Espionage 2.0: Protecting Human Intelligence Sources in the Digital Age
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Pulitzer Prizes for International Reporting in the Third Phase of Their Development, 1963-1977
INTRODUCTION THE PULITZER PRIZES FOR INTERNATIONAL REPORTING IN THE THIRD PHASE OF THEIR DEVELOPMENT, 1963-1977 Heinz-Dietrich Fischer The rivalry between the U.S.A. and the U.S.S.R. having shifted, in part, to predomi- nance in the fields of space-travel and satellites in the upcoming space age, thus opening a new dimension in the Cold War,1 there were still existing other controversial issues in policy and journalism. "While the colorful space competition held the forefront of public atten- tion," Hohenberg remarks, "the trained diplomatic correspondents of the major newspa- pers and wire services in the West carried on almost alone the difficult and unpopular East- West negotiations to achieve atomic control and regulation and reduction of armaments. The public seemed to want to ignore the hard fact that rockets capable of boosting people into orbit for prolonged periods could also deliver atomic warheads to any part of the earth. It continued, therefore, to be the task of the responsible press to assign competent and highly trained correspondents to this forbidding subject. They did not have the glamor of TV or the excitement of a space shot to focus public attention on their work. Theirs was the responsibility of obliging editors to publish material that was complicated and not at all easy for an indifferent public to grasp. It had to be done by abandoning the familiar cliches of journalism in favor of the care and the art of the superior historian .. On such an assignment, no correspondent was a 'foreign' correspondent. The term was outdated. -

Fellows and Faculty Directory
Fellows and Faculty Directory Danielle Abada Associate Program and Year: Law 2015 Sullivan & Cromwell Email: [email protected] Current City: New York, NY Rachel Abdoler PhD Student Program and Year: Seminary 2015 University of Chicago Divinity School Email: [email protected] Current City: Chicago, IL Daniel Abel Senior Manager Strategy and Operations Program and Year: Business 2015 HERE Email: [email protected] Current City: Berlin, Germany Ben Abelson Urologist Program and Year: Medical 2010 Email: [email protected] Current City: Shaker Heights, OH Kamal Abu-Shamsieh Working on PhD Program and Year: Seminary 2010 Graduate Theological Union Email: [email protected] Current City: Fresno, CA Farah Al-khersan Immigration Attorney Program and Year: Law 2014 Law Office of Michael Carlin PLLC Email: [email protected] Current City: Detroit, MI Hasenin Al-khersan Resident Program and Year: Medical 2014 MacNeal Hospital Email: [email protected] Current City: Chicago, IL Agostina Allori Professor of Human Rights Program and Year: Law 2016 University of Palermo Email: [email protected] Current City: Buenos Aires, Argentina James Allred Associate Program and Year: Law 2011 Hogan Lovells Email: [email protected] Current City: Takoma Park, MD 1 Alex Alper Petrobras and Vale Correspondant Program and Year: Journalism 2011 Reuters Email: [email protected] Current City: Rio de Janeiro, Brazil Philipe Andal Freelance Journalist Program and Year: Seminary 2017 Email: [email protected] Current City: New Haven, CT Lindsey -

By Any Other Name: How, When, and Why the US Government Has Made
By Any Other Name How, When, and Why the US Government Has Made Genocide Determinations By Todd F. Buchwald Adam Keith CONTENTS List of Acronyms ................................................................................. ix Introduction ........................................................................................... 1 Section 1 - Overview of US Practice and Process in Determining Whether Genocide Has Occurred ....................................................... 3 When Have Such Decisions Been Made? .................................. 3 The Nature of the Process ........................................................... 3 Cold War and Historical Cases .................................................... 5 Bosnia, Rwanda, and the 1990s ................................................... 7 Darfur and Thereafter .................................................................... 8 Section 2 - What Does the Word “Genocide” Actually Mean? ....... 10 Public Perceptions of the Word “Genocide” ........................... 10 A Legal Definition of the Word “Genocide” ............................. 10 Complications Presented by the Definition ...............................11 How Clear Must the Evidence Be in Order to Conclude that Genocide has Occurred? ................................................... 14 Section 3 - The Power and Importance of the Word “Genocide” .. 15 Genocide’s Unique Status .......................................................... 15 A Different Perspective .............................................................. -

