Risky Business: the Global Threat Network and the Politics of Contraband
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Declaration Under Section 4 (4) of the Telecommunication (Broadcasting and Cable) Services Interconnection (Addressable System) Regulation, 2017 (No
Version 1.0/2019 Declaration Under Section 4 (4) of The Telecommunication (Broadcasting and Cable) Services Interconnection (Addressable System) Regulation, 2017 (No. 1 of 2017) 4(4)a: Target Market Distribution Network Location States/Parts of State covered as "Coverage Area" Bangalore Karnataka Bhopal Madhya Pradesh Delhi Delhi; Haryana; Rajasthan and Uttar Pradesh Hyderabad Telangana Kolkata Odisha; West Bengal; Sikkim Mumbai Maharashtra 4(4)b: Total Channel carrying capacity Distribution Network Location Capacity in SD Terms Bangalore 506 Bhopal 358 Delhi 384 Hyderabad 456 Kolkata 472 Mumbai 447 Kindly Note: 1. Local Channels considered as 1 SD; 2. Consideration in SD Terms is clarified as 1 SD = 1 SD; 1 HD = 2 SD; 3. Number of channels will vary within the area serviced by a distribution network location depending upon available Bandwidth capacity. 4(4)c: List of channels available on network List attached below in Annexure I 4(4)d: Number of channels which signals of television channels have been requested by the distributor from broadcasters and the interconnection agreements signed Nil Page 1 of 37 Version 1.0/2019 4(4)e: Spare channels capacity available on the network for the purpose of carrying signals of television channels Distribution Network Location Spare Channel Capacity in SD Terms Bangalore Nil Bhopal Nil Delhi Nil Hyderabad Nil Kolkata Nil Mumbai Nil 4(4)f: List of channels, in chronological order, for which requests have been received from broadcasters for distribution of their channels, the interconnection agreements -

T H E G L O B a L I S S
FALL 2017 MAGAZINE the GLOBAL issue ON THE COVER Her Doorway. Photo by Emma Wellman ’19 While visiting a kasbah in Marrakech to study intricate tiles and painted designs on wood during the French Language and Culture in Morocco Interim, Wellman photographed her classmate Anna Lutz ’18 in the doorway. The door and Anna’s hat and scarf, purchased in the Fez medina, exemplify the bright colors that weave their way through every [Moroccan] city,” says Wellman. “Morocco is diverse, unified, colorful, and beautiful.” ST. OLAF MAGAZINE FALL 2017 · VOLUME 64 · NO. 3 EDITOR Carole Leigh Engblom ART DIRECTOR Don Bratland ’87 26 COPY EDITOR Laura Hamilton Waxman CONTRIBUTING WRITERS Gaju Aline ’19, Renata Erickson ’19, Sarah Gruidl ’17, Joel Hoekstra ’92, Marla Hill Holt ’88, Erin Peterson, Jeff Sauve CONTRIBUTING PHOTOGRAPHERS Anne Christianson ’07, Mac Gimse ’58, Tom Roster, Anne Ryan/Polaris, Fernando Sevilla Readers may send name/address changes and corrections to: Advancement Services, St. Olaf College, 1520 St. Olaf Ave., Northfield, MN 55057; email [email protected] or call 507-786-3330 Class Notes and Milestones Submission Deadlines: