Protecting Children on the Internet Hearing Committee
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Unusual Sexual Behavior
UNUSUAL SEXUAL BEHA VIOR UNUSUAL SEXUAL BEHAVIOR THE STANDARD DEVIATIONS By DAVID LESTER, Ph.D. R ichard Stockton State College Pomona, New Jersey CHARLES C THOMAS • PUBLISHER Springfield • Illinois • U.S.A. Published and Distributed Throughout the World by CHARLES C THOMAS. PUBLISHER Bannerstone House 301-327 East Lawrence Avenue, Springfield, I1!inois, U.S.A. This book is protected by copyright. No part of it may be reproduced in any manner without written permission from the publisher. ©1975, by CHARLES C THOMAS. PUBLISHER ISBN 0-398-03343-9 Library of Congress Catalog Card Number: 74 20784 With THOMAS BOOKS careful attention is given to all details of manufacturing and design. It is the Publisher's desire to present books that are satisfactory as to their physical qualities and artistic possibilities and appropriate for their particular use. THOMAS BOOKS will be true to those laws of quality that assure a good name and good will. Library of Congress Cataloging in Publication Data Lester, David, 1942- Unusual sexual behavior. Includes index. 1. Sexual deviation. I. Title. [DNLM: 1. Sex deviation. WM610 L642ul RC577.IA5 616.8'583 74-20784 ISBN 0-398-03343-9 Printed in the United States of America A-2 INTRODUCTION The purpose of this book is to review the literature on sexual deviations. Primarily the review is concerned with the research literature and not with clinical studies. However, occasional refer ence is made to the conclusions of clinical studies and, in particular, to psychoanalytic hypotheses about sexual deviations. The coverage of clinical and psychoanalytic ideas is by no means intended to be exhaustive, unlike the coverage of the research literature. -

Criminalizing "Virtual" Child Pornography Under the Child Pornography Prevention Act: Is It Really What It "Appears to Be?" Wade T
University of Richmond Law Review Volume 35 | Issue 2 Article 6 2001 Criminalizing "Virtual" Child Pornography Under the Child Pornography Prevention Act: Is it Really What it "Appears to Be?" Wade T. Anderson University of Richmond Follow this and additional works at: http://scholarship.richmond.edu/lawreview Part of the Other Law Commons Recommended Citation Wade T. Anderson, Criminalizing "Virtual" Child Pornography Under the Child Pornography Prevention Act: Is it Really What it "Appears to Be?", 35 U. Rich. L. Rev. 393 (2001). Available at: http://scholarship.richmond.edu/lawreview/vol35/iss2/6 This Comment is brought to you for free and open access by the Law School Journals at UR Scholarship Repository. It has been accepted for inclusion in University of Richmond Law Review by an authorized editor of UR Scholarship Repository. For more information, please contact [email protected]. COMMENTS CRIMINALIZING "VIRTUAL" CHILD PORNOGRAPHY UNDER THE CHILD PORNOGRAPHY PREVENTION ACT: IS IT REALLY WHAT IT "APPEARS TO BE?" David is 11 years old. He weighs 60 pounds. He is 4 feet, 6 inches tall. He has brown hair. His love is real. But he is not. -Advertisement for Steven Spielberg's June 2001 film, Artificial Intelligence.' Years after his death, John Wayne sells beer in television commercials. 2 Eons after their extinction, lifelike dinosaurs con- tinue to terrorize actors and thrill moviegoers.3 The highest- grossing film of all time4 employs "virtual" passengers aboard the 1. AL. Artificial Intelligence, at http:/aimovie.warnerbros.com (last visited Apr. 3, 2001). 2. Robert Lemos, Virtual Actors: Cheaper, Better, Faster Than Humans?, ZDNET NEWS, June 15, available at 1998, 1998 WL 28812578 ("John Wayne and Fred Astaire, or at least the computer-enhanced images of the deceased stars, are starring in commer- cials."). -
![[ Captioner Standing by ] 1 >> the Broadcast Is Now Starting. All Attendees Are in Listen-Only Mode. >> JESSIE](https://docslib.b-cdn.net/cover/4385/captioner-standing-by-1-the-broadcast-is-now-starting-all-attendees-are-in-listen-only-mode-jessie-194385.webp)
