Extracting Windows Command Line Details from Physical Memory
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Doskey Singleton MVP Her Independent, Colleges and Knew She Was in Senior Universities of Wisconsin Operate Trouble When She Year
WTG Achievers Vol. 11, No. 4 November 2010 About the WTG Basketball star finds her stride again with WTG The twenty private, or Doskey Singleton MVP her independent, colleges and knew she was in senior universities of Wisconsin operate trouble when she year. And without taxpayer support, but fl unked an informa- thanks to a provide an invaluable public tion technology class suggestion service to the state, educating in her fi rst semester from her more than 60,000 students a at Silver Lake Col- basketball year. Many of Wisconsin’s best lege. coach, Dos- and brightest need financial help key visited to attend the college of their Doskey is the fi rst to Silver Lake. choice. admit that she didn't start out as the best Doskey The State of Wisconsin created student. Attend- joined the Wisconsin Tuition Grant ing three different DoskeyDoskey Singleton,Singleton, Milwaukee,Milwaukee, faced her share of chal-chal- the SLC (WTG) in 1965 to help qualified Milwaukee high lenges as a freshman, but says she’s stronger now. basketball Wisconsin citizens to succeed. schools, she fi nally team last fall, Fully one-third of the low-income found the right fi t at a school I would have never made but the transition to college students who apply for the WTG that helped her integrate her it to college,” Doskey says. wasn’t easy as she struggled are turned away every year studies and life goals. “If At Destiny, Doskey was the academically. “When I was for lack of funds. Each month it wasn’t for Destiny High, school’s leading scorer and continued on page 2 WTG Achievers brings you success stories of Wisconsinites for whom the WTG has made a WTG helps senior “pay it forward” as graduation looms significant difference. -
![[D:]Path[...] Data Files](https://docslib.b-cdn.net/cover/6104/d-path-data-files-996104.webp)
[D:]Path[...] Data Files
Command Syntax Comments APPEND APPEND ; Displays or sets the search path for APPEND [d:]path[;][d:]path[...] data files. DOS will search the specified APPEND [/X:on|off][/path:on|off] [/E] path(s) if the file is not found in the current path. ASSIGN ASSIGN x=y [...] /sta Redirects disk drive requests to a different drive. ATTRIB ATTRIB [d:][path]filename [/S] Sets or displays the read-only, archive, ATTRIB [+R|-R] [+A|-A] [+S|-S] [+H|-H] [d:][path]filename [/S] system, and hidden attributes of a file or directory. BACKUP BACKUP d:[path][filename] d:[/S][/M][/A][/F:(size)] [/P][/D:date] [/T:time] Makes a backup copy of one or more [/L:[path]filename] files. (In DOS Version 6, this program is stored on the DOS supplemental disk.) BREAK BREAK =on|off Used from the DOS prompt or in a batch file or in the CONFIG.SYS file to set (or display) whether or not DOS should check for a Ctrl + Break key combination. BUFFERS BUFFERS=(number),(read-ahead number) Used in the CONFIG.SYS file to set the number of disk buffers (number) that will be available for use during data input. Also used to set a value for the number of sectors to be read in advance (read-ahead) during data input operations. CALL CALL [d:][path]batchfilename [options] Calls another batch file and then returns to current batch file to continue. CHCP CHCP (codepage) Displays the current code page or changes the code page that DOS will use. CHDIR CHDIR (CD) [d:]path Displays working (current) directory CHDIR (CD)[..] and/or changes to a different directory. -