Spring issue: Feb. 1; Fall issue: June 1; Winter issue: Oct. 1. Contact the Office of Alumni and Parent Relations, 507-786-3028 or 888-865-6537; email [email protected]; update online at stolaf.edu/alumni/share-your-news St. Olaf Magazine is published three times annually (Winter, Spring, Fall) by St. Olaf College, with editorial offices at the Office of Marketing and Communications; email: [email protected] 34 stolaf.edu 6 facebook.com/stolafcollege twitter.com/StOlaf instagram.com/stolafcollege youtube.com/user/stolaf · CHENNAI, INDIA · ALEXANDRA MADSEN ’18 MADSEN ALEXANDRA · INDIA CHENNAI, · THE SARI MAKER SARI THE MAGAZINE FALL 2017 2 Letter to Oles From President David R. -

APNA CHOICE HINDI 225 225 ### (Pay Channels + Delhi FTA)
A DELHI / HARYANA /UTTAR PRADESH HATHWAY RECOMMENDED PACK DRP ₹ a (Excluding Tax) APNA CHOICE HINDI 225 225 ### (Pay Channels + Delhi FTA) SD 53 PAY CHANNELS HD 0 TOTAL: 53 LANGUAGE ~ GENRE CHANNEL NAME(S) CHANNEL TYPE ASSAMESE NEWS NEWS18 ASSAM/NE SD ENGLISH MUSIC VH1 SD ENGLISH NEWS CNBC TV18 SD CNN NEWS18 SD ET NOW SD INDIA TODAY SD MIRROR NOW SD NDTV 24X7 SD NDTV PROFIT SD TIMES NOW SD HINDI GEC COLORS SD COLORS RISHTEY SD SONY SD SONY PAL SD SONY SAB SD STAR BHARAT SD STAR PLUS SD STAR UTSAV SD ZOOM SD HINDI MOVIE COLORS CINEPLEX SD MOVIES OK SD SONY MAX SD SONY MAX 2 SD SONY WAH SD STAR GOLD SD STAR UTSAV MOVIES SD HINDI MUSIC MTV SD MTV BEATS SD SONY MIX SD HINDI NEWS AAJ TAK SD CNBC AWAAZ SD NDTV INDIA SD NEWS18 BR/JH SD NEWS18 INDIA SD NEWS18 MPCG SD NEWS18 RAJASTHAN SD NEWS18 UP/UK SD TEZ SD INFOTAINMENT FYI TV18 SD Page 1 of 186 HISTORY TV18 SD NAT GEO WILD SD NATIONAL GEOGRAPHIC SD NDTV GOODTIMES SD KIDS NICK SD NICK JR SD SONIC SD SONY YAY SD PUNJABI NEWS NEWS18 PB/HR/HP SD SPORTS STAR SPORTS 1 HINDI SD STAR SPORTS 2 SD STAR SPORTS 3 SD STAR SPORTS FIRST SD URDU NEWS NEWS18 URDU SD HATHWAY RECOMMENDED PACK DRP ₹ a (Excluding Tax) APNA CHOICE HINDI 275 275 ### (Pay Channels + Delhi FTA) SD 85 PAY CHANNELS HD 0 TOTAL: 85 LANGUAGE ~ GENRE CHANNEL NAME(S) CHANNEL TYPE ASSAMESE NEWS NEWS18 ASSAM/NE SD BHOJPURI GEC BIG GANGA SD ENGLISH MUSIC VH1 SD ENGLISH NEWS BBC WORLD NEWS SD CNBC TV18 SD CNN NEWS18 SD ET NOW SD INDIA TODAY SD MIRROR NOW SD NDTV 24X7 SD NDTV PROFIT SD TIMES NOW SD GUJARATI NEWS ZEE 24 KALAK SD HINDI GEC &TV -

Hathway Recommended Pack
HATHWAY RECOMMENDED PACK KARNATAKA Prices are excluding taxes INFINITY HD MRP : ₹ 668 (142 PAY CHANNELS + KARNATAKA FTA) Total Pay Channels 78 SD + 64 HD (Excluding tax) LANG - GENRE CHANNEL_NAME SD/HD Bengali - Gec SONY AATH SD English - Gec STAR WORLD HD HD English - Gec STAR WORLD PREMIERE HD HD English - Gec ZEE CAFE HD HD English - Infotainment TLC HD HD English - Kids BABY TV HD HD English - Kids NICK JR SD English - Movie &FLIX HD HD English - Movie &PRIVE HD HD English - Movie HBO HD HD English - Movie MN+ HD HD English - Movie MNX HD HD English - Movie MOVIES NOW HD HD English - Movie ROMEDY NOW HD HD English - Movie SONY PIX HD HD English - Movie STAR MOVIES