Full Administrator's Guide
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

P6 Underscores Intel's Lead: 2/16/95
MICROPROCESSOR REPORT MICROPROCESSOR REPORT THE INSIDERS’ GUIDE TO MICROPROCESSOR HARDWARE VOLUME 9 NUMBER 2 FEBRUARY 16, 1995 P6 Underscores Intel’s Lead Sets New x86 Performance Standard, Thrusts into Server Market by Linley Gwennap Accelerating the Generational Pace While its competitors struggle to complete their The P6 is the first fruit of Intel’s effort to double its Pentium-class chips, Intel is well on the way to deliver- pace of processor generations. In the past, new x86 pro- ing its next-generation P6 processor. Looking under the cessor cores have rolled out every four years or so from hood (see page 9), we see that the microarchitecture of what was essentially a single design team at Intel’s main the P6 is not that different from the design of AMD’s K5 facility in Santa Clara (California). The P6 is the first or even NexGen’s 586. From the user’s perspective, x86 processor core from the company’s Hillsboro (Ore- though, the difference is clear: the first P6 should out- gon) team, which had previously focused on i960 chips. perform its competitors by about 50% on typical applica- The P6 project began in late 1991, several months before tions, based on initial performance estimates. the first tape out of the Pentium processor. Intel estimates that the P6 will deliver 200 SPEC- The decision to start a second x86 design center int92 at 133 MHz, the target frequency of the initial im- shows excellent foresight. Without the P6, Intel’s high plementation, although it has not yet announced any end throughout 1996 would have been limited to 150- specific P6 products. -

Advanced Micro Devices (AMD)
Strategic Report for Advanced Micro Devices, Inc. Tad Stebbins Andrew Dialynas Rosalie Simkins April 14, 2010 Advanced Micro Devices, Inc. Table of Contents Executive Summary ............................................................................................ 3 Company Overview .............................................................................................4 Company History..................................................................................................4 Business Model..................................................................................................... 7 Market Overview and Trends ...............................................................................8 Competitive Analysis ........................................................................................ 10 Internal Rivalry................................................................................................... 10 Barriers to Entry and Exit .................................................................................. 13 Supplier Power.................................................................................................... 14 Buyer Power........................................................................................................ 15 Substitutes and Complements............................................................................ 16 Financial Analysis ............................................................................................. 18 Overview ............................................................................................................ -

Computer Architectures an Overview
Computer Architectures An Overview PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sat, 25 Feb 2012 22:35:32 UTC Contents Articles Microarchitecture 1 x86 7 PowerPC 23 IBM POWER 33 MIPS architecture 39 SPARC 57 ARM architecture 65 DEC Alpha 80 AlphaStation 92 AlphaServer 95 Very long instruction word 103 Instruction-level parallelism 107 Explicitly parallel instruction computing 108 References Article Sources and Contributors 111 Image Sources, Licenses and Contributors 113 Article Licenses License 114 Microarchitecture 1 Microarchitecture In computer engineering, microarchitecture (sometimes abbreviated to µarch or uarch), also called computer organization, is the way a given instruction set architecture (ISA) is implemented on a processor. A given ISA may be implemented with different microarchitectures.[1] Implementations might vary due to different goals of a given design or due to shifts in technology.[2] Computer architecture is the combination of microarchitecture and instruction set design. Relation to instruction set architecture The ISA is roughly the same as the programming model of a processor as seen by an assembly language programmer or compiler writer. The ISA includes the execution model, processor registers, address and data formats among other things. The Intel Core microarchitecture microarchitecture includes the constituent parts of the processor and how these interconnect and interoperate to implement the ISA. The microarchitecture of a machine is usually represented as (more or less detailed) diagrams that describe the interconnections of the various microarchitectural elements of the machine, which may be everything from single gates and registers, to complete arithmetic logic units (ALU)s and even larger elements. -

Modern Processor Design: Fundamentals of Superscalar
Fundamentals of Superscalar Processors John Paul Shen Intel Corporation Mikko H. Lipasti University of Wisconsin WAVELAND PRESS, INC. Long Grove, Illinois To Our parents: Paul and Sue Shen Tarja and Simo Lipasti Our spouses: Amy C. Shen Erica Ann Lipasti Our children: Priscilla S. Shen, Rachael S. Shen, and Valentia C. Shen Emma Kristiina Lipasti and Elias Joel Lipasti For information about this book, contact: Waveland Press, Inc. 4180 IL Route 83, Suite 101 Long Grove, IL 60047-9580 (847) 634-0081 info @ waveland.com www.waveland.com Copyright © 2005 by John Paul Shen and Mikko H. Lipasti 2013 reissued by Waveland Press, Inc. 10-digit ISBN 1-4786-0783-1 13-digit ISBN 978-1-4786-0783-0 All rights reserved. No part of this book may be reproduced, stored in a retrieval system, or transmitted in any form or by any means without permission in writing from the publisher. Printed in the United States of America 7 6 5 4 3 2 1 Table of Contents PrefaceAbout the Authors x ix 1 Processor Design 1 1.1 The Evolution of Microprocessors 2 1.21.2.1 Instruction Digital Set Systems Processor Design Design 44 1.2.2 Architecture,Realization Implementation, and 5 1.2.3 Instruction Set Architecture 6 1.2.4 Dynamic-Static Interface 8 1.3 Principles of Processor Performance 10 1.3.1 Processor Performance Equation 10 1.3.2 Processor Performance Optimizations 11 1.3.3 Performance Evaluation Method 13 1.4 Instruction-Level Parallel Processing 16 1.4.1 From Scalar to Superscalar 16 1.4.2 Limits of Instruction-Level Parallelism 24 1.51.4.3 Machines Summary for Instruction-Level -