[ Captioner Standing by ] 1 >> the Broadcast Is Now Starting. All Attendees Are in Listen-Only Mode. >> JESSIE
[ Captioner standing by ] 1 >> The broadcast is now starting. All attendees are in listen-only mode. >> JESSIE: Hello, everyone. Welcome to today's Webinar Understanding Chemsex Essentials for Testing the Addictive Fusion of Drug and Sex. It's so great that you could be with us here. I'm Jessica O'Brien. I will be the facilitator. Make sure to bookmark this page so you can stay up to date on all of the latest in addiction education. Closed captioning is provided by CaptionAccess. You will notice the Go-To Webinar. You can use the orange arrow at any point to minimize or maximize the menu and you can just move it out of the way if that's what is best for you. I will bring your attention to the questions box. We're going to gather any questions for our presenter today in the questions box and then ask him during the Q&A session at the -- towards the end of the presentation. So if you have any questions for Dr. Fawcett, feel free to right those in the Q&A box. Also, we have -- bringing your attention to the handouts tab. You can find a copy of the slides for today's presentation as well as a user-friendly instructional guide on how to access our online CE quiz and immediately earn your certificate. If you have never gotten a certificate from us before, make sure you use the instructions in our handout tab when you are ready to take the quiz. Every NAADAC Webinar has its own web page that houses everything that you need to know about that 2 particular Webinar. -
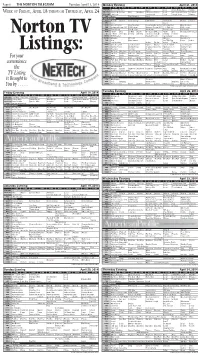
06 4-15-14 TV Guide.Indd
Page 6 THE NORTON TELEGRAM Tuesday, April 15, 2014 Monday Evening April 21, 2014 7:00 7:30 8:00 8:30 9:00 9:30 10:00 10:30 11:00 11:30 KHGI/ABC Dancing With Stars Castle Local Jimmy Kimmel Live Nightline WEEK OF FRIDAY, APRIL 18 THROUGH THURSDAY, APRIL 24 KBSH/CBS 2 Broke G Friends Mike Big Bang NCIS: Los Angeles Local Late Show Letterman Ferguson KSNK/NBC The Voice The Blacklist Local Tonight Show Meyers FOX Bones The Following Local Cable Channels A&E Duck D. Duck D. Duck Dynasty Bates Motel Bates Motel Duck D. Duck D. AMC Jaws Jaws 2 ANIM River Monsters River Monsters Rocky Bounty Hunters River Monsters River Monsters CNN Anderson Cooper 360 CNN Tonight Anderson Cooper 360 E. B. OutFront CNN Tonight DISC Fast N' Loud Fast N' Loud Car Hoards Fast N' Loud Car Hoards DISN I Didn't Dog Liv-Mad. Austin Good Luck Win, Lose Austin Dog Good Luck Good Luck E! E! News The Fabul Chrisley Chrisley Secret Societies Of Chelsea E! News Norton TV ESPN MLB Baseball Baseball Tonight SportsCenter Olbermann ESPN2 NFL Live 30 for 30 NFL Live SportsCenter FAM Hop Who Framed The 700 Club Prince Prince FX Step Brothers Archer Archer Archer Tomcats HGTV Love It or List It Love It or List It Hunters Hunters Love It or List It Love It or List It HIST Swamp People Swamp People Down East Dickering America's Book Swamp People LIFE Hoarders Hoarders Hoarders Hoarders Hoarders Listings: MTV Girl Code Girl Code 16 and Pregnant 16 and Pregnant House of Food 16 and Pregnant NICK Full H'se Full H'se Full H'se Full H'se Full H'se Full H'se Friends Friends Friends SCI Metal Metal Warehouse 13 Warehouse 13 Warehouse 13 Metal Metal For your SPIKE Cops Cops Cops Cops Cops Cops Cops Cops Jail Jail TBS Fam. -

Turns to Affect in Feminist Film Theory 97 Anu Koivunen Sound and Feminist Modernity in Black Women’S Film Narratives 111 Geetha Ramanathan
European Film Studies Mutations and Appropriations in THE KEY DEBATES FEMINISMS Laura Mulvey and 5 Anna Backman Rogers (eds.) Amsterdam University Press Feminisms The Key Debates Mutations and Appropriations in European Film Studies Series Editors Ian Christie, Dominique Chateau, Annie van den Oever Feminisms Diversity, Difference, and Multiplicity in Contemporary Film Cultures Edited by Laura Mulvey and Anna Backman Rogers Amsterdam University Press The publication of this book is made possible by grants from the Netherlands Organisation for Scientific Research (NWO). Cover design: Neon, design and communications | Sabine Mannel Lay-out: japes, Amsterdam Amsterdam University Press English-language titles are distributed in the US and Canada by the University of Chicago Press. isbn 978 90 8964 676 7 e-isbn 978 90 4852 363 4 doi 10.5117/9789089646767 nur 670 © L. Mulvey, A. Backman Rogers / Amsterdam University Press B.V., Amsterdam 2015 All rights reserved. Without limiting the rights under copyright reserved above, no part of this book may be reproduced, stored in or introduced into a retrieval system, or transmitted, in any form or by any means (electronic, mechanical, photocopying, recording or otherwise) without the written permission of both the copyright owner and the author of the book. Contents Editorial 9 Preface 10 Acknowledgments 15 Introduction: 1970s Feminist Film Theory and the Obsolescent Object 17 Laura Mulvey PART I New Perspectives: Images and the Female Body Disconnected Heroines, Icy Intelligence: Reframing Feminism(s) -

The Porn Circuit Understand Your Brain and Break Porn Habits in 90 Days XXX
XXX tHe porn Circuit Understand your brain and break porn habits in 90 days XXX Table of Contents Introduction: Stop Looking at Porn, You Sicko! 3 www.covenanteyes.com Chapter 1: Your Sexy Plastic Brain 6 1.877.479.1119 1525 W. King St., PO Box 637 Chapter 2: Owosso, MI 48867 Your Brain’s Sexual Cocktail 9 Copyright © 2013 Covenant Eyes, Inc. All rights reserved. Chapter 3: Stuck in a Rut 14 You are free to distribute print copies of this e-book to anyone you choose. As a courtesy, e-mail us at [email protected] Chapter 4: and let us know you are doing this so we can 32 Flavors: Why We Like Sexual Variety 20 keep you informed of other similar resources. To distribute this e-book electronically, we ask that you share the page: Chapter 5: www.covenanteyes.com/science-of-porn- Ain’t Nothing Like the Real Thing, Baby 24 addiction-ebook For more information about sharing our Chapter 6: materials electronically, see: Habits of Freedom 29 www.covenanteyes.com/permissions-policy/ Resources that can help 42 Endnotes 44 About The Author: Sam Black Sam Black is an Internet Safety Consultant and a manager at Covenant Eyes. He joined the Covenant Eyes team in 2007 after 18 years as a journalist, serving as a reporter and editor for newspapers and magazines in six states. He has been married for 17 years and is a father of two. The Porn Circuit | 2 XXX Introduction: Stop Looking at Porn, You Sicko! Comedian Bob Newhart has been making people laugh for decades. -
Heartthrob Can't Inject Life Into Latest Nicholas Sparks Tale
PAGE b8 THE STATE JOURNAL Ap RiL 19, 2012 Thursday ALMANAC 50 YEARS AGO Danny Rodgers set a new ‘Lucky One’ not Zac Efron school record for the high jump and Frankie Brown picked up 10 individual points in two hurdles events Heartthrob can’t inject life into latest Nicholas Sparks tale to lead the Franklin County Flyers to a 71.5 to 46.5 victory over Clark County in a dual By RogeR MooRe (Blythe Danner). Zac track meet at Kentucky State McT clA chy-TriBune news service Logan (Zac Efron) is a Efron College’s Alumni Field. brooding ex-soldier, and “The Lucky One” is the attends chivalrous. edgiest-ever film adaptation Warner 25 YEARS AGO “Isn’t he chivalrous, dear?” of the writings of Nicholas Bros. Franklin County School granny says, elbowing Beth. Sparks. Pic- board members attended Which isn’t saying much. And the viewer. tures the Kentucky School Boards Logan met Beth before she Yeah, it has the violence of “The Association conference in knew it. He found her photo Louisville. Mac Quarles, war, and the heat of near-sex. Lucky And profanity! Don’t forget in the dust after a fierce fire- Jack Badgett, Billy Perkins, fight in Iraq. He lost comrades One” Dr. Harry Cowherd and Lee the profanity! pre- But it still has the ro- that day, and one of them had Troutwine heard speakers miere mance novelist’s favorite her photo. Somehow, Logan offering national and state- tropes – most of them, any- manages to track Beth down held at wide perspectives on issues way. -

Is Mainstream Pornography Becoming Increasingly Violent and Do Viewers Prefer Violent Content?
