Social Networks, Virtual Worlds, and the Shadow Internet : the Explosion of Virtual Identity and the Anonymous Economy
Total Page:16
File Type:pdf, Size:1020Kb

Load more
Recommended publications
-

Uila Supported Apps
Uila Supported Applications and Protocols updated Oct 2020 Application/Protocol Name Full Description 01net.com 01net website, a French high-tech news site. 050 plus is a Japanese embedded smartphone application dedicated to 050 plus audio-conferencing. 0zz0.com 0zz0 is an online solution to store, send and share files 10050.net China Railcom group web portal. This protocol plug-in classifies the http traffic to the host 10086.cn. It also 10086.cn classifies the ssl traffic to the Common Name 10086.cn. 104.com Web site dedicated to job research. 1111.com.tw Website dedicated to job research in Taiwan. 114la.com Chinese web portal operated by YLMF Computer Technology Co. Chinese cloud storing system of the 115 website. It is operated by YLMF 115.com Computer Technology Co. 118114.cn Chinese booking and reservation portal. 11st.co.kr Korean shopping website 11st. It is operated by SK Planet Co. 1337x.org Bittorrent tracker search engine 139mail 139mail is a chinese webmail powered by China Mobile. 15min.lt Lithuanian news portal Chinese web portal 163. It is operated by NetEase, a company which 163.com pioneered the development of Internet in China. 17173.com Website distributing Chinese games. 17u.com Chinese online travel booking website. 20 minutes is a free, daily newspaper available in France, Spain and 20minutes Switzerland. This plugin classifies websites. 24h.com.vn Vietnamese news portal 24ora.com Aruban news portal 24sata.hr Croatian news portal 24SevenOffice 24SevenOffice is a web-based Enterprise resource planning (ERP) systems. 24ur.com Slovenian news portal 2ch.net Japanese adult videos web site 2Shared 2shared is an online space for sharing and storage. -

Windows 7 Operating Guide
Welcome to Windows 7 1 1 You told us what you wanted. We listened. This Windows® 7 Product Guide highlights the new and improved features that will help deliver the one thing you said you wanted the most: Your PC, simplified. 3 3 Contents INTRODUCTION TO WINDOWS 7 6 DESIGNING WINDOWS 7 8 Market Trends that Inspired Windows 7 9 WINDOWS 7 EDITIONS 10 Windows 7 Starter 11 Windows 7 Home Basic 11 Windows 7 Home Premium 12 Windows 7 Professional 12 Windows 7 Enterprise / Windows 7 Ultimate 13 Windows Anytime Upgrade 14 Microsoft Desktop Optimization Pack 14 Windows 7 Editions Comparison 15 GETTING STARTED WITH WINDOWS 7 16 Upgrading a PC to Windows 7 16 WHAT’S NEW IN WINDOWS 7 20 Top Features for You 20 Top Features for IT Professionals 22 Application and Device Compatibility 23 WINDOWS 7 FOR YOU 24 WINDOWS 7 FOR YOU: SIMPLIFIES EVERYDAY TASKS 28 Simple to Navigate 28 Easier to Find Things 35 Easy to Browse the Web 38 Easy to Connect PCs and Manage Devices 41 Easy to Communicate and Share 47 WINDOWS 7 FOR YOU: WORKS THE WAY YOU WANT 50 Speed, Reliability, and Responsiveness 50 More Secure 55 Compatible with You 62 Better Troubleshooting and Problem Solving 66 WINDOWS 7 FOR YOU: MAKES NEW THINGS POSSIBLE 70 Media the Way You Want It 70 Work Anywhere 81 New Ways to Engage 84 INTRODUCTION TO WINDOWS 7 6 WINDOWS 7 FOR IT PROFESSIONALS 88 DESIGNING WINDOWS 7 8 WINDOWS 7 FOR IT PROFESSIONALS: Market Trends that Inspired Windows 7 9 MAKE PEOPLE PRODUCTIVE ANYWHERE 92 WINDOWS 7 EDITIONS 10 Remove Barriers to Information 92 Windows 7 Starter 11 Access -