External Commands
5/22/2018 External commands External commands Previous | Content | Next External commands are known as Disk residence commands. Because they can be store with DOS directory or any disk which is used for getting these commands. Theses commands help to perform some specific task. These are stored in a secondary storage device. Some important external commands are given below- MORE MOVE FIND DOSKEY MEM FC DISKCOPY FORMAT SYS CHKDSK ATTRIB XCOPY SORT LABEL 1. MORE:-Using TYPE command we can see the content of any file. But if length of file is greater than 25 lines then remaining lines will scroll up. To overcome through this problem we uses MORE command. Using this command we can pause the display after each 25 lines. Syntax:- C:\> TYPE <File name> | MORE C:\> TYPE ROSE.TXT | MORE or C: \> DIR | MORE 2. MEM:-This command displays free and used amount of memory in the computer. Syntax:- C:\> MEM the computer will display the amount of memory. 3. SYS:- This command is used for copy system files to any disk. The disk having system files are known as Bootable Disk, which are used for booting the computer. Syntax:- C:\> SYS [Drive name] C:\> SYS A: System files transferred This command will transfer the three main system files COMMAND.COM, IO.SYS, MSDOS.SYS to the floppy disk. 4. XCOPY:- When we need to copy a directory instant of a file from one location to another the we uses xcopy command. This command is much faster than copy command. Syntax:- C:\> XCOPY < Source dirname > <Target dirname> C:\> XCOPY TC TURBOC 5. -

Ch 7 Using ATTRIB, SUBST, XCOPY, DOSKEY, and the Text Editor
Using ATTRIB, SUBST, XCOPY, DOSKEY, and the Text Editor Ch 7 1 Overview The purpose and function of file attributes will be explained. Ch 7 2 Overview Utility commands and programs will be used to manipulate files and subdirectories to make tasks at the command line easier to do. Ch 7 3 Overview This chapter will focus on the following commands and programs: ATTRIB XCOPY DOSKEY EDIT Ch 7 4 File Attributes and the ATTRIB Command Root directory keeps track of information about every file on a disk. Ch 7 5 File Attributes and the ATTRIB Command Each file in the directory has attributes. Ch 7 6 File Attributes and the ATTRIB Command Attributes represented by single letter: S - System attribute H - Hidden attribute R - Read-only attribute A - Archive attribute Ch 7 7 File Attributes and the ATTRIB Command NTFS file system: Has other attributes At command line only attributes can change with ATTRIB command are S, H, R, and A Ch 7 8 File Attributes and the ATTRIB Command ATTRIB command: Used to manipulate file attributes Ch 7 9 File Attributes and the ATTRIB Command ATTRIB command syntax: ATTRIB [+R | -R] [+A | -A] [+S | -S] [+H | -H] [[drive:] [path] filename] [/S [/D]] Ch 7 10 File Attributes and the ATTRIB Command Attributes most useful to set and unset: R - Read-only H - Hidden Ch 7 11 File Attributes and the ATTRIB Command The A attribute (archive bit) signals file has not been backed up. Ch 7 12 File Attributes and the ATTRIB Command XCOPY command can read the archive bit. -

MS-DOS Secret And/Or Unknown Commands
MS-DOS secret and/or unknown commands Below is a listing of MS-DOS commands that are not listed in any available help manual or in the commands syntax or are commonly unknown commands. Many of these commands that are known can be very useful when using MS-DOS, while some of the other commands are unknown and/or appear to do nothing. Please use these commands cautiously, some of the commands can erase data and/or erase data without warning. ATTRIB , The command is short for ATTRIB -a -h -r - s *.* (removes all attributes of a file). BACKUP /HP Unknown DIR , This lists all files including hidden files, does not work in Windows 95 / 98 / NT / 2000. DIR ... Lists all directories that do not have extensions. In Windows 95 / Windows 98 will list the contents of the directories previous to the directory currently in. DOSKEY /APPEDIT Utilize doskey functions in MS-DOS command utilities such as edlin and debug. DOSKEY Unknown /COMMAND DOSKEY Unknown /PERMANENT DOSKEY /SCRSIZE Unknown DOSKEY Unknown /XHISTORY FDISK /MBR Recreates the Master Boot Record See CH000175 for additional information. FDISK /PRI See FDISK Page for additional information. FDISK /EXT See FDISK Page for additional information. FDISK /LOG See FDISK Page for additional information. FDISK /Q Prevents fdisk from booting the system automatically after exiting fdisk. FDISK /STATUS Shows you the current status of your hard drives. FORMAT Formats the hard drive without any prompting. /AUTOTEST FORMAT /BACKUP Like /AUTOTEST but it will ask you for a volume label. FORMAT /Z:n Command used with FDISK supporting FAT32, used to specify the cluster size in bytes where n is multiplied by 512. -