HD HD English - Movie STAR MOVIES SELECT HD HD English - Movie WB SD English - Music VH1 HD HD English - News BBC WORLD NEWS SD English - News CNBC TV18 SD English - News CNN INTERNATIONAL SD English - News CNN NEWS18 SD English - News ET NOW SD English - News INDIA TODAY SD English - News MIRROR NOW SD English - News NDTV 24X7 SD English - News NDTV PROFIT SD English - News TIMES NOW SD English - News TIMES NOW WORLD HD HD English - Sports EUROSPORT HD HD Hindi - Gec &TV HD HD Hindi - Gec BIG MAGIC SD Page 1 of 98 Hindi - Gec COLORS HD HD Hindi - Gec COLORS RISHTEY SD Hindi - Gec INVESTIGATION DISCOVERY HD HD Hindi - Gec SONY HD HD Hindi - Gec SONY PAL SD Hindi - Gec SONY SAB HD HD Hindi - Gec ZEE ANMOL SD Hindi - Gec ZEE TV HD HD Hindi - Infotainment HISTORY TV18 HD HD Hindi - Kids CARTOON NETWORK SD Hindi - Kids NICK SD Hindi - Kids NICK HD+ HD Hindi - Kids POGO SD Hindi -

CURRICULUM VITAE KRISHNASWAMY JAYACHANDRAN Earth and Environment Department Florida International University
CURRICULUM VITAE KRISHNASWAMY JAYACHANDRAN Earth and Environment Department Florida International University Professor Phone: (305) 348-6553 PSM-EPM Program Director Fax: (305) 348-6137 Co-Director, Agroecology Program E-mail:[email protected] AHC5 383 Modesto Maidique Campus http://casegroup.fiu.edu Miami, FL 33199 http://agroecology.fiu.edu EDUCATION: Ph.D. Kansas State University, Manhattan, KS, Plant Pathology (Soil Microbiology), April 1991. M.Sc. Tamil Nadu Agricultural University, Coimbatore, India, Agricultural Microbiology, December 1983. B.Sc. Tamil Nadu Agricultural University, Coimbatore, India, Agriculture Sciences, May 1981. ACADEMIC EXPERIENCE: Dept. of Earth and Environment Professor Aug 2010-present Florida International University, Miami (Soil Microbiology) Dept. of Earth and Environment PSM-EPM Program Jan 2014-present Florida International University, Miami STEM Transformation Institute Founding Fellow Jan 2015-present Florida International University, Miami Dept. of Earth and Environment Co-Director, Agroecology Aug 2005-present Florida International University, Miami (Founding) Dept. of Earth and Environment Graduate Program Director Aug 2008-2015 Florida International University, Miami Dept. of Earth and Environment Associate Professor Aug 2002-2010 Florida International University, Miami (Soil Microbiology) The Honors College Fellow Aug 2003-2009 Florida International University, Miami The Honors College Founding Director-SRAI Aug 2003-2005 1 Florida International University, Miami Dept. of Environmental Studies Graduate Program Director Aug 2003-Jan 04 Florida International University, Miami (Interim) Dept. of Environmental Studies Assistant Professor May 1996-2002 Florida International University, Miami National Laboratory for Agriculture & Assistant Scientist May 1991-1996 Environment, USDA-ARS, Ames, IA Dept. of Plant Pathology Grad Res Assistant Aug 1887-1991 Kansas State University, Manhattan, KS International Crops Research Institute for Research Associate Jan 1984–1987 The Semi-Arid Tropics (ICRISAT) Hyderabad, India Dept. -