Virtual Worlds? "Outlook Good" (EDUCAUSE Review) | EDUCAU
Virtual Worlds? "Outlook Good" (EDUCAUSE Review) | EDUCAU... http://connect.educause.edu/Library/EDUCAUSE+Review/VirtualWo... "Outlook Good" © 2008 AJ Kelton. The text of this article is licensed under the Creative Commons VIEW A PDF Attribution-Noncommercial-No Derivative Works 3.0 License OF THIS ARTICLE (http://creativecommons.org/licenses/by-nc-nd/3.0/). EDUCAUSE Review, vol. 43, no. 5 (September/October 2008) Virtual Worlds? “Outlook Good” AJ KELTON (“AJ BROOKS”) AJ Kelton (“AJ Brooks”) is Director of Emerging Instructional Technology in the College of Humanities and Social Sciences at Montclair State University. Comments on this article can be sent to the author at [email protected] or [email protected] and/or can be posted to the web via the link at the bottom of this page. A year ago, I picked up the Magic 8-Ball sitting on my desk and asked: “Are virtual worlds a viable teaching and learning environment?” Turning the ball over, I received my answer: “Reply hazy, try again.” Even six months ago, the outlook for virtual worlds was uncertain. Many people believed that virtual worlds would end up like the eight-track audiotape: a fond memory of something no longer used (or useful). Yet today there are hundreds of higher education institutions represented in three-dimensional (3D) virtual worlds such as Active Worlds and Second Life. Indeed, the movement toward the virtual realm as a viable teaching and learning environment seems unstoppable. The idea of synchronous interactive spaces is not new, of course. Chat rooms, MOOs, MUDs, and other multi-user online experiences have been on the periphery of education for decades. -

Figure 1 Timeline of the Launch Dates of Many Major Snss and Dates When Community Sites Re-Launched with SNS Features
Figure 1 Timeline of the launch dates of many major SNSs and dates when community sites re-launched with SNS features 212 Journal of Computer-Mediated Communication 13 (2008) 210–230 ª 2008 International Communication Association Beyond profiles, Friends, comments, and private messaging, SNSs vary greatly in their features and user base. Some have photo-sharing or video-sharing capabilities; others have built-in blogging and instant messaging technology. There are mobile- specific SNSs (e.g., Dodgeball), but some web-based SNSs also support limited mobile interactions (e.g., Facebook, MySpace, and Cyworld). Many SNSs target people from specific geographical regions or linguistic groups, although this does not always determine the site’s constituency. Orkut, for example, was launched in the United States with an English-only interface, but Portuguese-speaking Brazilians quickly became the dominant user group (Kopytoff, 2004). Some sites are designed with specific ethnic, religious, sexual orientation, political, or other identity-driven categories in mind. There are even SNSs for dogs (Dogster) and cats (Catster), although their owners must manage their profiles. While SNSs are often designed to be widely accessible, many attract homoge- neous populations initially, so it is not uncommon to find groups using sites to segregate themselves by nationality, age, educational level, or other factors that typically segment society (Hargittai, this issue), even if that was not the intention of the designers. A History of Social Network Sites The Early Years According to the definition above, the first recognizable social network site launched in 1997. SixDegrees.com allowed users to create profiles, list their Friends and, beginning in 1998, surf the Friends lists. -

The Notube Beancounter: Aggregating User Data for Television Programme Recommendation
The NoTube BeanCounter: Aggregating User Data for Television Programme Recommendation Chris van Aart1, Lora Aroyo1, Dan Brickley13, Vicky Buser2, Libby Miller2, Michele Minno3, Michele Mostarda3, Davide Palmisano3, Yves Raimond2, Guus Schreiber1, and Ronald Siebes1 1 VU University Amsterdam, the Netherlands 2 BBC - Future Media & Technology, London, UK 3 Asemantics Srl, Rome Italy Abstract. In this paper we present our current experience of aggregat- ing user data from various Social Web applications and outline several key challenges in this area. The work is based on a concrete use case: reusing activity streams to determine a viewer's interests and generating television programme recommendations from these interests. Three sys- tem components are used to realise this goal: (1) an intelligent remote control: iZapper for capturing viewer activities in a cross-context televi- sion environment; (2) a backend: BeanCounter for aggregation of viewer activities from the iZapper and from different social web applications; and (3) a recommendation engine: iTube for recommending relevant tele- vision programmes . The focus of the paper is the BeanCounter as the first step to apply Social Web data for viewer and context modelling on the Web. This is work in progress of the NoTube project4. 1 Introduction: Television Meets the Social Web Television watching has always been a social activity, but as channels and deliv- ery mechanisms multiply, the enablers of social watching - simultaneous broad- cast times for everyone and limited choice - are decreasing[7]. There is a trend towards watching television or using television-related services[1] such as Elec- tronic Programme Guides (EPGs) on PC, handheld or other networked device. -