Low-Power X86 Solutions for Networked Storage and Media Servers
Low-Power x86 Solutions for Networked Storage and Media Servers OVERVIEW fEAtuRE-RIch cApAbIlItIEs Whether at the office or at home, everyone seems to be using, AMD Processors support Microsoft® and Linux® operating systems creating, and sharing content. Information such as financial that are tailored for these markets to be easy-to-use, protect data records, email, marketing collateral, home video, music and and serve applications. For SMB users, Windows® Small Business pictures must be organized, secure and accessible. And this Server 2011 Essentials is an ideal fit. Automatic backup and information must be protected from hardware failures using recovery protects business information. Organize information, techniques such as RAID and protected from software issues serve business applications such as accounting software and by using snapshots and backup to ensure nothing is lost. connect to online services such as email and CRM. This content requires new embedded solutions to manage, Windows® Home Server organizes, protects and streams digital manipulate and store data. This embedded network storage media content throughout the home. Centralize the iTunes® folder, appliance needs to be affordable, scalable, and easy to use videos, photos and financial spreadsheets. Automatically backup for managing information for business and home users. files to a server to protect from system disk failure or recover from a software or virus attack. AMD plAtfORM sOlutIOns To help meet the wide range of performance, power and price AMD’s pROcEssOR sOlutIOns provide thE fOllowing requirements for SoHo and home users, AMD offers a selection bEnEfIts fOR nEtworkED stORAgE AnD MEDIA sERVERs ™ of processor and chipset solutions. -

AMD's Early Processor Lines, up to the Hammer Family (Families K8
AMD’s early processor lines, up to the Hammer Family (Families K8 - K10.5h) Dezső Sima October 2018 (Ver. 1.1) Sima Dezső, 2018 AMD’s early processor lines, up to the Hammer Family (Families K8 - K10.5h) • 1. Introduction to AMD’s processor families • 2. AMD’s 32-bit x86 families • 3. Migration of 32-bit ISAs and microarchitectures to 64-bit • 4. Overview of AMD’s K8 – K10.5 (Hammer-based) families • 5. The K8 (Hammer) family • 6. The K10 Barcelona family • 7. The K10.5 Shanghai family • 8. The K10.5 Istambul family • 9. The K10.5-based Magny-Course/Lisbon family • 10. References 1. Introduction to AMD’s processor families 1. Introduction to AMD’s processor families (1) 1. Introduction to AMD’s processor families AMD’s early x86 processor history [1] AMD’s own processors Second sourced processors 1. Introduction to AMD’s processor families (2) Evolution of AMD’s early processors [2] 1. Introduction to AMD’s processor families (3) Historical remarks 1) Beyond x86 processors AMD also designed and marketed two embedded processor families; • the 2900 family of bipolar, 4-bit slice microprocessors (1975-?) used in a number of processors, such as particular DEC 11 family models, and • the 29000 family (29K family) of CMOS, 32-bit embedded microcontrollers (1987-95). In late 1995 AMD cancelled their 29K family development and transferred the related design team to the firm’s K5 effort, in order to focus on x86 processors [3]. 2) Initially, AMD designed the Am386/486 processors that were clones of Intel’s processors. -

