Applications of Matching Theory in Constraint Programming
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Remembering Frank Harary
Discrete Mathematics Letters Discrete Math. Lett. 6 (2021) 1–7 www.dmlett.com DOI: 10.47443/dml.2021.s101 Editorial Remembering Frank Harary On March 11, 2005, at a special session of the 36th Southeastern International Conference on Combinatorics, Graph The- ory, and Computing held at Florida Atlantic University in Boca Raton, the famous mathematician Ralph Stanton, known for his work in combinatorics and founder of the Institute of Combinatorics and Its Applications, stated that the three mathematicians who had the greatest impact on modern graph theory have now all passed away. Stanton was referring to Frenchman Claude Berge of France, Canadian William Tutte, originally from England, and a third mathematician, an American, who had died only 66 days earlier and to whom this special session was being dedicated. Indeed, that day, March 11, 2005, would have been his 84th birthday. This third mathematician was Frank Harary. Let’s see what led Harary to be so recognized by Stanton. Frank Harary was born in New York City on March 11, 1921. He was the oldest child of Jewish immigrants from Syria and Russia. He earned a B.A. degree from Brooklyn College in 1941, spent a graduate year at Princeton University from 1943 to 1944 in theoretical physics, earned an M.A. degree from Brooklyn College in 1945, spent a year at New York University from 1945 to 1946 in applied mathematics, and then moved to the University of California at Berkeley, where he wrote his Ph.D. Thesis on The Structure of Boolean-like Rings, in 1949, under Alfred Foster. -

(November 12-13)- Page 545
College Park Program (October 30-31) - Page 531 Baton Rouge Program (November 12-13)- Page 545 Notices of the American Mathematical Society < 2.. c: 3 ('1) ~ z c: 3 C" ..,('1) 0'1 October 1982, Issue 220 Volume 29, Number 6, Pages 497-616 Providence, Rhode Island USA ISSN 0002-9920 Calendar of AMS Meetings THIS CALENDAR lists all meetings which have been approved by the Council prior to the date this issue of the Notices was sent to press. The summer and annual meetings are joint meetings of the Mathematical Association of America and the Ameri· can Mathematical Society. The meeting dates which fall rather far in the future are subject to change; this is particularly true of meetings to which no numbers have yet been assigned. Programs of the meetings will appear in the issues indicated below. First and second announcements of the meetings will have appeared in earlier issues. ABSTRACTS OF PAPERS presented at a meeting of the Society are published in the journal Abstracts of papers presented to the American Mathematical Society in the issue corresponding to that of the Notices which contains the program of the meet· ing. Abstracts should be submitred on special forms which are available in many departments of mathematics and from the office of the Society in Providence. Abstracts of papers to be presented at the meeting must be received at the headquarters of the Society in Providence, Rhode Island, on or before the deadline given below for the meeting. Note that the deadline for ab· stracts submitted for consideration for presentation at special sessions is usually three weeks earlier than that specified below. -

Decompositions and Graceful Labelings (Supplemental Material for Intro to Graph Theory)
Decompositions and Graceful Labelings (Supplemental Material for Intro to Graph Theory) Robert A. Beeler∗ December 17, 2015 1 Introduction A graph decomposition is a particular problem in the field of combinatorial designs (see Wallis [22] for more information on design theory). A graph decomposition of a graph H is a partition of the edge set of H. In this case, the graph H is called the host for the decomposition. Most graph decomposition problems are concerned with the case where every part of the partition is isomorphic to a single graph G. In this case, we refer to the graph G as the prototype for the decomposition. Further, we refer to the parts of the partition as blocks. As an example, consider the host graph Q3 as shown in Figure 1. In this case, we want to find a decomposition of Q3 into isomorphic copies of the path on three vertices, P3. We label the vertices of P3 as an ordered triple (a, b, c). where ab and bc are the edges of P3. The required blocks in the decompositions are (0, 2, 4), (1, 0, 6), (1, 3, 2), (1, 7, 5), (3, 5, 4), and (4, 6, 7). Usually, the goal of a combinatorial design is to determine whether the particular design is possible. The same is true for graph decompositions. Namely, given a host graph H and a prototype G, determine whether there exist a decomposition of H into isomorphic copies of G. Often, this is a difficult problem. In fact, there are entire books written on the subject (for ∗Department of Mathematics and Statistics, East Tennessee State University, Johnson City, TN 37614-1700 USA email: [email protected] 1 2 0 1 2 3 4 5 6 7 Figure 1: A P3-decomposition of a Q3 example, see Bos´ak [1] and Diestel [5]). -

