Annual Report 2006 Two Year Summary of Financial Results Reconciliation of Gaap to Non-Gaap Financials
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Cluster Server Installation Guide
Veritas™ Cluster Server Installation Guide Solaris 5.0 N18534F Veritas Cluster Server Installation Guide Copyright © 2006 Symantec Corporation. All rights reserved. Veritas Cluster Server 5.0 Symantec, the Symantec logo, Veritas are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THIS DOCUMENTATION IS PROVIDED “AS IS” AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID, SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be “commercial computer software” and “commercial computer software documentation” as defined in FAR Sections 12.212 and DFARS Section 227.7202. Symantec Corporation 20330 Stevens Creek Blvd. Cupertino, CA 95014 www.symantec.com Third-party legal notices Third-party software may be recommended, distributed, embedded, or bundled with this Symantec product. Such third-party software is licensed separately by its copyright holder. All third-party copyrights associated with this product are listed in the accompanying release notes. -

VERITAS Cluster Server 4.0 Installation Guide for Linux
VERITAS Cluster Server 4.0 Installation Guide Linux N10923H August 2004 Disclaimer The information contained in this publication is subject to change without notice. VERITAS Software Corporation makes no warranty of any kind with regard to this manual, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. VERITAS Software Corporation shall not be liable for errors contained herein or for incidental or consequential damages in connection with the furnishing, performance, or use of this manual. VERITAS Legal Notice Copyright © 1998-2004 VERITAS Software Corporation. All rights reserved. VERITAS, the VERITAS logo, VERITAS Cluster Server, and all other VERITAS product names and slogans are trademarks or registered trademarks of VERITAS Software Corporation. VERITAS and the VERITAS logo, Reg. U.S. Pat. & Tm. Off. Other product names and/or slogans mentioned herein may be trademarks or registered trademarks of their respective companies. VERITAS Software Corporation 350 Ellis Street Mountain View, CA 94043 USA Phone 650–527–8000 Fax 650–527–2908 www.veritas.com Third-Party Copyrights Apache License Version 2.0, January 2004 http://www.apache.org/licenses/ TERMS AND CONDITIONS FOR USE, REPRODUCTION, AND DISTRIBUTION 1. Definitions. “License” shall mean the terms and conditions for use, reproduction, and distribution as defined by Sections 1 through 9 of this document. “Licensor” shall mean the copyright owner or entity authorized by the copyright owner that is granting the License. “Legal Entity” shall mean the union of the acting entity and all other entities that control, are controlled by, or are under common control with that entity. -

Symantec™ Cluster Server 6.2.1 Installation Guide - Linux
Symantec™ Cluster Server 6.2.1 Installation Guide - Linux Platform Release OL7 UEK R3 April 2015 Symantec™ Cluster Server Installation Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Product version: 6.2.1 Document version: 6.2.1 Rev 0 Legal Notice Copyright © 2015 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Veritas, Veritas Storage Foundation, CommandCentral, NetBackup, Enterprise Vault, and LiveUpdate are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, "Rights in Commercial Computer Software or Commercial Computer Software Documentation", as applicable, and any successor regulations, whether delivered by Symantec as on premises or hosted services. -

Norton Antivirus Product Manual
NortonTM AntiVirus Product Manual Care for our Environment; ‘It's the right thing to do.’ Symantec has removed the cover from this manual to reduce the Environmental Footprint of our products. This manual is made from recycled materials. Norton AntiVirus™ Product Manual The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 21.4 Copyright © 2014 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, LiveUpdate, Norton 360, and Norton are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Portions of this product Copyright 1996-2011 Glyph & Cog, LLC. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED “AS IS” AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, et seq. -

Zerohack Zer0pwn Youranonnews Yevgeniy Anikin Yes Men
Zerohack Zer0Pwn YourAnonNews Yevgeniy Anikin Yes Men YamaTough Xtreme x-Leader xenu xen0nymous www.oem.com.mx www.nytimes.com/pages/world/asia/index.html www.informador.com.mx www.futuregov.asia www.cronica.com.mx www.asiapacificsecuritymagazine.com Worm Wolfy Withdrawal* WillyFoReal Wikileaks IRC 88.80.16.13/9999 IRC Channel WikiLeaks WiiSpellWhy whitekidney Wells Fargo weed WallRoad w0rmware Vulnerability Vladislav Khorokhorin Visa Inc. Virus Virgin Islands "Viewpointe Archive Services, LLC" Versability Verizon Venezuela Vegas Vatican City USB US Trust US Bankcorp Uruguay Uran0n unusedcrayon United Kingdom UnicormCr3w unfittoprint unelected.org UndisclosedAnon Ukraine UGNazi ua_musti_1905 U.S. Bankcorp TYLER Turkey trosec113 Trojan Horse Trojan Trivette TriCk Tribalzer0 Transnistria transaction Traitor traffic court Tradecraft Trade Secrets "Total System Services, Inc." Topiary Top Secret Tom Stracener TibitXimer Thumb Drive Thomson Reuters TheWikiBoat thepeoplescause the_infecti0n The Unknowns The UnderTaker The Syrian electronic army The Jokerhack Thailand ThaCosmo th3j35t3r testeux1 TEST Telecomix TehWongZ Teddy Bigglesworth TeaMp0isoN TeamHav0k Team Ghost Shell Team Digi7al tdl4 taxes TARP tango down Tampa Tammy Shapiro Taiwan Tabu T0x1c t0wN T.A.R.P. Syrian Electronic Army syndiv Symantec Corporation Switzerland Swingers Club SWIFT Sweden Swan SwaggSec Swagg Security "SunGard Data Systems, Inc." Stuxnet Stringer Streamroller Stole* Sterlok SteelAnne st0rm SQLi Spyware Spying Spydevilz Spy Camera Sposed Spook Spoofing Splendide -