The Journal of Sex Research ISSN: 0022-4499 (Print) 1559-8519 (Online) Journal homepage: http://www.tandfonline.com/loi/hjsr20 “Harder and Harder”? Is Mainstream Pornography Becoming Increasingly Violent and Do Viewers Prefer Violent Content? Eran Shor & Kimberly Seida To cite this article: Eran Shor & Kimberly Seida (2018): “Harder and Harder”? Is Mainstream Pornography Becoming Increasingly Violent and Do Viewers Prefer Violent Content?, The Journal of Sex Research, DOI: 10.1080/00224499.2018.1451476 To link to this article: https://doi.org/10.1080/00224499.2018.1451476 Published online: 18 Apr 2018. Submit your article to this journal View related articles View Crossmark data Full Terms & Conditions of access and use can be found at http://www.tandfonline.com/action/journalInformation?journalCode=hjsr20 THE JOURNAL OF SEX RESEARCH,00(00), 1–13, 2018 Copyright © The Society for the Scientific Study of Sexuality ISSN: 0022-4499 print/1559-8519 online DOI: https://doi.org/10.1080/00224499.2018.1451476 “Harder and Harder”? Is Mainstream Pornography Becoming Increasingly Violent and Do Viewers Prefer Violent Content? Eran Shor and Kimberly Seida Department of Sociology, McGill University, Montreal, Quebec, Canada It is a common notion among many scholars and pundits that the pornography industry becomes “harder and harder” with every passing year. Some have suggested that porn viewers, who are mostly men, become desensitized to “soft” pornography, and producers are happy to generate videos that are more hard core, resulting in a growing demand for and supply of violent and degrading acts against women in mainstream pornographic videos. We examined this accepted wisdom by utilizing a sample of 269 popular videos uploaded to PornHub over the past decade. -

Ashcroft V. Free Speech Coalition: How Can Virtual Child Pornography Be Banned Under the First Amendment?
Pepperdine Law Review Volume 31 Issue 3 Article 5 4-20-2004 Ashcroft v. Free Speech Coalition: How Can Virtual Child Pornography Be Banned Under the First Amendment? Virginia F. Milstead Follow this and additional works at: https://digitalcommons.pepperdine.edu/plr Part of the First Amendment Commons Recommended Citation Virginia F. Milstead Ashcroft v. Free Speech Coalition: How Can Virtual Child Pornography Be Banned Under the First Amendment?, 31 Pepp. L. Rev. Iss. 3 (2004) Available at: https://digitalcommons.pepperdine.edu/plr/vol31/iss3/5 This Note is brought to you for free and open access by the Caruso School of Law at Pepperdine Digital Commons. It has been accepted for inclusion in Pepperdine Law Review by an authorized editor of Pepperdine Digital Commons. For more information, please contact [email protected], [email protected], [email protected]. Ashcroft v. Free Speech Coalition: How Can Virtual Child Pornography Be Banned Under the First Amendment? TABLE OF CONTENTS I. BACKGROUND: OBSCENITY AND CHILD PORNOGRAPHY A. Roth v. United States B. Miller v. California C. New York v. Ferber D. Osborne v. Ohio E. Background to the CPPA II. ASHCROFT V. FREE SPEECH COALITION: THE COURT CONSIDERS A FIRST AMENDMENT CHALLENGE TO THE CPPA. A. Majority Opinion B. Justice Thomas's Concurrence C. Justice O'Connor'sConcurrence and Dissent in Part D. Chief Justice Rehnquist's Dissent E. The Reasoning of the Justices: Considerationsand Critique I. The Seduction of Children 2. Whets the Appetites of Pedophiles 3. Need to Eliminate the Market for Real Pornography 4. Hinders Prosecution 5. -

Homelessness, Survival Sex and Human Trafficking: As Experienced by the Youth of Covenant House New York
Homelessness, Survival Sex and Human Trafficking: As Experienced by the Youth of Covenant House New York May 2013 Jayne Bigelsen, Director Anti-Human Trafficking Initiatives, Covenant House New York*: Stefanie Vuotto, Fordham University: Tool Development and Validation Project Coordinators: Kimberly Addison, Sara Trongone and Kate Tully Research Assistants/Legal Advisors: Tiffany Anderson, Jacquelyn Bradford, Olivia Brown, Carolyn Collantes, Sharon Dhillon, Leslie Feigenbaum, Laura Ferro, Andrea Laidman, Matthew Jamison, Laura Matthews-Jolly, Gregory Meves, Lucas Morgan, Lauren Radebaugh, Kari Rotkin, Samantha Schulman, Claire Sheehan, Jenn Strashnick, Caroline Valvardi. With a special thanks to Skadden Arps, Slate, Meagher & Flom LLP and Affiliates for their financial support and to the Covenant House New York staff who made this report possible. And our heartfelt thanks go to the almost 200 Covenant House New York youth who shared their stories with us. *For questions on the use of the trafficking screening tool discussed in this report or anything else related to the substance of the study, please contact study author, Jayne Bigelsen at [email protected] Table of Contents: Executive Summary . 