Mathematics Throughout the Ages. II
Mathematics throughout the ages. II Helena Durnová A history of discrete optimalization In: Eduard Fuchs (editor): Mathematics throughout the ages. II. (English). Praha: Výzkumné centrum pro dějiny vědy, 2004. pp. 51–184. Persistent URL: http://dml.cz/dmlcz/401175 Terms of use: © Jednota českých matematiků a fyziků Institute of Mathematics of the Czech Academy of Sciences provides access to digitized documents strictly for personal use. Each copy of any part of this document must contain these Terms of use. This document has been digitized, optimized for electronic delivery and stamped with digital signature within the project DML-CZ: The Czech Digital Mathematics Library http://dml.cz MATHEMATICS THROUGHOUT THE AGES II A History of Discrete Optimization Helena Durnová PRAGUE 2004 This is a Ph.D. thesis written under the supervision of Prof. Eduard Fuchs, defended at the Department of Mathematics of the Faculty of Science of Masaryk University in Brno on 24st May 2001. Contents 1 Introduction 57 1.1 Optimality and Mathematics . 58 1.2 GraphTheory......................... 64 1.3 ObjectivesoftheThesis . 69 2 Mathematical Background 71 2.1 Basic Definitions in Graph Theory . 71 2.1.1 Directed and undirected graphs . 71 2.1.2 Weighted graphs . 74 2.1.3 Description of graphs . 75 2.2 Algorithms, Heuristics, Complexity . 77 2.2.1 Algorithms and heuristics . 77 2.2.2 Complexity ...................... 78 3 Shortest Path Problem 81 3.1 SpecificBackground . 82 3.2 Origins and Development of Shortest Path Problems . 83 3.3 Early Shortest Path Algorithms . 85 3.3.1 Shimbel,1954. .. .. .. .. .. 85 3.3.2 G. B. -

Matematický Časopis
Matematický časopis Anton Kotzig; Bohdan Zelinka Regular Graphs, Each Edge of Which Belongs to Exactly One s-Gon Matematický časopis, Vol. 20 (1970), No. 3, 181--184 Persistent URL: http://dml.cz/dmlcz/127084 Terms of use: © Mathematical Institute of the Slovak Academy of Sciences, 1970 Institute of Mathematics of the Academy of Sciences of the Czech Republic provides access to digitized documents strictly for personal use. Each copy of any part of this document must contain these Terms of use. This paper has been digitized, optimized for electronic delivery and stamped with digital signature within the project DML-CZ: The Czech Digital Mathematics Library http://project.dml.cz Matematický časopis 20 (1970), No. 3 REGULAR GRAPHS, EACH EDGE OF WHICH BELONGS TO EXACTLY ONE 8 GON ANTON KOTZIG, Bratislava and BOHDAN ZELINKA, Liberec At the Colloquium on Graph Theory at Tihany (1966) the first author expressed the following conjecture: To every pair of positive integers r, s there exists a regular graph G of the degree 2r, in which each edge belongs to exactly one s-gon. We are going to prove this conjecture. The conjecture is evidently true for s = 1 and 5 = 2. We define the (r, s)-graph as a graph whose vertex set is the union of two disjoint sets U and V, while each vertex of U has the degree r, each vertex of V has the degree s and each edge of this graph joins a vertex of U with a vertex of V. We shall prove a theorem, which has the character of a lemma for us. -