Norton Antivirus™ Producthandleiding
NortonTM AntiVirus Producthandleiding Zorg voor het milieu: een vanzelfsprekende zaak. Symantec heeft de kaft van deze handleiding verwijderd om de ecologische voetafdruk van onze producten te verkleinen. Deze handleiding is gemaakt van gerecyclede materialen. Norton AntiVirus™ Producthandleiding De software die in deze handleiding wordt beschreven, wordt geleverd met een licentieovereenkomst en mag alleen worden gebruikt in overeenstemming met de voorwaarden in deze overeenkomst. Documentatieversie 21.0 Copyright © 2013 Symantec Corporation. Alle rechten voorbehouden. Symantec, het Symantec-logo, LiveUpdate, Norton 360 en Norton zijn handelsmerken of gedeponeerde handelsmerken van Symantec Corporation of haar aangesloten ondernemingen in de Verenigde Staten en andere landen. Delen van dit product Copyright 1996-2011 Glyph & Cog, LLC. Andere namen kunnen handelsmerken zijn van hun respectieve eigenaars. Het product dat in dit document wordt beschreven, wordt gedistribueerd onder licenties waarmee het gebruik, het kopiëren, het distribueren en het decompileren/toepassen van reverse-engineering ervan wordt beperkt. Geen enkel deel van dit document mag worden gereproduceerd in enige vorm op enige wijze zonder voorafgaande schriftelijke toestemming van Symantec Corporation en zijn eventuele licentiegevers. DE DOCUMENTATIE WORDT ALS ZODANIG GELEVERD EN ALLE EXPLICIETE OF IMPLICIETE VOORWAARDEN, REPRESENTATIES EN GARANTIES, WAARONDER IMPLICIETE GARANTIES VAN VERHANDELBAARHEID, GESCHIKTHEID VOOR EEN BEPAALD DOEL OF NIET-INBREUKMAKENDHEID, WORDEN -
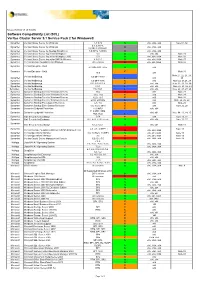
Wxrt VCS for Windows 5.1 SCL Based GA Version
Release Revision 1.6 25 Oct 2012 Software Compatibility List (SCL) Veritas Cluster Server 5.1 Service Pack 2 for Windows® Symantec Veritas Cluster Server for Windows 5.1 SP2 S x86, IA64, x64 Note 01, 02 5.1, 5.1AP1, Symantec Veritas Cluster Server for Windows U x86, IA64, x64 5.1SP1,5.1SP1AP1 Symantec Veritas Cluster Server for NetApp SnapMirror 5.0 RP1a, 5.0RP2 U x86, IA64, x64 Symantec Veritas Cluster Server Agent for Websphere 5.1 S x86, x64 Note 05 Symantec Veritas Cluster Server Agent for Websphere MQ 5.0 S x86, x64, IA64 Note 06 Symantec Veritas Cluster Server Agent for SAP NetWeaver 4.3.01.0 S x86, x64, IA64 Note 07 Symantec Veritas Storage Foundation for Windows All versions X x86, x64, IA64 Note 02 Symantec Veritas Enterprise Vault 8.0 SP1-SP5, 9.0.x S x86 Symantec Veritas Enterprise Vault C Note 31 10.0 x86 Note 21, 22, 23, 28, Veritas NetBackup 6.0 MP1-MP3 Symantec L x86 29 Symantec Veritas NetBackup 6.0 MP4-MP6 C x86 Note 22, 23,28, 29 Symantec Veritas NetBackup 6.5, 6.5.2-6.5.4 C x86, x64 Note 22, 23, 28, 29 Symantec Veritas NetBackup 6.5.1 L x86, x64 Note 22, 23, 28, 29 Symantec Veritas NetBackup 7.0, 7.0.1 L x86, x64 Note 22, 23, 27, 28 Symantec Symantec Backup Exec for Windows Servers 10.x X x86 Note 28 Symantec Symantec Backup Exec for Windows Servers 11.0, 11d C x86 Note 28 Symantec Symantec Backup Exec for Windows Servers 12.0, 12.5 C x86 Note 28 Symantec Symantec Backup Exec for Windows Servers 2010, 2010 R2 L x86 Note 24, 25, 28 Symantec Symantec Backup Exec System Recovery 6.5, 7.0 C x86 Note 28 Symantec Symantec -

