds) given observed ones. We train and then sample from our model by iteratively masking and replacing different parts of initialized graphs. We evaluate our 1234567890():,; approach on the QM9 and ChEMBL datasets using the GuacaMol distribution-learning benchmark. We find that validity, KL-divergence and Fréchet ChemNet Distance scores are anti-correlated with novelty, and that we can trade off between these metrics more effec- tively than existing models. On distributional metrics, our model outperforms previously proposed graph-based approaches and is competitive with SMILES-based approaches. Finally, we show our model generates molecules with desired values of specified properties while maintaining physiochemical similarity to the training distribution. 1 Center for Data Science, New York University, New York, NY, USA. 2 Department of Computer Science, Courant Institute of Mathematical Sciences, New ✉ York, NY, USA. 3 Center for Genomics and Systems Biology, New York University, New York, NY, USA. email: [email protected] NATURE COMMUNICATIONS | (2021) 12:3156 | https://doi.org/10.1038/s41467-021-23415-2 | www.nature.com/naturecommunications 1 ARTICLE NATURE COMMUNICATIONS | https://doi.org/10.1038/s41467-021-23415-2 he design of de novo molecules in-silico with desired prop- enable more informative comparisons between models that use Terties is an essential part of drug discovery and materials different molecular representations. -

The Seeds of Rural Resilience
NEWS & VIEWS FROM THE SUSTAINABLE SOUTHWEST Growing a Regional Food System THE SEEDS OF RURAL RESILIENCE October 2017 NORTHERN NEW MEXICO’S LARGEST DISTRIBUTION NEWSPAPER Vol. 9 No. 10 2 Green Fire Times • October 2017 www.GreenFireTimes.com Is Your Roof Winter Ready? Whether your roof is currently leaking or you’d like to restore your roof before it fails, Fix My Roof is the right choice. Call today for a free roof assessment! www.GreenFireTimes.com Green Fire Times • October 2017 3 YOU’LL LOVE WHAT YOU SEE! PROGRAM PARTNERS: FRIDAY SATURDAY OCT 27 NOV 14 7:30 PM 7:30 PM Sponsored by The L.A. Grow the Growers Browns Dance Farm Training 5 Project Business Incubation A CULTIVATING BERNALILLO COUNTY INITIATIVE bernalillo Applications for the 2018 Opencounty Space internships now available Lensic.org 505-988-1234 For more information NONPROFIT • COMMUNITY FUNDED SERVICE CHARGES APPLY AT ALL POINTS OF PURCHASE A special thanks to our www.bernco.gov/growthegrowers 2017/2018 sponsor: Find Your Future in ENGINEERING @Northern New Mexico College NORTHERN The most affordable 4-year now offering college in the Southwest classes at Santa Fe HEC! Northern Engineering programs include: n ABET-accredited Bachelor in INFORMATION ENGINEERING Tech (IET) n Ask about our new CYBERSECURITY concentration in IET Schedule your campus visit today! n Bachelor in ELECTROMECHANICAL Engineering/Solar Energy Concentration CALL 505.747.2111 or visit nnmc.edu n Associate of Applied Science degrees in RENEWABLE ENERGY and ELECTRICAL TECH 4 Green Fire Times Oc tober 2017 www.GreenFireTimes.com Vol. 9, No. 10 October 2017 Issue No. -

AD Bridge User Guide
AD Bridge User Guide May 2019 Legal Notice © Copyright 2019 Micro Focus or one of its affiliates. The only warranties for products and services of Micro Focus and its affiliates and licensors (“Micro Focus”) are set forth in the express warranty statements accompanying such products and services. Nothing herein should be construed as constituting an additional warranty. Micro Focus shall not be liable for technical or editorial errors or omissions contained herein. The information contained herein is subject to change without notice. For additional information, such as certification-related notices and trademarks, see http://www.microfocus.com/about/legal/. Contents About This Guide 5 1 Getting Started 7 2 Installing AD Bridge 9 Linux Requirements and Supported Platforms . 9 Linux Requirements . 9 Supported Linux Platforms. 10 Installing the AD Bridge Linux Agent. 11 Licensing the Linux Agent . 12 Joining Active Directory - Post Installation . 13 Installing the AD Bridge GPEdit Extension . 13 3 Managing Linux GPO Settings 15 Accessing or Creating Group Policy Objects . 15 Configuring Linux GPO Settings . 16 Managing Linux Agent Services with GPOs . 17 Importing Custom Configuration File Settings. 18 Managing Linux Applications with GPOs . 18 Managing User Logins with GPOs . 19 Viewing Policy Injection on a Linux Agent. 20 A Appendix 21 Linux Agent GPO Settings . 21 Linux Agent Commands and Lookups . 22 GPO Best Practices . 23 Contents 3 4 About This Guide The AD Bridge User Guide provides information to help you understand, install, configure, and employ the Micro Focus AD Bridge product to help manage your enterprise environment. Audience This guide is written for administrators and users who will use Micro Focus AD Bridge to more effectively manage Active Directory and group policies in a cross-platform environment. -