Proceedings Resilience Dividend: Towards Sustainable and Inclusive Societies
Proceedings Resilience Dividend: Towards Sustainable and Inclusive Societies Convened and organized by Hosted by Proceedings #GP2019Geneva Table of contents Acknowledgements 4 01 2019 Global Platform for Disaster Risk Reduction 5 The UN Office for Disaster Risk Reduction 5 Foreword 6 Co-Chairs’ Summary 7 Agenda 11 Greening / Accessibility 12 Numbers 13 Official Events 14 02 Official Opening Ceremony 15 Official Statements 18 Ministerial Roundtables 21 High-Level Dialogues 25 Special Session 33 Working Sessions 34 Closing Ceremony 58 03 Side Events 59 Other Events 77 04 Award Ceremonies 85 Preparatory Meetings 87 Ignite Stage 89 Innovation Platform 92 Learning Labs 96 05 List of Participants 97 2 Proceedings Introduction #GP2019Geneva INTRODUCTION 01 © 2019 UNITED NATIONS For additional information, please contact: United Nations Office for Disaster Risk Reduction 9-11 Rue de Varembé, 1202 Geneva, Switzerland, Email : [email protected] Copyright pertaining to all photos and images in this publication are reserved by the UN Office for Disaster Risk Reduction. Unauthorized copying, replication, selling and any other secondary use of the pictures are strictly prohibited. For permission to use, distribute or reprint any part of this publication, please contact the UN Office for Disaster Risk Reduction at [email protected]. 3 Proceedings Introduction #GP2019Geneva Acknowledgements The United Nations Office for Disaster Risk Reduction (UNDRR) expresses its deep appreciation and gratitude to Switzerland for having hosted and co-chaired the 2019 Global Platform for Disaster Risk Reduction (GP2019) and for its staunch political, logistical and financial support which contributed to a successful and impactful event. Furthermore, deep appreciation is expressed to the following governments who supported the GP2019 with either earmarked or unearmarked contributions: Australia, Cyprus, the Czech Republic, Finland, France, Germany, Ireland, Japan, Luxembourg, New Zealand, Norway, Sweden and as well as the European Commission. -
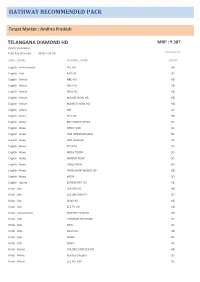
Hathway Recommended Pack
HATHWAY RECOMMENDED PACK Target Market : Andhra Pradesh TELANGANA DIAMOND HD MRP : ₹ 387 (74 PAY CHANNELS) Total Pay Channels 39 SD + 35 HD (Excluding tax) LANG - GENRE CHANNEL_NAME SD/HD English - Infotainment TLC HD HD English - Kids NICK JR SD English - Movie HBO HD HD English - Movie MN+ HD HD English - Movie MNX HD HD English - Movie MOVIES NOW HD HD English - Movie ROMEDY NOW HD HD English - Movie WB SD English - Music VH1 HD HD English - News BBC WORLD NEWS SD English - News CNBC TV18 SD English - News CNN INTERNATIONAL SD English - News CNN NEWS18 SD English - News ET NOW SD English - News INDIA TODAY SD English - News MIRROR NOW SD English - News TIMES NOW SD English - News TIMES NOW WORLD HD HD English - News WION SD English - Sports EUROSPORT HD HD Hindi - Gec COLORS HD HD Hindi - Gec COLORS RISHTEY SD Hindi - Gec SONY HD HD Hindi - Gec ZEE TV HD HD Hindi - Infotainment HISTORY TV18 HD HD Hindi - Kids CARTOON NETWORK SD Hindi - Kids NICK SD Hindi - Kids NICK HD+ HD Hindi - Kids POGO SD Hindi - Kids SONIC SD Hindi - Movie COLORS CINEPLEX HD HD Hindi - Movie Rishtey Cineplex SD Hindi - Movie ZEE ACTION SD Hindi - Music MTV BEATS HD HD Hindi - Music MTV HD+ HD Hindi - Music ZEE ETC SD Hindi - Music ZOOM SD Hindi - News AAJ TAK HD HD Hindi - News CNBC AWAAZ SD Hindi - News NEWS18 BR/JH SD Hindi - News NEWS18 INDIA SD Hindi - News NEWS18 MPCG SD Hindi - News NEWS18 RAJASTHAN SD Hindi - News NEWS18 UP/UK SD Hindi - News TEZ SD Hindi - News ZEE HINDUSTAN SD Hindi - News ZEE NEWS SD Multi Audio - Infotainment ANIMAL PLANET HD WORLD -

Hathway Digital Private Limited
HATHWAY DIGITAL PRIVATE LIMITED BROADCASTER BOUQUET CHANNEL BOUQUET NAME DRP* CHANNEL NAMES NAME TYPE COUNT SUN HD KANNADA BASIC HD 50 6 CHINTU TV UDAYA COMEDY UDAYA MOVIES UDAYA MUSIC UDAYA NEWS UDAYA TV HD SUN HD KANNADA PRIME HD 70 9 CHINTU TV GEMINI TV HD KTV HD SUN TV HD UDAYA COMEDY UDAYA MOVIES UDAYA MUSIC UDAYA NEWS UDAYA TV HD SUN HD KANNADA SUPER HD 80 11 CHINTU TV GEMINI MOVIES HD GEMINI TV HD KTV HD SUN MUSIC HD SUN TV HD UDAYA COMEDY UDAYA MOVIES UDAYA MUSIC UDAYA NEWS UDAYA TV HD SUN HD KERALA BASIC HD 30 5 KOCHU TV SURYA COMEDY SURYA MOVIES *Price is excluding applicable taxes. Channel availability will be subject to Headend capacity and technical feasibility in respective locations. Subscriber is liable to pay other charges like STB rental, STB Maintenance, etc based on availed scheme. For any further information please call contact center or your Local Cable Operator HATHWAY DIGITAL PRIVATE LIMITED BROADCASTER BOUQUET CHANNEL BOUQUET NAME DRP* CHANNEL NAMES NAME TYPE COUNT SURYA MUSIC SURYA TV HD SUN HD KERALA PRIME HD 70 8 KOCHU TV KTV HD SUN TV HD SURYA COMEDY SURYA MOVIES SURYA MUSIC SURYA TV HD UDAYA TV HD SUN HD KERALA SUPER HD 80 11 ADITHYA TV KOCHU TV KTV HD SUN MUSIC SUN TV HD SURYA COMEDY SURYA MOVIES SURYA MUSIC SURYA TV HD UDAYA MOVIES UDAYA TV HD SUN HD SUN ULTIMATE PACK HD 110 25 ADITHYA TV CHINTU TV CHUTTI TV GEMINI COMEDY GEMINI LIFE GEMINI MOVIES HD GEMINI MUSIC HD GEMINI NEWS *Price is excluding applicable taxes. -

Crocodile Specialist Group Newsletter
CROCODILE SPECIALIST GROUP _____________________________________________________________________________________ NEWSLETTER VOLUME 21 No. 3 ! JULY 2002 – SEPTEMBER 2002 IUCN - World Conservation Union ! Species Survival Commission The CSG NEWSLETTER is produced and distributed by the Crocodile Specialist Group of the Species Survival CROCODILE Commission, IUCN – The World Conservation Union. CSG NEWSLETTER provides information on the conservation, status, news and current events concerning crocodilians, and on the activities of the SPECIALIST CSG. The NEWSLETTER is distributed to CSG members and, upon request, to other interested individuals