5 Introduction . 5 Key Findings . 6 Terminology . 7 Objectives/Method . 8 Results and Discussion . 10 Compelled Sex Trafficking . 10 Survival Sex . 11 Relationship between Sex Trafficking and Survival Sex . 12 Labor Trafficking . 13 Contributing Factors . 14 Average Age of Entry into Commercial Sexual Activity . 16 Transgender and Gay Youth . 16 Development and Use of the Trafficking Assessment Tool . 17 Implications for Policy and Practice . 19 Conclusion . 21 Appendix: Trafficking Screening Tool . 22 EXECUTIVE SUMMARY Introduction In recent years, the plight of human trafficking victims has received a great deal of attention among legislators, social service providers and the popular press. -

In the Supreme Court of Missouri ______
Electronically Filed OF Filed - SUPREME COURT MISSOURI - March 19, 2018 - 09 Electronically IN THE SUPREME COURT OF MISSOURI __________________________________________________________________ IN THE MATTER OF THE ) CARE AND TREATMENT OF ) No. SC96830 N.G., ) Respondent/Appellant. ) __________________________________________________________________ APPEAL TO THE SUPREME COURT OF MISSOURI FROM THE CIRCUIT COURT OF JACKSON COUNTY, MISSOURI SIXTEENTH JUDICIAL CIRCUIT THE HONORABLE KATHLEEN A. FORSYTH, JUDGE __________________________________________________________________ APPELLANT’S SUBSTITUTE BRIEF :28 AM __________________________________________________________________ Chelseá R. Mitchell, MOBar #63104 Attorney for Appellant Woodrail Centre, 1000 West Nifong Building 7, Suite 100 Columbia, Missouri 65203 Telephone (573) 777-9977 FAX (573) 777-9974 E-mail: [email protected] Electronically Filed OF Filed - SUPREME COURT MISSOURI - March 19, 2018 - 09 Electronically INDEX Page TABLE OF AUTHORITIES ............................................................................................... 3 JURISDICTIONAL STATEMENT .................................................................................... 8 STATEMENT OF FACTS .................................................................................................. 9 POINTS RELIED ON ....................................................................................................... 12 ARGUMENT .................................................................................................................... -

Universities of Leeds, Sheffield and York
promoting access to White Rose research papers Universities of Leeds, Sheffield and York http://eprints.whiterose.ac.uk/ This is an author produced version of a paper published in Philosophy and Phenomenological Research. White Rose Research Online URL for this paper: http://eprints.whiterose.ac.uk/3349/ Published paper Kieran, M. (2002) On Obscenity: The Thrill and Repulsion of the Morally Prohibited. Philosophy and Phenomenological Research, LXIV (1). pp. 31-56. ISSN 1933-1592 White Rose Research Online [email protected] On Obscenity: The Thrill and Repulsion of the Morally Prohibited Matthew Kieran, University of Leeds Abstract The paper proceeds by criticising the central accounts of obscenity proffered by Feinberg, Scruton and the suggestive remarks of Nussbaum and goes on to argue for the following formal characterization of obscenity: x is appropriately judged obscene if and only if either A/ x is appropriately classified as a member of a form or class of objects whose authorized purpose is to solicit and commend to us cognitive-affective responses which are (1) internalized as morally prohibited and (2) does so in ways found to be or which are held to warrant repulsion and (3) does so in order to a/ indulge first order desires held to be morally prohibited or b/ indulge the desire to be morally transgressive or the desire to feel repulsed or c/ afford cognitive rewards or d/ any combination thereof or B/ x successfully elicits cognitive-affective responses which conform to conditions (1)- (3). I: Introduction What is it for something to be obscene? The question is both interesting philosophically and of practical import.