Chapter 10 Introduction to Batch Files
Instructor’s Manual Chapter 10 Lecture Notes Introduction to Batch Files Chapter 10 Introduction to Batch Files LEARNING OBJECTIVES 1. Compare and contrast batch and interactive processing. 2. Explain how batch files work. 3. Explain the purpose and function of the REM, ECHO, and PAUSE commands. 4. Explain how to stop or interrupt the batch file process. 5. Explain the function and use of replaceable parameters in batch files. 6. Explain the function of pipes, filters, and redirection in batch files. STUDENT OUTCOMES 1. Use Edit to write batch files. 2. Use COPY CON to write batch files. 3. Write and execute a simple batch file. 4. Write a batch file to load an application program. 5. Use the REM, PAUSE, and ECHO commands in batch files. 6. Terminate a batch file while it is executing. 7. Write batch files using replaceable parameters. 8. Write a batch file using pipes, filters, and redirection. CHAPTER SUMMARY 1. Batch processing means running a series of instructions without interruption. 2. Interactive processing allows the user to interface directly with the computer and update records immediately. 3. Batch files allow a user to put together a string of commands and execute them with one command. 4. Batch files must have the .BAT or .CMD file extension. 5. Windows looks first internally for a command, then for a .COM files extension, then for a .EXE file extension, and finally for a .BAT or .CMD file extension. 6. Edit is a full-screen text editor used to write batch files. 7. A word processor, if it has a means to save files in ASCII, can be used to write batch files. -

Uni Hamburg – Mainframe Summit 2010 Z/OS – the Mainframe Operating System
Uni Hamburg – Mainframe Summit 2010 z/OS – The Mainframe Operating System Appendix 2 – JES and Batchprocessing Redelf Janßen IBM Technical Sales Mainframe Systems [email protected] © Copyright IBM Corporation 2010 Course materials may not be reproduced in whole or in part without the prior written permission of IBM. 4.0.1 Introduction to the new mainframe Chapter 7: Batch processing and the Job Entry Subsystem (JES) © Copyright IBM Corp., 2010. All rights reserved. Introduction to the new mainframe Chapter 7 objectives Be able to: • Give an overview of batch processing and how work is initiated and managed in the system. • Explain how the job entry subsystem (JES) governs the flow of work through a z/OS system. © Copyright IBM Corp., 2010. All rights reserved. 3 Introduction to the new mainframe Key terms in this chapter • batch processing • procedure • execution • purge • initiator • queue • job • spool • job entry subsystem (JES) • symbolic reference • output • workload manager (WLM) © Copyright IBM Corp., 2010. All rights reserved. 4 Introduction to the new mainframe What is batch processing? Much of the work running on z/OS consists of programs called batch jobs. Batch processing is used for programs that can be executed: • With minimal human interaction • At a scheduled time or on an as-needed basis. After a batch job is submitted to the system for execution, there is normally no further human interaction with the job until it is complete. © Copyright IBM Corp., 2010. All rights reserved. 5 Introduction to the new mainframe What is JES? In the z/OS operating system, JES manages the input and output job queues and data. -

Approaches to Optimize Batch Processing on Z/OS
Front cover Approaches to Optimize Batch Processing on z/OS Apply the latest z/OS features Analyze bottlenecks Evaluate critical path Alex Louwe Kooijmans Elsie Ramos Jan van Cappelle Lydia Duijvestijn Tomohiko Kaneki Martin Packer ibm.com/redbooks Redpaper International Technical Support Organization Approaches to Optimize Batch Processing on z/OS October 2012 REDP-4816-00 Note: Before using this information and the product it supports, read the information in “Notices” on page v. First Edition (October 2012) This edition applies to all supported z/OS versions and releases. This document created or updated on October 24, 2012. © Copyright International Business Machines Corporation 2012. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . .v Trademarks . vi Preface . vii The team who wrote this paper . vii Now you can become a published author, too! . viii Comments welcome. viii Stay connected to IBM Redbooks . ix Chapter 1. Getting started . 1 1.1 The initial business problem statement. 2 1.2 How to clarify the problem statement . 3 1.3 Process to formulate a good problem statement . 3 1.4 How to create a good business case . 5 1.5 Analysis methodology . 6 1.5.1 Initialization . 6 1.5.2 Analysis. 6 1.5.3 Implementation . 10 Chapter 2. Analysis steps. 13 2.1 Setting the technical strategy . 14 2.2 Understanding the batch landscape . 15 2.2.1 Identifying where batch runs and the available resources . 15 2.2.2 Job naming conventions . 15 2.2.3 Application level performance analysis. -

