Appendix A: Navy Activity Descriptions
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Should the United States Develop and Employ Strategic Information Warfare Capabilities?
Should the United States develop and employ strategic information warfare capabilities? Information technologies have transformed U.S. and, indeed, international society. The ways we socialize, educate and inform ourselves, engage in business and practice our religions have been changed, and in many cases now rely, on digital information and communication. Can warfare—the defense and promotion of our national security and interests—be exempt under any circumstances from developing and employing the latest information strategies? Is this even a choice in the 21st century, much less a hard choice? Information warfare has been variously defined by different analysts but a standard general definition, as provided by the U.S. Air Force is “any action to deny, exploit, corrupt, or destroy the enemy’s information and its functions; protecting ourselves against the actions and exploiting our own information operations.” The goal of information war is now frequently described as “information dominance.” (1) Major General Kenneth Minihan, stated, “information dominance is not ‘my pile of information is bigger than yours’…It is a way of increasing our capabilities by using that information to make right decisions, (and) apply them faster than the enemy can. It is a way to alter the enemy’s entire perception of reality. It is a method of using all the information at our disposal to predict (and affect) what happens tomorrow before the enemy even jumps out of bed and thinks about what to do today.” (2) Pro: Information warfare is not a new concept that arose with the Internet. Information has always been a decisive factor in deciding the victory or defeat of one military force over another. -

Unlocking NATO's Amphibious Potential
November 2020 Perspective EXPERT INSIGHTS ON A TIMELY POLICY ISSUE J.D. WILLIAMS, GENE GERMANOVICH, STEPHEN WEBBER, GABRIELLE TARINI Unlocking NATO’s Amphibious Potential Lessons from the Past, Insights for the Future orth Atlantic Treaty Organization (NATO) members maintain amphibious capabilities that provide versatile and responsive forces for crisis response and national defense. These forces are routinely employed in maritime Nsecurity, noncombatant evacuation operations (NEO), counterterrorism, stability operations, and other missions. In addition to U.S. Marine Corps (USMC) and U.S. Navy forces, the Alliance’s amphibious forces include large ships and associated landing forces from five nations: France, Italy, the Netherlands, Spain, and the United Kingdom (UK). Each of these European allies—soon to be joined by Turkey—can conduct brigade-level operations, and smaller elements typically are held at high readiness for immediate response.1 These forces have been busy. Recent exercises and operations have spanned the littorals of West and North Africa, the Levant, the Gulf of Aden and Arabian Sea, the Caribbean, and the Pacific. Given NATO’s ongoing concerns over Russia’s military posture and malign behavior, allies with amphibious capabilities have also been exploring how these forces could contribute to deterrence or, if needed, be employed as part of a C O R P O R A T I O N combined and joint force in a conflict against a highly some respects, NATO’s ongoing efforts harken back to the capable nation-state. Since 2018, NATO’s headquarters Cold War, when NATO’s amphibious forces routinely exer- and various commands have undertaken initiatives and cised in the Mediterranean and North Atlantic as part of a convened working groups to advance the political intent broader strategy to deter Soviet aggression. -
BA-6, Management Support Because It Includes Studies and Analyses in Support of R&D Efforts
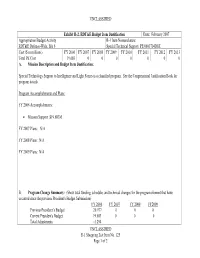
UNCLASSIFIED Exhibit R-2, RDT&E Budget Item Justification Date: February 2007 Appropriation/Budget Activity R-1 Item Nomenclature: RDT&E Defense-Wide, BA 6 Special Technical Support PE 0603704D8Z Cost ($ in millions) FY 2006 FY 2007 FY 2008 FY 2009 FY 2010 FY 2011 FY 2012 FY 2013 Total PE Cost 19.683 0 0 0 0 0 0 0 A. Mission Description and Budget Item Justification: Special Technology Support to Intelligence and Light Forces is a classified program. See the Congressional Justification Book for program details. Program Accomplishments and Plans: FY 2006 Accomplishments: • Mission Support $19.683M FY 2007 Plans: N/A FY 2008 Plans: N/A FY 2009 Plans: N/A B. Program Change Summary: (Show total funding, schedule, and technical changes for the program element that have occurred since the previous President's Budget Submission) FY 2006 FY 2007 FY 2008 FY2009 Previous President’s Budget 20.977 0 0 0 Current President's Budget 19.683 0 0 0 Total Adjustments -1.294 UNCLASSIFIED R-1 Shopping List Item No. 125 Page 1 of 2 UNCLASSIFIED Congressional program reductions Congressional rescissions Congressional increases Other Adjustments -1.294 FY 2006: Congressional add transferred to other activity FY 2007: Funding transferred out of USD-I C. Other Program Funding Summary: Not Applicable D. Acquisition Strategy: Not Applicable E. Performance Metrics: Classified UNCLASSIFIED R-1 Shopping List Item No. 125 Page 2 of 2 UNCLASSIFIED FY 2007 RDT&E,D BUDGET ITEM JUSTIFICATION SHEET DATE: FEBRUARY 2007 Exhibit R-2 BUDGET ACTIVITY: 06 PROGRAM ELEMENT: 0603757D8Z PROGRAM ELEMENT TITLE: TRAINING TRANSFORMATION (T2) PROJECT NUMBER: PROJECT TITLE: GENERAL COMMENTS: As directed in the National Defense Authorization Act for FY 2005, all RDT&E funding for U.S. -