Processor Check Utility for 64-Bit Compatibility
Processor Check Utility for 64-Bit Compatibility VMware Workstation Processor Check Utility for 64-Bit Compatibility VMware Workstation version 5.5 supports virtual machines with 64-bit guest operating systems, running on host machines with the following processors: • AMD™ Athlon™ 64, revision D or later • AMD Opteron™, revision E or later • AMD Turion™ 64, revision E or later • AMD Sempron™, 64-bit-capable revision D or later (experimental support) • Intel™ EM64T VT-capable processors (experimental support) When you power on a virtual machine with a 64-bit guest operating system, Workstation performs an internal check: if the host CPU is not a supported 64-bit processor, you cannot power on the virtual machine. VMware also provides this standalone processor check utility, which you can use without Workstation to perform the same check and determine whether your CPU is supported for virtual machines with 64-bit guest operating systems. Note: On hosts with EM64T VT-capable processors, you may not be able to power on a 64-bit guest, even though the processor check utility indicates that the processor is supported for 64- bit guests. VT functionality can be disabled via the BIOS, but the processor check utility cannot read the appropriate model-specific register (MSR) to detect that the VT functionality has been disabled in the BIOS. Note: In shopping for a processor that is compatible with Workstation 5.5 64-bit guests, you may be unable to determine the revision numbers of a given vendor's offering of AMD Athlon 64, Opteron, Turion 64, or Sempron processors. At this time, the only reliable way to determine whether any of these processors is a revision supported by Workstation 5.5, is by the manufacturing technology (CMOS): any of the AMD Athlon 64, Opteron, Turion 64, or Sempron processors whose manufacturing technology is 90nm SOI (.09 micron SOI) is compatible with Workstation 5.5 64-bit guests. -

A Dynamic Structural Analysis of the PC Microprocessor Industry
A Dynamic Structural Analysis of the PC Microprocessor Industry by Brett Russell Gordon Submitted in Partial Fulfillment of the Requirements for the Degree of Doctor of Philosophy in Economics Tepper School of Business Carnegie Mellon University May 2007 Dissertation Committee: Professor Ronald L. Goettler (co-chair) Professor Kannan Srinivasan (co-chair) Professor Dennis Epple Professor Holger Sieg Professor Vishal Singh Abstract In durable goods markets, sellers face a dynamic trade-off: more units sold today come at the expense of selling more units tomorrow. Buyers face a similar dynamic trade-off: should they purchase a new product today or retain their existing product and purchase a poten- tially better product tomorrow? These issues lay at the heart of durable goods markets - especially those involving high-tech products - yet relatively little research addresses them from an empirical perspective. To that end, this dissertation provides a dynamic structural analysis of demand and competition within the context of the PC microprocessor industry. This industry is particularly interesting because it is a duopoly that has experienced intense technological and price competition. First, I estimate a model of dynamic demand that allows for both product adoption and replacement decisions when consumers are uncertain about future product price and qual- ity. In the absence of panel data, I show how to infer replacement from a combination of aggregate data. The results show that heterogeneity in replacement behavior provides an opportunity for firms to tailor their product introduction and pricing strategies by targeting specific consumer replacement segments. Second, I extend this analysis to construct an equilibrium model of dynamic oligopoly with durable goods and endogenous innovation. -
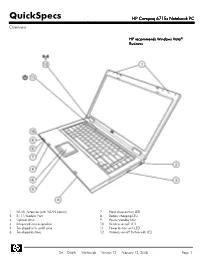
HP Compaq 6715S Notebook PC Overview
QuickSpecs HP Compaq 6715s Notebook PC Overview HP recommends Windows Vista® Business 1. WLAN Antennas (with WLAN option) 7. Hard drive activity LED 2. RJ-11/modem Port 8. Battery charging LED 3. Optical drive 9. Power/standby LED 4. Integrated stereo speakers 10. Wireless on/off LED 5. Touchpad with scroll zone 11. Power button with LED 6. Touchpad buttons 12. Wireless on/off Button with LED DA - 12688 Worldwide — Version 12 — February 12, 2008 Page 1 QuickSpecs HP Compaq 6715s Notebook PC Overview 1. Power connector 6. PC Card eject button 2. 2 USB 2.0 ports 7. VGA/external monitor connector 3. Stereo headphone/line out 8. RJ-45/Ethernet Port 4. Stereo microphone in 9. Kensington Lock slot 5. Type I/II PC Card slot At A Glance Genuine Windows Vista Business*, Genuine Windows Vista Home Basic, or FreeDOS Widescreen 15.4-inch diagonal display with wide-viewing angle, BrightView and HP Privacy Filter support Wireless connectivity options: Integrated 802.11a/b/g or 802.11b/g wireless LAN module Bluetooth® AMD Turion™ 64 X2 Dual-Core Mobile Technology, AMD Athlon™ 64 X2 Dual-Core Processors for Notebook PCs, or Mobile AMD Sempron™ processors Thin, lightweight design starting at 5.7 lb/2.59 kg and 1.37 in/34.9 mm thin at front Security features including HP ProtectTools Security Manager and Device Access Manager for HP ProtectTools Integrated optical drive, including optional DVD+/-RW SuperMulti DL LightScribe Drive HP 90W Smart AC Adapter Up to 250-GB 5400 rpm user-removable hard drive with HP DriveGuard protection Up to 4 GB of 667-MHz DDR2 SDRAM, dual channel memory support ATI Radeon X1250 graphics, with up to 831 MB shared system memory (select models) Broadcom NetLink Fast Ethernet Controller Touchpad with scroll zone * At initial boot, either 32- or 64-bit can be selected. -

