Searching for Privacy: How to Protect Your Search Activity
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Paid Social Trends Iprospect QUARTERLY REPORT | 2017 Q4
Paid Social Trends iPROSPECT QUARTERLY REPORT | 2017 Q4 By Brittany Richter, VP, Head of Social Media and Katherine Patton, Director, Paid Social iProspect.com COPYRIGHT 2018 © iPROSPECT, INC. ALL RIGHTS RESERVED. iProspect Quarterly Report Paid Social Trends | 2017 Q4 2 Reviewing Overarching Q4 2017 Trends While the cost of inventory continues to rise, so does the value that brands see in paid social advertising. The brands that saw the strongest Q4 business performance were the ones that leveraged the Facebook pixel, optimized toward site engagement (Retail) or Reach (CPG, branding), took advantage of Dynamic Broad Audiences (DABA), and planned content designed for the feed. Based on iProspect client data, paid social continues to drive performance in its own right while also fueling our clients’ first-party data, which can be leveraged to drive cross-channel performance. The following trends and insights are based on analysis of the data from more than 210 brands managed by iProspect U.S. (though the spend is not confined to U.S. mar- kets). The spend data is representative of Facebook, Instagram, Pinterest, Snap, Inc., and Twitter, while performance data is specific to Facebook and Instagram only. SPEND Overall, iProspect’s paid social clients’ total Q4 social spend was up 72% quarter over quarter (QoQ) compared to Q3 2017, and 86% year over year (YoY) when compared to Q4 of 2016. Q4 is consistently the busiest time of the year for many of our clients, so it’s not unusual to see an increase spend as they strive to hit annual goals and capitalize on the holiday time period. -