Historie Matematiky
30. MEZINÁRODNÍ KONFERENCE HISTORIE MATEMATIKY Jevíþko, 21. 8. – 25. 8. 2009 Praha 2009 1 Památce Jaroslava Šedivého (1934–1988) zakladatele konferencí Historie matematiky Všechna práva vyhrazena. Tato publikace ani žádná její þást nesmí být reprodu- kována nebo šíĜena v žádné formČ, elektronické nebo mechanické, vþetnČ fotokopií, bez písemného souhlasu vydavatele. © J. BeþváĜ, M. BeþváĜová (ed.), 2009 © MATFYZPRESS, vydavatelství Matematicko-fyzikální fakulty Univerzity Karlovy v Praze, 2009 ISBN 978-80-7378-092-0 2 Vážené kolegynČ, vážení kolegové, pĜedkládáme vám sborník obsahující texty tĜí vyzvaných pĜednášek, rekapitulaci uplynulých tĜiceti konferencí, texty delších a kratších sdČlení, které byly pĜihlášeny na jubilejní, 30. mezinárodní konferenci Historie matematiky. Všechny pĜíspČvky byly graficky a typograficky sjednoceny, nČkteré byly upraveny i jazykovČ. ZaĜazen byl též program konference a seznam všech úþastníkĤ, kteĜí se pĜihlásili ve stanoveném termínu (15. kvČten 2009). Sborník vznikl díky finanþní podpoĜe Katedry didaktiky matematiky MFF UK a Ústavu aplikované matematiky FD ýVUT. V první þásti sborníku jsou zaĜazeny hlavní pĜednášky, o nČž byli požádáni zkušení pĜednášející, kteĜí se vČnují matematice, dČjinám matematiky, souvislostem matematiky s ostatními sférami lidské þinnosti, výchovČ doktorandĤ, Ĝízení a organizaci vČdecké práce a mnoha dalším aktivitám. Ve druhé þásti sborníku jsou uveĜejnČny kratší þi delší pĜíspČvky jednotlivých úþastníkĤ. Konference není monotematicky zamČĜena, snažili jsme se poskytnout dostateþný prostor k aktivním vystoupením, diskusím a neformálním setkáním všem pĜihlášeným, tj. matematikĤm, historikĤm matematiky, uþitelĤm vysokých i stĜedních škol, doktorandĤm oboru Obecné otázky matematiky a informatiky i všem dalším zájemcĤm o matematiku a její vývoj. Program letošní konference je opČt pomČrnČ pestrý. VČĜíme, že každý najde Ĝadu témat, která ho zaujmou a potČší, že objeví nové kolegy, pĜátele a spolupracovníky, získá inspiraci, Ĝadu podnČtĤ, motivaci i povzbuzení ke své další odborné práci a ke svému studiu. -

Cycle Double Covers and Spanning Minors II
Cycle Double Covers and Spanning Minors II Roland H¨aggkvist and Klas Markstr¨om Abstract. In this paper we continue our investigations from [HM01] regarding spanning subgraphs which imply the existence of cycle doub- le covers. We prove that if a cubic graph G has a spanning subgraph isomorphic to a subdivision of a bridgeless cubic graph on at most 10 vertices then G has a CDC. A notable result is thus that a cubic graph with a spanning Petersen minor has a CDC, a result also obtained by Goddyn [God88]. 1. Introduction A cycle (or circuit) double cover, or CDC for short, of a graph G is a collection of cycles in G, not necessarily distinct, such that any edge in G belongs to exactly two of the cycles. Here we use the currently standard graph theoretical definition of a cycle, a connected 2-regular graph, although in this subject it is often the case that the word cycle is used for a spanning subgraph with all vertex degrees even — by default we also use the word graph for simple graph. The outstanding problem in the theory of cycle double covers, and by now one of the classic unsolved problems in graph theory, is the following Conjecture 1.1. Every 2-edge-connected graph has a cycle double cover. This conjecture has become known as the cycle double cover conjecture (CDCC) and is generally attributed to Seymour [Sey79] and Szekeres [Sze73]. The subject of graph embeddings is of course much older, and, as pointed out by Seymour, some forms of the conjecture may also have been present in earlier work by Tutte for instance. -