Appendix A. Navy Activity Descriptions
Atlantic Fleet Training and Testing Draft EIS/OEIS June 2017 APPENDIX A Navy Activity Descriptions Appendix A Navy Activity Descriptions Atlantic Fleet Training and Testing Draft EIS/OEIS June 2017 This page intentionally left blank. Appendix A Navy Activity Descriptions Atlantic Fleet Training and Testing Draft EIS/OEIS June 2017 Draft Environmental Impact Statement/Overseas Environmental Impact Statement Atlantic Fleet Training and Testing TABLE OF CONTENTS A. NAVY ACTIVITY DESCRIPTIONS ................................................................................................ A-1 A.1 Description of Sonar, Munitions, Targets, and Other Systems Employed in Atlantic Fleet Training and Testing Events .................................................................. A-1 A.1.1 Sonar Systems and Other Acoustic Sources ......................................................... A-1 A.1.2 Munitions .............................................................................................................. A-7 A.1.3 Targets ................................................................................................................ A-11 A.1.4 Defensive Countermeasures ............................................................................... A-13 A.1.5 Mine Warfare Systems ........................................................................................ A-13 A.1.6 Military Expended Materials ............................................................................... A-16 A.2 Training Activities .................................................................................................. -

The Civil War and Early Submarine Warfare, 1863 Introduction
1 The Civil War and early submarine warfare, 1863 Introduction Civil War combat foreshadowed modern warfare with the introduction of the machine gun, repeater rifles, and trench warfare, and the use of trains to quickly move troops. However, one of the most celebrated tactical innovations of the war was the use of submarines by the Confederate Navy. An early example of this type of naval ingenuity was the CSS Pioneer developed by Horace Lawson Hunley, James McClintock, and Baxter Watson. The Confederates were forced to abandon the Pioneer during testing for fear of capture but she eventually found her way into Union hands, where the submersible was examined and sketched by Ensign David Stauffer of the USS Alexandria. Following the war, the Pioneer was scrapped for metal. Most accounts of actual Civil War submarine combat focus on the sinking of the USS Housatonic by the CSS H. L. Hunley in February 1864, but few mention an earlier but unsuccessful attack by a cigar-shaped vessel, the CSS David, in October 1863. This letter from Union sailor Lewis H. West is a rare eyewitness account of that incident, one of the earliest submarine attacks in naval history. On his first night on board the USS New Ironsides, West experienced the David’s attack. Stealthily cutting through Charleston Bay almost entirely submerged, the David crew attempted to explode a torpedo (what we now refer to as a mine) and in the process nearly destroyed their own vessel. According to West, the “nondescript craft” barely damaged the New Ironsides, and divers found “that not a plate or bolt is started.” The CSS David survived the explosion and the small-arms fire that raked the hull. -