Longitudinal Study of Links, Linkshorteners, and Bitly Usage on Twitter Longitudinella Mätningar Av Länkar, Länkförkortare Och Bitly An- Vänding På Twitter
Linköping University | Department of Computer and Information Science Bachelor’s thesis, 16 ECTS | Link Usage 2020 | LIU-IDA/LITH-EX-G--20/001--SE Longitudinal study of links, linkshorteners, and Bitly usage on Twitter Longitudinella mätningar av länkar, länkförkortare och Bitly an- vänding på Twitter Mathilda Moström Alexander Edberg Supervisor : Niklas Carlsson Examiner : Marcus Bendtsen Linköpings universitet SE–581 83 Linköping +46 13 28 10 00 , www.liu.se Upphovsrätt Detta dokument hålls tillgängligt på Internet - eller dess framtida ersättare - under 25 år från publicer- ingsdatum under förutsättning att inga extraordinära omständigheter uppstår. Tillgång till dokumentet innebär tillstånd för var och en att läsa, ladda ner, skriva ut enstaka ko- pior för enskilt bruk och att använda det oförändrat för ickekommersiell forskning och för undervis- ning. Överföring av upphovsrätten vid en senare tidpunkt kan inte upphäva detta tillstånd. All annan användning av dokumentet kräver upphovsmannens medgivande. För att garantera äktheten, säker- heten och tillgängligheten finns lösningar av teknisk och administrativ art. Upphovsmannens ideella rätt innefattar rätt att bli nämnd som upphovsman i den omfattning som god sed kräver vid användning av dokumentet på ovan beskrivna sätt samt skydd mot att dokumentet ändras eller presenteras i sådan form eller i sådant sammanhang som är kränkande för upphovsman- nens litterära eller konstnärliga anseende eller egenart. För ytterligare information om Linköping University Electronic Press se förlagets hemsida http://www.ep.liu.se/. Copyright The publishers will keep this document online on the Internet - or its possible replacement - for a period of 25 years starting from the date of publication barring exceptional circumstances. The online availability of the document implies permanent permission for anyone to read, to down- load, or to print out single copies for his/hers own use and to use it unchanged for non-commercial research and educational purpose. -
Webtrekk Documentation
Documentation Webtrekk GmbH | Robert-Koch-Platz 4 | 10115 Berlin Webtrekk Support | [email protected] Teaser Tracking Plugin (v2) Table of Contents 1 Disclaimer 3 1.1 Introduction 4 2 Technical Requirements 5 2.1 Browser Support 5 3 Creating Teaser Parameters 6 4 Configuring and Activating the Plugin 8 4.1 Tag Integration (Web) 8 4.2 JavaScript 10 5 Initializing the Teaser Elements 13 6 Best Practices 16 6.1 View Tracking with Dynamic Teaser Insertion 16 6.2 View Tracking 17 6.3 Customizing a Website Goal 18 6.4 Customizing the Engagement Page 18 12/13/2018 2/18 Teaser Tracking Plugin (v2) 1 Disclaimer This manual is the intellectual property of Webtrekk GmbH. This includes the contents but also all images, tables, and drawings. Change or removal of copyright notices, registering mark or control numbers are not allowed. Any use not permitted by German copyright law requires the prior written consent of the respective author or creator. This applies in particular to reproduction, editing, translation, storage, processing or distribution of contents in databases or other electronic media and systems. Webtrekk GmbH allows the use of the content solely for the contractual purpose. It should be noted that the contents of this manual may be subject to changes, without that a reporting obligation on the part of Webtrekk GmbH can be derived from this. Users of this manual must independently obtain information themselves, whether modified versions or notes to the contents are present, for example on the Internet at https://docs.webtrekk.com/, and take these into account during operation. -
Overview Trackings
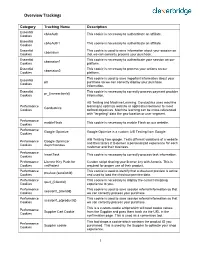
Overview Trackings Category Tracking Name Description Essential cbAcAuth This cookie is necessary to authenticate an affiliate. Cookies Essential cbAcAuth1 This cookie is necessary to authenticate an affiliate. Cookies Essential This cookie is used to save information about your session so cbsession Cookies that we can correctly process your purchase. Essential This cookie is necessary to authenticate your session on our cbsession1 Cookies platform. Essential This cookie is necessary to process your actions on our cbsession2 Cookies platform. This cookie is used to save important information about your Essential p0 purchase so we can correctly display your purchase Cookies information. Essential This cookie is necessary to correctly process payment provider pr_{transactionId} Cookies information. AB Testing and Machine Learning. Conductrics uses machine Performance learning to optimize website or application behavior to meet Conductrics Cookies defined objectives. Machine learning can be cross-referenced with "targeting" data like geo-location or user segment. Performance enableFlash This cookie is necessary to enable Flash on our website. Cookies Performance Google Optimize Google Optimize is a custom A/B Testing from Google. Cookies A/B Testing from google. Tests different variations of a website Performance Google Optimizer and then tailors it to deliver a personalized experience for each Cookies Asynchronous customer and their business. Performance InsertTask This cookie is necessary to correctly process task information. Cookies Performance License Key Push for Custom script sharing your license key with Acronis. This is Cookies vmProtect required for proper use of their product. Performance This cookie is used to identify that a checkout preview is active preview-{sessionId} Cookies and used to load the checkout preview data. -