Twitter – a Personal Perspective
Twitter – a personal perspective Catriona Fisher Customer Services Manager University of Glasgow Library Email: catriona.fisher@glasgow. ac.uk twitter: @catrionafisher I joined Twitter in March 2009, but like most people I spent the first few months wondering what on earth this strange new world was all about. As a devoted user of Multiply, then Bebo and later Facebook, I was no stranger to social net- working, but Twitter was quite obviously some- thing different. I quickly realised the following: • you need your tweets to be public • the best way to get followers is to follow other people • hashtags are a must if you want your voice to be heard amongst the millions of tweets. I started out tweeting solely about work and had intended to have two accounts, one for work and a personal account (as I do with Facebook), but I quickly realised that many professionals on Twit- ter were tweeting about their work lives and their personal lives from the same account. This takes a bit of getting used to, but is very much the norm on Twitter. I now tweet from my own account @catrionafisher and also on behalf of the University of Glasgow Library @uofglibrary, along with a group of staff from Library Services. We’ve found Twitter to be a really powerful way of reaching out to students and other library users and it is now one of our primary channels of communication when we need to share informa- tion quickly. For example, we are using it to keep students up to date with any disruption during the work to re-clad the library building. -

Online Media Business Models: Lessons from the Video Game Sector
Komorowski, M and Delaere, S. (2016). Online Media Business Models: Lessons from the Video Game Sector. Westminster Papers in Communication and Culture, 11(1), 103–123, DOI: http://dx.doi. org/10.16997/wpcc.220 RESEARCH ARTICLE Online Media Business Models: Lessons from the Video Game Sector Marlen Komorowski and Simon Delaere imec-SMIT, Vrije Universiteit, Brussels, BE Corresponding author: Marlen Komorowski ([email protected]) Today’s media industry is characterized by disruptive changes and business models have been acknowledged as a driving force for success. Current business model research manages only to grasp static descriptions while in reality media managers are struggling with the dynamics of the industry. This article aims to close this gap by investigating a new paradigm of online media business models. Based on three video game case studies of the massively multiplayer online role-playing game genre, this article explores a novel theoretical approach to explain the changes that can be made within business models. The article highlights the importance of changing processes within online media business models and emphasises that the video game sector is at the forefront of business innovation. Finally, it demonstrates that online media business model change is in a trade-off paradigm between capturing or offering potentially higher value per player vs. accessing a potentially larger player-base. Key words: Media industry; business model; process; disruption; video game sector Introduction Today’s media industry is characterized by disruptive transformations shaped by digitization. Digitization is not only generating new business opportunities but threatens traditional commercialization strategies and is proving highly unpredictable with regards to future market development. -