The Importance of the War at Sea During WWI
The Importance of The War At Sea During WWI By: Taylor Pressdee, Anna Ward, Nathan Urquidi What Was the Impact of ‘The War at Sea’? ● Opened a new kind of warfare: Submarine Warfare ● Involved civilians as well as sailors and soldiers ● One of the major reasons that the United States joined the Allies ● Influenced major events during the war: Battle of Jutland, the naval blockade, submarine warfare and the sinking of the Lusitania Who Was Affected By The War at Sea? ● “Total War” ● War At Sea affected civilians as well as soldiers ● Ship Liners, and Coastal cities were in danger of attack ● Starvation was prevalent in specifically Germany because supply ships were being sunk Timeline May 31st 1916 September 1915 Battle of Jutland Germans stop using U-boats February 1st 1916 Germans begin using U-boats again May 7th 1916 Lusitania Sinks Battle of Jutland Battle of Jutland ● Fought on May 31st 1916 ● Only major battle fought at sea ● Fought by the Jutland Peninsula between England and Germany ● Two Admirals in charge of both fleets: Vice Admiral Reinhard Scheer (Left) and Admiral Sir John Jellicoe (Right) The Battle ● British forces intercepted a German message containing a plan to attack them on May 28th ● However, Admiral Scheer postponed the attack due to bad weather ○ Attempted to plan another attack down by the Jutland Peninsula, however Britain intercepted this plan as well ● Vice Admiral Jellicoe moved his fleet down to the Jutland Peninsula, awaiting the attack Aftermath of the Battle ● The British suffered losses, but not nearly -

Torpedo Technology
DRDO MONOGRAPH ERIES NO. I INTRODUCTION TO TORPEDO TECHNOLOGY Rear Adm (Retd) NK Ramanarasaiah, VSM Former Director Naval Science & Technological Laboratory Visakhapatnam DEFEN E RESEARCH & DEVELOPMENT ORGANISATION MINISTR Y OF DEFENCE, GOVT OF INDIA NEW DELHI·II0 011 1993 © 1993, Defence Scientific Information & Documentation Centre (DESIDOC), Delhi-110 054 Cover Photograph (Taken by the author) : The firing of a practice torpedo from a Kamorta class ship. Designed, typeset and printed at DESIDOC, Metcalfe House, Delhi-110 054. uthor r eh ing the' ienti t of the Y ar' award from the then Prime Mini ter ,'mt. Indira ;undhi - 198 ... uthor with Shri R Venkataraman, the then Defence Mini °ter \ hen he vi ited TL in the earl eightee. FOREWORD Oceans have always fascinated man and he has, from early days of civilisation, turned to them for adventure and exploration. Indeed, they have been his 'main highways' for extending his 'empire' and 'trade'. Over the last century, he has been exploiting the waters of the ocean for re ources-living and nonliving-and to fill his unsatiating need for energy. With such a role to play, oceans have been the arena where man has been waging wars to protect his sovereignty over the resources and to subjugate his enemies resulting in 'Armadas'-from Spanish wars to the present. It would not be an overstatement to declare that the 'sea power' to a large extent dictated the outcome of many wars upto and including the World War II The most potent weapon the seagoing ships of this century have been carrying is the 'torpedo', be it for antiship warfare or antisubmarine warfare, the latter being dominant since the World War II. -