On the Cumberland Plateau: Thomas Hughes and the East Tennessee Rugby
University of Tennessee, Knoxville TRACE: Tennessee Research and Creative Exchange Doctoral Dissertations Graduate School 5-2014 Planting a "Community of Gentlemen and Ladies" on the Cumberland Plateau: Thomas Hughes and the East Tennessee Rugby Brenda Louise Alexander University of Tennessee - Knoxville, [email protected] Follow this and additional works at: https://trace.tennessee.edu/utk_graddiss Part of the History Commons Recommended Citation Alexander, Brenda Louise, "Planting a "Community of Gentlemen and Ladies" on the Cumberland Plateau: Thomas Hughes and the East Tennessee Rugby. " PhD diss., University of Tennessee, 2014. https://trace.tennessee.edu/utk_graddiss/2674 This Dissertation is brought to you for free and open access by the Graduate School at TRACE: Tennessee Research and Creative Exchange. It has been accepted for inclusion in Doctoral Dissertations by an authorized administrator of TRACE: Tennessee Research and Creative Exchange. For more information, please contact [email protected]. To the Graduate Council: I am submitting herewith a dissertation written by Brenda Louise Alexander entitled "Planting a "Community of Gentlemen and Ladies" on the Cumberland Plateau: Thomas Hughes and the East Tennessee Rugby." I have examined the final electronic copy of this dissertation for form and content and recommend that it be accepted in partial fulfillment of the equirr ements for the degree of Doctor of Philosophy, with a major in History. John Bohstedt, Major Professor We have read this dissertation and recommend its acceptance: -

For Their Eyes Only
FOR THEIR EYES ONLY How Presidential Appointees Treat Public Documents as Personal Property Steve Weinberg THE CENTER FOR PUBLIC INTEGRITY FOR THEIR EYES ONLY How Presidential Appointees Treat Public Documents as Personal Property Steve Weinberg THE CENTER FOR PUBLIC INTEGRITY The Center for Public Integrity is an independent, nonprofit organization that examines public service and ethics-related issues. The Center's REPORTS combine the substantive study of government with in-depth journalism. The Center is funded by foundations, corporations, labor unions, individuals, and revenue from news organizations. This Center study and the views expressed herein are those of the author. What is written here does not necessarily reflect the views of individual members of The Center for Public Integrity's Board of Directors or Advisory Board. Copyright (c) 1992 THE CENTER FOR PUBLIC INTEGRITY. All rights reserved. No part of this publication may be reproduced or used in any form or by any means, electronic or mechanical, including photocopying, recording, or by any information storage or retrieval system, without the written permission of The Center for Public Integrity. ISBN 0-962-90127-X "Liberty cannot be preserved without a general knowledge among the people, who have a right and a desire to know. But, besides this, they have a right, an indisputable, unalienable, indefeasible, divine right to that most dreaded and envied kind of knowledge - I mean of the characters and conduct of their rulers." John Adams (1735-1826), second president of the United States Steve Weinberg is a freelance investigative journalist in Columbia, Mo. From 1983-1990, he served as executive director of Investigative Reporters & Editors, an international organization with about 3000 members. -
The View | from the University of Vermont
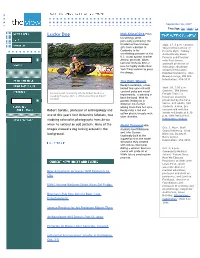
September 26, 2007 Text Size: Sm | Med | Lg Lucky Dog Nick Kristof Q+A From his writings about personally purchasing the freedom of two teenage Sept. 27, 5 p.m. Lecture: girls from a brothel in "Beyond the Culture of Cambodia to his Poverty Myth: Talking unrelenting pressure on the Authentically about U.S. to act against another Poverty and Classism" African genocide, Aiken with Paul Gorski, Lecturer Nicholas Kristof assistant professor of uses his highly visible New education, Graduate York Times column to press School of Education, for change. Hamline University. John Dewey Lounge, Old Mill. Information: 656-9511. The Right Wheels Boedy Leombruno, a tow- haired four-year-old with Sept. 28, 7:30 p.m. cerebral palsy and visual Concert: "Old School Current event: University Scholar Robert Gordon is impairments, is grinning to Freight Train," a speaking Tuesday, Oct. 2. (Photo courtesy of Robert beat the band. With his bluegrass ensemble Gordon) presented by the Lane parents looking on in disbelief, his mother Series. $25 adults, $20 wiping tears from her eyes, students. A free, pre- Robert Gordon, professor of anthropology and Boedy rides a red and concert talk with the artists will begin at 6:30 one of this year's four University Scholars, was yellow plastic tricycle with utter abandon. p.m. UVM Recital Hall. studying colonialist photographs from Africa Information, tickets. when he noticed an odd pattern. Many of the Model Proposal MBA Oct. 2, Noon. Staff images showed a dog lurking around in the students Geoff Robinson Council Meeting. Livak and John Stewart background. -