Famitsu PC Game Sales Ranking: April 2007
Famitsu PC Game Sales Ranking: April 2007 Data Collected: from April 1 to April 30, 2007 Game Titles Month Copies Cumulative This Last Price Average Before Title Platform Publisher Sales Date Genre Sold/Month Copies Sold Month Month (incl. tax) Price Last (Estimated) (Estimated) Final Fantasy XI: Treasures of Aht Urhgan 12 4 Win2000/XP SQUARE ENIX 04-20-06 Open ¥7,900 RPG 3,409 44,215 All-in-One Pack 2006 Medieval 2: Total War Japanese Version - 2 NEW Windows XP SEGA 04-05-07 ¥8,190 ¥7,250 Sim 3,151 3,151 Limited First Release 3 3 Lineage II: Interlude - Beginner's Kit Win2000/XP/Vista NC Japan 03-09-07 ¥3,150 ¥2,865 RPG 2,979 6,011 4 15 7 Nobunaga no Yabo Online: Haten no Sho Win2000/XP KOEI 12-13-06 ¥7,140 ¥6,205 RPG 2,502 8,831 5 7 3 Nobunaga no Yabo: Tenka Sosei Win2000/XP SOURCENEXT 10-06-06 ¥3,970 ¥3,562 Sim 1,936 13,602 6 8 The Sims 2: Seasons! Expansion Pack Win98/Me/2000/XP/Vista Electronic Arts 03-22-07 Open ¥2,864 DAT 1,618 3,636 7 4 5 SimCity 4: Deluxe Win98/Me/2000/XP Electronic Arts 09-25-03 ¥5,980 ¥4,738 Sim 1,518 62,996 8 1 Lineage II: Interlude - Master's Kit Win2000/XP/Vista NC Japan 03-09-07 ¥6,300 ¥5,675 RPG 1,317 11,737 9 10 1 Flight Simulator X WinXP/Vista Microsoft 01-26-07 ¥9,870 ¥9,187 Sim 1,296 10,802 Hoshi no Oujo: Uchu Ishiki ni Mezameta 10 5 Win98/Me/2000/XP Mirai 03-23-07 ¥4,801 ¥4,330 Adv 1,255 3,440 Yoshitsune - For All Ages 11 11 2 Sukatto Golf Pangya: Marugoto Kit Win2000/XP Gamepot 01-19-07 ¥2,940 ¥2,826 Act 1,107 14,910 QuinRos 12 6 16 Heart no Kuni no Alice: Wonderful Wonder World Win98/Me/2000/XP e -

Internet Peer-To-Peer File Sharing Policy Effective Date 8T20t2010
Title: Internet Peer-to-Peer File Sharing Policy Policy Number 2010-002 TopicalArea: Security Document Type Program Policy Pages: 3 Effective Date 8t20t2010 POC for Changes Director, Office of Computing and Information Services (OCIS) Synopsis Establishes a Dalton State College-wide policy regarding copyright infringement. Overview The popularity of Internet peer-to-peer file sharing is often the source of network resource allocation problems and copyright infringement. Purpose This policy will define Internet peer-to-peer file sharing and state the policy of Dalton State College (DSC) on this issue. Scope The scope of this policy includes all DSC computing resources. Policy Internet peer-to-peer file sharing applications are frequently used to distribute copyrighted materials such as music, motion pictures, and computer software. Such exchanges are illegal and are not permifted on Dalton State Gollege computers or network. See the standards outlined in the Appropriate Use Policy. DSG Procedures and Sanctions Failure to comply with the appropriate use of these resources threatens the atmosphere for the sharing of information, the free exchange of ideas, and the secure environment for creating and maintaining information property, and subjects one to discipline. Any user of any DSC system found using lT resources for unethical and/or inappropriate practices has violated this policy and is subject to disciplinary proceedings including suspension of DSC privileges, expulsion from school, termination of employment and/or legal action as may be appropriate. Although all users of DSC's lT resources have an expectation of privacy, their right to privacy may be superseded by DSC's requirement to protect the integrity of its lT resources, the rights of all users and the property of DSC and the State. -