System Requirements General Disclaimers & Disclosures
General Disclaimers & Disclosures Noonecanpreventallcybercrimeoridentitytheft. ²RequiresyourdevicetohaveanInternet/dataplanandbeturnedon. 1PAYMENT METHOD REQUIRED FOR 1 YEAR PRE-PAID SUBSCRIPTION:Youare ³Defaultstomonitoryouremailaddressonly.LogintoyourNortonaccounttoenter purchasingarecurringsubscriptionwhichwillautomaticallyrenewafterthefirst moreinfoformonitoring.IfyouareacurrentLifeLockmember,youmustreview year.Toactivate,youmustenrollonlineandprovideyourbillinginformation.The andmanagethosesettingsinyourLifeLockportal. pricepaidtodayisvalidforthefirstyearofyoursubscription,andwillautomatically renewandchargeyourstoredpaymentmethodtheapplicablerenewalpricefound *VirusProtectionPromise:Restrictionsapply.Mustsubscribewithautomatic atwww.us.norton.com/pricing.Thepriceissubjecttochange,butwewillalways renewal.SeeNorton.com/guaranteefordetails. sendyouanotificationemailinadvance.Youmaycanceltheautomaticrenewalby ‡NortonFamilyParentalControlfeaturesarenotsupportedonMac. loggingintoyouraccount,orcontactingusat:844-488-4540. Yourcoveragemayincludeproduct,serviceand/orprotectionupdatesand featuresthatmaybeadded,modifiedorremoved,subjecttotheapplicableTerms &ConditionsfoundonNortonLifeLock.com.Datacollection,storageandusefor subscriptionmanagementandrenewalpurposessubjecttoourGlobalPrivacy Statementfoundatwww.nortonlifelock.com/privacy. System Requirements • Notallfeaturesareavailableonallplatforms. ™ • Norton™360isavailablefor1,3,5,10and20Devices(PC,Mac®,iOS Norton AntiVirus Plus Available for 1 Windows™ PC or Mac® andAndroid) • NortonAntiVirus™Plusisavailablefor1PCorMac® -

Norton Utilities TM
Norton TM Norton Utilities Proof Utilities of Purchase Benutzerhandbuch Wir schützen weltweit mehr Benutzer vor Bedrohungen aus dem Internet als jedes andere Unternehmen. Umweltschutz ist wichtig. Symantec hat dieses Handbuch ohne Umschlag gestaltet, um die Einwirkung auf die Umwelt durch unsere Produkte zu reduzieren. TM Norton Utilities Benutzerhandbuch Die in diesem Handbuch beschriebene Software wird unter Lizenz vertrieben und darf nur entsprechend den Vertragsbedingungen verwendet werden. Dokumentationsversion 14.0 Copyright © 2009 Symantec Corporation. Alle Rechte vorbehalten. Symantec, das Symantec-Logo, Norton, Ghost, GoBack, LiveUpdate, Norton AntiSpam, Norton AntiVirus, Norton Internet Security, Norton 360 und Norton SystemWorks sind Marken oder eingetragene Marken der Symantec Corporation oder ihrer Tochtergesellschaften in den USA und anderen Ländern. Windows ist eine Marke der Microsoft Corporation. Andere Produktnamen können Marken der jeweiligen Rechteinhaber sein. Die in diesem Handbuch beschriebene Software wird Ihnen im Rahmen einer Lizenzvereinbarung zur Verfügung gestellt und darf nur unter den darin beschriebenen Bedingungen eingesetzt, kopiert, verteilt, dekompiliert und zurückentwickelt werden. Kein Teil dieser Veröffentlichung darf ohne ausdrückliche schriftliche Genehmigung der Symantec Corporation und ihrer Lizenzgeber vervielfältigt werden. DIE DOKUMENTATION WIRD "OHNE MÄNGELGEWÄHR" GELIEFERT. ALLE AUSDRÜCKLICHEN ODER STILLSCHWEIGENDEN BEDINGUNGEN, DARSTELLUNGEN UND GEWÄHRLEISTUNGEN EINSCHLIESSLICH DER STILLSCHWEIGENDEN -