Pengantar Basis Data
Prak. Pengantar Teknologi Informasi Sistem Operasi (Disk Operating System) / DOS Ade Putra, M.Kom. UNIVERSITAS BINA DARMA 2013 Perintah Eksternal Command Perintah yang memiliki file tersendiri dan tidak lagi ditampung pada file command.com merupakan perintah yang dapat dijalankan apabila file system untuk operasionalnya terdapat pada disk (hardisk atau disket). Sebelum kita mengetikkan perintah eksternal ini pada prompt perintah, terlebih dahulu kita harus memeriksa apakah file yang dibutuhkan telah ada. Untuk melihat apakah file pendukungnya dapat dipergunakan perintah dir. 1. FORMAT [format.com] Perintah format digunakan untuk memformat agar disket dapat dipergunakan dalam operasi penyimpanan dan pengolahan data. Sintaks : DRIVE:\>FORMAT_DRIVE:[/spesifikasi][/..] Contoh : A:\>format C:\>format a:/s Perintah Eksternal Command 2. ATTRIB [attrib.exe] Perintah ini digunakan untuk menambahkan atau menghapus atribut suatu file atau beberapa file sekaligus. Sintaks : DRIVE:\>ATTRIB_[+|-]_[spesifikasi]_[nama file] Contoh : A:\>attrib +r *.doc A:\>attrib +a –r *.doc Setiap file yang dibuat selalu memiliki atribut yang menunjukkan sifat file tersebut. Atribut file ada 5 macam: • A : Archive. File dengan atribut ini merupakan file arsip dan perlu di-backup. • H : Hidden. File dengan atribut ini merupakan file hidden,yang tidak terlihat ketika dilisting dengan perintah biasa. • R : Read-only. File dengan atribut ini merupakan file yang hanya bisa dibaca saja. • S : System. File dengan atribut ini merupakan file sistem. • Attribute (+ = ON, - = OFF) Perintah Eksternal Command Contoh perintah: Attrib +h +r name file (on hidden & Read Only) Attrib -h -r -s system.dat (off hidden, read only & system) Pengetahuan mengenai attrib ini amat penting apabila kita ingin membuat salinan file system.dat dan user.dat atau lebih dikenali sebagai registry file Perintah Eksternal Command Latihan Perintah Attrib : 1. -

Basic Ms-Dos
8/23/2017 History ■ MS-DOS 1.0 was released in August 1981, and was updated until April 1994 when it BASIC MS-DOS was replaced by Windows 95 ■ All versions of windows still contain some type of DOS, in windows 95 and 98 you can go to run and type command to get to DOS prompt, in NT, 2000, and XP you can type ~ Dharma Raj Poudel CMD and get DOS. Introduction File Manipulation The role of DOS is to interpret commands that the user enters via the keyboard. DIR - Lists files and subdirectories • Wildcard Characters ? * EDIT - creates a new file or modifies an existing file These commands allow the following tasks to be COPY - copies a file or a group of files executed: XCOPY - copies all files in a directory (and its subdirectories) file and folder management DEL or ERASE - deletes a file or a group of files UNDELETE - undeletes files disk upgrades COPY (or XCOPY) plus DEL - moves files hardware configuration DOSKEY - recalls commands memory optimization RENAME or REN - renames files TYPE - displays text files program execution PRINT - prints a text file COPY - used to create a file ATTRIB - sets file properties FC - compares two files 1 8/23/2017 Directory Manipulation Basic Structure MD or MKDIR - creates a directory ■ Most DOS commands use the same CD or CHDIR - changes directory structure PROMPT - changes the command prompt ■ Command Source Destination /Switch TREE - displays the directory structure ■ The switch will give options to the command RD or RMDIR - removes a directory ■ Example COPY A:\file.txt c:\ /v ■ /v will verify if the file copied correctly REN - Renaming directories PATH - creates a search path The Help Switch /? MS-DOS Prompt ■ You can use the help switch with any command. -