Operational Semantics with Hierarchical Abstract Syntax Graphs*
Operational Semantics with Hierarchical Abstract Syntax Graphs* Dan R. Ghica Huawei Research, Edinburgh University of Birmingham, UK This is a motivating tutorial introduction to a semantic analysis of programming languages using a graphical language as the representation of terms, and graph rewriting as a representation of reduc- tion rules. We show how the graphical language automatically incorporates desirable features, such as a-equivalence and how it can describe pure computation, imperative store, and control features in a uniform framework. The graph semantics combines some of the best features of structural oper- ational semantics and abstract machines, while offering powerful new methods for reasoning about contextual equivalence. All technical details are available in an extended technical report by Muroya and the author [11] and in Muroya’s doctoral dissertation [21]. 1 Hierarchical abstract syntax graphs Before proceeding with the business of analysing and transforming the source code of a program, a com- piler first parses the input text into a sequence of atoms, the lexemes, and then assembles them into a tree, the Abstract Syntax Tree (AST), which corresponds to its grammatical structure. The reason for preferring the AST to raw text or a sequence of lexemes is quite obvious. The structure of the AST incor- porates most of the information needed for the following stage of compilation, in particular identifying operations as nodes in the tree and operands as their branches. This makes the AST algorithmically well suited for its purpose. Conversely, the AST excludes irrelevant lexemes, such as separators (white-space, commas, semicolons) and aggregators (brackets, braces), by making them implicit in the tree-like struc- ture. -

List of New Applications Added in ARL #2517
List of New Applications Added in ARL #2517 Application Name Publisher ActiveEfficiency 1.10 1E ACL Add-In 14.0 ACL Services ACL for Windows 14.2 ACL Services ACL for Windows 14.1 ACL Services Direct Link 7.5 ACL Services ACL Add-In 1.1 ACL Services Creative Cloud Connection 5 Adobe Experience Manager forms 6.5 Adobe Elements Auto Analyzer 12.0 Adobe Token Resolver 3.4 Adobe Token Resolver 3.6 Adobe LogTransport 1.6 Adobe LogTransport 2.4 Adobe IPC Broker 5.6 Adobe Data Workbench Adobe Token Resolver 3.5 Adobe Token Resolver 3.7 Adobe Dimension 3.2 Adobe Photo Downloader 8.0 Adobe LogTransport 2.2 Adobe GC Invoker Utility 4.5 Adobe GC Client 5.0 Adobe Crash Reporter 2.0 Adobe Crash Reporter 2.1 Adobe GC Invoker Utility 6.4 Adobe Dynamic Link Media Server 12.1 Adobe Token Resolver 3.3 Adobe Token Resolver 4.7 Adobe GC Client 4.4 Adobe Genuine Software Integrity Service 6.4 Adobe Creative Cloud Libraries 3 Adobe Token Resolver 3.9 Adobe Token Resolver 5.0 Adobe Genuine Software Integrity Service 6.5 Adobe Create PDF 17.1 Adobe Crash Reporter 1.5 Adobe Notification Client 4.9 Adobe GC Client 6.4 Adobe GC Client 6.5 Adobe Crash Reporter 1.6 Adobe Crash Reporter 2.2 Adobe Crash Reporter 2.4 Adobe GPU Sniffer 19.0 Adobe Token Generator 7.0 Adobe Token Resolver 3.8 Adobe LogTransport 1.5 Adobe InDesign Server CC (2020) Adobe GC Invoker Utility 5.0 Adobe GC Invoker Utility 6.5 Adobe RED Importer Plugin Unspecified Adobe Token Generator 8.0 Adobe GC Client 1.2 Adobe GC Client 4.5 Adobe EmailNotificationPlugin 11.0 Apple BatteryUIKit 1.0 Apple