Wsn, COURT STAFF) (Filed on 8/23/2013
Haskins v. Symantec Corporation Doc. 32 1 2 3 4 UNITED STATES DISTRICT COURT 5 NORTHERN DISTRICT OF CALIFORNIA 6 KATHLEEN HASKINS, 7 Case No. 13-cv-01834-JST Plaintiff, 8 v. ORDER GRANTING MOTION TO 9 DISMISS SYMANTEC CORPORATION, 10 ECF No. 22 Defendant. 11 12 13 Before the Court is Defendant Symantec Corporation’s (“Symantec”) Motion to Dismiss 14 Plaintiff’s First Amended Complaint (“Motion”). ECF No. 22. The Court has carefully 15 considered the papers filed in support of the motion and finds the matter appropriate for resolution 16 without oral argument. See Civil L.R. 7-1(b). The hearing scheduled for August 29, 2013 is 17 therefore VACATED. United States District United Court District States Northern District of California Northern California of District 18 I. BACKGROUND 19 A. Factual Background 20 The Court accepts the following allegations as true for the purpose of resolving 21 Defendant’s motion to dismiss. Cahill v. Liberty Mutual Ins. Co., 80 F.3d 336, 337–38 (9th Cir. 22 1996). 23 Symantec provides security, storage, and systems management to consumers, small 24 businesses, and large global organizations through its antivirus, data management utility and 25 enterprise software products. First Amended Complaint (“FAC”), ECF No. 17, ¶ 3. In 2006, 26 hackers infiltrated Symantec’s network and stole the source code for the 2006 versions of 27 pcAnywhere, Norton SystemWorks, Norton Antivirus Corporate Edition and Norton Internet 28 Dockets.Justia.com 1 Security (which Plaintiff identifies in the FAC the “Compromised Symantec Products”1). Id. ¶ 18. 2 The stolen Symantec source code includes instructions written in various computer programming 3 languages, and comments made by engineers to explain the design of the software. -

Yes, Virginia, There Really Is a Norton
05_579932 bk01ch01.qxd 2/24/05 10:44 PM Page 9 Chapter 1: Getting to Know Norton Products In This Chapter ߜ Appreciating Norton’s long history in the PC help biz ߜ Figuring out exactly who Norton is ߜ Getting to know Norton products by type ven if you’re brand-spankin’-new to computers, and before you pur- Echased your Norton software, you probably heard or read the name Norton many times. In fact, Norton is one of the relatively few PC-industry names that has been with us since early on in the history of personal com- puters. If you only knew how many companies have gone bust or been bought up by bigger firms over the last two-plus decades, you would be astounded! This chapter introduces you to the various tools that are available under the Norton name (plenty!). Here, I focus in on the type of software, because you have so many different ones to choose from. Just as finding and using the right tool in your household tool chest is important when you’re want- ing to do a specific repair, choosing the right Norton product for the PC protection, repair, or maintenance job you face is important — and in this chapter, I help you do just that. Norton: A Name Long Associated with PC Care IBM’s name is still associated with the original PC-class computer that rolled out in 1981. This is true even though so many other manufacturers have joined theCOPYRIGHTED PC design and rollout industry. MATERIAL Not very long after the debut of the IBM PC, the name IBM was joined by the name Norton for some of the first utilities created to help consumers work with those PCs. -

(In) Security in Security Products 2013
iViZ Security Inc (In) Security in Security Products 2013 ©iViZ Security Inc 2013 Introduction We use security products to secure our systems and our businesses. However, the very security products we use, can themselves have vulnerabilities which can leave us susceptible to attacks. In this annual report iViZ studies the vulnerability trends in security products. In our last year’s report, we published trends in major security products and security vendors. We concluded with the fact that security products and vendors are as vulnerable and insecure as are any other products and vendors respectively. We took some time to find out what were the major security breaches over the last couple of years and the results are quite interesting. In 2012 alone, some major security vendors like Symantec Corporation, GlobalCerts and Panda Security among others got targeted and breached by attackers. Here is a summary of some recent major events of Security companies that got hacked. Symantec Corporation -Security software giant attacked by anonymous hacker in Jan 2012 The company had source code stolenfor software titles like Norton Antivirus corporate edition, Norton Internet security, Norton Utilities, Norton GoBack and pcAnywhere. They were hacked again in November with the complete database from the Symantec online portal leaked. Their employee’s database containing email addresses and passwords was breachedwith the loss of around 3,195 records. Panda Security, a cloud security company was hacked by LulzSec and the hacking group Anonymous in Mar 2012 Multiple usernames and passwords of employees were breached. Atleast 35 of their public facing websites hacked. GlobalCerts, a firm which provides Email Security Solutions hacked by an anonymous hacker in Aug 2012 Database hacked with over 1000 client details leaked.