Extracting Windows Command Line Details from Physical Memory
Extracting Windows Command Line Details from Physical Memory. Richard Stevens and Eoghan Casey Introduction • Recent research has demonstrated how effective memory forensics can be in identifying information of forensic value. • One area of interest is the commands that have been typed by a user or attacker into the command prompt. • The presence of a command string in memory might indicate a command that was typed by the user. Or it could be a fragment of a help file. • Context is important - even if commands can be identified using simple string searches the order can change the meaning • Is it possible to recover the history of a command prompt from a Windows XP memory capture by examining the data structures used to store the command history? Windows Command Line History • DOSKEY – Originally a separate application for MS-DOS that has been incorporated into Windows XP as a command. – Accessed by entering “doskey / history” or pressing “F7” – stores the last 50 commands entered by the user by default – The buffer’s size is stored in: HKEY_CURRENT_USER\Console\HistoryBufferSize – Most familiar to DOS and Windows users using the “up” and “down” arrows to scroll through previous commands. – Memory resident and only normally accessible from within a running cmd.exe process. – Can be cleared using “doskey /reinstall” or pressing “ALT-F7” DOSKEY Initial Research • A literary review was conducted to identify any indications of how DOSKEY structures might be stored. No significant resources were found. • A Windows XP VM was created and memory captures were taken using 256mb, 512mb, and 1024mb of RAM. – Each capture contained one or more command prompt windows containing known commands including readily identifiable strings. -

&Kdswhu ' 8Vlqj 0Lfurvriw 06
&KDSWHU' 8VLQJ 0LFURVRIW06'26 &KDSWHU'8VLQJ0LFURVRIW06'26 '8VLQJ0LFURVRIW06'26 After having explained the installation of the ICP Controller and the host-drives in chapters B and C, we now explain how to install the operating system MS-DOS. By using some ex- amples, we shall demonstrate how to partition a host-drive, transfer MS-DOS to the host- drive, install Windows 3.x and use a CD-ROM drive (standing for any other Not Direct Access Device) under MS-DOS. In addition, we will give you further information on how to install Windows 95. '7UDQVSDUHQF\RI+RVW'ULYHV The structure of the Host Drives, which have been installed with GDTSETUP (in chapter C), is not known to DOS. i.e., the operating system does not recognize that a given Host Drive consists of a number of hard disks forming a disk array. To DOS this Host Drive simply ap- pears as one single SCSI hard disk with the capacity of the disk array. This complete trans- parency represents the easiest way to operate disk arrays under DOS; neither DOS nor the PCI computer need to be involved in the administration of these complex disk array con- figurations. '3DUWLWLRQLQJD+RVW'ULYHDQG7UDQVIHUULQJ06'26 You can partition the host-drives installed in chapter C with GDTSETUP as well as with the MS-DOS program FDISK. However, in our explanation we shall only use GDTSETUP. For fur- ther information on FDISK, please refer to your MS-DOS manual. During the following in- stallation instructions we assume that there is not yet a boot disk in the computer system. -
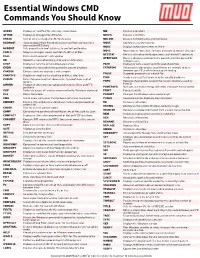
Essentials-Windows-CMD-Command-You-Should-Know-2.Pdf
https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/15- cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user- know/Essential https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ Windows CMD https://www.makeuseof.com/ tag/15-cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd-commands-every- windows-user-know/Commands https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ You Should Know https:// www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ https://www.makeuseof.com/tag/15-cmd- commands-every-windows-user-know/ASSOC Displays or modifies file extension associations https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-MD Creates a directory know/ATTRIB https://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/Displays or changes file attributes MKDIR Creates a directory https://www.makeuseof.com/ tag/15-cmd-commands-every-windows-user-know/BREAK Sets or clears extended CTRL+C checking https://www.makeuseof.com/tag/15-cmd-commands-every-MKLINK Creates Symbolic Links and Hard Links windows-user-know/BCDBOOT Used to copy criticalhttps://www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/ files to the system partition and to crate a MODE Configures a system device https:// new system BCD store www.makeuseof.com/tag/15-cmd-commands-every-windows-user-know/MORE Displays https://www.makeuseof.com/tag/15-cmd- output one screen at a time BCDEDIT Sets -