and organizations. All subscribers are asked to contribute news and other materials. A GROUP voluntary contribution (suggested $40.00 US per year) is requested from subscribers to defray expenses of ____________________________ producing the NEWSLETTER. All communications should be addressed to: Dr. J. P. Ross, Executive Officer CSG, Florida Museum of Natural History, Gainesville, FL 32611, USA. Fax 1 352 392 9367, E- NEWSLETTER mail [email protected] ____________________________ VOLUME 21 Number 3 PATRONS JULY 2002 – SEPTEMBER 2002 We gratefully express our thanks to the following patrons who have donated to the CSG conservation program during 2002. IUCN−The World Conservation Union Species Survival Commission Big Bull Crocs! ($25,000 or more annually or in aggregate donations) ____________________________ Japan, JLIA − Japan Leather & Leather Goods Industries Association, CITES Promotion Committee & All Japan Reptile Skin and Prof. Harry Messel, Chairman Leather Association, Tokyo, Japan. IUCN Crocodile Specialist Group Mainland Holdings Ltd., Lae, Papua New School of Physics Guinea. University of Sydney Heng Long Leather Co. Pte. Ltd., Singapore. Australia Reptilartenshutz, Offenbach am Main, Germany. D. & J. Lewkowicz, France Croco et Cie-Inter Reptile, Paris, France. -

00001. Rugby Pass Live 1 00002. Rugby Pass Live 2 00003
00001. RUGBY PASS LIVE 1 00002. RUGBY PASS LIVE 2 00003. RUGBY PASS LIVE 3 00004. RUGBY PASS LIVE 4 00005. RUGBY PASS LIVE 5 00006. RUGBY PASS LIVE 6 00007. RUGBY PASS LIVE 7 00008. RUGBY PASS LIVE 8 00009. RUGBY PASS LIVE 9 00010. RUGBY PASS LIVE 10 00011. NFL GAMEPASS 1 00012. NFL GAMEPASS 2 00013. NFL GAMEPASS 3 00014. NFL GAMEPASS 4 00015. NFL GAMEPASS 5 00016. NFL GAMEPASS 6 00017. NFL GAMEPASS 7 00018. NFL GAMEPASS 8 00019. NFL GAMEPASS 9 00020. NFL GAMEPASS 10 00021. NFL GAMEPASS 11 00022. NFL GAMEPASS 12 00023. NFL GAMEPASS 13 00024. NFL GAMEPASS 14 00025. NFL GAMEPASS 15 00026. NFL GAMEPASS 16 00027. 24 KITCHEN (PT) 00028. AFRO MUSIC (PT) 00029. AMC HD (PT) 00030. AXN HD (PT) 00031. AXN WHITE HD (PT) 00032. BBC ENTERTAINMENT (PT) 00033. BBC WORLD NEWS (PT) 00034. BLOOMBERG (PT) 00035. BTV 1 FHD (PT) 00036. BTV 1 HD (PT) 00037. CACA E PESCA (PT) 00038. CBS REALITY (PT) 00039. CINEMUNDO (PT) 00040. CM TV FHD (PT) 00041. DISCOVERY CHANNEL (PT) 00042. DISNEY JUNIOR (PT) 00043. E! ENTERTAINMENT(PT) 00044. EURONEWS (PT) 00045. EUROSPORT 1 (PT) 00046. EUROSPORT 2 (PT) 00047. FOX (PT) 00048. FOX COMEDY (PT) 00049. FOX CRIME (PT) 00050. FOX MOVIES (PT) 00051. GLOBO PORTUGAL (PT) 00052. GLOBO PREMIUM (PT) 00053. HISTORIA (PT) 00054. HOLLYWOOD (PT) 00055. MCM POP (PT) 00056. NATGEO WILD (PT) 00057. NATIONAL GEOGRAPHIC HD (PT) 00058. NICKJR (PT) 00059. ODISSEIA (PT) 00060. PFC (PT) 00061. PORTO CANAL (PT) 00062. PT-TPAINTERNACIONAL (PT) 00063. RECORD NEWS (PT) 00064. -

International Premium Israel