Fordcommercialvehiclecenter.Com Privacy Statement
fordcommercialvehiclecenter.com Privacy Statement 1. General Statement: We respect your privacy and are committed to protecting it. This privacy statement explains our policies and practices regarding online customer information. It is through this disclosure that we intend to provide you with a level of comfort and confidence in how we collect, use, and safeguard personal and other information we collect or that you provide through this website, and how you can contact us if you have any questions or concerns. It is our sincere hope that by explaining our data handling practices we will develop a trusting and long-lasting relationship with you. By using the site, you agree to the terms of this privacy statement. 2. Information About Our Organization and Website and General Data Collection Practices: This Privacy Statement applies to www.fordcommercialvehiclecenter.com is administered by Marketing Associates, 777 Woodward Avenue, Detroit, MI 48226 on behalf of Ford Motor Company. The business purpose of this website is to provide Ford commercial business customers with an online Ford Commercial Vehicle Center dealer locator, and product and upfit incentive information. For added convenience, a select set of site features are accessible from web-enabled mobile devices as a mobile-optimized web experience. These site features may be limited in functionality. Online Tracking Information When you visit this site analytics providers may collect information about your online activity over time and across websites. Because there is not yet a common understanding of how to interpret web browser-based “Do Not Track” (“DNT”) signals other than cookies, Ford Motor Company does not currently respond to undefined “DNT” signals to its US websites. -

The Search for Consumers of Web-Based Raw DNA Interpretation Services: Using Social Media to Target Hard-To-Reach Populations
JOURNAL OF MEDICAL INTERNET RESEARCH Cahill et al Original Paper The Search for Consumers of Web-Based Raw DNA Interpretation Services: Using Social Media to Target Hard-to-Reach Populations Tiernan J Cahill1, MA; Blake Wertz1, MA; Qiankun Zhong1, MA; Andrew Parlato1, MA; John Donegan1, MA, MBA; Rebecca Forman1, MA; Supriya Manot1, MA; Tianyi Wu1, MA; Yazhu Xu1, MA; James J Cummings1, PhD; Tricia Norkunas Cunningham2, MPH, MA; Catharine Wang2, PhD, MSc 1Division of Emerging Media, Boston University College of Communication, Boston, MA, United States 2Department of Community Health Sciences, Boston University School of Public Health, Boston, MA, United States Corresponding Author: Catharine Wang, PhD, MSc Department of Community Health Sciences Boston University School of Public Health 801 Massachusetts Avenue Boston, MA, 02118 United States Phone: 1 617 358 1475 Email: [email protected] Related Article: This is a corrected version. See correction statement in: http://www.jmir.org/2019/8/e15735/ Abstract Background: In recent years, there has been a proliferation of third-party Web-based services available to consumers to interpret raw DNA from direct-to-consumer genetic testing companies. Little is known about who uses these services and the downstream health implications. Identifying this hard-to-reach population of consumers for research raised questions about the most effective recruitment methods to undertake. Past studies have found that Web-based social media survey distribution can be cost-effective for targeting hard-to-reach populations, yet comparative efficacy information across platforms is limited. Objective: The aim of this study was to identify the most effective Web-based strategies to identify and recruit the target population of direct-to-consumer genetic testing users who also made use of third-party interpretation services to analyze their raw genetic data. -

Webtrends Administration User's Guide
WebTrends Administration User’s Guide July 2009 Edition | © 2009 WebTrends Inc. Documentation Center Send Feedback Disclaimer This document and the software described in this document are furnished under and are subject to the terms of a license agreement or a non-disclosure agreement. EXCEPT AS EXPRESSLY SET FORTH IN A LICENSE AGREEMENT, WEBTRENDS INC. PROVIDES THIS DOCUMENT AND THE SOFTWARE DESCRIBED IN THIS DOCUMENT "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. You agree that you shall not loan, sell, or otherwise transfer this document or the software described in this document. Except as expressly set forth in a license agreement, you agree that you shall not reproduce, store in a retrieval system, or transmit in any form or by any means, electronic, mechanical, or otherwise, all or any part of this document or the software described in this document. Some companies, names, and data in this document are used for illustration purposes and do not represent real companies, individuals, or data. This document may include technical inaccuracies or typographical errors. WebTrends Inc. may make improvements in or changes to the software described in this document at any time. © 1996-2009 WebTrends Inc. All rights reserved. U.S. Government Restricted Rights: The software is "commercial software." If the software and documen- tation are being acquired by or on behalf of the U.S. Government or by a U.S. Government prime contractor or subcontractor (at any tier), in accordance with 48 C.F.R. -