An Exploratory Study of Global and Local Discourses on Social Media Regulation
Global Media Journal German Edition From the field An Exploratory Study of Global and Local Discourses on Social Media Regulation Andrej Školkay1 Abstract: This is a study of suggested approaches to social media regulation based on an explora- tory methodological approach. Its first aim is to provide an overview of the global and local debates and the main arguments and concerns, and second, to systematise this in order to construct taxon- omies. Despite its methodological limitations, the study provides new insights into this very rele- vant global and local policy debate. We found that there are trends in regulatory policymaking to- wards both innovative and radical approaches but also towards approaches of copying broadcast media regulation to the sphere of social media. In contrast, traditional self- and co-regulatory ap- proaches seem to have been, by and large, abandoned as the preferred regulatory approaches. The study discusses these regulatory approaches as presented in global and selected local, mostly Euro- pean and US discourses in three analytical groups based on the intensity of suggested regulatory intervention. Keywords: social media, regulation, hate speech, fake news, EU, USA, media policy, platforms Author information: Dr. Andrej Školkay is director of research at the School of Communication and Media, Bratislava, Slovakia. He has published widely on media and politics, especially on political communication, but also on ethics, media regulation, populism, and media law in Slovakia and abroad. His most recent book is Media Law in Slovakia (Kluwer Publishers, 2016). Dr. Školkay has been a leader of national research teams in the H2020 Projects COMPACT (CSA - 2017-2020), DEMOS (RIA - 2018-2021), FP7 Projects MEDIADEM (2010-2013) and ANTICORRP (2013-2017), as well as Media Plurality Monitor (2015). -
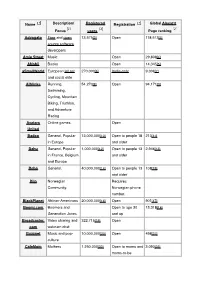
Page Ranking Advogato Free and Open So
Name Description/ Registered Registration Global Alexa[1] Focus users Page ranking Advogato Free and open 13,575[2] Open 118,513[3] source software developers Amie Street Music Open 29,808[4] ANobii Books Open 14,345[5] aSmallWorld European jet set 270,000[6] Invite-only 9,306[7] and social elite Athlinks Running, 54,270[8] Open 94,171[9] Swimming, Cycling, Mountain Biking, Triathlon, and Adventure Racing Avatars Online games. Open United Badoo General, Popular 13,000,000[10] Open to people 18 213[11] in Europe and older Bahu General, Popular 1,000,000[12] Open to people 13 2,946[13] in France, Belgium and older and Europe Bebo General. 40,000,000[14] Open to people 13 108[15] and older Biip Norwegian Requires Community. Norwegian phone number. BlackPlanet African-Americans 20,000,000[16] Open 901[17] Boomj.com Boomers and Open to age 30 15,318[18] Generation Jones and up Broadcaster. Video sharing and 322,715[19] Open com webcam chat Buzznet Music and pop- 10,000,000[20] Open 498[21] culture CafeMom Mothers 1,250,000[22] Open to moms and 3,090[23] moms-to-be Cake Investing Open Financial Care2 Green living and 9,961,947[24] Open social activism Classmates.c School, college, 50,000,000[25] Open 923[26] om work and the military Cloob General. Popular Open in Iran. College College students. requires an e-mail Tonight address with an ".edu" ending CouchSurfin Worldwide network 871,049[27] Open g for making connections between travelers and the local communities they visit. -

ROUSE-DISSERTATION-2020.Pdf (646.5Kb)
REUNITED AND IT FEELS SO GOOD? THE LIVED EXPERIENCE OF USING TECHNOLOGY TO RECONNECT WITH OLD FLAMES/LOST LOVES: A QUALITATIVE STUDY A DISSERTATION SUBMITTED IN PARTIAL FULFILLMENT OF THE REQUIREMENTS FOR THE DEGREE OF DOCTOR OF PHILOSOPHY IN THE GRADUATE SCHOOL OF THE TEXAS WOMAN’S UNIVERSITY DEPARTMENT OF HUMAN DEVELOPMENT, FAMILY STUDIES, & COUNSELING COLLEGE OF PROFESSIONAL EDUCATION BY THELMA L. ROUSE, M.B.A., M.A. DENTON, TEXAS AUGUST 2020 Copyright ©Thelma L. Rouse, 2020 all rights reserved. ACKNOWLEDGEMENTS With God all things are possible and through Christ I can do all things. I would like to thank God Almighty for surrounding me with such a wonderful support system to finish this portion of my journey. He placed a lot of awesome people and great opportunities in my life along this journey. As I continue to run this race. I look forward to so much more. To my husband Herman and my daughters, Imani and Iyana, I love you all very much and I thank you for the many times you have provided a listening ear, as I pondered various ideas over the course of my study at Texas Woman’s University or when you volunteered to be my “road dawgs” as I commuted to campus for various reasons. I like to thank my fur babies Coco and Ditto for remaining dutifully by my side to offer a belly to rub, a wet nose kiss, or a snuggle at my feet while I studied. To my dissertation committee, Dr. Brock, Dr. Hwang, and Dr. Ladd, I am grateful for your guidance and reassurance throughout this portion of my academic career.