Strange Bedfellows Strange Bedfellows Evan N
Strange Bedfellows Strange Bedfellows Evan N. Resnick U.S Bargaining Behavior with Allies of Convenience Throughout history, states have periodically made common cause with bitter adversaries for the purpose of confronting even more urgent national security threats. Although the term “alliance of convenience” has been widely used to depict these tenu- ous strategic partnerships, the dynamics of such alliances have yet to be sys- tematically explored by international relations scholars and U.S. policymakers. This is puzzling, given that alliances with unsavory, unreliable, and dangerous enemies—including Louis XVI’s France during the American Revolutionary War, Joseph Stalin’s Soviet Union during World War II, Mao Zedong’s China during the Cold War, and Saddam Hussein’s Iraq during the Iran-Iraq War— have repeatedly proven necessary to thwart a host of even greater near-term threats to the United States and its interests since the country’s founding. A crucial yet heretofore unexamined puzzle stemming from this recurrent phenomenon pertains to the terms on which the United States’ alliances of convenience have been consummated and maintained. Historically, in the face of shared threats, has the United States tended to exact a high price for its mili- tary cooperation with allies of convenience, or, more troubling, has it borne the heavier burden of creating and sustaining such partnerships? The answer to this question carries salient implications for current and future U.S. national security policy. As U.S. hegemony continues to erode as a result of a severe economic recession, rising government debt, and the continu- ing costs of the military interventions in Afghanistan and Iraq, U.S. -

Marshall Aid Commemoration Commission Year Ending 30 September 2013
ANNUAL REPORT Marshall Aid Commemoration Commission Year ending 30 September 2013 A Non-Departmental Public Body of 60 Sixtieth Annual Report of the Marshall Aid Commemoration Commission for the year ending 30 September 2013 Presented to Parliament by the Secretary of State for Foreign and Commonwealth Affairs pursuant to section 2(6) of Marshall Aid Commemoration Act 1953 A Non-Departmental Public Body of March 2014 Sixtieth Annual Report: Marshall Aid Commemoration Commission © Marshall Aid Commemoration Commission (2014) The text of this document (this excludes, where present, the Royal Arms and all departmental or agency logos) may be reproduced free of charge in any format or medium provided that it is reproduced accurately and not in a misleading context. The material must be acknowledged as Marshall Aid Commemoration Commission’s copyright and the document title specified. Where third party material has been identified, permission from the respective copyright holder must be sought. Any enquiries related to this publication should be sent to us at [email protected] This publication is available at https://www.gov.uk/government/publications Print ISBN 9781474100267 Web ISBN 9781474100274 Printed in the UK by the Williams Lea Group on behalf of the Controller of Her Majesty’s Stationery Office ID P002625532 03/14 Printed on paper containing 75% recycled fibre content minimum 4 Sixtieth Annual Report: Marshall Aid Commemoration Commission Contents Introduction 6 Welcome from the MACC Chair Dr John Hughes 6 MACC Membership and Meetings -

Butler Hansen a Trailblazing Washington Politician John C
Julia Butler Hansen A trailblazing Washington politician John C. Hughes Julia Butler Hansen A trailblazing Washington politician John C. Hughes First Edition Second Printing Copyright © 2020 Legacy Washington Office of the Secretary of State All rights reserved. ISBN 978-1-889320-45-8 Ebook ISBN 978-1-889320-44-1 Front cover photo: John C. Hughes Back cover photo: Hansen Family Collection Book Design by Amber Raney Cover Design by Amber Raney and Laura Mott Printed in the United States of America by Gorham Printing, Centralia, Washington Also by John C. Hughes: On the Harbor: From Black Friday to Nirvana, with Ryan Teague Beckwith Booth Who? A Biography of Booth Gardner Nancy Evans, First-Rate First Lady Lillian Walker, Washington State Civil Rights Pioneer The Inimitable Adele Ferguson Slade Gorton, a Half Century in Politics John Spellman: Politics Never Broke His Heart Pressing On: Two Family-Owned Newspapers in the 21st Century Washington Remembers World War II, with Trova Heffernan Korea 65, the Forgotten War Remembered, with Trova Heffernan and Lori Larson 1968: The Year that Rocked Washington, with Bob Young and Lori Larson Ahead of the Curve: Washington Women Lead the Way, 1910-2020, with Bob Young Legacy Washington is dedicated to preserving the history of Washington and its continuing story. www.sos.wa.gov/legacy For Bob Bailey, Alan Thompson and Peter Jackson Julia poses at the historic site sign outside the Wahkiakum County Courthouse in 1960. Alan Thompson photo Contents Preface: “Like money in the bank” 6 Introduction: “Julia Who?” 10 Chapter 1: “Just Plain Me” 17 Chapter 2: “Quite a bit of gumption” 25 Chapter 3: Grief compounded 31 Chapter 4: “Oh! Dear Diary” 35 Chapter 5: Paddling into politics 44 Chapter 6: Smart enough, too 49 Chapter 7: Hopelessly disgusted 58 Chapter 8: To the last ditch 65 Chapter 9: The fighter remains 73 Chapter 10: Lean times 78 Chapter 11: “Mrs. -