The Windows Command Line, Batch Files, and Scripting- Using the Command Shell
The Command Line in Windows Vic Laurie All rights reserved, Copyright 2005-2010 The Windows Command Line, Batch Files, and Scripting- Using the Command Shell The Windows Command Line, Batch Files, and Scripting Site navigation The Windows command line is a mainstay for systems administrators and power users but is relatively unknown to many PC users. The purpose of this site is to make the power and utility of the command line more familiar to a wider community of computer users. Also under-appreciated are the related resources of batch files and scripts and powered by FreeFind these will be discussed as well. Pages Windows is famous as a graphical user interface and many computer users tend to forget (or never knew) that there are also very useful command line functions in Windows. In fact, there is a great deal more to Windows than just point and click. The Home keyboard and the command line can be substantial adjuncts to the mouse and icons. There are two basic features involving a Assoc and Ftype command line. One is the entry 'Run" (or "Start Search" in Vista) that is in the Start menu and the other is the command prompt Batch files- basics window. Batch files - branching Introduction to the Command Line Batch files- iterating Command Line- Those who are new to the command line or need a refresher can read basic material on these pages: Introduction Command Line- Introduction Command line list and Command line list and reference reference Commands that everybody can use Commands that everybody Configuring the command prompt window can use Start-Run line Configuring the command prompt window Specific Applications of the Command Shell Doskey Some details and examples for various commands are considered in a series of pages listed below. -

An AZ Index of the Windows XP Command Line
An A-Z Index of the Windows XP command line ADDUSERS Add or list users to/from a CSV file ARP Address Resolution Protocol ~ ASSOC Change file extension associations ASSOCIAT One step file association AT Schedule a command to run at a later time ATTRIB Change file attributes b BOOTCFG Edit Windows boot settings BROWSTAT Get domain, browser and PDC info c CACLS Change file permissions ~ CALL Call one batch program from another ~ CD Change Directory - move to a specific Folder CHANGE Change Terminal Server Session properties CHKDSK Check Disk - check and repair disk problems CHKNTFS Check the NTFS file system CHOICE Accept keyboard input to a batch file CIPHER Encrypt or Decrypt files/folders CleanMgr Automated cleanup of Temp files, recycle bin CLEARMEM Clear memory leaks CLIP Copy STDIN to the Windows clipboard. ~ CLS Clear the screen CLUSTER Windows Clustering CMD Start a new CMD shell ~ COLOR Change colors of the CMD window COMP Compare the contents of two files or sets of files COMPACT Compress files or folders on an NTFS partition COMPRESS Compress individual files on an NTFS partition CON2PRT Connect or disconnect a Printer CONVERT Convert a FAT drive to NTFS. ~ COPY Copy one or more files to another location CSCcmd Client-side caching (Offline Files) CSVDE Import or Export Active Directory data d ~ DATE Display or set the date Dcomcnfg DCOM Configuration Utility DEFRAG Defragment hard drive ~ DEL Delete one or more files DELPROF Delete NT user profiles DELTREE Delete a folder and all subfolders DevCon Device Manager Command Line Utility