The X86 Is Dead. Long Live the X86!
the x86 is dead. long live the x86! CC3.0 share-alike attribution copyright c 2013 nick black with diagrams by david kanter of http://realworldtech.com “Upon first looking into Intel’s x86” that upon which we gaze is mankind’s triumph, and we are its stewards. use it well. georgia tech ◦ summer 2013 ◦ cs4803uws ◦ nick black The x86 is dead. Long live the x86! Why study the x86? Used in a majority of servers, workstations, and laptops Receives the most focus in the kernel/toolchain Very complex processor, thus large optimization space Excellent documentation and literature Fascinating, revealing, lengthy history Do not think that x86 is all that’s gone on over the past 30 years1. That said, those who’ve chased peak on x86 can chase it anywhere. 1Commonly expressed as “All the world’s an x86.” georgia tech ◦ summer 2013 ◦ cs4803uws ◦ nick black The x86 is dead. Long live the x86! In the grim future of computing there are 10,000 ISAs Alpha + BWX/FIX/CIX/MVI SPARC V9 + VIS3a AVR32 + JVM JVMb CMS PTX/SASSc PA-RISC + MAX-2 TILE-Gxd SuperH ARM + NEONe i960 Blackfin IA64 (Itanium) PowerISA + AltiVec/VSXf MIPS + MDMX/MIPS-3D MMIX IBMHLA (s390 + z) a Most recently the “Oracle SPARC Architecture 2011”. b m68k Most recently the Java SE 7 spec, 2013-02-28. c Most recently the PTX ISA 3.1 spec, 2012-09-13. VAX + VAXVA d TILE-Gx ISA 1.2, 2013-02-26. e z80 / MOS6502 ARMv8: A64, A32, and T32, 2011-10-27. f MIX PowerISA v.2.06B, 2010-11-03. -

Take a Way: Exploring the Security Implications of AMD's Cache Way
Take A Way: Exploring the Security Implications of AMD’s Cache Way Predictors Moritz Lipp Vedad Hadžić Michael Schwarz Graz University of Technology Graz University of Technology Graz University of Technology Arthur Perais Clémentine Maurice Daniel Gruss Unaffiliated Univ Rennes, CNRS, IRISA Graz University of Technology ABSTRACT 1 INTRODUCTION To optimize the energy consumption and performance of their With caches, out-of-order execution, speculative execution, or si- CPUs, AMD introduced a way predictor for the L1-data (L1D) cache multaneous multithreading (SMT), modern processors are equipped to predict in which cache way a certain address is located. Conse- with numerous features optimizing the system’s throughput and quently, only this way is accessed, significantly reducing the power power consumption. Despite their performance benefits, these op- consumption of the processor. timizations are often not designed with a central focus on security In this paper, we are the first to exploit the cache way predic- properties. Hence, microarchitectural attacks have exploited these tor. We reverse-engineered AMD’s L1D cache way predictor in optimizations to undermine the system’s security. microarchitectures from 2011 to 2019, resulting in two new attack Cache attacks on cryptographic algorithms were the first mi- techniques. With Collide+Probe, an attacker can monitor a vic- croarchitectural attacks [12, 42, 59]. Osvik et al. [58] showed that tim’s memory accesses without knowledge of physical addresses an attacker can observe the cache state at the granularity of a cache or shared memory when time-sharing a logical core. With Load+ set using Prime+Probe. Yarom et al. [82] proposed Flush+Reload, Reload, we exploit the way predictor to obtain highly-accurate a technique that can observe victim activity at a cache-line granu- memory-access traces of victims on the same physical core. -

Test Report for Single Event Effects of the 80386DX M=Croprocessor
JPL Publication 93-12 Test Report for Single Event Effects of the 80386DX M=croprocessor R. Kevin Watson Harvey R. Schwartz Donald K. Nichols February 15, 1993 tU/ A National Aeronautics and Space Administration Jet Propulsion Laboratory California Institute of Technology Pasadena, California The research described in this publication was carried out by the Jet Propulsion Laboratory, California Institute of Technology, under a contract with the National Aeronautics and Space Administration. Funding from this support came from Code QR, Reliability, Maintainability, and Quality Assurance, for the Microelectronics Space Radiation Effects Program. Reference herein to any specific commercial product, process, or service by trade name, trademark, manufacturer, or otherwise, does not constitute or imply its endorsement by the United States Government or the Jet Propulsion Laboratory, California Institute of Technology. Table of Contents Introduction......................................................................................................1 80386DX Overview and Background ..............................................................2 Modes ofOperation..........................................................................................3 Test Philosophy................................................................................................4 "AOK Circuit"forRegisterTests.....................................................................5 DUT Card and Test System Overview............................................................5