To Speak One's Mind Society's Lonesome End the Isle Is Full of Noises
Ieman• orts March 1968 To Speak One's Mind John S. Knight Society's Lonesome End W es Gallagher The Isle is Full of Noises Sir William Haley 2 NIEMAN REPORTS editor who carried his policy in his hat and expressed the mood in which he got out of bed in the morning. But since Lippmann the column itself has become increasingly NiemanR~ports a stereotype. The reader can classify and label it-Buckley, right wing; Alsop, pro war; McGill, civil rights; Kempton, VOL. XXII, NO. 1 MARCH 1968 liberal; and so on. There may be exceptions. But for the most part the na Louis M. Lyons, Editor, 1947-64 tionally syndicated columnist is limited to certain few na tionally accepted topics. He deals either with the policy and Dwight E. Sargent, Editor performance of the national administration, or at another Editorial Board of the Society of Nieman Fellows level with the celebrity whose private life is public game. Robert W. Brown C. Ray Jenkins One has to look elsewhere for the rare examples of per Rock Hill Evening Herald Alabama Journal sonal journalism. Cervi's Journal in Denver is so personal Millard C. Browne John Strohmeyer in its views and so uninhibited that one assumes Gene BuHalo News Bethlehem Globe-Times Cervi writes it all himself. It is by no means restricted to William B. Dickinson E. J. Paxton, Jr. the main lines of the daily news headlines but it has its solid Philadelphia Bulletin Paducah Sun-Democrat following. The Carolina Israelite is of course the personal Tillman Durdin Harry T. -

John T. Hughes Papers 1909-1945 (Bulk 1921-1945) MS.1986.160
John T. Hughes Papers 1909-1945 (bulk 1921-1945) MS.1986.160 https://hdl.handle.net/2345.2/MS1986-160 Archives and Manuscripts Department John J. Burns Library Boston College 140 Commonwealth Avenue Chestnut Hill 02467 library.bc.edu/burns/contact URL: http://www.bc.edu/burns Table of Contents Summary Information .................................................................................................................................... 3 Administrative Information ............................................................................................................................ 4 Biographical note ........................................................................................................................................... 5 Scope and Contents ........................................................................................................................................ 5 Arrangement ................................................................................................................................................... 6 Collection Inventory ....................................................................................................................................... 7 I: Clippings, articles, and obituary .............................................................................................................. 7 II: Correspondence ...................................................................................................................................... 7 III: Photographs -

“The Creative Producer”: John Hughes, Synergy and Late 1980S Hollywood
A University of Sussex DPhil thesis Available online via Sussex Research Online: http://sro.sussex.ac.uk/ This thesis is protected by copyright which belongs to the author. This thesis cannot be reproduced or quoted extensively from without first obtaining permission in writing from the Author The content must not be changed in any way or sold commercially in any format or medium without the formal permission of the Author When referring to this work, full bibliographic details including the author, title, awarding institution and date of the thesis must be given Please visit Sussex Research Online for more information and further details 1 MAINSTREAM MAVERICK? JOHN HUGHES AND NEW HOLLYWOOD CINEMA HOLLY CHARD SUBMITTED FOR THE DEGREE OF DOCTOR OF PHILOSOPHY UNIVERSITY OF SUSSEX MAY 2014 2 I hereby declare that this thesis has not been and will not be, submitted in whole or in part to another university for the award of any other degree. Signature:……………………………………… 3 UNIVERSITY OF SUSSEX HOLLY CHARD SUBMITTED FOR THE DEGREE OF DOCTOR OF PHILOSOPHY MAINSTREAM MAVERICK? JOHN HUGHES AND NEW HOLLYWOOD CINEMA SUMMARY My thesis explores debates on the commercial and textual priorities of New Hollywood cinema through examination of the career of John Hughes. I argue that scrutiny of Hughes’ career and the products associated with him expose the inadequacy of established approaches to cinematic authorship and New Hollywood cinema. By mounting a historically grounded investigation of Hughes’ career, his status within the cinema industry, and his work as a commercially successful and agenda-setting filmmaker, I aim to reevaluate existing perspectives on post-1970s mainstream popular U.S.