INTERNATIONAL PREMIUM ISRAEL AFGHANISTAN ITALY AFRICA KOREA KURDISTAN ALBANIA MACEDONIA ARABIC MALAYSIA ARGENTINA MALTA AUSTRALIA NETHERLANDS AUSTRIA NEW ZEALAND BELGIUM NORWAY BRAZIL PAKISTAN BULGARIA PHILIPPINES CANADA POLAND CARRIBEAN PORTUGAL CHINA ROMANIA CZECH REPUBLIC RUSSIA SPAIN DENMARK SWEDEN FINLAND SWITZERLAND FRANCE THAILAND GERMANY TURKEY GREECE UNITED KINGDOM HUNGARY UNITED STATES INDONESIA VIETNAM AFGHANISTAN AFG: Arezo AFG: ARIANA INTERNATIONAL AFG: Aryana TV AFG: ATN AFGHAN AFG: ATN EUROPE AFG: ATN USA AFG: Jawan TV AFG: KHURSHID TV AFG: LEMAR AFG: NEGAAH AFG: PASHTO TV AFG: SHAMSHAD AFG: SROOD AFG: TAMADON TV AFG: Trace Naija HD AFG: RTA Afghanistan AF: IL TV AF: Mouridiyah tv (Senegal) AFRICA AF: EBC ETHIOPIA AF: Music TV Singhal AF: Vox Africa AF: AITInt'l AF: Ndiouroul TV (Senegal) AF: RTS 1 AFRICA AF: SOMALI CABLE AF: Neem TV Congo AF: ORTM AFRICA AF: Gabon TV AF: Nigezie TV (Nigeria) AF: AFRICA 24 AF: CRTV TV AF: NollyWood French AF: Africable AF: Equinoxe AF: Nollywood Movies AF: Africahwood TV AF: Maisha TV AF: Gtv Sports Plus (Ghana) AF: Erbu Africa AF: RTNC AF: Novelas TV AF: Africa Today TV AF: TVT International (Togo) AF: NTAi (Nigeria) AF: Africa TV AF: AIT International (Nigeria) AF: NTV (Uganda) AF: Africa TV 2 AF: Burkina Info (Burkina Faso) AF: Ole Tfm AF: Africa TV 3 AF: CANAL 225 (BENIN) AF: Oromia Sudan AF: ANN 7 South Africa AF: Channels 24 TV (Nigeria) AF: Qacaid TV AF: IBN TV Africa AF: ENN AF: RTN TV (Gabon) AF: Trace Africa AF: Espace TV (Guinee) AF: Rwanda tv AF: Rave TV (Nigeria) AF: Lamp Fall -

Hathway Recommended Packs
DELHI / HARYANA /UTTAR PRADESH HATHWAY RECOMMENDED PACK DRP ₹ (Excluding Tax) (Pay Channels + DL/HR/UP FTA) APNA CHOICE HINDI 225 225 SD 53 PAY CHANNELS HD 0 TOTAL: 53 LANGUAGE ~ GENRE CHANNEL NAME(S) CHANNEL TYPE ASSAMESE NEWS NEWS18 ASSAM/NE SD ENGLISH MUSIC VH1 SD ENGLISH NEWS CNBC TV18 SD CNN NEWS18 SD ET NOW SD INDIA TODAY SD MIRROR NOW SD NDTV 24X7 SD NDTV PROFIT SD TIMES NOW SD HINDI GEC COLORS SD COLORS RISHTEY SD SONY SD SONY PAL SD SONY SAB SD STAR BHARAT SD STAR PLUS SD STAR UTSAV SD ZOOM SD HINDI MOVIE COLORS CINEPLEX SD MOVIES OK SD SONY MAX SD SONY MAX 2 SD SONY WAH SD STAR GOLD SD STAR UTSAV MOVIES SD HINDI MUSIC MTV SD MTV BEATS SD SONY MIX SD HINDI NEWS AAJ TAK SD CNBC AWAAZ SD NDTV INDIA SD NEWS18 BR/JH SD NEWS18 INDIA SD NEWS18 MPCG SD NEWS18 RAJASTHAN SD NEWS18 UP/UK SD TEZ SD INFOTAINMENT FYI TV18 SD HISTORY TV18 SD NAT GEO WILD SD Page 1 of 98 NATIONAL GEOGRAPHIC SD NDTV GOODTIMES SD KIDS NICK SD NICK JR SD SONIC SD SONY YAY SD PUNJABI NEWS NEWS18 PB/HR/HP SD SPORTS STAR SPORTS 1 HINDI SD STAR SPORTS 2 SD STAR SPORTS 3 SD STAR SPORTS FIRST SD URDU NEWS NEWS18 URDU SD HATHWAY RECOMMENDED PACK DRP ₹ (Excluding Tax) (Pay Channels + DL/HR/UP FTA) APNA CHOICE HINDI 275 275 SD 85 PAY CHANNELS HD 0 TOTAL: 85 LANGUAGE ~ GENRE CHANNEL NAME(S) CHANNEL TYPE ASSAMESE NEWS NEWS18 ASSAM/NE SD BHOJPURI GEC BIG GANGA SD ENGLISH MUSIC VH1 SD ENGLISH NEWS BBC WORLD NEWS SD CNBC TV18 SD CNN NEWS18 SD ET NOW SD INDIA TODAY SD MIRROR NOW SD NDTV 24X7 SD NDTV PROFIT SD TIMES NOW SD GUJARATI NEWS ZEE 24 KALAK SD HINDI GEC &TV SD BIG MAGIC