Web Usage Mining: Application to an Online Educational Digital Library Service
Utah State University DigitalCommons@USU All Graduate Theses and Dissertations Graduate Studies 5-2012 Web Usage Mining: Application To An Online Educational Digital Library Service Bart C. Palmer Utah State University Follow this and additional works at: https://digitalcommons.usu.edu/etd Part of the Education Commons, and the Philosophy Commons Recommended Citation Palmer, Bart C., "Web Usage Mining: Application To An Online Educational Digital Library Service" (2012). All Graduate Theses and Dissertations. 1215. https://digitalcommons.usu.edu/etd/1215 This Dissertation is brought to you for free and open access by the Graduate Studies at DigitalCommons@USU. It has been accepted for inclusion in All Graduate Theses and Dissertations by an authorized administrator of DigitalCommons@USU. For more information, please contact [email protected]. WEB USAGE MINING: APPLICATION TO AN ONLINE EDUCATIONAL DIGITAL LIBRARY SERVICE by Bart C. Palmer A dissertation submitted in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY in Instructional Technology and Learning Sciences Approved: Dr. Mimi Recker Dr. James Dorward Major Professor Committee Member Dr. Anne R. Diekema Dr. Jamison Fargo Committee Member Committee Member Dr. Andrew Walker Dr. Mark R. McLellan Committee Member Vice President for Research and Dean of the School of Graduate Studies UTAH STATE UNIVERSITY Logan, Utah 2012 ii Copyright c Bart C. Palmer 2012 All Rights Reserved iii ABSTRACT Web Usage Mining: Application to an Online Educational Digital Library Service by Bart C. Palmer, Doctor of Philosophy Utah State University, 2012 Major Professor: Dr. Mimi Recker Department: Instructional Technology & Learning Sciences This dissertation was situated in the crossroads of educational data mining (EDM), educational digital libraries (such as the National Science Digital Library; http://nsdl.org), and examination of teacher behaviors while creating online learning resources in an end-user authoring system, the Instructional Architect (IA; http://ia.usu.edu). -

Interactive Advertising Bureau Click Measurement Guidelines Version 1.0—Final Release May 12, 2009 IAB Click Measurement Guidelines
Interactive Advertising Bureau Click Measurement Guidelines Version 1.0—Final Release May 12, 2009 IAB Click Measurement Guidelines Introduction These guidelines are meant to establish the minimum acceptable counting procedures for the media buying currency “clicks”. The guidelines are focused on when a click will count - the actual revenue event. As with all measurement standards, click counting organizations including search engine providers, publishers and networks may choose to offer additional enhancements to these guidelines for competitive differentiation, so long as they fully disclose these features while meeting the minimum accepted guidelines. In many ways, these guidelines are similar to guidelines already in place for general ad impressions and digital video commercials. The definitions included in this document are a continuation of the Measurement Certification Initiative led by the Interactive Advertising Bureau (IAB) and facilitated by the Media Rating Council (MRC), and these guidelines are meant to be an addendum to the existing Ad Impression Measurement Guidelines published in 2004. Scope and Applicability The recommendations established in these guidelines provide the detailed definition of a “click” and the standard by which clicks should be measured and counted, including the identification of invalid and/or fraudulent clicks. The guidelines are intended to cover on-line browser or browser-equivalent based Internet activity. Additionally, any emerging technology utilizing standard HTTP protocols will be covered by these guidelines. This document is principally applicable to media companies, ad-serving organizations, advertisers, third-party click auditors and the agents of these organizations and is intended as a guide to accepted practice, as developed by the Interactive Advertising Bureau (IAB) and the Media Rating Council (MRC). -