US EPA, Pesticide Product Label, ARSENAL HERBICIDE APPLICATORS CONCENTRATE,09/07/2017
UNITED STATES ENVIRONMENTAL PROTECTION AGENCY WASHINGTON, DC 20460 OFFICE OF CHEMICAL SAFETY AND POLLUTION PREVENTION September 7, 2017 Nina S. Rao Regulatory Manager BASF Corporation 26 Davis Drive P. O. Box 13528 Research Triangle Park, NC 27709-3528 Subject: Notification per PRN 98-10 – Updating label language to specify NY State applicator requirements. Product Name: Arsenal Herbicide Applicators Concentrate EPA Registration Number: 241-299 Application Date: 08/10/2017 Decision Number: 532575 Dear Nina S. Rao: The Agency is in receipt of your Application for Pesticide Notification under Pesticide Registration Notice (PRN) 98-10 for the above referenced product. The Registration Division (RD) has conducted a review of this request for its applicability under PRN 98-10 and finds that the action requested falls within the scope of PRN 98-10. The label submitted with the application has been stamped “Notification” and will be placed in our records. Should you wish to add/retain a reference to the company’s website on your label, then please be aware that the website becomes labeling under the Federal Insecticide Fungicide and Rodenticide Act and is subject to review by the Agency. If the website is false or misleading, the product would be misbranded and unlawful to sell or distribute under FIFRA section 12(a)(1)(E). 40 CFR 156.10(a)(5) list examples of statements EPA may consider false or misleading. In addition, regardless of whether a website is referenced on your product’s label, claims made on the website may not substantially differ from those claims approved through the registration process. -

And Financial Implications of Unmanned
Disruptive Innovation and Naval Power: Strategic and Financial Implications of Unmanned Underwater Vehicles (UUVs) and Long-term Underwater Power Sources MASSACHUsf TTT IMef0hrE OF TECHNOLOGY by Richard Winston Larson MAY 0 8 201 S.B. Engineering LIBRARIES Massachusetts Institute of Technology, 2012 Submitted to the Department of Mechanical Engineering in partial fulfillment of the requirements for the degree of Master of Science in Mechanical Engineering at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY February 2014 © Massachusetts Institute of Technology 2014. All rights reserved. 2) Author Dep.atment of Mechanical Engineering nuaryL5.,3014 Certified by.... Y Douglas P. Hart Professor of Mechanical Engineering Tbesis Supervisor A ccepted by ....................... ........ David E. Hardt Ralph E. and Eloise F. Cross Professor of Mechanical Engineering 2 Disruptive Innovation and Naval Power: Strategic and Financial Implications of Unmanned Underwater Vehicles (UUVs) and Long-term Underwater Power Sources by Richard Winston Larson Submitted to the Department of Mechanical Engineering on January 15, 2014, in partial fulfillment of the requirements for the degree of Master of Science in Mechanical Engineering Abstract The naval warfare environment is rapidly changing. The U.S. Navy is adapting by continuing its blue-water dominance while simultaneously building brown-water ca- pabilities. Unmanned systems, such as unmanned airborne drones, are proving piv- otal in facing new battlefield challenges. Unmanned underwater vehicles (UUVs) are emerging as the Navy's seaborne equivalent of the Air Force's drones. Representing a low-end disruptive technology relative to traditional shipborne operations, UUVs are becoming capable of taking on increasingly complex roles, tipping the scales of battlefield entropy. They improve mission outcomes and operate for a fraction of the cost of traditional operations. -