Aviezri Fraenkel and Combinatorial Games
Aviezri Fraenkel and Combinatorial Games Richard K. Guy Calgary, Canada The subject of combinatorial games has, like combinatorics itself, been slow to find recognition with the mathematical establishment. Combinatorics is now on sure ground, and combinatorial games is well on its way. This is in no small part due to the energy, enthusiasm and insight of Aviezri Fraenkel, who has linked combinatorial games with much else in mathematics | graph theory [24], error-correcting codes [22], numeration systems [25, 28], continued fractions [17] and especially complexity theory. The great variety in the difficulty of the vast range of combinatorial games has en- abled him to exhibit the whole spectrum of complexity theory [18, 27, 55], He has also ascertained the status of many particular combinatorial games [34], diophantine games [60], the Grundy function [14], chess [40], and checkers [33]. His interest in games may well have been sparked by a classic paper of Coxeter [6]: certainly he has long been fascinated by the relation between Beatty sequences, i.e. com- plementing sequences of integers, on the one hand, and Wythoff's Game [9, 39, 11, 1, 8] on the other. Wythoff's Game is played with two heaps from which players alternately take any number from one heap or equal numbers from each; several of Aviezri's papers have been concerned with generalizations of this game [3, 7, 15, 17, 32, 45, 61]. He has written on a variety of individual games, many of which are his own invention: Nimbi [36], Nimhoff games [43], and Nim itself [4]; Geography [50], Epidemiography [41, 42, 44], geodetic contraction games [35], Particles and Antiparticles [12], a deletion game [48], a new heap game [58], modular Nim (sometimes called Kotzig's Nim) [37], Multivision [26], partizan octal and subtraction games [38] and extensions of Conway's `short games' [52]. -

Notices of the American Mathematical Society
Notices of the American Mathematical Society November 1985, Issue 244 Volume 32, Number 6, Pages 737- 872 Providence, Rhode Island USA ISSN 0002-9920 Calendar of AMS Meetings THIS CALENDAR lists all meetings which have been approved by the Council prior to the date this issue of the Notices was sent to the press. The summer and annual meetings are joint meetings of the Mathematical Association of America and the American Mathematical Society. The meeting dates which fall rather far in the future are subject to change: this is particularly true of meetings to which no numbers have yet been assigned. Programs of the meetings will appear in the issues indicated below. First and supplementary announcements of the meetings will have appeared in earlier issues. ABSTRACTS OF PAPERS presented at a meeting of the Society are published in the journal Abstracts of papers presented to the American Mathematical Society in the issue corresponding to that of the Notices which contains the program of the meeting. Abstracts should be submitted on special forms which are available in many departments of mathematics and from the headquarters office of the Society. Abstracts of papers to be presented at the meeting must be received at the headquarters of the Society in Providence. Rhode Island, on or before the deadline given below for the meeting. Note that the deadline for abstracts for consideration for presentation at special sessions is usually three weeks earlier than that specified below. For additional information consult the meeting announcements and the list of organizers of special sessions. ABSTRACT MEETING# DATE PLACE DEADLINE ISSUE 825 January 7-11. -
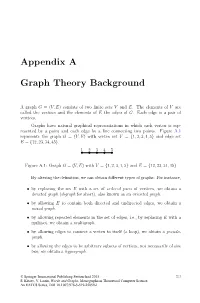
Appendix a Graph Theory Background
Appendix A Graph Theory Background A graph G = (V; E) consists of two finite sets V and E. The elements of V are called the vertices and the elements of E the edges of G. Each edge is a pair of vertices. Graphs have natural graphical representations in which each vertex is rep- resented by a point and each edge by a line connecting two points. Figure A.1 represents the graph G = (V; E) with vertex set V = f1; 2; 3; 4; 5g and edge set E = f12; 23; 34; 45g. 1 2 3 4 5 Figure A.1: Graph G = (V; E) with V = f1; 2; 3; 4; 5g and E = f12; 23; 34; 45g By altering the definition, we can obtain different types of graphs. For instance, • by replacing the set E with a set of ordered pairs of vertices, we obtain a directed graph (digraph for short), also known as an oriented graph. • by allowing E to contain both directed and undirected edges, we obtain a mixed graph. • by allowing repeated elements in the set of edges, i.e., by replacing E with a multiset, we obtain a multigraph. • by allowing edges to connect a vertex to itself (a loop), we obtain a pseudo- graph. • by allowing the edges to be arbitrary subsets of vertices, not necessarily of size two, we obtain a hypergraph. © Springer International Publishing Switzerland 2015 231 S. Kitaev, V. Lozin, Words and Graphs, Monographs in Theoretical Computer Science. An EATCS Series, DOI 10.1007/978-3-319-25859-1 232 Appendix A. -