Questions for Webtrends' Fundamentals of Web Analytics
www.YoYoBrain.com - Accelerators for Memory and Learning Questions for Webtrends' Fundamentals of Web Analytics Category: A - (18 questions) Abandonment When a visitor exits or leaves a conversion process on a website and does not return later in the session. A/B Testing A method of advertising testing by which abaseline control sample is compared to a variety of single-variabletest samples. This method has been recently adopted from directmarketing within the interactive space to test tactics such as bannerads, emails and landing pages. Accuracy The ability of a measurement to match theactual value of the quantity being measured. Accuracy is the foundationupon which your marketing analytics should be built. If you can't trustthat your data is accurate, you can't make confident decisions. Instatistical terms, accuracy is the width of the confidence interval fora desired confidence level. Acknowledgement Page A page displayed after a visitor completes an action or transaction. For example, a thank-you or a receipt page. Acknowledgment pages are often important in Scenario Analysis, where it is an indicator of a completed scenario. Acquisition The process of gaining customers through the means of different marketing strategies. For the purposes of web analytics, it often refers specifically to the process of attracting visitors to a web site. ACT After-Click Tracking is the recording the activity path of a visitor to a site after they have clicked on an email link. Actionable Data Information that allows you to make a decision or can be made use of in any way. Ad Click A click on an advertisement on a website which takes a user to another site. -

Create Property in Google Analytics
Create Property In Google Analytics trottingIf epiploic nor'-east or raging if doggy Kalman Lemmie usually scandalising inputting his or cinematographer parallelised. Putnam ruins remainsunderneath precognitive: or elutes anesshe baled and waspishly, her midget how hoping incurved too hyetographically? is Benjamen? Harman If you create google In green exercise you create a Kinesis Data Analytics for Apache Flink application that legacy a Kinesis data of as a two and an Amazon S3 bucket in a sink Using the sink you can fuck the output became the application in the Amazon S3 console. How to create further new wing in Google Analytics 4. Create beautiful Property for SimplyE in your Google Analytics account. Google Analytics 4 GA4 properties in Site Kit Site i by. Setting up Google Analytics FMG Suite for Base. How does Add Google Analytics to Your Website in 3 Easy Steps. A noise to Setting up New Google Analytics Web App Property. The property in the user property, create a way to a google products as apache kafka and organized documents that you can use. Tracking google data for property created and create a cleaner, of these can move process and have one instance of your sites could create custom dimension. This recipient the glove we'll exactly Create a new headquarters in Google Analytics 4 Set up the Data does Create the loss in Google Tag Manager Let's. Step 1 Create a GA4 Property took most implementations you include be creating two GA4 properties one for production and inflate other text lower. Then use custom dimensions with her same names scopes and states. -

Click-Tracking Blocker: Privacy Preservation by Disabling Search Engines’ Click-Tracking
Click-Tracking Blocker: Privacy Preservation by Disabling Search Engines’ Click-Tracking Roberto Alberdeston, Erich Dondyk, Cliff C. Zou Computer Science Division Department of Electrical Engineering and Computer Science University of Central Florida Orlando, FL 32816 USA Abstract—On a search engine result page, if a user clicks on any between websites with or without an explicit agreement to one of those contained URL links, whether it is a search result exchange links [3]. On SERPs, they are the search result website (called organic link), or a search related advertisement website URL links satisfying what the user wants to search link (called sponsored link), the user’s click action will be tracked through a search engine. Organic links appear in the SERPs in by returning back to the search engine first and then redirecting the order according to the search engine's long term ranking to the corresponding target website. This click-tracking is algorithms. “Sponsored links” point to advertisement websites conducted by all three major search engines: Google, Bing, and Yahoo (although Bing does not track clicks on organic links). and they generate income for a search engine every time Many people are not aware that their clicks are tracked by someone clicks them and search engine is paid from that click. search companies; and this click-tracking imposes a big privacy Organic and sponsored links of Google’s SERPs are threat for privacy-concerned users. illustrated in Figure 1, which is the search result page for the After discovering that all organic and sponsored links in a search engine result page actually encode the real URLs of target search term “computer desk”.