APPENDIX a Navy Activity Descriptions
Atlantic Fleet Training and Testing Final EIS/OEIS September 2018 APPENDIX A Navy Activity Descriptions Appendix A Navy Activity Descriptions Atlantic Fleet Training and Testing Final EIS/OEIS September 2018 This page intentionally left blank. Appendix A Navy Activity Descriptions Atlantic Fleet Training and Testing Final EIS/OEIS September 2018 Final Environmental Impact Statement/Overseas Environmental Impact Statement Atlantic Fleet Training and Testing TABLE OF CONTENTS APPENDIX A NAVY ACTIVITY DESCRIPTIONS _____________________________________________A-1 A.1 Description of Sonar, Munitions, Targets, and Other Systems Employed in Atlantic Fleet Training and Testing Events .................................................................. A-1 A.1.1 Sonar Systems and Other Acoustic Sources ......................................................... A-1 A.1.2 Munitions .............................................................................................................. A-7 A.1.3 Targets ................................................................................................................ A-11 A.1.4 Defensive Countermeasures ............................................................................... A-12 A.1.5 Mine Warfare Systems ........................................................................................ A-13 A.1.6 Military Expended Materials ............................................................................... A-15 A.2 Training Activities .................................................................................................. -

A Retrospective on the So-Called Revolution in Military Affairs, 2000-2020
SECURITY, STRATEGY, AND ORDER A RETROSPECTIVE ON THE SO-CALLED REVOLUTION IN MILITARY AFFAIRS, 2000-2020 MICHAEL O’HANLON A RESTROSPECTIVE ON THE SO-CALLED REVOLUTION IN MILITARY AFFAIRS, 2000-2020 MICHAEL O’HANLON EXECUTIVE SUMMARY1 This paper revisits the debate that raged in American defense circles in the 1990s over whether a revolution in military affairs was imminent in the early parts of the 21st century. It also seeks to establish a benchmark, and reaffirm as well as refine a methodology, for forecasting future changes in military-related technologies by examining what has transpired in the first two decades of the 21st century. Taking this approach helps improve and validate the methodology that is employed in my forthcoming book, The Senkaku Paradox: Risking Great Power War Over Small Stakes (2019). A subsequent paper seeks to extrapolate a similar analysis out to 2040, gauging the potential for major breakthroughs in military technology and associated operational concepts over the next two decades. Such analysis is of critical importance for evaluating American and allied military and strategic options relevant to great-power war and deterrence in the years ahead. The paper’s category-by-category examination of military technology mirrors the approach that I employed in a book published in 2000, Technological Change and the Future of Warfare (though it really should have been entitled, The So-Called Revolution in Military Affairs, because I was largely challenging the then-popular notion that a military revolution of historic importance was afoot). Much of the research foundation of that book was the study of a list of 29 different types of technologies in an attempt to gauge which might undergo revolutionary change by 2020. -

Cyber Warfare
Downloaded by [University of Defence] at 23:51 30 May 2016 Cyber Warfare This book is a multidisciplinary analysis of cyber warfare, featuring contribu- tions by leading experts from a mixture of academic and professional backgrounds. Cyber warfare, meaning interstate cyber aggression, is an increasingly important emerging phenomenon in international relations, with state- orchestrated (or apparently state- orchestrated) computer network attacks occur- ring in Estonia (2007), Georgia (2008) and Iran (2010). This method of waging warfare – given its potential to, for example, make planes fall from the sky or cause nuclear power plants to melt down – has the capacity to be as devastating as any conventional means of conducting armed conflict. Every state in the world now has a cyber- defence programme and over 120 states also have a cyber- attack programme. While the amount of literature on cyber warfare is growing within disciplines, our understanding of the subject has been limited by a lack of cross- disciplinary engagement. In response, this book, drawn from the fields of computer science, military strategy, international law, political science and military ethics, provides a critical overview of cyber warfare for those approaching the topic from what- ever angle. Chapters consider the emergence of the phenomena of cyber warfare in international affairs; what cyber- attacks are from a technological standpoint; the extent to which cyber- attacks can be attributed to state actors; the strategic value and danger posed by cyber conflict; the legal regulation of cyber- attacks, both as international uses of force and as part of an ongoing armed conflict, and the ethical implications of cyber warfare.