Two Hamiltonian Cycles of L(G), As Follows
TWO HAMILTONIAN CYCLES VAIDY SIVARAMAN AND THOMAS ZASLAVSKY Abstract. If the line graph of a graph G decomposes into Hamiltonian cycles, what is G? We answer this question for decomposition into two cycles. Prelude Two problems that are known to be NP-complete are: Is a cubic graph Hamiltonian [2]? Does a graph L decompose into two Hamiltonian cycles [8]? An example for L is the line graph of a cubic graph G: L(G) has a Hamilton decomposition if and only if G, the root graph, is Hamiltonian; this was discovered by Kotzig [4] and later Martin [6]. (We say a graph is Hamilton decomposable if its edge set partitions into Hamiltonian cycles.) The proofs are by polynomial-time constructions. Since Hamiltonicity of a cubic graph is NP-complete, it follows that Hamiltonian decomposability of a 4-regular graph remains NP-complete when restricted to line graphs of cubic graphs. An opposite question seems not to have been asked. (It was briefly considered by the second author for an undergraduate graph theory examination.) Problem 1. The line graph L(G) of a simple graph G is decomposable into two Hamiltonian cycles. What is G? We answer this question by characterizing all root graphs G. One would like to describe all Hamilton decomposable line graphs. We offer some thoughts at the end of this paper. Presto Theorem 2. The graph G of Problem 1 is either K1,5, or the first subdivision of a 4-regular graph G′ that decomposes into two Hamiltonian cycles, or a Hamiltonian cubic graph. The first subdivision SG of a graph G is obtained by subdividing every edge into a path of length 2. -

Graphs Without Dead Ends
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Elsevier - Publisher Connector Europ . J . Combinatorics (1996) 17 , 69 – 87 Graphs Without Dead Ends G ERT S ABIDUSSI In memory of Anton Kotzig . We consider graphs G which are antipodal in the sense that the distance function of G , rooted at any vertex , has a unique relative maximum . These graphs can be characterised as a certain type of 2-cover of their natural quotient , obtained by identifying each vertex with its antipode . We use this characterisation to discuss various properties of antipodal graphs , e . g . their degrees , girth , and automorphisms . ÷ 1995 Academic Press Limited . 1 . I NTRODUCTION The hypercubes Q n are prototypes of a class of graphs with an interesting property which , in spite of an obvious potential for applications , has hitherto received little attention in the literature . It is usually referred to as antipodality , although distance- additivity would be an equally justifiable term . Put crudely , the property is that , starting at any vertex of the graph , one can go to a diametrically opposite vertex in such a way as to pass through any third vertex without making a detour . To be precise , a connected graph G is antipodal if for any vertex x P V ( G ) there is an x# P V ( G ) such that d ( x , y ) 1 d ( y , x# ) 5 d ( x , x# ) for all y P V ( G ) , (1) where d is the usual shortest path distance . It is then immediate that x# (the antipode of x ) is unique and that d ( x , x# ) equals the diameter of G .